Learning from the LockBit Takedown
An international law-enforcement task force composed of agencies from 10 countries (including Australia and Japan) has announced the successful takedown of the LockBit ransomware gang.
Operation Cronos, led by UK and US authorities, seized the darknet sites run by LockBit, the infamous and prolific ransomware group that claimed more than 2,000 victims worldwide and extorted more than US$120 million in ransom payments.
At the February 24, 2024, press conference announcing the takedown of the LockBit gang, Federal Bureau of Investigation (FBI) Cyber Deputy Assistant Director Brett Leatherman shared that “a joint sequenced operation among 10 countries disrupted LockBit's front- and back-end infrastructure in the U.S. and abroad.” Details of the takedown were announced at the FBI briefing about the disruption and dismantling of the LockBit gang.
This is an updating report and we’ll add more information to it as our research progresses — stay tuned!
The takedown details
At 4:00 PM ET on February 19, 2024, the authorities took action to disrupt and dismantle the LockBit ransomware-as-a-service (RaaS) infrastructure, seize funds, and arrest two individuals. The authorities placed a seizure notice on the LockBit site.
Operation Cronos seized more than 11,000 domains and 34 servers.
More than 14,000 rogue accounts responsible for exfiltration and 34 servers in the Netherlands, Germany, Finland, France, Switzerland, Australia, the United States, and the United Kingdom have been closed.
At 6:30PM ET, the seizure notice was replaced by a site detailing the activities of Operation Cronos.
The Department of Justice charged a total of five LockBit affiliates and issued three arrest warrants.
Two LockBit actors have been arrested in Poland and Ukraine.
All StealBit servers used by the LockBit StealBit data exfiltration tool have been taken offline.
All accounts affiliated with LockBit 3.0 are known to authorities.
More than 200 cryptocurrency accounts have been frozen.
US sanctions have been published.
Approximately 1,000 potential decryption keys have been seized by the FBI, the U.K. National Crime Agency’s (NCA) Cyber Division, and Europol who are working to engage with 1,600+ known US victims via the IC3 website.
- Victims in the United States are encouraged to reach out to your local FBI office or fill out the form on lockbitvictims.ic3.gov.
The impact of Operation Cronos
The operation was named Cronos (Greek for “time”) as a reference to the hourly countdown that led to the announcement of LockBit’s takedown. The impact of Operation Cronos is truly unprecedented and the scope and scale of this takedown has ushered a new era for cyber law enforcement. Never before have authorities been able to take complete control of a major ransomware gang’s infrastructure and operations.
The entire command and control infrastructure of LockBit is now under the control of the authorities (Figure 1). A vast amount of data detailing LockBit and its affiliates is in the possession of the authorities and will be used for further investigations and actions.
This takedown was not simply a leak of some files and operational documents of a ransomware group (such as Conti), but the systemic disruption and dismantling of the largest and most prolific RaaS group and its affiliates while operational (Figure 2).
 Fig. 2: The announcement of the systemic disruption of the largest and most prolific RaaS group and its affiliates
Fig. 2: The announcement of the systemic disruption of the largest and most prolific RaaS group and its affiliates
Since its emergence, LockBit has been the most deployed ransomware variant in the world. For four years, the LockBit gang sowed fear among enterprises and governments worldwide and contributed to a significant share of ransomware attacks. An Akamai research report from 2023 highlights that LockBit influenced the ransomware scene with 39% of the total ransomware victims (1,091 victims) — more than triple the number of the second-highest ranked ransomware gang.
Since January 2020, LockBit has been responsible for hundreds of attacks worldwide. In the Asia-Pacific region, it targeted organizations across financial services, critical infrastructure, agriculture, education, and government. LockBit also recruited minimally skilled attackers as affiliates, which amplified the scale, reach, and damage caused by their signature ransomware attacks. LockBit leaked the sensitive data of the organizations that refused to pay the ransom to coerce payment.
A brief timeline of the evolution of the LockBit malware
LockBit 1.0 was released in January 2020 as ABCD ransomware.
Lockbit 2.0 (aka LockBit Red) was released in June 2021 with StealBit, a data exfiltration tool to perform ransomware operations. The gang and its affiliates would drop this ransomware in compromised environments.
