Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
Network security is an area of cybersecurity that is dedicated to protecting computer networks from cyberthreats , intrusions, and breaches. The primary objective of network security is to employ security measures that prevent unauthorized access to an organization’s IT network or its various components, while allowing legitimate users to access the resources they need without delay.
How does network security work?
Today’s IT networks are increasingly complex and highly distributed, making network security more important than ever. Combining multiple layers of defense, network security involves a variety of software and hardware solutions along with policies, processes, and best practices required to keep network resources safe from attackers.
What are the types of network security?
Network security typically involves three layers of controls: physical, technical, and administrative.
Physical security controls prevent unauthorized individuals from accessing the hardware that powers a network, including routers and cabling in data centers. Physical security controls may include locks, biometric authentication, and physical access control.
Technical security controls protect data stored on or moving in and out of the network. Technical controls are designed both to block access by unauthorized personnel as well as malicious insiders.
Administrative controls are the security policies and processes that authenticate users, govern their behavior, manage their level of access, and permit IT administrators to implement changes to network infrastructure.
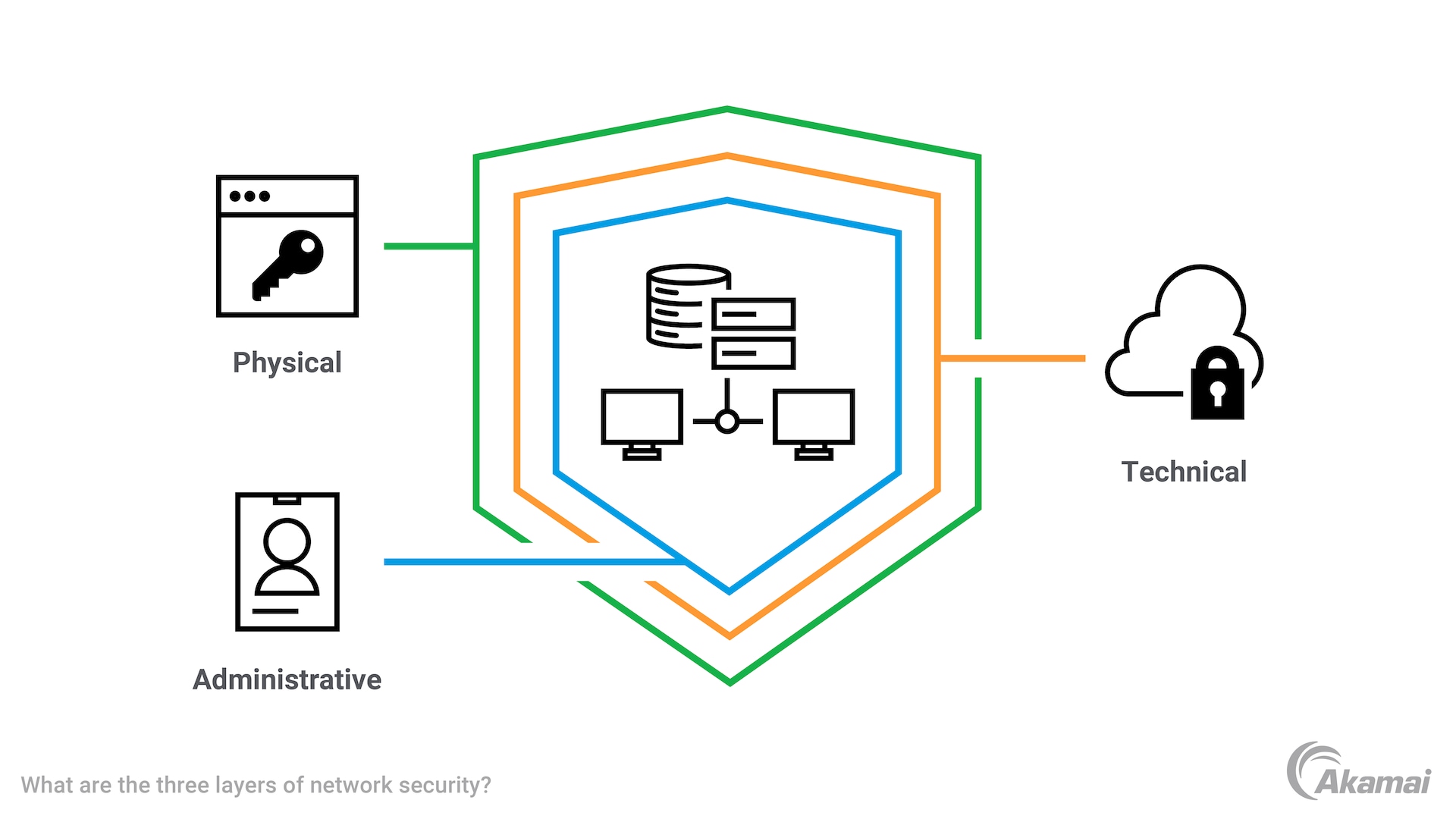 Diagram illustrating the three layers of network security
Diagram illustrating the three layers of network security
What are threats to network security?
