Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
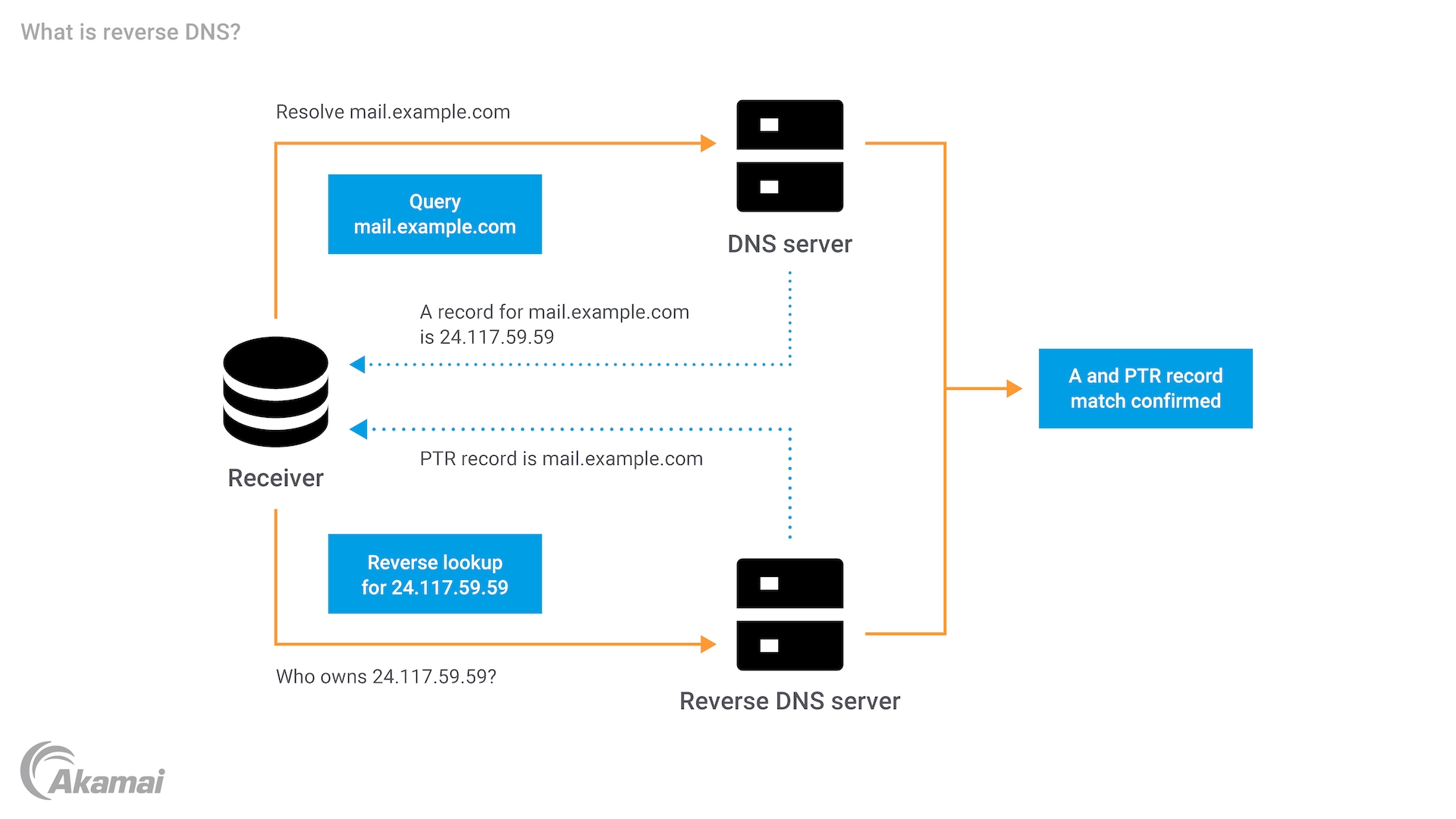
Reverse DNS (rDNS) is the process of discovering a name from an IP address input, whereas “traditional” DNS lookups accomplish the opposite feat by translating a hostname to an IP.
dig -x 24.117.59.59
Example of reverse DNS lookup on a Mac (using Terminal)
nslookup 24.117.59.59
Example of reverse DNS lookup for Windows and Linux
Specifically, rDNS entails resolving the IP value in reverse with “in-addr.arpa” appended at the end.1 Thus, the command in the example above will actually look up “59.59.117.24.in-addr.arpa”. If the owner of the IP successfully configured rDNS, this query will return a “pointer” (PTR) record, which associates the IP with a domain:
59.59.117.24.in-addr.arpa. 43200 IN PTR 24-117-59-59.cpe.sparklight.net.
