dhpcd: The Cryptominer That Hid for Four Years
Executive summary
Akamai Security Intelligence Group observed a long-running attack campaign, which we’ve dubbed “dhpcd.” The campaign targets Linux machines with SSH servers by brute forcing passwords and eventually runs a Monero cryptominer on those machines.
The campaign was first identified by Akamai’s threat sensors network in April 2018, and it still remains active today.
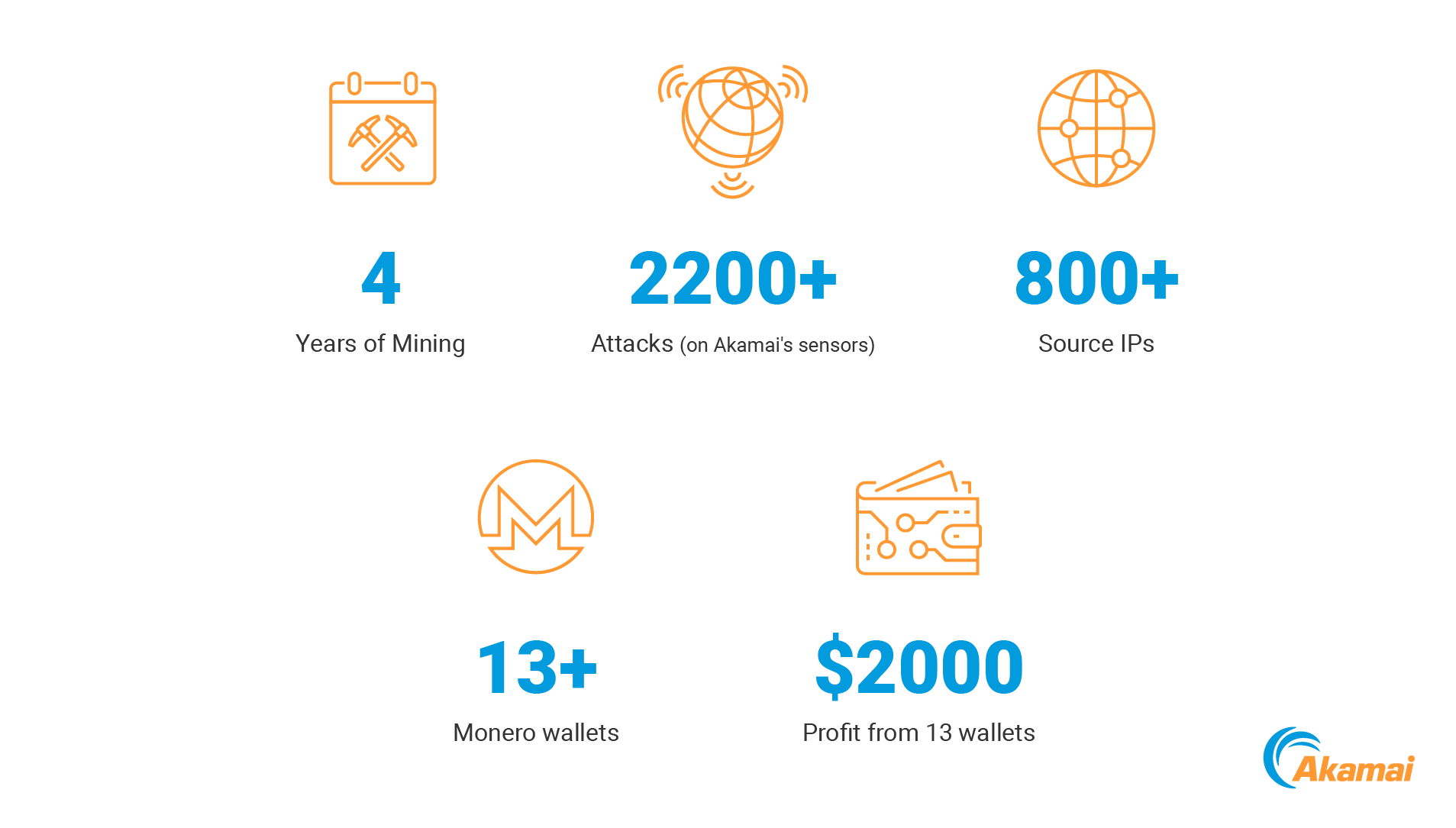
We have observed more than 2,200 attacks from over 800 unique source IPs on our threat sensors network since the first appearance, with a distinguishable peak in May 2022.
