Defend Against Account Abuse in Financial Services
Executive summary
In Q2 2024, Akamai helped a North American bank mitigate 12.7 million account abuse requests and 6.9 million bot requests by using sophisticated detection methods that analyzed user behavior to distinguish between genuine and malicious activities.
Threat actors used evolved techniques, including advanced artificial intelligence (AI) and machine learning, to mimic human behavior and evade traditional detection, necessitating a focus on analyzing legitimate user behavior.
Akamai Account Protector is a comprehensive security solution designed to prevent and defend against account takeover attacks and abuse both during and after login.
Introduction
Bot management is critical to any organization's security strategy. It is especially important when protecting against credential stuffing campaigns and preventing account takeover (ATO) of online accounts. Credential stuffing bots attempt to give hackers unauthorized access to user accounts by repeatedly entering stolen usernames and passwords into a website’s login fields.
Once a login is successful, the operator uses the valid login credentials to execute account takeover, drain stolen accounts of value, access sensitive data to steal credit card details and commit identity theft, send phishing messages, deliver malware, and more.
Credential stuffing and account takeover fraud can have devastating impacts for businesses as they can lead to mass data breaches that have financial consequences, tarnish customer trust, and harm brand reputation.
Protecting against account takeover attacks
Evasion techniques used by cybercriminals for these attacks have steadily progressed in recent years thanks to advances in both machine learning and AI. In addition to volumetric and low and slow bots, threat actors also use actual humans as a part of an attack.
Beyond this, bot operators are now capable of mimicking human behavior incredibly well, which makes it increasingly difficult to determine a valid request. While advanced bot detection tools are necessary, they are no longer sufficient. Organizations must now also focus on detecting legitimate users by analyzing their behavior to truly protect against account takeover attacks (or ATO attacks).
Case study: An attack on financial services
Consider the example observed by Akamai in April 2024 of a North American bank targeted by sophisticated threat actors. That attack combined both bot and account abuse activities to take over bank accounts, emphasizing the fact that advanced techniques are often being used in today’s campaigns.
The attack began by using bots to launch a low and slow attack that averaged 0.5 requests per second, and peaked at only 1.3 requests per second to avoid traditional rate-limiting defenses. As Akamai Bot Manager endpoint protection persistently detected behavioral anomalies and successfully blocked bot traffic, the fraudsters escalated their tactics. They manipulated the volume of malicious requests by refining their telemetry to create highly realistic simulations of human interactions.
Mimicking authentic user behavior
These simulations were so sophisticated that they mimicked authentic user behavior with remarkable accuracy. To further complicate detection efforts, the threat actors interspersed these simulated requests with genuine human login attempts, thereby making it increasingly challenging to distinguish between legitimate and malicious activities, such as account takeover fraud.
Detection and mitigation
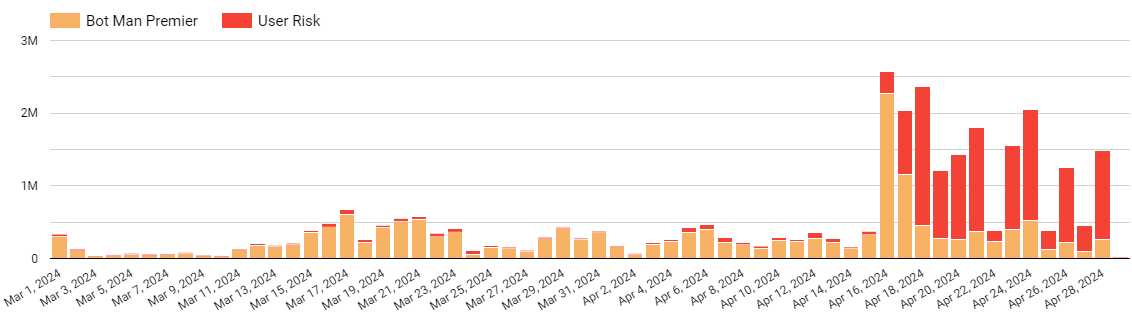
With Akamai Account Protector, the bank was able to not only detect and stop the suspicious bot activity, but also detect and mitigate the inauthentic user behavior that could have led to account takeover and other abuse. During the credential stuffing campaign, Account Protector's user risk and trust model effectively mitigated 12.7 million requests relating to account abuse activities, while its bot detection capabilities mitigated 6.9 million requests.