Common network security threats include:
Authentication issues. When users, devices, and applications are not appropriately or accurately authenticated, hackers may easily gain unauthorized access to network resources.
Injection attacks. Attackers may use operating system command injection or SQL injection to cause an application or server to perform unauthorized actions that compromise the network.
Lack of encryption. When unencrypted data is purposefully or accidentally exposed, it can be easily read or accessed by malicious individuals or the general public.
Malware attacks. Attackers often gain access to networks by infecting network devices with malicious software (malware) that spreads easily from one device to another. Malware can execute a wide range of malicious actions such as exfiltrating data, causing disruption, or launching larger attacks.
Password attacks. Hackers frequently gain access to networks by exploiting weak or reused passwords, or passwords that have been exposed in a data breach. Hackers may also access networks by guessing or cracking passwords.
Social engineering. Social engineering attacks like phishing or spear phishing use deception to dupe users into sharing confidential information like login credentials or credit card account numbers.
Viruses. Viruses are malicious files that spread from one device or application to another to corrupt or destroy data, or alter code in malicious ways.
Trojans. A Trojan is a type of virus that creates a backdoor, which allows hackers to access a computer system.
Ransomware. Ransomware is a type of malware that encrypts files on networks and devices, preventing users from accessing data or applications. Ransomware allows cybercriminals to demand a ransom in exchange for a decryption key.
Denial of service. In denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks, hackers cause servers or other network resources to slow down or crash by overwhelming them with malicious requests. As a result, the servers can no longer provide service to legitimate users or requests.
What are network security technologies?
Network security encompasses a broad array of technologies and solutions.
Firewalls. Firewalls monitor traffic entering or leaving a network and use security policies to block, quarantine, or flag any traffic that is deemed to be suspicious.
Segmentation. Network segmentation partitions a network into smaller segments, enabling administrators to implement more granular security controls and policies. Tools like software-defined microsegmentation can even protect individual workloads and assets to prevent unauthorized access or lateral movement.
Antivirus software. To mitigate viruses, antivirus solutions scan network traffic for known signatures that indicate malicious activity, based on constantly updated threat intelligence.
Network access control. By limiting network access to specific users, groups, and devices, organizations can prevent unauthorized use of network resources.
Anti-malware. Anti-malware technology detects, removes, and blocks malware such as Trojans, ransomware, spyware, and adware.
Data leak prevention (DLP). DLP solutions classify data assets within the organization, identify the most important and at-risk assets, manage policies around who can access and use those assets, and monitor activity to block suspicious behavior.
Email security. Email security solutions monitor both the content and metadata of email messages to identify and block malware and phishing attacks that commonly use email as an attack vector.
Intrusion detection systems (IDS) and intrusion prevention systems (IPS). IDS and IPS solutions detect and block unauthorized attempts to access the network.
Security information and event management (SIEM) platforms. SIEM solutions collect and aggregate data from internal security tools to uncover and alert network administrators to suspicious behavior.
VPN. A virtual private network (VPN) uses tunneling protocols to encrypt data that is transmitted across an unsecured network. VPNs may be used to enable remote access for employees working outside the office.
Security orchestration, automation, and response (SOAR) technology. SOAR solutions collect and analyze security data and enable security administrators to define and execute automated responses to specific cyberthreats.
Network detection and response (NDR). NDR platforms use AI and machine learning to monitor network traffic and uncover suspicious or anomalous activity.
Endpoint security. Every device connected to a network is a potential target for attackers. Endpoint security solutions enable teams to quickly protect against malware and other threats on various devices.
Extended detection and response (XDR). An XDR platform is an open architecture that integrates a range of security tools to unify security efforts across multiple layers, including users, applications, cloud workloads, data, endpoints, and email. XDR platforms allow diverse solutions to work together more easily.
Why is network security important?
Network security helps organizations mitigate several kinds of risk.
Financial risk. A successful data breach can easily cost a company millions of dollars in lost productivity, fines, and penalties, plus the cost of mitigating attacks and recovering data.
Operational risk. Cyberattacks frequently disrupt business operations by taking down networks, servers, and applications. As a result, employees and customers no longer have access to the data, services, and applications they rely on, causing operations to slow down or halt completely.