As part of the attack chain, the attackers deploy multiple backdoors using password changes and adding an SSH key, execute numerous scripts to neutralize competitors, and use cron jobs and the rc.local file for persistence.
Some of the cryptominer binary files are unfamiliar to other security vendors.
The origins of the attackers' infrastructure are unknown as they operate behind Tor exit nodes. Some of those Tor exit nodes belong to universities, nonprofit organizations, cybersecurity companies, and so forth.
The partial list of indicators of compromise (IOCs) is available in the appendix; a full list of IOCs and a detection script are available in our public repository.
What is dhpcd?
Because so much of the internet runs on Akamai’s infrastructure, we have an expansive view of what goes on, and finding new (or new-ish) malware is one of the results of this wide-ranging view. In April 2018, the cryptominer based off the open source XMRig, which we have named “dhpcd,” hit Akamai’s threat sensors for the first time and have remained active ever since. It’s not often we come across malware that has been flagged and is still running for that long with relative consistency that hasn’t been discussed. This is because this cryptominer brute forces in, hides, and pulls reconnaissance for things that would detect it.
The name comes from a difficult-to-detect play on the legitimate Linux daemon dhcpd: a process in charge of configuring the DHCP server running on the machine when it starts. This technique of letter swapping is heavily used for multiple attack vectors to evade detection, which