An example of a domain generation algorithm is the Conficker worm’s DGA, which was used to generate a large number of unique domain names for its command and control infrastructure.
A domain generation algorithm (DGA) is a program that generates large numbers of new domain names. Cybercriminals and botnet operators use domain generation algorithms to frequently change the domains they use to launch malware attacks. This technique enables hackers to avoid malware-detection solutions that block specific domain names and static IP addresses.
Why do cybercriminals use domain generation algorithms?
Threat actors use malware to infect a large number of computers or devices within corporate IT environments. Attackers can issue commands to these malware-infected machines or bots and collect information from them using a command and control server (C2 server), which is typically also a machine hosted within a compromised system. This network of bots, or botnet, can be used to propagate spam, steal sensitive data, or conduct distributed denial-of-service (DDoS) campaigns and other cyberattacks.
To prevent these malicious activities, cybersecurity services and solutions attempt to identify the IP addresses of machines and websites involved in communication between C2 servers and infected devices, blocking any traffic going to or coming from those IP addresses based on threat intelligence from a network security provider. To continue their attacks, cybercriminals must continually switch domains to avoid detection by blocklists, signature filters, security gateways, reputation systems, intrusion prevention systems, and other security technology.
Using DGAs to generate a large number of domain names, cybercriminals can quickly switch domains at a pace that makes it hard for detection engines to keep up.
How do domain generation algorithms work?
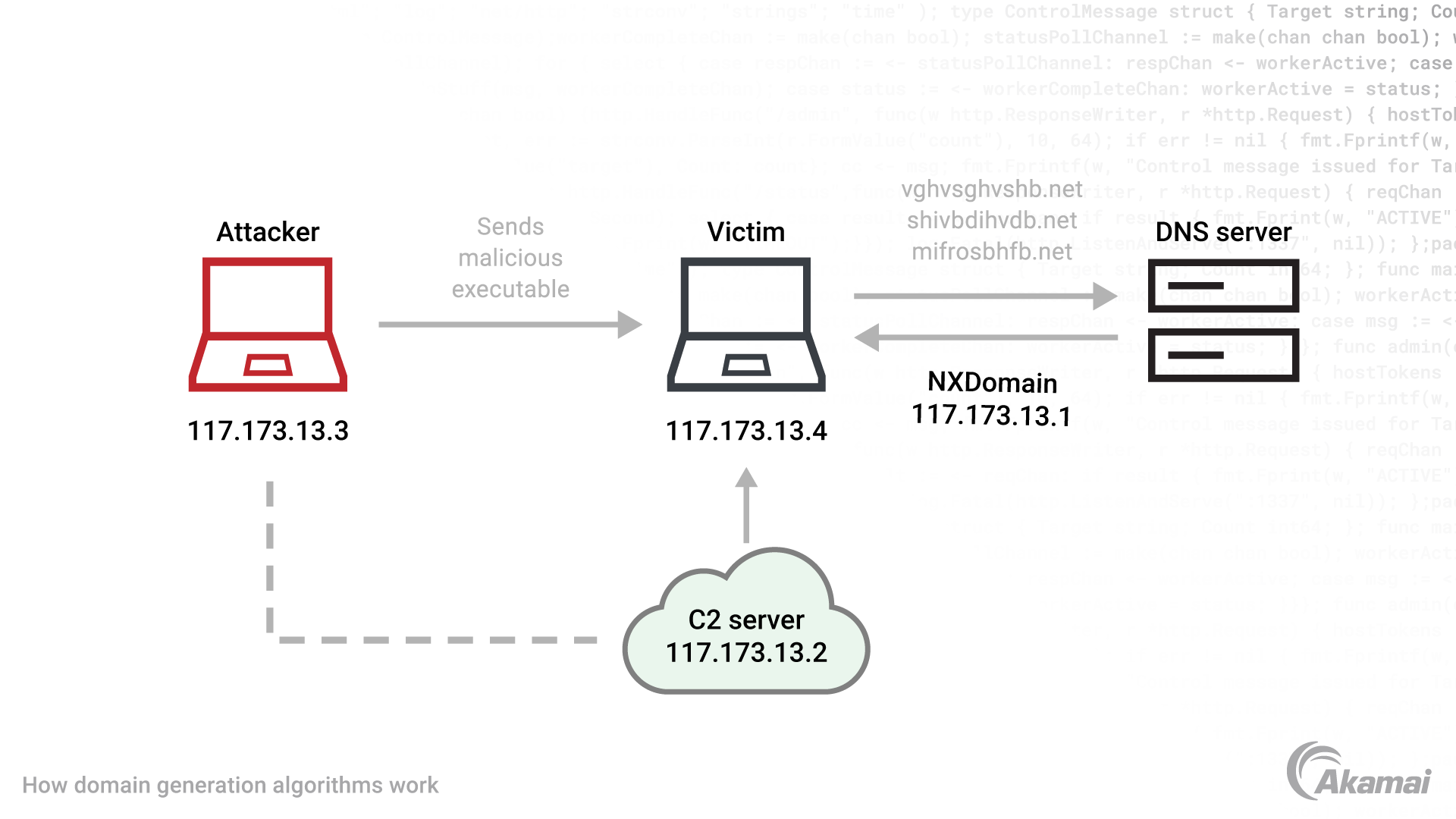
Domain generation algorithms are applications that use sequences of characters to quickly produce thousands of domain names that could serve as a rendezvous point where attackers can communicate with C2 servers. These algorithms can generate tens of thousands of DGA domain names each day — most of them unregistered. Hackers use the unregistered domains to hide the registered ones, making it easier to evade detection by inspection engines that use signatures and IP reputation. The algorithm is executed on both the client and source sides. It starts with a seed that is known to both the attacker and the C2 server, allowing both to know which domains will be generated and which domain will be registered to serve as the communication channel for malware. If that domain is identified by security systems and blocked, attackers can quickly switch to the next domain to maintain contact with the C2 server, following a pattern that both the hacker and the malware or botnet understand.
What are the types of DGAs?
