How Americaneagle.com Thwarted a Massive DNS DDoS Attack with Akamai Shield NS53
Blazing the trail with proactive digital infrastructure security
Founded in 1978, Americaneagle.com is an esteemed digital agency that offers a wide range of services to clients across industries and geographies.
One of the agency’s key services is web and Domain Name System (DNS) hosting on its state-of-the-art private cloud servers, demonstrating their position as an industry leader in web development and hosting. They managed the hosting of some of the world’s biggest brands, including Reinsurance Group of America (RGA), Portillo’s, United Airlines, MetLife Stadium, Chicago Transit Authority, and more.
As part of their commitment to providing strong network security, Americaneagle.com uses Akamai’s cybersecurity products to protect clients’ servers and other digital assets from distributed denial-of-service (DDoS) attacks — demonstrating exemplary leadership and reinforcing their reputation as a trustworthy digital partner.
Recently, the agency’s proactive security approach protected a client’s DNS infrastructure and the larger digital stack from a massive DDoS attack. DNS is a crucial base technology required for the internet to function — had the attacker succeeded in taking down the client’s DNS, the attack could have potentially spread to other clients and caused catastrophic repercussions.
Identifying the DNS DDoS attack
The Americaneagle.com client that came under cyberattack is a large, high-profile media company that hundreds of thousands of customers depend on daily. A successful attack could have had devastating consequences for the business and its customers. For this client’s end users, personal fortunes rise and fall in seconds — so a slow or unresponsive website could seriously damage the client’s business and reputation.
Cambridge, we have a problem!
In the first week of May 2024, Americaneagle.com’s team noticed that their client’s authoritative DNS nameservers were experiencing an unusually high query volume.
As a longtime user of Akamai Prolexic, the industry’s most robust and comprehensive DDoS protection platform, Americaneagle.com collaborated with Akamai’s Security Operations Command Center team in Cambridge, Massachusetts, to investigate if this was a DDoS attack.