Why is reverse DNS important?
While rDNS is not universally adopted for traditional web traffic, PTR records are particularly important for email servers, which often perform rDNS lookups to block or filter out spam. To ensure messages are received without any red flags, legitimate email providers are required to properly implement rDNS for IP addresses and forward DNS for the resulting hostnames. This expectation was established to prevent spammers from sending emails from compromised machines since these IPs often don’t have rDNS records, and when they do, the response is frequently a generic, dynamic output that suggests the client is not a valid email service.
As shown above, the residential IP 24.117.59.59 points to a 24-117-59-59.cpe.sparklight.net PTR record, which is a dynamic output, as it is simply the IP address with the sparklight domain appended. So if a spammer were to hack the machine and send an email from the residential IP, the receiver would likely block or filter the message since dynamic responses are a strong spam signal (for reference, a hypothetical acceptable response would be email.sparklight.net). In short, a spammer would have to own an IP space to arrange the necessary DNS settings for the message to be universally accepted — a prohibitive cost for most threat actors.
Finally, some email servers rely on more nuanced rDNS settings with the help of SMTP (Simple Mail Transfer Protocol), a standardized communications protocol for email transmission. For example, email servers can be configured to reject emails when the rDNS query does not match the HELO command, a message that starts the SMTP session. Thus, if a botnet was able to send thousands of emails from hundreds or thousands of hijacked machines belonging to a variety of networks, it would be difficult for the malicious actor to announce the correct domain in each HELO message, even if rDNS was properly configured for the IP.
Client: HELO mail.example.com
Server: 250 mail.example.com Hello
How do you set up reverse DNS?
For an rDNS lookup to return a valid response, an in-addr.arpa rDNS zone file will need to be created that reflects the fixed network range allocated to the IP owner. Specifically, the zone admin should remove the last dotted quad that contains the values explicitly under their control, reverse the order of the remaining dotted octet, and append .in-add.arpa.
Since Sparklight owns a Class B address, their rDNS zone file name is 117.24.in-addr.arpa. Looking at the full resolution process, ARPA owns the 24.0.0.0/8 Class A addresses2 but delegates 117.24 queries to Sparklight:
Zone |
Comments |
|
|---|---|---|
Root servers |
j.root-servers.net. |
Like all DNS requests, the query starts at the root server |
Delegation to ICANN |
in-addr.arpa. |
Root servers delegate to a set of ICANN servers responsible for managing the ARPA zone |
Another delegation to ICANN / ARPA |
24.in-addr.arpa. |
ICANN delegates to ARPA, who owns the 24.0.0.0/8 class A |
Delegation to Sparklight |
117.24.in-addr.arpa. |
The query is then delegated to Sparklight, who owns this range |
Answer |
59.59.117.24.in-addr.arpa. |
PTR record returned |
Just like with forward DNS, each “dot” in an rDNS hostname is a potential delegation point. ICANN manages the in-addr.arpa zone and delegates subzones to owners of an IP space.
Within the zone file, the relevant PTR records should be advertised, and just like with any other zone, nameserver (NS) records should be defined as well.
59.59.117.24.in-addr.arpa. 43200 IN PTR 24-117-59-59.cpe.sparklight.net.
117.24.in-addr.arpa. 43200 IN NS ns2.cableone.net.
117.24.in-addr.arpa. 43200 IN. NS ns4.cableone.net.
117.24.in-addr.arpa. 43200 IN NS ns3.cableone.net.
117.24.in-addr.arpa. 43200 IN NS ns1.cableone.net.
Conclusion
While rDNS may not be necessary for a typical web or native application to function on the open internet, it is an important requirement for any functional email service. A reverse lookup can also be a helpful tool for analytics and troubleshooting, as application owners can determine if an IP belongs to a commercial ISP, cloud provider, or another organization/business entity. This information is often useful to track leads, especially for B2B companies that want to better understand who is browsing their site. Similarly, knowing who owns an IP can help security tools determine whether the request belonged to an attacker or a legitimate source.
While not nearly as prevalent or well known as forward DNS, rDNS plays an important role in today’s internet ecosystem — and understanding this nuance of the protocol is imperative for email administrators, B2B marketing analysts, and cybersecurity experts.
1 ip6.arpa is the zone for IPv6 addresses.
2 Class A addresses are for networks with a large number of total hosts. Class A allows for 126 networks by using the first octet for the network ID. Class B addresses are for medium to large networks. Class B allows for 16,384 networks by using the first two octets for the network ID.