Hackers have developed different types of DGAs to increase their ability to create malicious domains while evading detection.
- Pseudorandom number generator (PRNG) DGAs are the most common methodology, using a random seed (often the system date and time) to generate domain sequences that both the attacker and the malware can predict.
- Character-based DGAs use a random seed to generate domain names with letters or numbers. These DGAs are the easiest to detect.
- Dictionary-based DGAs randomly combine words to generate domains that appear to be readable and are more challenging for security systems to detect since they look like legitimate domains.
- High-collision DGAs are designed to look like legitimate domain names and are paired with top-level domains (TLDs) like .com, .net, and .org. With high-collision DGAs, there’s a greater likelihood that the domain produced is already registered, causing a “collision” that can add a layer of confusion to the detection process.
How can organizations detect DGA domains?
The steps organizations take to prevent malware may also prevent DGAs. Since domain generation algorithms are used to advance malware, most anti-malware solutions will offer basic defenses against these threats. Best practices include:
- Adopt an optimal patching cadence to keep software updated, preventing attackers from exploiting software vulnerabilities to penetrate defenses and install malware.
- Conduct security awareness training to help users recognize potentially malicious links, websites, and emails that may be part of a malware attack.
- Use URL filtering to prevent users from accessing websites or clicking on links that are known to be malicious.
- Deploy security solutions to block users’ ability to open malicious attachments or enable macros on attached documents.
- Choose DNS security solutions that can aid DGA detection by identifying and blocking communication between C2 servers and malware using DNS traffic, which can often otherwise pass through firewalls without inspection.
- Deploy anti-DGA technology that uses machine learning and big data to identify anomalous activity and take down malicious sites.
Frequently Asked Questions (FAQ)
Three factors that can be used in domain generation algorithms are time, random seed, and mathematical calculations.
DGAs are useful for cybercriminals because they allow them to constantly change the domains used for communication with infected machines, making it difficult for security researchers and law enforcement to track and take down their infrastructure.
The main difference between a domain generation algorithm and a word list is that a DGA generates domain names algorithmically based on certain factors, while a word list is a static list of predetermined domain names that can be used by a malware or botnet for communication purposes. DGAs provide a higher level of variability and unpredictability compared to word lists.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.

