Major Enhancements to Akamai API Security, Q4 2024
The recent Akamai API Security updates 3.38, 3.39, and 3.40 introduce the abilities to block API threats using direct integration with Akamai App & API Protector, and to correlate runtime incidents with the underlying API vulnerabilities. It also includes improved logging for native connector configuration changes, and major enhancements to the user interface.
In addition, the API Security sensor and Remote Engine are now certified and available in the Red Hat Ecosystem Catalog.
Configurable blocking with Akamai native connector
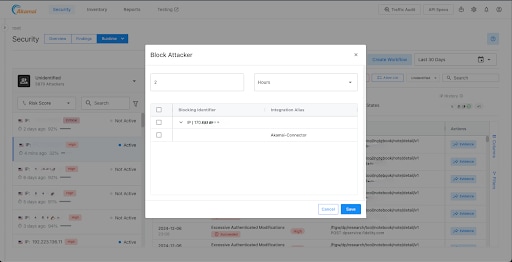
With the Akamai native connector, you can analyze Akamai traffic in API Security without deploying or installing additional components. You can now use the native connector to respond to identified API attacks by blocking specific IP addresses.
This blocking capability is supported by direct integration with the Akamai App & API Protector, allowing you to seamlessly use your Akamai web application firewall (WAF) to block active attack sessions.
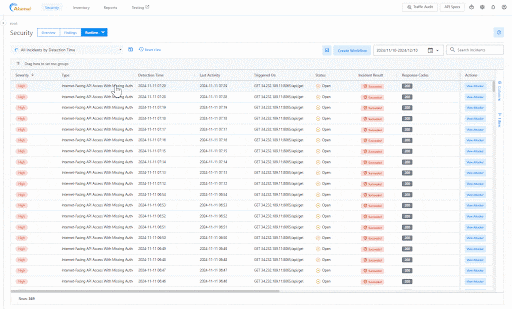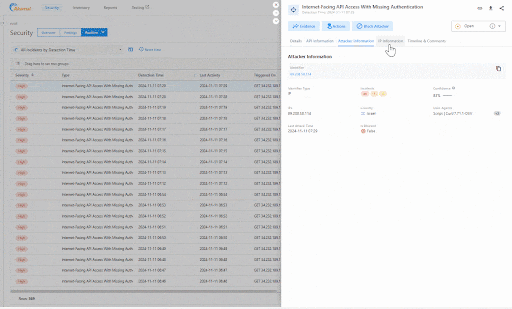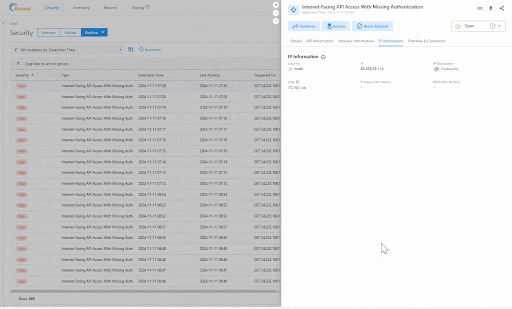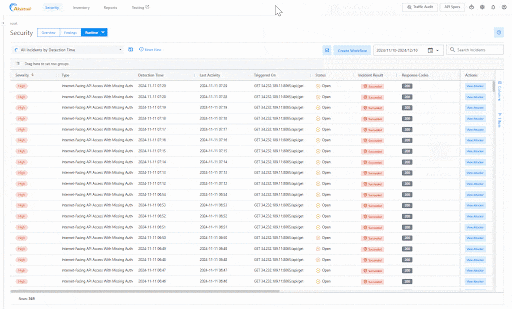
For further flexibility, you can add IP addresses to a "penalty box" to ensure protection from anomalous behavior without permanently blocking legitimate API clients (Figure 1). The penalty box duration is configurable, but IP addresses added to a permanent blocklist must be removed manually. Learn more about the Akamai native connector in the documentation.