It quickly became apparent that an attacker was targeting the client’s DNS nameservers by looking up pointer (PTR) records and creating a massive surge of illegitimate DNS queries. Attackers can use PTR records to identify whether a particular IP address is linked to a target domain name. Several publicly available tools facilitate such PTR lookups.
Types of DNS attacks
There are several different types of DNS attacks. In this instance, the attacker initiated a DNS resource exhaustion attack, a type of denial-of-service attack. This type of attack aims to disrupt DNS resolution, slowing down a website or app’s response rate and disrupting an API’s ability to respond to legitimate queries.
Such an attack can slow down or exhaust the DNS server resources and take the client offline. DNS resource exhaustion attacks are also often referred to by other names, including NXDOMAIN floods, pseudo-random subdomain attacks, or just simply DNS flood attacks.
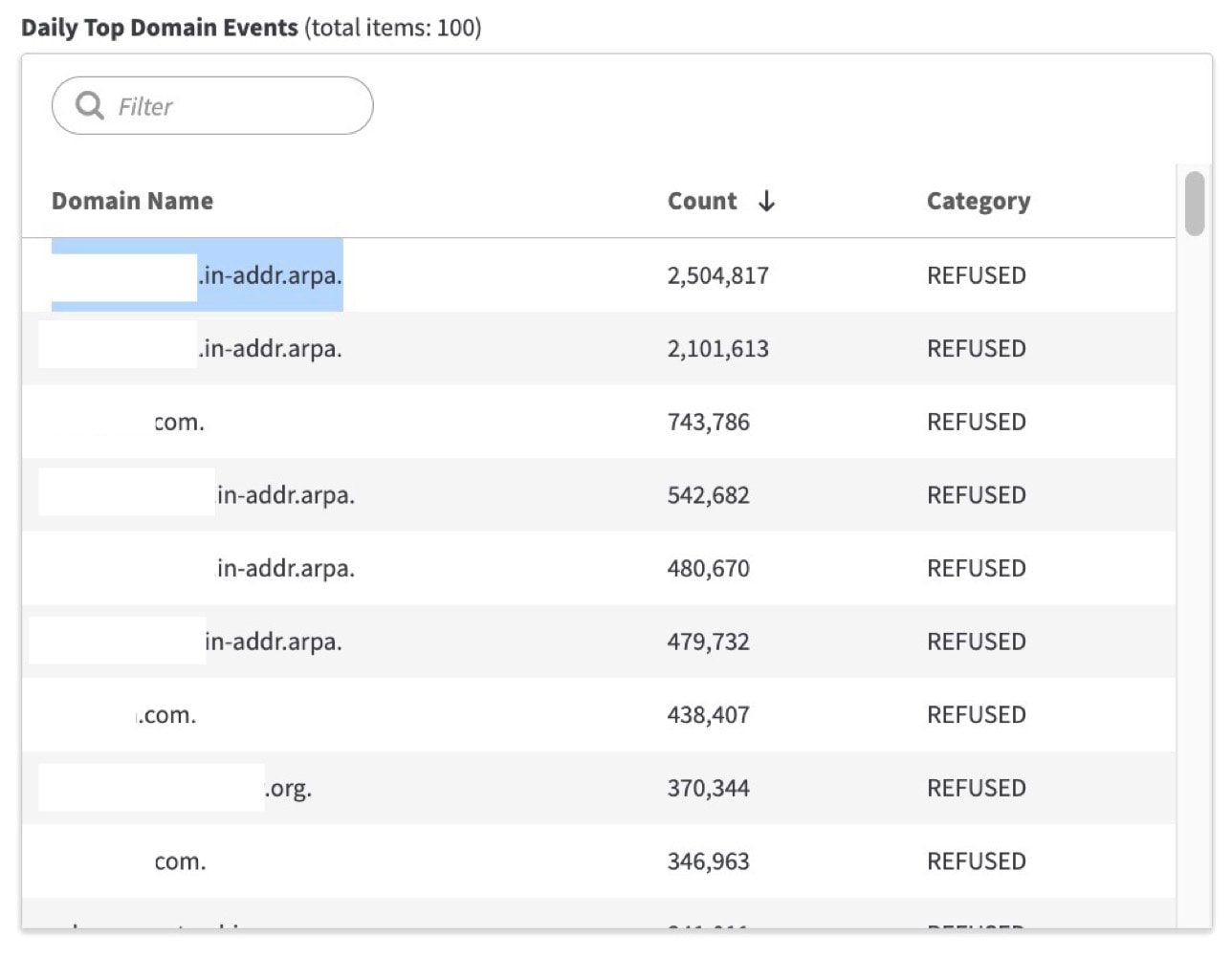
Reverse DNS lookups for IPv4 addresses use the special domain in-addr.arpa: a second-level domain suffix that’s appended to a 32-bit IPv4 address to aid in the reverse lookup process. Attackers used this method to identify the client’s DNS records and send illegitimate DNS queries ranging from several thousand to millions per IP address (Figure 1).
The solution: Akamai Shield NS53
Americaneagle.com and Akamai security teams worked together to rapidly onboard the recently launched Akamai Shield NS53 solution.
Shield NS53 is a DNS proxy solution that implements proactive security policies and drops all illegitimate DNS requests at the edge of Akamai’s network. The solution is designed precisely for scenarios like Americaneagle.com’s, where on-premises or private cloud and/or hybrid DNS infrastructure — including DNS nameservers, global server load balancers, and firewalls — are protected from resource exhaustion attacks with a zero-second SLA. The implementation of Shield NS53 is quick and the solution can be easily self-configured by customers without requiring any additional service.
DNS attack mitigation
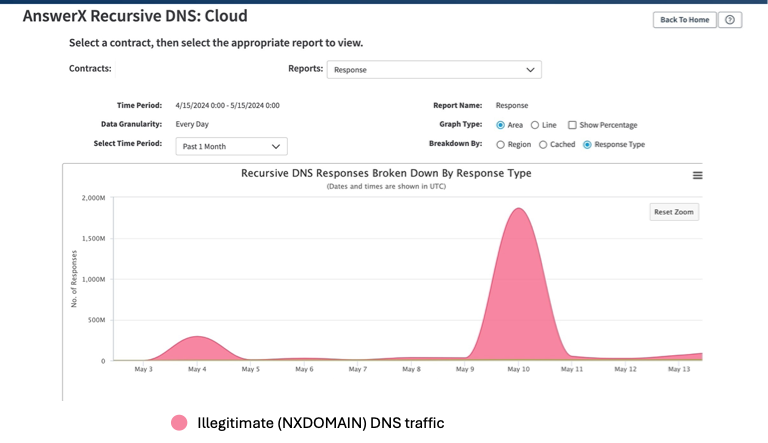
The threat actor launched the attack on May 10, 2024, with nearly two billion illegitimate DNS queries sent over four hours. The scale of this attack was 200 times the baseline DNS traffic for that particular client of Americaneagle.com.
Akamai Shield NS53 immediately and successfully blocked the illegitimate DNS query attack at the edge of the network with no impact whatsoever on the speed, performance, or availability of the client’s DNS services (Figure 2).