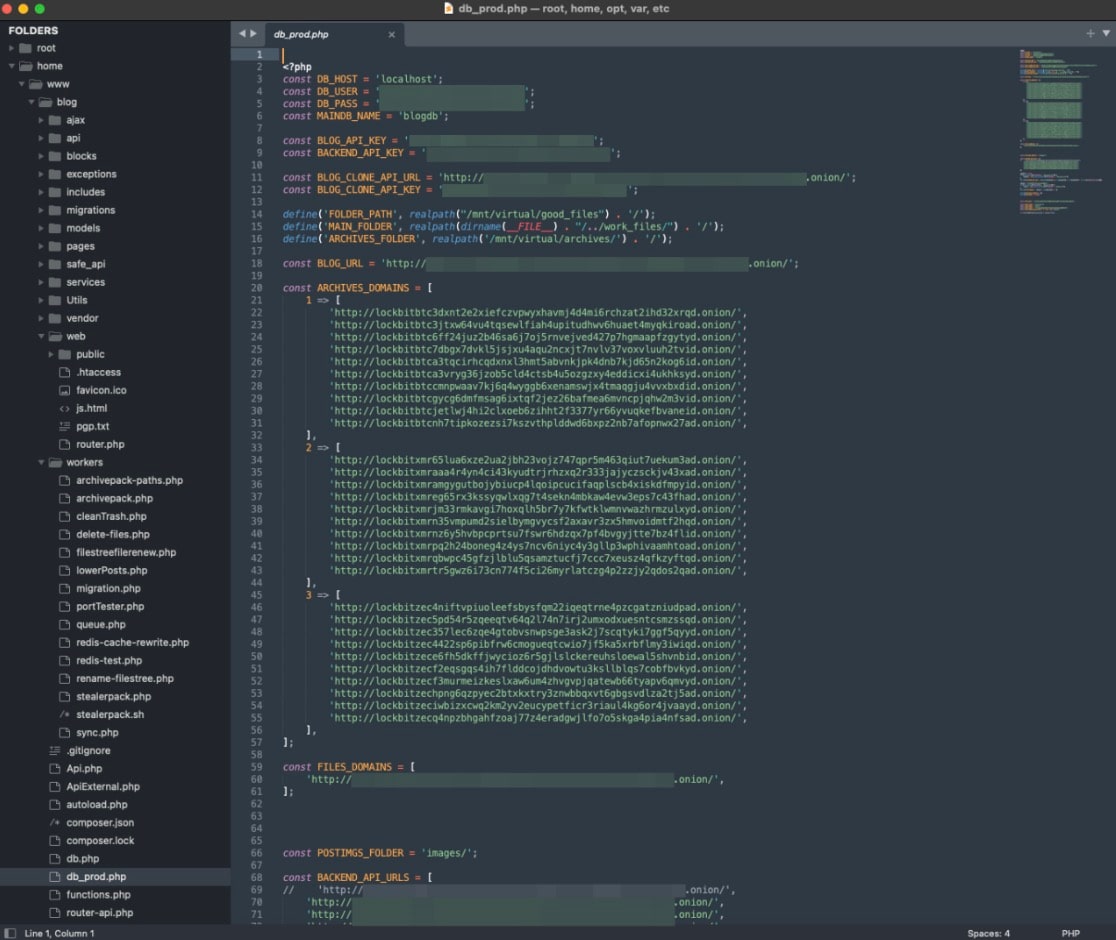
LockBit Linux was released in October 2021 as a Linux encryptor targeting the popular VMware vSphere platform and the ESXi virtualization platform (Figure 3).
LockBit 3.0 (aka LockBit Black) was released in March 2022 to exfiltrate sensitive company data files before encryption by using StealBit and rclone exfiltration tools, which LockBit commonly used, as a public file-sharing service.
- Lockbit Green was reported by vx-underground and released in January 2023. It is ransomware based on the leaked code of the Conti encryptor and designed to target cloud services. It uses BCryptGenRandom for faster encryption. As with other variants, files are encrypted until a ransom is paid or data leaked for double extortion.
 Fig. 3: Snapshot of the LockBit Linux encryptor
Fig. 3: Snapshot of the LockBit Linux encryptor
Who is LockBitSupp?
The operation was not without its drama. LockBit’s infamous leader, LockBitSupp, trolled Operation Cronos and complained about the lack of bounty on his head. He even offered a US$10 million bounty on himself to unmask his identity (Figure 4). As of this publication, LockBitSupp’s true identity remains a mystery.
