Akamai Guardicore Platform: Microsegmentation Just Got a Whole Lot Better
Executive summary
Today’s landscape of increasing — and increasingly complex — cyberthreats underscores the continual need for innovative cybersecurity solutions to protect against relentless cyberattacks.
The Akamai Guardicore Platform is based on a leading microsegmentation solution for enterprise organizations looking to minimize attack surfaces.
Multi-Factor Segmentation directly integrates multi-factor authentication (MFA) with Akamai Guardicore Platform’s segmentation rules to offer an additional layer of network and data security, ensuring that only authenticated users can access specific services and ports.
Essential Policies immediately protects organizations’ networks without the need to learn complex traffic patterns, enables network administrators to mitigate common attack vectors, and quickly and easily enhances overall resilience.
Worksites gives organizations granular control over network traffic, autonomy over security policies to improve network visibility, and more, for multisite environments.
Cyberthreats are a constant challenge for organizations, growing more complex and frequent over time. In 2024, IBM’s X-Force Threat Intelligence Index report highlighted a 71% year-over-year increase in attacks using stolen or compromised credentials, showing a significant shift toward credential-based entry points over traditional hacking methods like malware, as well as rising incidents of sensitive data theft and leaks.
Additionally, in 2023, the FBI reported a record 880,418 cybercrime complaints, with potential losses exceeding US$12.5 billion.
Together, these figures underscore the continual need for innovative and impactful cybersecurity solutions to protect against relentless cyberattacks.
Handling the microsegmentation heavy lifting
Akamai reaffirms our ongoing commitment to offering excellent, innovative security solutions beyond basic firewalls by further optimizing the Akamai Guardicore Platform, which is based on a leading microsegmentation solution for enterprise organizations that are looking to minimize attack surfaces. Our experts pay close attention to the cybersecurity landscape by monitoring the latest events and emerging threats to continually improve organization-wide microsegmentation, as well as other types of network segmentation.
We’re pleased to introduce a suite of Akamai Guardicore Platform features designed to streamline workflows, enhance business resilience, and do all the microsegmentation heavy lifting for enterprise organizations. These new features will empower businesses to more rapidly implement robust security measures with minimal business disruptions.
Read on to learn more about three new Akamai Guardicore Platform features and discover how they can save your team time while reducing security policy management complexity.
Enhancing end-to-end security with Multi-Factor Segmentation
Identity theft has become a significant pain point for organizations worldwide. Across industries and geographies, cybercriminals regularly exploit network vulnerabilities to obtain stolen or compromised credentials and gain unauthorized access to sensitive resources.
As a result, many organizations fall victim to data breaches and data theft — with potentially devastating impacts on customer trust, brand reputation, and their bottom line. Unfortunately, traditional security measures often fall short in preventing these breaches — highlighting the need for a more robust cybersecurity solution.
In response to this urgent threat, we’re pleased to introduce Multi-Factor Segmentation: Akamai’s advanced approach to directly integrating multi-factor authentication (MFA) with Akamai Guardicore Platform’s segmentation rules. This powerful feature offers businesses an additional layer of network and data security, ensuring that only authenticated users can access specific services and ports.
As a result, Multi-Factor Segmentation drastically reduces the risk of unauthorized entities accessing data on your:
Computer networks, including internal networks
Subnetworks (subnets)
Virtual local area networks (VLANs)
Virtual private networks (VPNs)
Cloud environments
Network endpoints
Network perimeters
Multi-Factor Segmentation also minimizes lateral movement of those entities between devices on your segmented network.
What sets Multi-Factor Segmentation apart from other microsegmentation options?
Multi-Factor Segmentation offers unmatched flexibility by using technology to secure your network across all touchpoints — including ports and services — without the need for specific network configurations like software-defined networking (SDN). Multi-Factor Segmentation extends MFA security to workloads, ensuring that critical network resources are only accessible to verified users on your access control lists.
With seamless integrations with leading identity providers (IdPs) like Okta, Duo, and Azure Active Directory, Multi-Factor Segmentation eliminates the need for complex migrations or additional hardware. Accordingly, Multi-Factor Segmentation streamlines user management and authentication processes, enhancing organizational security without disrupting existing workflows.