was part of this malware’s success in remaining active for at least four years. It uses Tor exit nodes to hide, which makes it difficult, if not impossible, to track the attack origins. It then mines the privacy coin Monero. We were able to obtain the Monero wallets from the cryptominer binary files.
It has gone through a few variations, which has contributed to its success in evading detection, not only locally on the infected machine, but also with security vendors and various threat intel feeds. In this blog post, we will explore the attack flow, mitigation, and the impact of the various deployments.
Incident activity
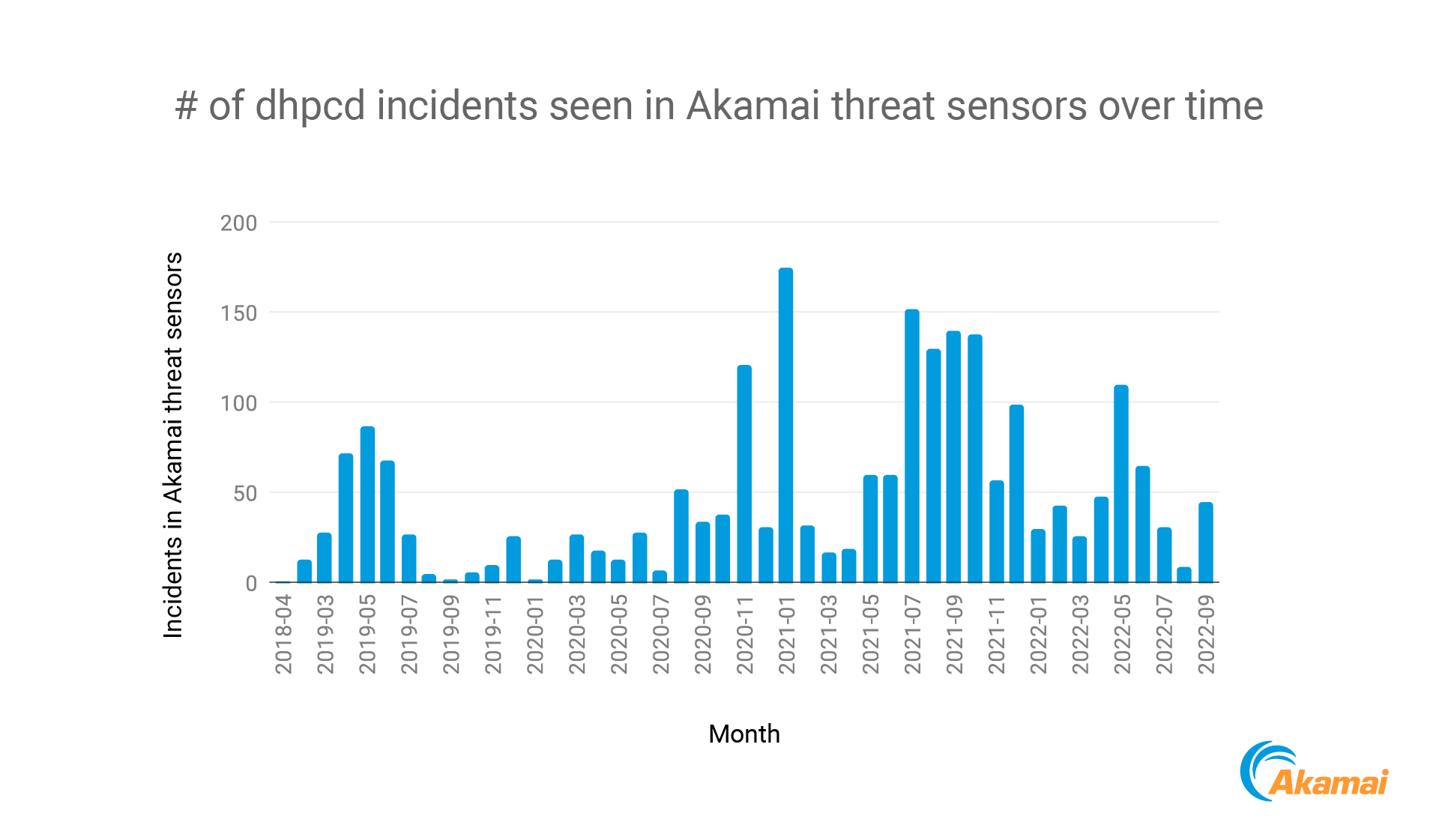
Since April 2018, our sensors have recorded over 2,200 incidents from more than 800 unique IP addresses. These IP addresses primarily belonged to hosting and communications companies. However, there were also a significant number of IPs from universities and nonprofit organizations, which in effect, became the infrastructure to further the malware’s intended purpose.
In March 2022, we noticed a major version update of XMRig, the cryptominer on which dhpcd is based, from version 2.13.0 to 5.2.0. In tandem with this significant version update, we observed a large uptick in both scale and scope. Shortly after this, in May 2022, we observed the highest peak of the year thus far. Although it wasn’t as high as the 2021 peak, this illustrates the attackers’ desire to level up the potential gains from this particular malware in the future. It stands to reason we will be seeing more examples of this in the coming months.
