Beware the Rising Tide: Financial Services Is Awash in Attacks
The financial services industry is a cornerstone of the world economy, fueling growth and development. However, its critical importance makes it a prime target for threat actors. These threat actors include ransomware groups focused mainly on financially profiting (e.g., CL0P, LockBit) and hacktivists focused on disrupting financial institutions with possible political ties (e.g., BlackCat [ALPHV], REvil). The impact of their attacks can be far-reaching and may undermine trust in the global financial system.
Given these realities, we’re seeing a rising tide of attacks on the financial services sector — from banks and payment processors to investment firms and financial technology (fintech) companies.
We describe this threat landscape — and explore what financial services organizations can do to protect themselves — in a new State of the Internet (SOTI) report, Navigating the Rising Tide: Attack Trends in Financial Services. Some key findings from the report include:
Financial services was the most frequently targeted industry by Layers 3 and 4 distributed denial-of-service (DDoS) attacks. Geopolitical tensions, such as the Israel-Hamas and Russia-Ukraine wars, have driven a surge in hacktivist activities.
The growing use of digital services and APIs, particularly undocumented shadow APIs, has expanded the attack surface, making financial institutions more vulnerable to Layer 7 DDoS attacks.
The financial services industry is a top target for phishing and brand impersonation schemes. Phishing websites account for 68% of suspicious domains that impersonate financial institutions, leading to a rise in identity theft and account abuse.
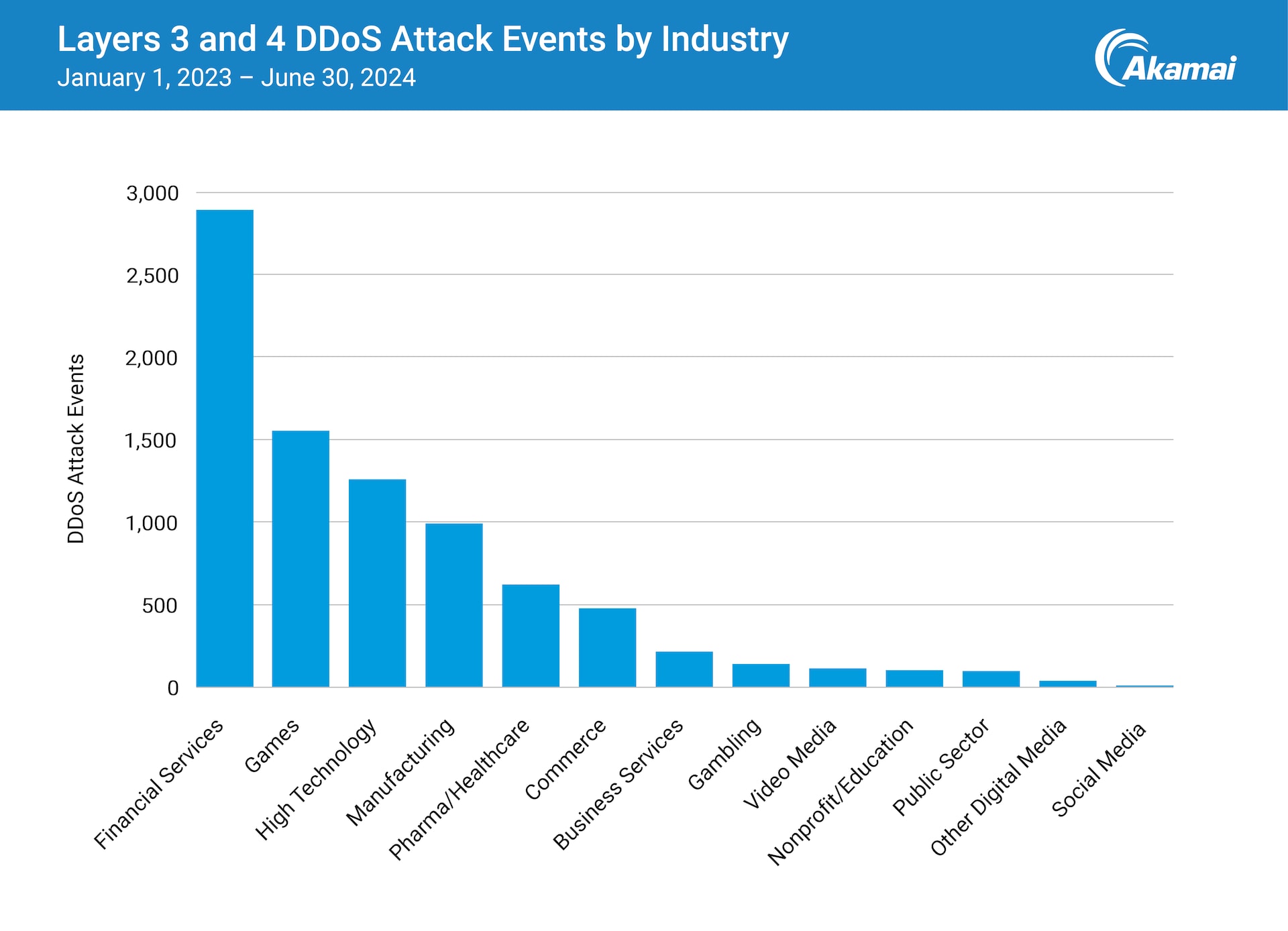
Leading target for DDoS attacks
For the second consecutive year, the financial services industry has a towering lead over other industries in the number of DDoS attacks targeting Layer 3 and Layer 4 (network and transport layers; Figure 1).
