2021: Volumetric DDoS Attacks Rising Fast

In our 2020 DDoS retrospective, we highlighted the twists and turns of a very, very active threat landscape. As a quick refresher, we mitigated some of the largest attacks ever seen (1.44 Tbps and 809 Mpps); saw more attacks on customers across more diverse industries than ever before; and observed the largest DDoS extortion campaign, which impacted thousands of companies globally. So, it came as no surprise when 2021 threat actors continued to double down on DDoS.
Let's look at several key trending observations:
Attackers pick up the pace and raise the bar. In 2021 alone, we've already seen more attacks over 50 Gbps (as of 03/24/2021) than we saw in all of 2019. Keep in mind attacks of this scale can take almost anyone offline.
DDoS attacks are getting bolder and badder. Three of the six biggest volumetric DDoS attacks Akamai has ever recorded and mitigated have been in the past month, including the two largest known DDoS extortion attacks to date. The latest three attacks targeted an organization in Europe in the gambling industry and an organization in Asia in the video games industry.
Threat actors continue to expand their sights. The number of customer attacks per month has continued at near record volume, and we have continued to see diversification of attacks across geographies and industries. A recent analysis showed a 57% increase in the number of different customers attacked year over year.

Fig. 1: Top DDoS Gbps Recorded/Mitigated Attacks

Fig. 2: DDoS attacks and projections by year. Bars = DDoS attacks; red line = attacks over 50 Gbps.
The 2021 stats are projected based on current totals.
Apparently clinging to the hope of a major Bitcoin payout, criminal actors have started to ramp up their efforts and their attack bandwidth, which puts to rest any notion that DDoS extortion was old news.
The most recent extortion attack -- peaking at more than 800 Gbps and targeting a European gambling company -- was the biggest and most complex we've seen since the widespread return of extortion attacks that kicked off in mid-August 2020. Since the start of the campaign, show-of-force attacks have grown from 200+ Gbps in August to 500+ Gbps by mid-September, then ballooned to 800+ Gbps by February 2021.
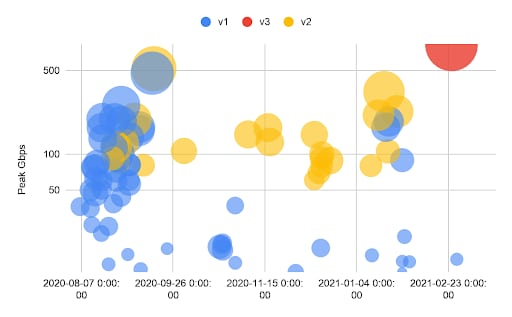
Fig. 3: Likely DDoS extortion attacks. Bubble size = Mpps; color = extortion attack profile.
But the size of the extortion attack wasn't the only notable characteristic of the actors' modus operandi. As reported by the Akamai Security Intelligence Response Team's threat advisory released March 23, 2021, the criminal actors used a previously unseen DDoS attack vector that leveraged a networking protocol known as protocol 33, or Datagram Congestion Control Protocol (DCCP). This attack is akin to a SYN flood in DCCP, but in this case is volumetric in nature. Threat actors abuse protocol 33 in an attempt to bypass defenses focused on traditional Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) traffic flows. The new DCCP DDoS attack vector is just the latest example of protocol abuse discoveries made by the Akamai SIRT.