Having an IP address is no longer sufficient; users must authenticate with their IdP to gain access, which ensures that only legitimate users can interact with all the different parts of the network (Figure 1).
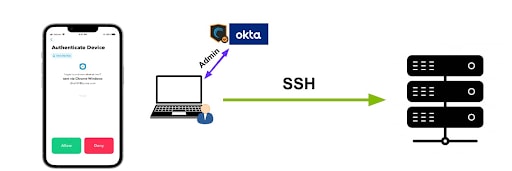 Fig. 1: Authenticated users are only allowed access to the destination after MFA approval
Fig. 1: Authenticated users are only allowed access to the destination after MFA approval
The idea behind Multi-Factor Segmentation is simple yet powerful: only when MFA is approved can an authenticated user access a destination — all others are blocked.
Once connected to the network, users must authenticate with their IdP to approve the connection (Figure 2). Akamai can integrate with any IdP you already use, so you can keep working with the IdP you’re already comfortable with — no need to transition to Akamai as your IdP.
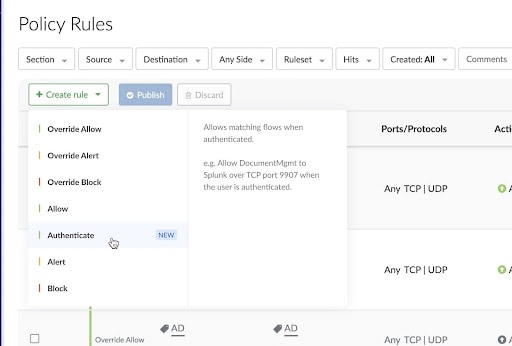 Fig. 2: The new Authenticate rule requires authenticating users before they can initiate a connection
Fig. 2: The new Authenticate rule requires authenticating users before they can initiate a connection
Core benefits of Multi-Factor Segmentation
Enhanced security. By requiring MFA for network access, Multi-Factor Segmentation significantly reduces the risk of unauthorized access and lateral movement.
Seamless integration. Multi-Factor Segmentation seamlessly integrates with popular IdPs, minimizing the need for complex migrations or additional hardware.
Comprehensive logging and reporting. Multi-Factor Segmentation provides organizations with detailed authentication attempt logs, which creates an audit trail that serves as a central source of truth for security monitoring, incident analysis, and regulatory compliance.
Unified management. With Multi-Factor Segmentation you no longer have to manage multiple segmentation policies and enforcement rules. Instead, easily manage and administer all your Multi-Factor Segmentation configurations with enhanced network visibility from one central user interface.
Key Multi-Factor Segmentation use cases
Protect remote access to critical servers. Secure frequently used services like remote desktop protocol (RDP) and secure shell (SSH) from unauthorized access
Secure collaboration. Ensure secure access for third-party collaborators without needing to control their network devices
Access behavioral insights. Gain visibility into MFA interactions and identify anomalous behaviors in your network that could indicate security threats
Simplify network security with Essential Policies
Network security management often requires extensive customization to establish effective security strategies and measures. But applying policies to the entire network can be time-consuming and resource-intensive, which could potentially delay the implementation of critical protections and leave networks vulnerable to attacks.
More robust network performance and protection
Essential Policies changes the status quo by introducing a set of global rules ready for immediate implementation, and gives organizations more robust network performance and protection. Akamai’s security experts developed these Essential Policies rules based on industry best practices and insights gained from big data analysis and machine learning (ML) technologies.
With Essential Policies, organizations’ networks are immediately protected with no need for their teams and leaders to learn complex traffic patterns and label assets.
From the Essential Policies dashboard, network administrators can mitigate common attack vectors and enhance overall resilience in only a few clicks (Figure 3). Essential Policies also includes a comprehensive library of predefined rulesets tailored to various industry standards and best practices, which allows rapid deployment of policies that more stringently comply with regulatory requirements.