Geopolitical tensions and the resulting hacktivist activities have played a major role in the DDoS surge. For example, there is a concentration of attacks aimed at European banks with links to Ukraine, presumably launched by pro-Russian threat actors.
There has also been a recent outbreak of DDoS hacktivism among financial institutions in the Middle East, as well as an increase in Layer 7 DDoS attacks. Another factor driving the increase is the technological advancements that dramatically increase the capabilities of DDoS attackers, including virtual machine (VM) botnets.
In addition, the attack surface is expanding due to the increasing use of digital services and APIs, which present more potential vulnerabilities for attackers to exploit. A key concern is undocumented shadow APIs that often lack proper protection. Financial service institutions are also deploying APIs to meet evolving compliance and regulatory requirements, which further complicates the task of protecting these potential entry points.
Frequency does not always equal intensity
Our research into DDoS attacks in financial services reveals a critical insight: Event frequency doesn't always correlate with attack intensity. Although some months show few attacks, the corresponding Gbps data indicates significant traffic spikes, emphasizing the need to consider both attack frequency and volume when assessing DDoS attacks.
Brand abuse and brand impersonation
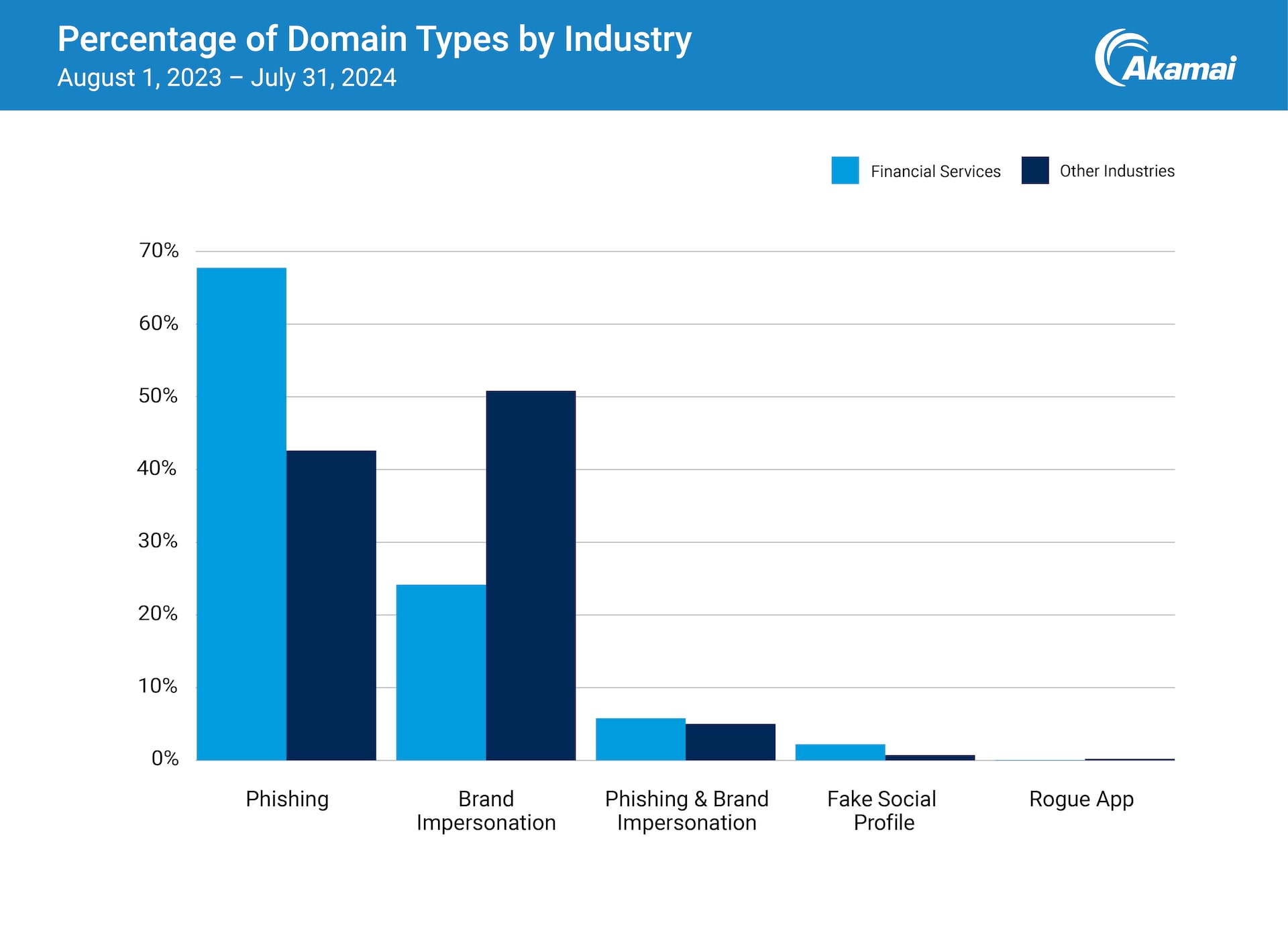
The financial services industry is seeing an increase in brand abuse, such as phishing and impersonation schemes that aim to exploit the trust between financial institutions and their customers. Our research revealed that a startling 30% of page visits are directed to phishing and brand impersonation sites. Financial services was the most impersonated industry, based on the number of suspicious sites monitored by Akamai.
The emergence of phishing as a service platforms and toolkits have lowered the barrier to entry for cybercriminals, increasing the scale and magnitude of phishing attacks against financial services and their customers. In fact, 68% of identified phishing pages from August 2023 through July 2024 targeted financial institutions and their customers (Figure 2).
Brand abuse can lead to a variety of criminal acts, including identity theft and account abuse. Organizations can suffer substantial financial losses due to reputational damages, compliance and legal issues, and even lost sales due to counterfeit products. The alarming number of fraudulent websites that mimic legitimate financial institutions and the rapid pace at which attackers create new domains after their original sites are taken offline are especially concerning.