Audit log for Akamai native connector
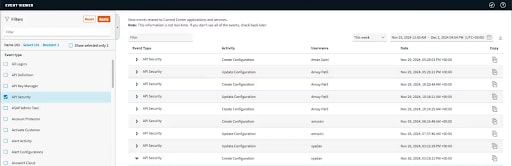
The audit log for the Akamai native connector is now available directly within the Akamai Control Center, which enhances transparency and simplifies compliance. The expanded logging capability for the Akamai native connector enables you to automatically record and view key actions and changes to the native connector configurations in the Control Center events viewer.
You can view all captured events and related details by filtering for API Security in the event viewer and selecting a relevant period (Figure 2). To learn more about this capability, please refer to the documentation.
Red Hat OpenShift certification
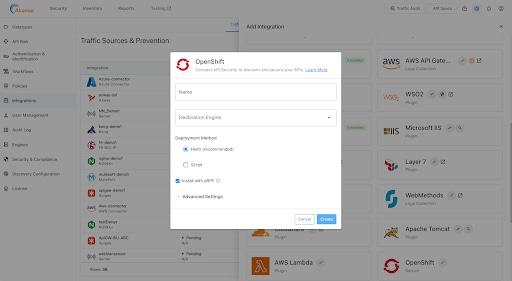
The API Security sensor and Remote Engine are now certified and available in the Red Hat Ecosystem Catalog. The API Security sensor is a lightweight eBPF-based component that captures traffic in real time and passes it to our remote engines for analysis.
With this release, our sensor and Remote Engine deployments are certified for Red Hat OpenShift environments to process API traffic data, which can help you identify API misconfigurations and runtime incidents (Figure 3).
This enhancement is especially beneficial for customers who work exclusively with Red Hat-certified vendors. They can now seamlessly analyze APIs directly within their OpenShift environments without transmitting sensitive data externally. This not only improves security but also simplifies compliance with data privacy regulations.
Automatic creation of posture findings from runtime incidents
Akamai API Security generates two types of issues for your APIs: posture findings and runtime incidents. Posture findings signify verified misconfigurations and vulnerabilities in your APIs that attackers could exploit. Runtime incidents signify attacks on your APIs resulting from misconfigurations.
With this update, API Security automatically generates posture findings based on confirmed runtime incidents. This feature enables you to block ongoing attacks using runtime incident remediation workflows while prioritizing the remediation of the underlying vulnerability or misconfiguration that allowed the attack to occur.
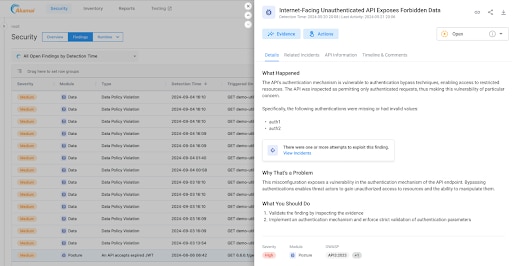
API Security also lets you correlate existing findings with new incidents. For example, you can now see incidents of APIs that are susceptible to authentication bypass, APIs that are accepting unsigned authentication tokens, and APIs that are vulnerable to permission spraying or stuffing directly from the correlated posture finding page (Figure 4).
Refer to the documentation to learn more about automated finding creation from your runtime incidents.
Enhanced user experience
This release brings you a complete redesign of the sidebar interfaces, along with improvements to the overall look and feel of the product, which simplify navigation across the platform and allow you to locate key information more efficiently. Our user experience redesign highlights include:
New icons. Sidebars for the API details pane, findings, and incidents now feature unique icons to facilitate easy identification.
Tabbed sidebar navigation. Sidebars now support tabbed navigation, which enables you to quickly locate relevant information without having to scroll through all the available content.
Redesigned Action button. We've updated the design and location of the main Action button to enhance functionality (Figure 5).
New Samples and Changes layout. The design and positioning of the Samples and Changes buttons have been updated for a cleaner appearance and easier access.
These updates are designed to create a more intuitive and efficient experience for our users. To learn more about the new user interface, please read the documentation.
Learn more
Please review the release notes for additional information about Akamai API Security updates 3.38, 3.39, and 3.40.