Campaign scope
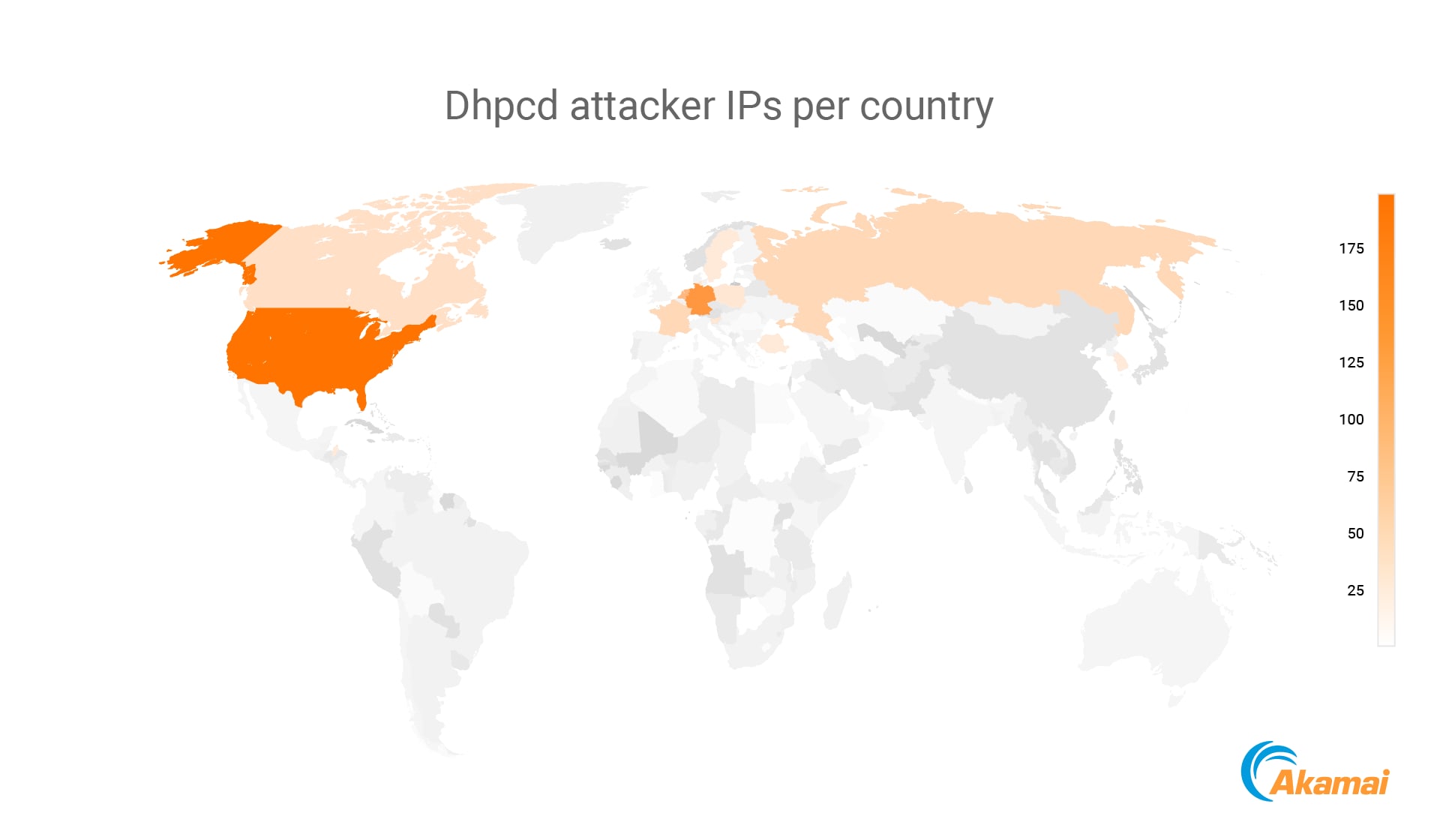
Since our first detection of dhpcd, we’ve had 2,215 attacks, spread over 843 different attacker IPs, averaging 2.6 attacks per IP. For each source IP, we observed a range of 1 to 27 attacks.