Regulatory risk. Governments around the world have enacted regulations that require organizations to take precautions to protect the private and sensitive data of customers, patients, and citizens. When businesses fail to adequately protect their networks, they may incur regulatory fines and legal action.
Business risk. When a network is compromised, all of the intellectual property and business plans within it may be compromised as well. This can lead to significant business losses as well as damage to competitive advantage.
What are the benefits of network security?
Network security enables organizations and security teams to:
Defend against cyberthreats. Network security solutions protect the network, users, and data from a broad range of cyberthreats and prevent the kinds of breaches that can result in costly losses of data, revenue, business, and reputation.
Enable business continuity. Network security ensures the continued availability and performance of the network, and ensures that businesses, users, and applications have access to the resources they need.
Maintain privacy. Network security solutions are critical for preventing security breaches that may expose confidential data, trade secrets, financial records, personally identifiable information (PII), and other sensitive information.
Ensure compliance. Network security helps organizations to comply with many regulatory frameworks, such as PCI DSS, GDPR, and HIPAA.
What are the challenges of network security?
Maintaining network security is frequently made more difficult by several factors.
Rapidly evolving attack vectors. As technologies evolve and networks become more complex, hackers inevitably find new ways to penetrate network defenses. Security teams must constantly monitor the network for known threats as well as new and emerging attack vectors.
User behavior. Many security teams find it a challenge to get users to adhere to security policies and best practices, especially when those measures require additional steps or extra time that distract users from their work.
Remote workforces. The trend toward mobile workforces and work-from-anywhere employees means more users are connecting to the network using unmanaged mobile devices and unsecured connections. This necessitates a paradigm shift in the way that users and devices are authenticated.
Third parties. Organizations today are more interconnected than ever. Many third parties, including cloud service providers and product vendors, have a certain amount of access to an organization’s network, creating new vulnerabilities and potential entry points for attackers.
What are best practices for network security?
To improve network security, IT teams may adopt solutions such as:
Multi-factor authentication (MFA). Many breaches are caused by weak, reused, or compromised passwords. MFA solutions prevent breaches by requiring users to present two or more forms of identification to be authenticated.
Security awareness training. From using weak passwords to clicking on malicious links, users frequently take actions that compromise network security. Awareness training helps users to recognize and avoid the techniques commonly used by attackers and to adopt appropriate security hygiene and behaviors.
Risk assessment. Conducting a cybersecurity risk assessment enables organizations to identify their most critical assets and the greatest risks to the security of each asset. This information helps administrators to prioritize network security strategies and investments.
Third-party risk management. Many companies have fallen prey to cyberattacks that initially targeted a company within their supply chain. Third-party risk management programs help organizations to identify the greatest areas of risk within their vendor relationships and to take steps to mitigate it.
Incident response plans (IRP). An IRP is a roadmap that enables security teams and organizations to take quick action that can limit the damage of a successful cyberattack or intrusion.
Least-privilege access. In traditional network security, users were frequently granted broad access to resources within the network. However, this allowed attackers who had successfully breached perimeter defenses to gain access to user accounts and highly valuable data. The principle of least privilege provides users, applications, and devices with access only to resources they need to perform a task at a given moment.
Zero Trust. A Zero Trust approach to security requires every user, device, and application to be authenticated and authorized on every request for access to network resources. This makes it much harder for hackers who have gained access to one part of a network to move laterally within it. It also enables security teams to quickly identify suspicious behavior and to limit the “blast radius” of successful attacks.
Encryption. Encryption helps to protect data from being exposed through malicious theft or inadvertent leaks.
Updates and patches. Adopting a regular and optimal cadence for updating software and applying patches can help to eliminate the vulnerabilities that attackers exploit to gain network access.
Deprecate unused software. Every public-facing application gives hackers another opportunity to penetrate defenses. By discarding unused apps, security teams can reduce the attack surface and eliminate vulnerabilities.
Frequent backups. Data should be frequently backed up to off-site locations that are protected from cyberthreats like ransomware, as well as from natural disasters or outages at a central data center.
FAQs
While network security solutions are designed to mitigate threats in network traffic and prevent attackers from accessing the network, application security focuses on defending against threats to internet-facing applications and application programming interfaces (APIs). Application security solutions help to identify and mitigate vulnerabilities in code as well as security misconfigurations, and to defend against the threats included in the OWASP Top 10 list. Application security occurs both at the development level and in production environments.
Network security is designed to protect data, applications, and resources at the network level by blocking threats within network traffic and preventing attackers from gaining unauthorized access.
Cloud security is intended to protect cloud environments, including cloud infrastructure managed by third-party service providers. In this context, cloud security includes network security but is also meant to protect servers, containers, applications, and services in cloud ecosystems.