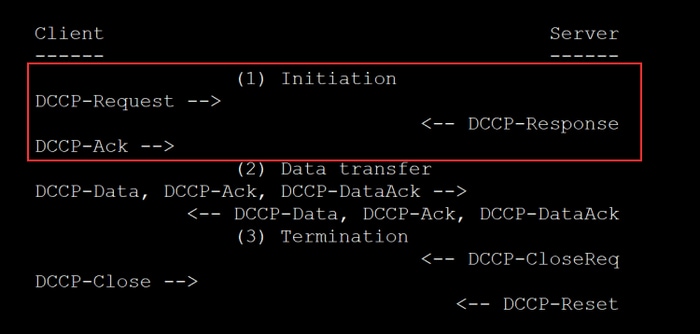
Fig. 4: DDCP flow diagram (New DDoS Attack Vector Discovered in DCCP Protocol. The Record.
The bottom line: Attackers are constantly probing for new and creative ways to launch DDoS attacks, and DCCP abuse is the latest example of such criminal pursuits.
In addition to the new DCCP attack vector described above, and also as part of a bigger trend, 2021 DDoS campaigns have become more targeted and much more persistent. Recently, we've witnessed several campaigns that targeted a range of IP addresses at two specific customers over an extended number of days. The attackers were relentlessly looking for weaknesses in defenses to exploit, as well as trying different attack vector combinations. In one attack, the threat actors targeted nearly a dozen IPs and rotated through multiple DDoS attack vectors trying to increase the likelihood of disrupting the back-end environments. In fact 65% of DDoS attacks launched against customers were multi-vector.
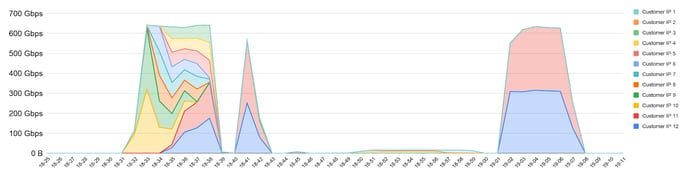
Fig. 5: Persistent DDoS campaign 1. Each color represents a different destination IP.
The attacker shifted from a number of destination IPs, eventually settling on two.
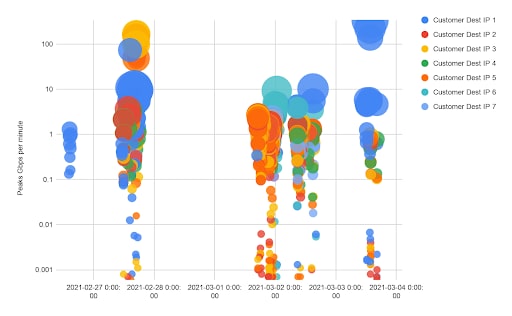
Fig. 6: Persistent DDoS campaign 2. Multiple targets at the same customer over a number of days.
It's clear from our attack trends and observations that 2021 will continue to be a year full of DDoS surprises, but that doesn't mean you can't be prepared. As we like to say, it's most important to "prepare during peacetime" so your organization isn't left to go it alone or scramble for defenses while under attack.
Looking ahead, our DDoS attack forecast continues to anticipate attack growth on four fronts:
number of DDoS attacks
number of large DDoS attacks (> 50 Gbps)
number of industries targeted with DDoS
number of organizations targeted with DDoS
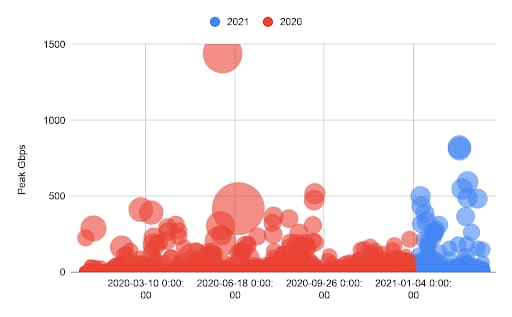
Fig. 7: DDos attacks 2020 to present. Bubble size = Mpps; color = year.
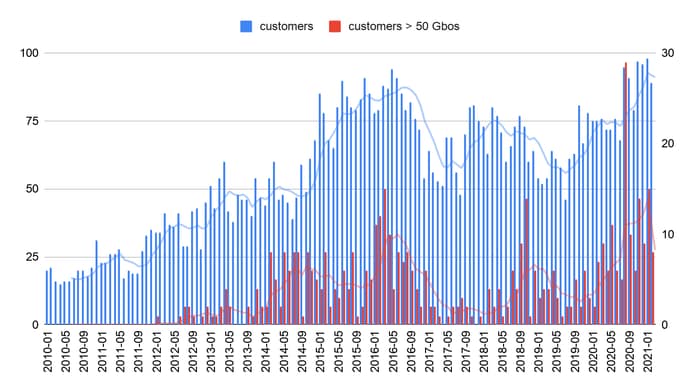
Fig. 8: Customers attack trends 2010 to present. Blue = total; red > 50 Gbps.
Based on what we witnessed in 2020 and in the first few months of 2021, do you have the right DDoS defenses in place to fight back?
If you are currently under DDoS attack or threat of extortion, reach out to the Akamai DDoS hotline, 1-877-425-2624, for immediate assistance.
For more technical details and additional DDoS-related resources, please see the following blog posts and materials:
- Akamai SIRT Threat Advisory
- DDoS Extortion Examination Unprecedented Levels of Ransom DDoS Extortion Attacks
- Ransom Demands Return: New DDoS Extortion Threats from Old Actors Targeting Finance and Retail
- 2020 Extortion Campaign: A Sequel More Thrilling Than the Original
- Don't Let DDoS Extortionists Deliver a KO Punch