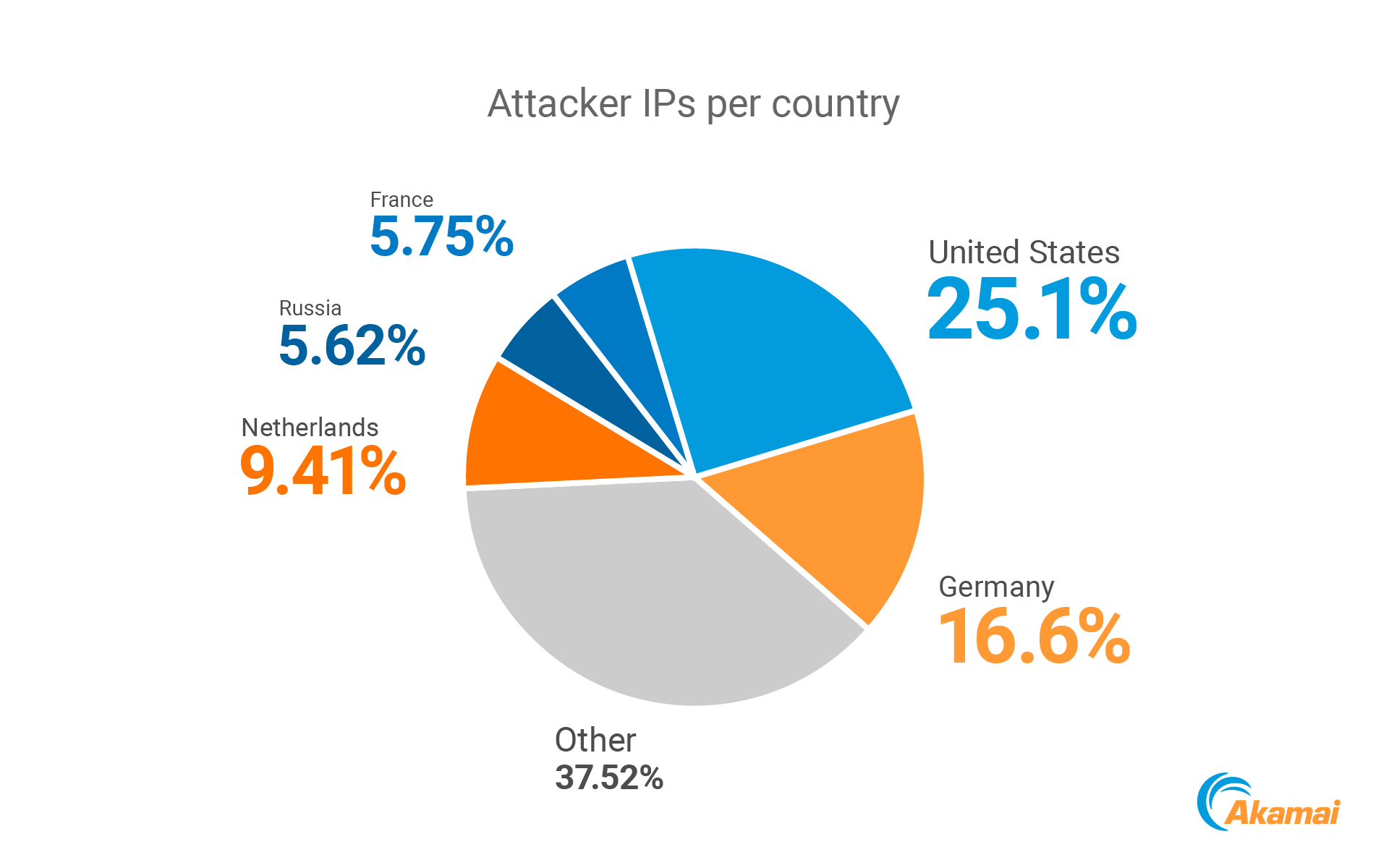
Of the 840 attacker IPs, approximately 80% were Tor exit nodes, making it nearly impossible to trace the threat actor behind the attack. Using Tor is an OPSEC best practice, on the attackers’ side; however, it means that organizations that use Tor take an active part of dhpcd’s (and other campaigns’) propagation and malware distribution. Among the organizations we saw attacking Akamai’s sensors were machines belonging to U.S. universities, European nonprofit organizations, and others.
Based on the number of Tor exit nodes in these countries, most of the attacker IPs are located in the United States and Europe. Most of the European attacks came from Germany and the Netherlands.