Figure 1 illustrates a high-level timeline of the mitigation efforts during this attack campaign. Threat actors attempted to evade detection by altering their telemetry and identities, and the timeline highlights these pivot points. The user risk mitigation, indicated in red, underscores the effectiveness of Account Protector’s mitigation strategies against these adapted account takeover attempts.
Account takeover attack forensics
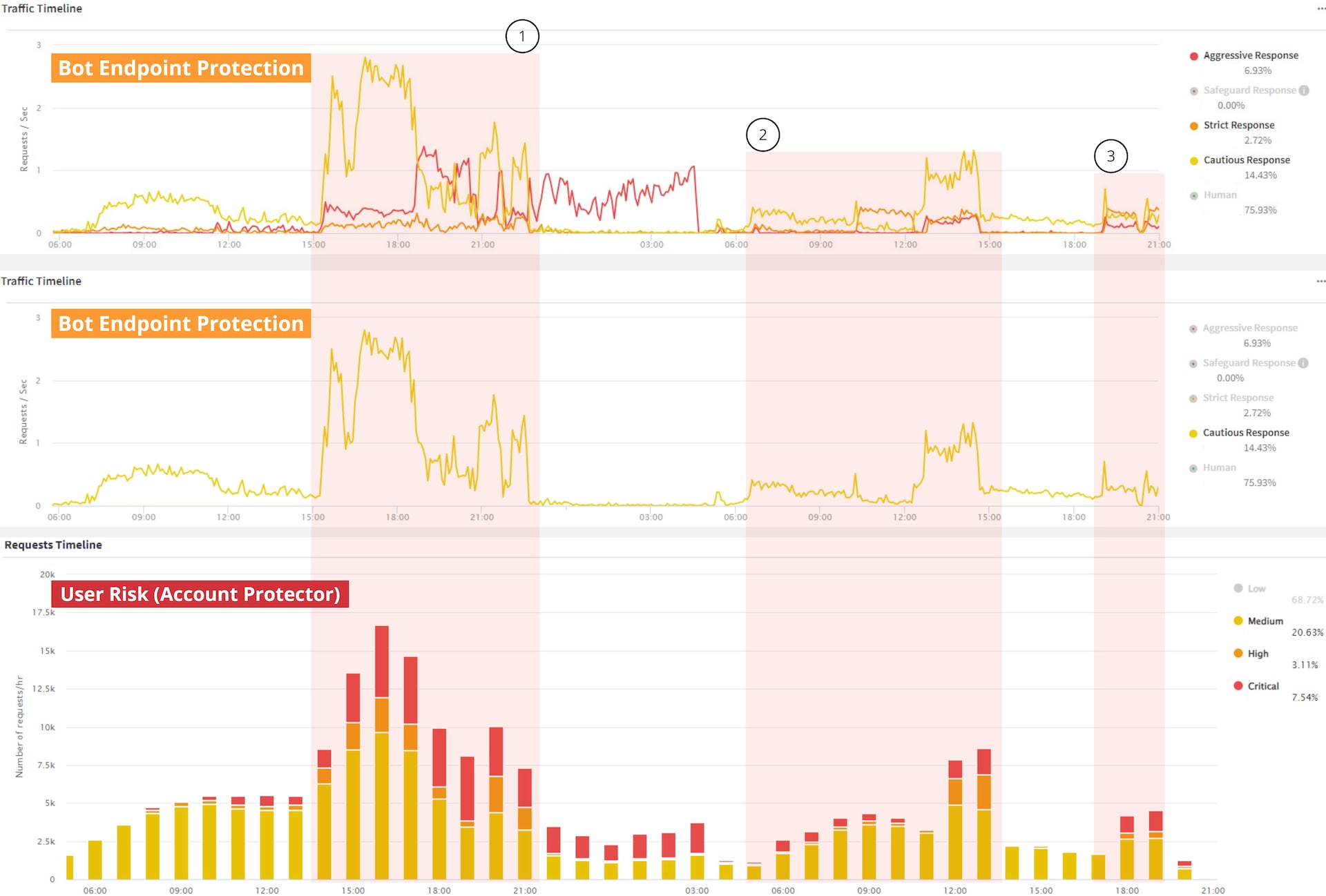
A thorough investigation by our security team into a 48-hour attack window revealed intricate details of the multiwave assault. This analysis showcased how the fraudsters repeatedly pivoted their strategies, attempting to outmaneuver our defenses and account takeover protection (Figure 2).
