Discover the 3 Trends Driving API Security Compliance
Most security teams have the complex responsibility of keeping up with the ever-changing regulatory landscape. Of course, the regulatory demands change based on factors like industry, geographic footprint, business model, and technology choices. Meanwhile, APIs are continuing to be used as a primary interface for interacting with business applications and data, which complicates global regulatory compliance.
Security and privacy requirements are now very common components of industry and government regulations, and understanding where these requirements intersect with APIs can be challenging. Although some regulations spell out specific requirements for APIs, most provide more generalized guidance or standards. This puts the burden on security executives and their teams to identify how these regulations and frameworks extend to API security practices.
Why is it important to protect APIs?
APIs are used to connect your business to partners, suppliers, and customers and often carry sensitive data in the process. Each API presents a risk of exploitation, especially if they go undocumented or unmonitored within an organization.
The OWASP API Security Top 10 details the major vulnerabilities that can be found in APIs and the potential ways attackers can take advantage of them. The kind of information APIs exchange can incentivize attackers to look for vulnerabilities. This list includes:
Personally identifiable information
Protected health information
Financial information
Intellectual property
Confidential business information
Classified information
API attacks that scrape this data and then sell it or publish it online have produced news headlines and inspired governments and industries to include API security regulations in existing criteria regulating technology. Without implementing a solution that meets the latest compliance standards, organizations are at risk of experiencing:
Identity theft
Reputation damage
Legal consequences
Regulatory fines
Financial losses
National security risks
The 3 trends that are driving API security
We’ve been keeping up with the challenge of protecting APIs, and we’ve identified three trends that are driving API security compliance around the globe.
A global precedent for how to protect API estates
The more personal data your APIs contain, the sooner they will be regulated
API regulations are both market-driven and government-driven
A global precedent for how to protect API estates
By now, you’ve probably heard that the Payment Card Industry Data Security Standards (PCI DSS) was updated to version 4.0 in 2022. As part of this process, specific requirements that pertain to APIs were added. If you’re not familiar with this area of compliance, PCI DSS is a set of security standards designed to ensure that organizations that store, process, or transmit credit card information have effective security measures in place.
API security plays an essential role in PCI DSS compliance, as APIs can be used to handle sensitive cardholder data and facilitate payment processing. Because PCI DSS is a global standard, it sets a precedent for implementing similar practices.
The areas of the new standards that apply to APIs include:
Requirements 6.2.3 and 6.3.4. Review bespoke and custom software and protect it from common software attacks such as business logic attacks
Requirement 6.3.2. Keep a continuous inventory of bespoke and custom software so that patching vulnerabilities can occur throughout the organization
Requirements 6.4.1 and 6.4.2. Protect public-facing web applications by addressing new threats using automated detection and prevention of threats
Requirements 10.2.1 and 10.2.5. Enable audit logs for all system components and cardholder data, retaining them for at least 12 months, with at least 3 months available for analysis
Requirement 11.3.2.1. Perform external vulnerability scans after any significant change with tools that detect vulnerabilities operating outside the network
In addition to addressing specific API security requirements, it’s also important to consider how other general requirements in the PCI DSS v4.0 must extend to APIs in areas such as:
Authentication and authorization
Monitoring and logging
Secure coding practices
Vulnerability management
Documentation
Ultimately, as security teams are looking to remain compliant, choosing a solution that is robust in those categories is a must. Also, they should look for a solution that is highly interoperable with complementary solutions, like a web application firewall (WAF) or web application and API protection (WAAP) solution.
The more personal data your APIs contain, the sooner they will be regulated
Personal data is often a driving force for compliance across the globe. Of course, the Health Insurance Portability and Accountability Act (HIPAA) and the Health Information Technology for Economic and Clinical Health Act (HITECH) are great examples of this.
In this blog post, though, we’ll focus on the European Union (EU), where API standards are part of their General Data Protection Regulation (GDPR) requirements. GDPR is a broad set of data privacy requirements that apply to organizations that conduct business within the EU. It was enacted in 2018 to protect and regulate the processing of the personal data of EU citizens.