Finance
The attackers use multiple wallets to collect their cryptomining profits. We found 13 unique Monero wallets hard-coded into the cryptominer binary files. In the process of monitoring these wallets, we found that each one contains an amount equivalent to $150—$160; after gaining this amount, the attackers probably “rotate” to another wallet. Considering this relatively low amount of balance that each wallet holds, we assume that the actual number of wallets is significantly higher. These low amounts are another example of this malware’s OPSEC: taking and keeping small amounts to reduce the chance of being noticed.
The total profits we’ve calculated so far are approximately 85 mBTC, which is equivalent to about $2,000. But again, we assume there are more wallets in malware files we did not obtain, thus the actual gain is likely significantly higher.
The attackers mined Monero coins (XMR) using the mining pool domains of minexmr[.]com, such as: sg97[.]minexmr[.]com, fr13[.]minexmr[.]com, us40[.]minexmr[.]com, etc. The full list is provided in our IOC repository.
On August 19, these mining pools were closed and the attackers had to find another pool to use, so the current mining pool is pool[.]supportxmr[.]com:80.
Attack flow

Initial breach
The attackers breach the target Linux machines running SSH servers by brute forcing passwords. Then, they download a dummy executable file to the bin folder using SCP. The dummy program simply writes “Hello, World” to the console – presumably to verify execution permissions. The file names are random alphanumeric strings of 26 characters; for example, /bin/cpuufcdmorv9crpa8h6wgh6iq2.
Cryptominer
The attackers then downloads the cryptominer — a file named “dhpcd” — to the same directory over SCP. The miner searches for available mining pool servers over TCP port 4444:
fr14[.]minexmr[.]com
ca61[.]minexmr[.]com
sg97[.]minexmr[.]com
fr13[.]minexmr[.]com
us40[.]minexmr[.]com
Persistence
The attackers can now take care of making the cryptominer persistent. They use several techniques to achieve this.
They start by changing passwords for existing users on the system, such as root, admin, test, oracle, test1, ubuntu, and more. They protect their changes by modifying the attributes of /etc/shadow, a file that holds the hashed passwords in the system as well as their metadata.
The attackers add their SSH key to ~/.ssh/authorized_keys file, and turn it immutable.
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCuhPmv3xdhU7JbMoc/ecBTDxiGqFNKbe564p4aNT6JbYWjNwZ5z6E4iQQDQ0bEp7uBtB0aut0apqDF/SL7pN5ybh2X44aCwDaSEB6bJuJi0yMkZwIvenmtCA1LMAr2XifvGS/Ulac7Qh5vFzfw562cWC+IOI+LyQZAcPgr+CXphJhm8QQ+O454ItXurQX6oPlA2rNfF36fnxYss1ZvUYC80wWTi9k2+/XR3IoQXZHKCFsJiwyKO2CY+j
The attackers use cron — a job scheduler that sets commands and tasks to run periodically — to run the cryptominer every hour. As another living-off-the-land persistence tool, they download an /etc/rc.local script file that launches the cryptominer with every system boot:
/bin/dhpcd -o ca.minexmr.com:4444 -B >/dev/null 2>/dev/null exit 0
Neutralizing competitors' activity
The attackers put effort in terminating other threat actors’ activity to maximize the machines resources, and consequently, maximize profits. For this purpose, they execute two scripts from the /dev/shm directory — /dev/shm/knrm and /dev/shm/r — but not before they verify execution permissions from this directory (again using the “Hello, World” program).
The /dev/shm folder is a tmpfs file system; it keeps all of its files in virtual memory instead of on a persistent storage device. By saving and running scripts from /dev/shm, the malware leaves no traces of these files on the file system.
The Bash scripts eliminate competition thoroughly, and we’ll use /dev/shm/r to demonstrate how. The script starts by querying the top resource-consuming processes running on the system and terminates those that take up a lot of RAM to ensure more memory is available for its own activity. Then, it deletes cron files that are associated with other attack campaigns, such as XorDdos, Tsunami, and aliyun.one.