 Fig. 4: The US$10 million question
Fig. 4: The US$10 million question
Sending a message to ransomware gangs
After years of being trolled and outmaneuvered by LockBit and other ransomware gangs, the authorities have finally turned the tables by taking a page out of the LockBit gang's media savviness book with a coordinated media campaign (Figure 5). The darknet sites that were leaking customer data are now sharing the decryptor keys for those who stood against extortion and refused to pay the ransom. The Japanese Police, supported by Europol, developed a decryption tool designed to recover files encrypted by LockBit 3.0 Black.
Authorities intended to send a clear message to all ransomware gangs that they can no longer hide behind The Onion Router (Tor) to evade surveillance in the dark web and that they will be held accountable for their actions.
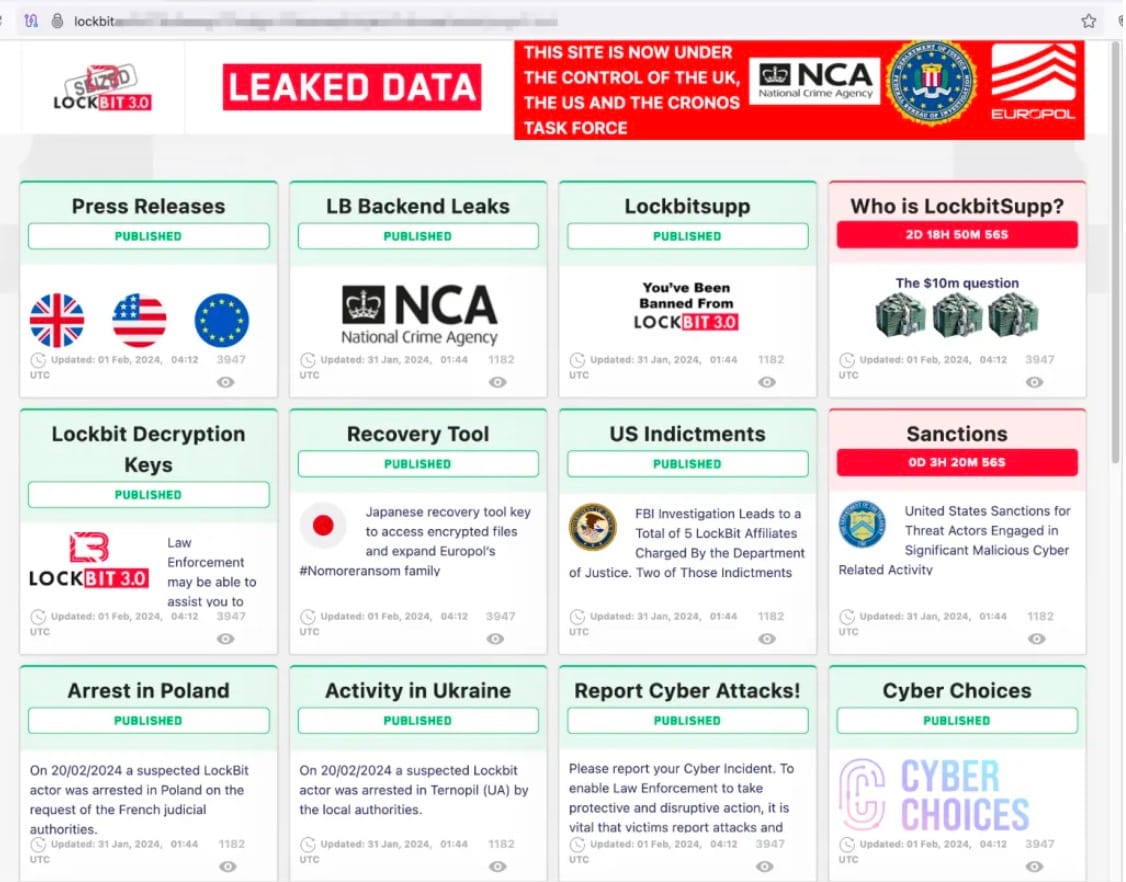 Fig. 5: The authorities’ takedown site
Fig. 5: The authorities’ takedown site
Prevention is better than recovery
This was a bold takedown realized by the collaboration of authorities across many countries. However, relying on multinational task forces to take down ransomware gangs and recover decryptor keys is not an effective security strategy. Prevention is better than recovery.