GDPR grants individuals specific rights over their own data and requires organizations to adhere to specific principles — or face significant fines. The ultimate goal is to safeguard privacy rights and hold organizations accountable for the collection, processing, and protection of personal data.
Although you won’t see APIs called out by name in the GDPR, your API security posture will heavily influence your compliance strategy. Here are three examples from GDPR that illustrate this point.
1. Article 25: Data protection by design and by default. This principle requires organizations to implement appropriate technical and organizational measures to ensure data protection throughout the lifecycle of their systems. APIs certainly fall under this umbrella given that they are often used to register users and access their personally identifiable information.
Therefore, foundational API protections like effective authentication, authorization, and encryption are a must. It could also be argued that proactive API vulnerability monitoring and threat detection are necessary measures for compliance.
2. Article 33: Notification of a personal data breach to the supervisory authority. Organizations must notify EU supervisory authorities within 72 hours of becoming aware of a personal data breach. Compliance with this requirement requires a detailed understanding how APIs are being used and a rapid detection of anomalies that may indicate a possible data breach.
Ideally, this will be supplemented by ongoing threat hunting activities to ensure that data breaches are avoided when possible and discovered quickly when they do occur. These detection efforts should also be combined with a robust response playbook that ensures that the data breach notification requirement can be met.
3. Article 35: Data protection impact assessment. Organizations must conduct formal assessments of high-risk data processing activities. The only way to conduct an assessment of this nature for API-accessible applications and datasets is by ensuring that you have a comprehensive inventory of your APIs and the ability to perform queries and analysis of API activity.
There are undoubtedly many other ways the GDPR requirements may affect your API security, but as these examples illustrate, some effort is required to map general requirements to specific attributes of your API implementation.
API regulations are both market-driven and government-driven
Market-driven regulations
Open banking regulations have appeared — and are under consideration — in many countries around the world. This has largely been driven by the finance sector, making open banking regulations a predominantly market-driven effort.
The purpose of these regulations is to promote competition and innovation in the financial services industry by allowing third-party providers to access customer data from banks and other financial institutions. While this is viewed as a net positive for the industry and consumers, it also creates new risks that must be managed.
APIs play an integral role in how open banking is implemented since they make it practical to exchange customer data in a secure and controlled manner. But the success of the model hinges on the use of effective API security practices. As a result, many open banking regulations include the adherence to specific security provisions.
Some countries are also taking a market-driven approach:
The United States is approaching open banking through industry collaborations like the no-profit Financial Data Exchange, a consortium of banks, fintech companies, and data aggregators
The Singapore government’s Monetary Authority of Singapore actively promotes open banking, providing detailed recommendations and guidelines, and collaborating with the private sector on initiatives like APIX, an open sandbox platform where financial firms can connect and collaborate
Government-driven regulations
An example of a government-driven effort is the Australian Cyber Security Centre (ACSC), which is a part of the Australian Signals Directorate (ASD), an intelligence agency responsible for signals intelligence and information security. The ACSC was established in 2014 to unify the government's cybersecurity efforts and provide a central point for collaboration between the private and public sectors.
ACSC’s Information Security Manual is a framework that “outline[s] a cyber security framework that an organisation can apply, using their risk management framework, to protect their systems and data from cyber threats.” Its latest Guidelines for Software Development framework includes a section specifically addressing APIs.
Several specific controls are prescribed for APIs, including:
Control: ISM-1817. Authentication and authorization of clients is performed when clients call web APIs that facilitate access to data not authorized for release into the public domain
Control: ISM-1818. Authentication and authorization of clients is performed when clients call web APIs that facilitate the modification of data
Control: ISM-1851. The OWASP API Security Top 10 are mitigated in the development of web APIs
Control: ISM-1910. Web API calls that facilitate modification of data, or access to data not authorized for release into the public domain, are centrally logged
In addition to these API-specific items, much of the broader guidance across areas such as data protection, application security, logging, and monitoring should also be applied to API-enabled applications.