/etc/cron.hourly/gcc.sh
/etc/cron.hourly/cron.sh
/etc/cron.hourly/gcc4.sh/lib/libudev.so
The script deletes files associated with the previously mentioned (and other) malware campaigns.
/root/pty
/tmp/bash
/dev/shm/bash
/var/tmp/bash
/var/lock/bash
/var/run/bash
/bin/httpsd
/lib/udev/udev
/lib/udev/debug
/root/sysem
/root/systma
/etc/jourxlv
/tmp/sysem
/tmp/su
'/tmp/ddgs.*'
/root/pty10
/root/pty4
/root/xmr64
/usr/local/sbin/t
/usr/local/sbin/rsync
/etc/ceurnad
Additionally, it kills malware-related processes, such as Xm64, Ceurnad, /tmp/samba, and Sc64u, if those are running.
To collect information on new or unknown competitors, the script runs the command atq to display the list of pending jobs, as well as the files in various system directories. After filtering out known file patterns (dump, docker, mount, etc.), the attacker is left with a list of files that are potentially rival malware.
Detection and mitigation
The use of SSH servers is very common. Also unfortunately common are SSH servers that run with high privileges and are accessed using basic passwords. SSH-targeting attacks such as dhpcd can be easily blocked by configuring SSH to work exclusively with private and public keys, while blocking all password-based login attempts.
To apply that, modify your SSH config file (/etc/ssh/sshd_config) to have the following two lines:
PermitRootLogin no
PasswordAuthentication no
To block dhpcd’s cryptomining activity, consider blocking outgoing TCP port 4444, which has been used in a significant number of attack incidents we’ve observed. Also, block all connections to known mining pool domains. You can find those related to dhpcd in our IoC repository.
To detect whether your system is infected, run our detection script for locating dhpcd traces.
Final thoughts
dhpcd is a cryptomining campaign that uses tried and true techniques: it spreads over SSH, runs a cryptominer based on the well-known XMRig, and uses known tactics to set up backdoors and eliminate competitors.
This campaign does demonstrate better OPSEC than most attack campaigns we observe, by incorporating Tor into the infection pipeline. Using Tor prevents defenders from tracing the attack infrastructure and origins, making the whole operation more stable and resistant.
The use of Tor represents a bit of a double-edged sword: Organizations use Tor to support anonymity, privacy, and security, but as a by-product, by installing exit nodes, they become part of the infection chain. Although not necessarily infected themselves, these organizations provide a mechanism that is used to spread the malware across the internet, helping the attackers stay anonymous and protected.
dhpcd proves to us once again that even the most basic and simple attack campaigns — ones characterized by dictionary attacks performed for compromise and file names that have their letters swapped to reduce detection — still manage to infect networks and make profits. Moreover, these campaigns are developed and maintained to level up the scale and scope of potential gains. The simple tactics, tips, and procedures, however, suggest that even with basic protection measures, alert defenders can increase the security of their systems.
Appendix: indicators of compromise
The following is a partial list of IOCs. Please find the complete list in our repository.
File names
/bin/[a-z0-9]{26} (Hello World program)
/bin/dhpcd
Domains
fr14[.]minexmr[.]com
ca61[.]minexmr[.]com
sg97[.]minexmr[.]com
fr13[.]minexmr[.]com
us40[.]minexmr[.]com
pool[.]supportxmr[.]com
File hashes
eb808932714c9533962e129e61d84c29536497e62b2a7d89dce3376d882c6965
e971fa0c392a9f43c37dccfdd4f8e6bc109e162716d9b206170f7bb133634ffd
76005592ad7d8901c64a5cfbcdde589a960ba35c9672da6182d131cd67ae0c97
2cca764d24212f8fc58780b9135740929f38b45bcd5fc82c4a2ff47e90890d06
3ea8cc0977e5542053353bcf3e58de947dd727259369707a13a4d0c8f14b7486