Despite these relentless efforts, our identity-aware approach maintained a high level of mitigation, effectively thwarting each account takeover attack wave and ensuring robust cybersecurity throughout all three waves of the attack.
First wave: Mitigated bot-like requests
During the initial wave of the attack, Akamai Bot Manager endpoint protection effectively mitigated requests characterized by strong bot-like behavior. These were categorized as "aggressive" (in red) and "strict" (in orange), as depicted in the top two parts of Figure 2. However, more subtle, humanlike requests, classified as "cautious" (in yellow), did not exhibit typical bot behaviors and required further evaluation.
This is where Account Protector's advanced account takeover protection capabilities came into play. By adopting an identity-aware approach, Account Protector considered a broader range of signals and indicators, which enabled the detection and mitigation of these sophisticated, human-mimicking attempts and ensured a more comprehensive analysis of each request's legitimacy.
Second wave: Detected and mitigated malicious traffic
Since the fraudsters were unable to bypass the robust mitigation efforts of Bot Manager and Account Protector, they resorted to sending even lower and slower requests in an attempt to stay under the radar.
Despite this subtler approach, both Bot Manager and Account Protector effectively detected and mitigated the malicious traffic to prevent compromised accounts. The solutions’ advanced capabilities ensured that even these stealthy attempts were identified and blocked, maintaining high detectability and mitigation performance.
Third wave: Delivered high-performing attack mitigation
In their final and most desperate attempt, the fraudsters pivoted their tactics once more to steal account credentials. They altered their telemetries, adopted even more virtual identities, and further reduced the volume and velocity of their malicious requests.
Despite these advanced maneuvers, their efforts proved futile. Akamai's account takeover protection defenses remained impenetrable, consistently delivering high performance in attack mitigation. Ultimately, the persistent failure forced the threat actors to abandon their attempt.
The importance of analyzing user behavior
The recent campaign on the North American bank highlights the importance of analyzing user behavior in real time to defend against today’s sophisticated account takeover attacks.
As a part of protecting against account abuse, it is critical to understand the actions of a user both during and after login by creating detailed profiles that include information such as:
Previous devices used
Common geographical locations
Typical networks and IP addresses
Normal activity patterns and times
Detecting deviations
Combining behavioral profiling with machine learning and AI helps detect deviations that may indicate a compromised account. For sophisticated ATO attacks, it is important that organizations implement tools that can identify subtle real-time changes in user behavior that may not be apparent through traditional bot detection methods.
For instance, if a user suddenly logs in from a new device, at an unusual time, or from an unexpected location, the solution can flag this activity for further investigation.
Detecting legitimate users
In addition, accurate detection of legitimate users helps reduce the incidence of false positives. When your protection understands normal user behavior, it’s less likely to mistakenly affect legitimate users. This ensures a smoother user experience and maintains customer trust.
Prevent and defend against account abuse and ATO attacks
Account Protector provides a comprehensive security solution designed to prevent and defend against ATO attacks and account abuse, both during and after account login. Using a variety of AI and machine learning models to analyze user behavior, it evaluates risk and trust through a user session to determine whether a user request is legitimate.
If suspicious or anomalous behavior is detected, Account Protector provides immediate mitigation options that still help to maintain a seamless user experience, such as blocking, serving alternate content, CAPTCHA, and more.
The solution also helps protect against sophisticated bots from the first interaction. It includes user behavior/telemetry analysis, browser fingerprinting, automated browser detection, HTTP anomaly detection, high request rate, and more.
Protect against account takeover fraud by ensuring user validity
In today’s landscape of sophisticated evasion attack techniques, ensuring the validity of a user to protect against account abuse and account takeover fraud is essential. By combining advanced bot detection and behavioral analysis, businesses can effectively mitigate threats while ensuring a frictionless user experience. Ultimately, this proactive approach helps maintain customer trust, uphold brand reputation, and protect revenue.