The guidance given by the ACSC should not be surprising, as it overlaps with guidance found around the world. API security compliance is growing at a fast pace, and the best way to avoid confusion and complexity is to proactively seek out an API security solution. API security professionals will be aware of the regulatory landscape for their region and can help you be prepared.
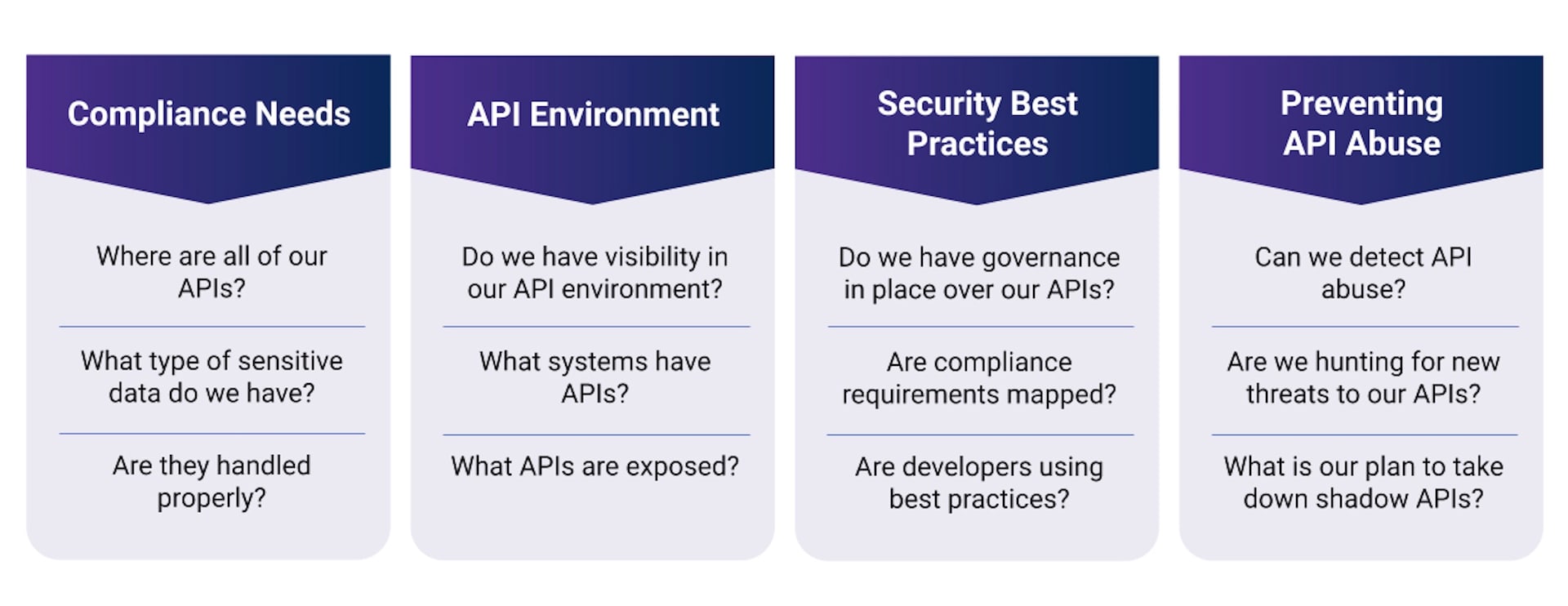
Questions to ask while developing an API security strategy
Security teams should talk to API security professionals about regulatory compliance and how their API security solution can help them remain compliant. Even if new regulations are introduced in their region post-implementation, the right solution will already provide a vast amount of data to document and enforce API regulations. The figure includes some key questions to ask.
Learn more
We’ve launched a monthly webinar series called If Your APIs Could Talk. Subscribing to this series is a great way to stay up-to-date on the latest API security trends.