Finding Cracks in the Wall: The Hazard of Single Authentication Factor

The use of authentication factors, one of the most fundamental and well understood concepts in information security, enables secure access to applications, services, and networks. While proper authentication improves security posture, the drastic increase in data breaches and system attacks are largely based on compromised authentication.
Authentication factors are classified as follows:
“Something I know” such as website credentials
“Something I have" such as a hardware security key
"Something I am" such as a fingerprint identification
The most prevalent authentication method is user credentials, also known as username and password. Credentials are commonly used to authenticate access to any online service, from bank accounts, to shopping carts, to company networks. As credentials became more widely used, the attacks to steal or abuse this authentication method also increased and evolved. Most noticeable are credential abuse attacks using stolen usernames and passwords to try to compromise accounts, exploiting the common habit of reusing the same credentials on different services.
The significant increase in data breaches we have seen over the past several years was primarily driven by compromised credentials. Compromised credentials provide threat actors the ability to launch internet-wide credential abuse attacks to hunt for accounts that are being accessed using those credentials.
The amplification impact of these attacks is achieved by the use of dedicated tools that can be customized to the targeted login interface as well as the use of botnet and proxy services that distribute and hide the attackers' origins.
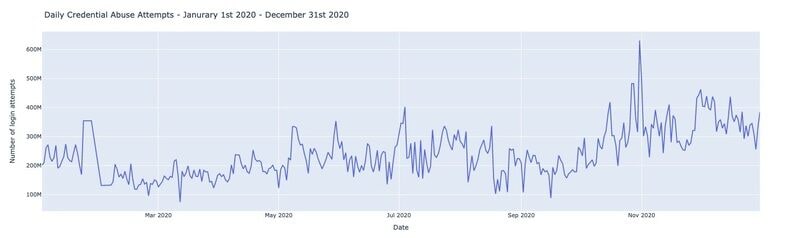 Figure: Number of daily credential abuse attempts in 2020
Figure: Number of daily credential abuse attempts in 2020
This figure shows the daily number of credential abuse attempts seen on the Akamai platform -- the average number of credential abuse attempts in 2020 was more than 200 million attempts per day. In addition, looking into the yearly trend of attacks shows a continued increase in the number of attempts, which reached a peak of more than 600 million attempts at the end of September 2020.
This continued increase in attacks represents threat actors' increased motivation to own compromised accounts as a function of the increased demand to reuse stolen credentials, mainly those that are associated with media services. A similar and complementary impact on the threat landscape was also observed by Akamai's threat research team over the same months in the phishing attacks in 2020, representing the increase in threat actor motivation to steal users' credentials to later be used in credential abuse scams.
As credential abuse attacks increased in the past few years, enterprises quickly realized that users' credentials alone are insufficient to ensure the authenticity of the connected user, leading to the increased adoption of multi-factor authentication (MFA) architecture. Enterprises were the first to adopt MFA, as the potential damage of compromised accounts can result in a data breach, stolen intellectual property, and reputational damage.
MFA enables the hardening of the user authentication process by using more than a single identification factor to reduce the risk of fraudulent and malicious activities. Each independent authentication factor gives more confidence in the authenticity of the connected user and reduces the risk of unauthorized access in the event one of those factors is stolen or lost.
Once more than one factor is being used, all the authentication factors need to be stolen or compromised in order for the unauthorized authentication to be successful. While such a scenario is harder to execute, a recent Akamai's threat research publication shows that threat actors have now stepped up their game and can now overcome MFA.
Compromising an account that is protected by MFA is more challenging, but not impossible. In recent years, we have seen more and more scams leveraging victims' mistakes and exploiting MFA weaknesses. This enables cybercriminals to execute sophisticated attacks against enterprises and allows individuals to execute fraud activities and steal sensitive data.
The turning point for the more widespread adoption of MFA will be driven by the combination of scale and order of magnitude of the credential abuse attacks and the potential damage and value of the compromised account.
In the next blog post, I will cover the details of some of the most recently observed attacks, explain the most common MFA bypass methods, and discuss what can be done to improve users' authentication and avoid unnecessary risk and the potential damage.
Learn more about the Akamai MFA solution at akamai.com/mfa.