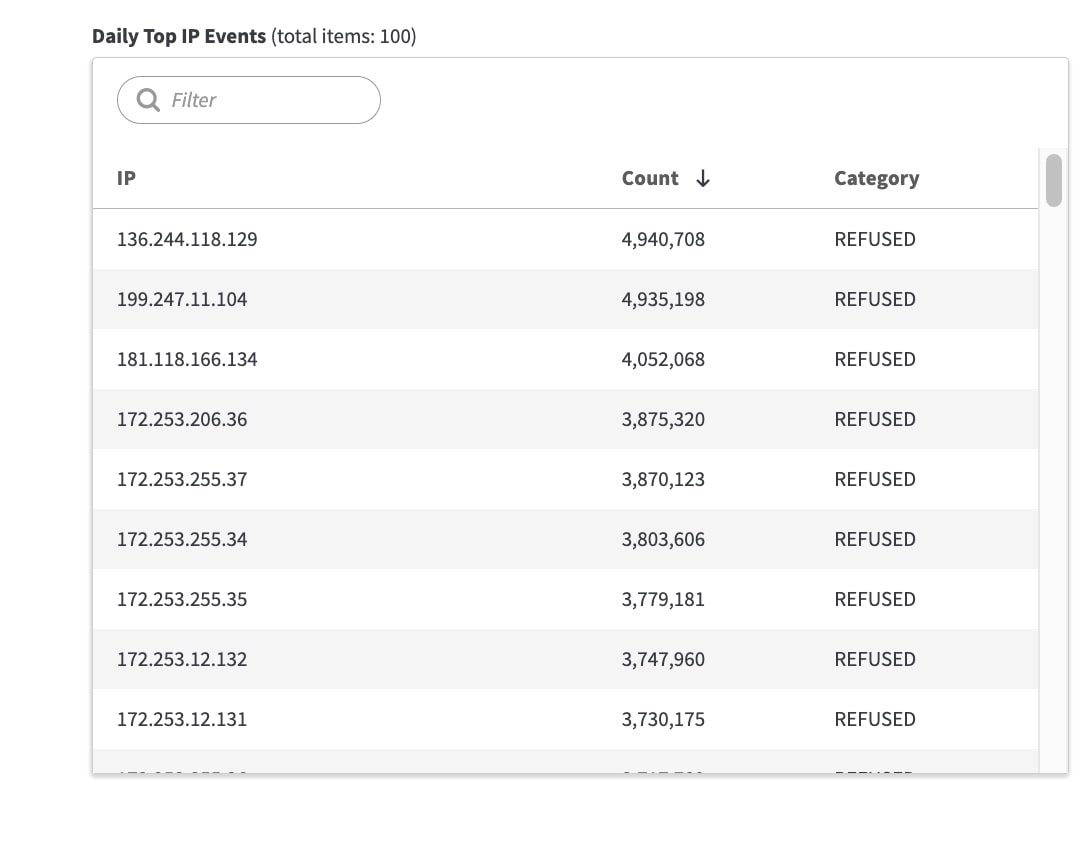
Some of the IPs sent as many as 4.9 million illegitimate DNS queries, which were effectively blocked or “refused” by Akamai Shield NS53 (Figure 3).
The NXDOMAIN attack playbook
NXDOMAIN DDoS attacks often follow a standard playbook.
They trigger millions or billions of illegitimate DNS queries for nonexistent domains or subdomains (hence the acronym NXDOMAIN).
They create randomized and unique illegitimate queries to avoid repeats, thus getting filtered out by the upstream DNS resolver cache.
They force the authoritative DNS nameservers to relentlessly search for such nonexistent domains or subdomains, to a point where the performance effectively degrades and ultimately gets overwhelmed enough to go offline.
Protection against NXDOMAIN flood attacks
With Shield NS53, Americaneagle.com strengthens DNS security and protects the key components of its origin DNS infrastructure. It also improves DNS service for its clients, creating a smart buffer between the components and potentially malicious queries. Shield NS53 comes with an industry-leading, zero-second SLA to stop NXDOMAIN flood attacks.
The Akamai Shield NS53 cache also helps alleviate the load on DNS infrastructure. The DNS cache responds to legitimate requests and drops illegitimate queries at the Akamai network’s edge. Queries are only forwarded to the origin nameservers when it’s absolutely necessary. Nonexistent subdomain queries are rejected.
Improved user experience and reduced spending
Akamai Shield NS53 also reduces latency, improving the user experience for all its clients. It does this by accessing Akamai’s global anycast network. The network has thousands of servers, and responses to user queries come from the closest location. Proximity of the user and the responding server reduces or eliminates lag times.
The only other solution Americaneagle.com could have used to protect itself and its clients was to increase capacity exponentially, resulting in wasteful redundancy, technological challenges related to scaling, and significant spending.
Americaneagle.com’s investment in Akamai Shield NS53 protected its competitive stance in the market by keeping defensive costs contained for itself and its clients.
Strengthen your organization’s threat intelligence
Protect your on-premises and hybrid DNS infrastructure from attackers who are looking to exploit vulnerabilities. Akamai Shield NS53 is a flexible and scalable solution that allows you to self-configure and enforce your own dynamic policies in real time.