Compliance and resilience
The SOTI report includes a guest column by Teresa Walsh, Global Head of Intelligence for the Financial Services Information Sharing and Analysis Center (FS-ISAC), that highlights the need for enhanced compliance and operational resilience in the face of today’s threats. New regulations, such as the Digital Operational Resilience Act (DORA), and updated SEC guidelines amplify the need for a holistic approach to cybersecurity in financial services. This involves identifying and prioritizing material risks, incorporating the outcome into the organization’s risk management frameworks, and ensuring robust incident response plans are in place.
Walsh notes that a proactive stance is vital to ensure operational resilience and maintain customer trust in an increasingly volatile threat landscape.
Fighting the tide
A multifaceted approach is essential to protect your financial institution from growing cyberthreats. The SOTI report reviews some practical tips for reducing the risks posed by phishing and brand impersonation, DDoS attacks, and ransomware.
The report also highlights the importance of implementing a Zero Trust framework to maintain a resilient security posture. This approach operates on the principle that any connection request, user, or device is a potential threat. By eliminating implicit trust and enforcing continuous verification, access to resources is denied by default unless authenticated and authorized. Additionally, Zero Trust prevents lateral movement within the infrastructure through segmentation and microsegmentation, reducing the potential “blast radius” of an attack to protect sensitive data.
Understanding the threat is the first step
The drive to digitize customer interactions will only increase in the financial services industry — and so will the cyberthreats that seek to exploit these interactions. Implementing effective mitigation strategies is crucial not only for protecting your institution and its customers but also for ensuring regulatory compliance. Fully understanding the nature and scope of the threat is an essential step in navigating the rising tide of cyberthreats.
Learn more
Get the full story: Download the new State of the Internet (SOTI) Report, Navigating the Rising Tide: Attack Trends in Financial Services.