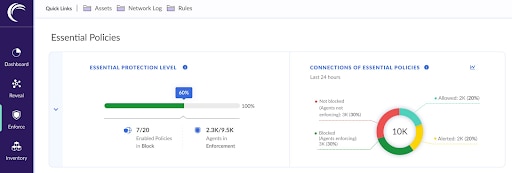 Fig. 3: Essential Policies screen in the Akamai Guardicore Platform
Fig. 3: Essential Policies screen in the Akamai Guardicore Platform
Core benefits of Essential Policies
Immediate protection. Essential Policies allows you to implement organization-wide policies from day one, ensuring instant defense against common and emerging cyberthreats.
Simplified management. You’ll save time and minimize complexity with a user-friendly dashboard for managing policies, monitoring high-risk traffic flows, and tracking security progress.
Enhanced security and resiliency. Essential Policies uses predefined rules based on industry best practices, as well as insights derived from big data analysis and machine learning by our security experts, to ensure continuously refined and optimized security measures.
Key Essential Policies use cases
Rapid response to emerging threats. Quickly deploy predefined security strategies tailored to addressing new and evolving threats to protect your network against the latest attack vectors
Compliance readiness. Comply with all your sector’s regulatory requirements without extensive manual effort using predefined security controls aligned with security industry standards and best practices
Improved operational efficiency. Apply your global security policy to all network entities, regardless of context, application, or business unit, to elevate security standards throughout your entire data center
Manage multisite security with Worksites
For businesses with multiple locations or business units, managing security zones and policies can be complex. Overlapping IP addresses and diverse network architectures increase this complexity, making it difficult to maintain consistent security measures across the organization.
Granular control and autonomy
Worksites offers a streamlined solution by providing granular control and autonomy over security policies, addressing the unique challenges of multisite and multiunit environments. This policy management solution partitions policies into smaller, more manageable segments, allowing different business units or locations to control their own security policies. In doing so, Worksites ensures all security measures are specific to each site’s needs, enhancing your overall security posture.
Worksites also features advanced role-based access control (RBAC) functionality for independently managing multiple sites, offering organizations granular control over network traffic while facilitating policy delegation. With Worksites, IT teams can assign assets, improve network visibility through filtered maps, and more flexibly scope traffic for diverse multisite environments (Figure 4).
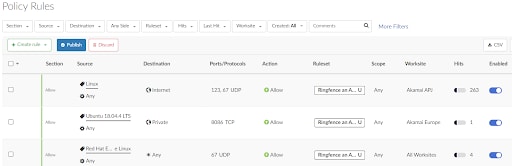 Fig 4: Worksites column on the Policy Rules screen in Akamai Guardicore Platform
Fig 4: Worksites column on the Policy Rules screen in Akamai Guardicore Platform
Core benefits of Worksites
Enhanced policy administration. Worksites simplifies administration with a centralized platform for managing policies across multiple sites or divisions, ensuring consistent organization-wide security measures while still allowing for customization based on specific site requirements.
Improved security posture. With Worksites, you can align security measures with each site's specific requirements, keeping policies effective and relevant to the evolving threat landscape.
Optimized operational efficiency. You can automate policy enforcement and management to reap the benefits of network segmentation and reduce complexity, affording your security teams more time to focus on strategic initiatives.
Key Worksites use cases
Delegated policy management. Enable different business units or locations to independently manage their own security policies, ensuring tailored security measures for each environment
Streamlined mergers and acquisitions. Group your assets based on divisions or business units to more flexibly scope security policies during significant organizational transitions
Multi-environment segmentation. Manage complex scenarios involving overlapping IP addresses and diverse network architectures by logically separating assets and policies, ensuring more consistent security measures across different business environments
Evolve microsegmentation across your organization
In an era dominated by relentless cyberattacks, the Akamai Guardicore Platform stands out as an example of cybersecurity innovation. With our suite of microsegmentation models, all part of the Akamai Guardicore Platform, organizations can do more than defend their business; they can proactively combat new and emerging cyberthreats.
Akamai Guardicore Platform is available now, complete with the latest microsegmentation updates, so you can start evolving your organization’s security posture without network congestion hassles. Contact us to learn what this microsegmentation and Zero Trust security solution can do for your organization.