Ransomware gangs are nimble and a variant of the LockBit gang could fill the newly created void and take over with even more damaging tools. The ransomware gangs are learning and will adapt to avoid the tools and techniques used by the authorities. Additionally they have still have a number of attacks that they completed they will try to monetize.
Let’s keep in mind the attempted takedown of another prolific ransomware group, BlackCat/ALPHV, which “UNSEIZED” their dark website hours after it was seized by the FBI: They posted the image of a black cat and a banner declaring "THIS WEBSITE HAS BEEN UNSEIZED." The gang is still at large and the U.S. State Department is offering up to a US$10million bounty for information on the group's leaders.
5 steps to preventing a LockBit attack
Organizations should reassess the state of their security postures today. It's time to shut down ransomware by implementing a security solution at each point of the ransomware kill chain (Figure 6).
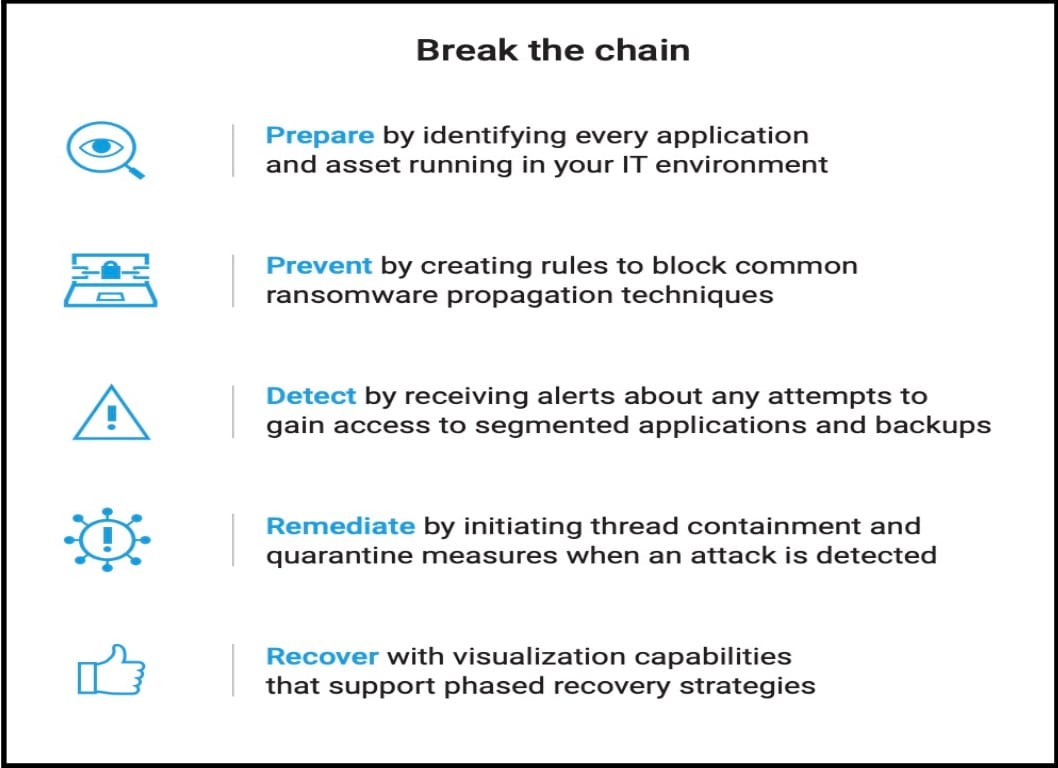 Fig. 6: The ransomware kill chain
Fig. 6: The ransomware kill chain
Prepare
There are five key elements in an effective security strategy. The first step is to prepare by identifying every asset and application in your IT environment.
Prevent
Then, you must prevent attackers from accessing and encrypting the data on critical servers — and have backups in the event that attackers are able to breach an environment. You can minimize the impact of any potential access through segmentation. Implementing a Zero Trust architecture, starting with software-defined microsegmentation to prevent lateral movement after ransomware infection, is critical.
Detect and remediate
Full network visibility to identify indicators of compromise (IOCs) will enable the third and fourth steps: detection and remediation before malware can have a larger impact. Visibility also helps guide compliance with local cybersecurity regulations.
Recover
Finally, it is essential to have a thorough understanding of attack surfaces, along with strong processes and playbooks to prevent and recover from ransomware attacks.
Learn more
See how Akamai can help you break the chain by downloading the ebook now.