Zero Trust Network Access Without the Performance Penalty
We've all been there: It’s the morning of an important meeting, and you’re doing a final check of the numbers you'll be presenting. You open your laptop, click on the business application, and head to the kitchen for that much-needed first coffee. When you return, the application is still loading — strange.
After waiting a bit longer, you reboot and try again. The application opens this time, but it's sluggish and the virtual private network (VPN) authentication is unresponsive. Frustrated, you call the IT help desk. The issue takes several hours to get resolved, leaving your stress levels high and your morning suddenly unproductive.
We expect applications to start quickly and respond instantly. Slow load times and unresponsive interfaces not only lead to user frustration, but can also create a ripple effect that disrupts workflows and impacts productivity — especially when time is wasted on troubleshooting or waiting for the application to catch up.
Addressing performance issues
This inefficiency often leads users to further strain resources by escalating the issues to IT support. As more users face similar performance issues, overwhelmed IT teams compound the frustration and resolutions don’t come quickly enough. In short, poor application performance affects both individual productivity and the overall efficiency of the organization.
The process can be further complicated when enterprises implement Zero Trust cybersecurity models that include security services like Zero Trust Network Access (ZTNA). Even with the knowledge that extra network security layers are in place, users' expectations on load times and responsiveness aren’t likely to change. Because of this, application performance in conjunction with ZTNA becomes even more important.
To learn how organizations can roll out ZTNA securely without compromising performance, we need to understand why ZTNA replaced VPNs in the first place.
ZTNA emerged as a more secure alternative to VPNs
For remote employees, VPNs have traditionally been the standard method for accessing private business applications. However, these same VPNs can create security vulnerabilities that malicious actors may exploit to infiltrate corporate networks.
To address these risks, ZTNA emerged as a more secure alternative for managing remote access to applications. This approach gained significant traction during the COVID-19 pandemic and continues to be relevant as hybrid and remote work become permanent fixtures in the modern workplace.
As time passed, however, enterprises realized they needed consistent Zero Trust access controls, regardless of whether employees were working remotely or on site.
ZTNA for all workforces — not just remote ones
Here’s an example: Consider a scenario where you’re working in the office, and the application you need to access is hosted in a data center in the same location. Because you are on the corporate network, once you are authenticated you would access the application directly, enjoying optimal application performance. However, that means the ZTNA granular application access policy is no longer in place, which means the business is no longer enforcing Zero Trust principles.
This situation is the opposite of Zero Trust; access controls should not be based on where an employee is located. If the business enables the ZTNA policy for on-premises users, then the users are forced to connect through a cloud point of presence (PoP), which then routes traffic back to the on-premises application. Secure access is enhanced, but this “hairpinning” of traffic often results in poor application performance for the users.
Ensuring secure application access without performance impact for on-site employees
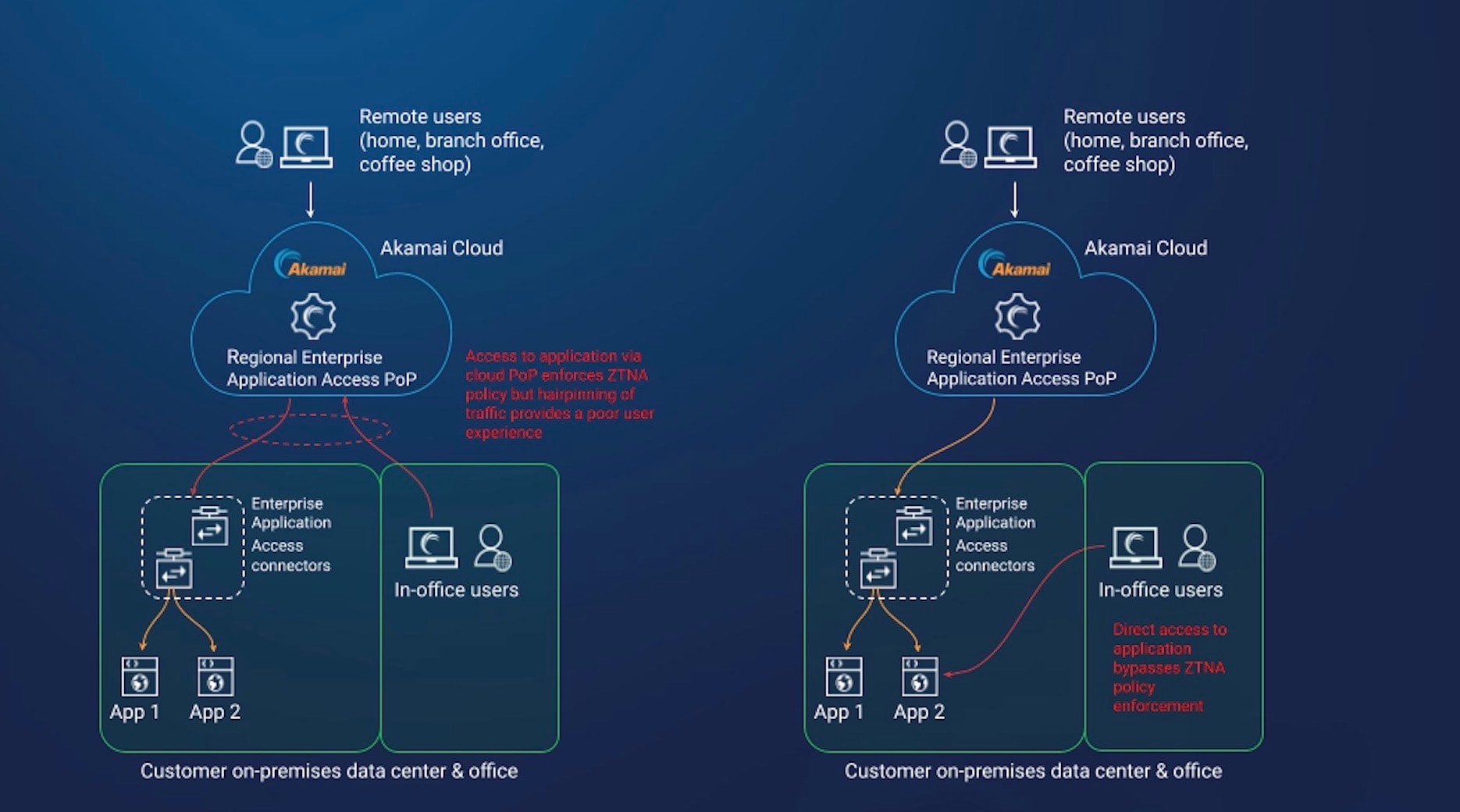
Figure 1 shows the existing architecture and traffic routing for Akamai Enterprise Application Access for on-premises applications when the users are in the office.
Performance challenges
On the left side of the figure, the in-office users connect to a regional Enterprise Application Access point of presence (PoP), where the ZTNA policy is enforced. The traffic is then hairpinned back to the application, which can negatively impact performance.
On the right side of the figure, Enterprise Application Access is deactivated for the in-office users. This architecture eliminates the hairpinning of traffic and gives direct access to the application, but ZTNA security policies are no longer being enforced. This goes against the basic tenets of Zero Trust in terms of least-privilege access based on identity and security posture.
Enterprise Application Access with local point of presence to the rescue
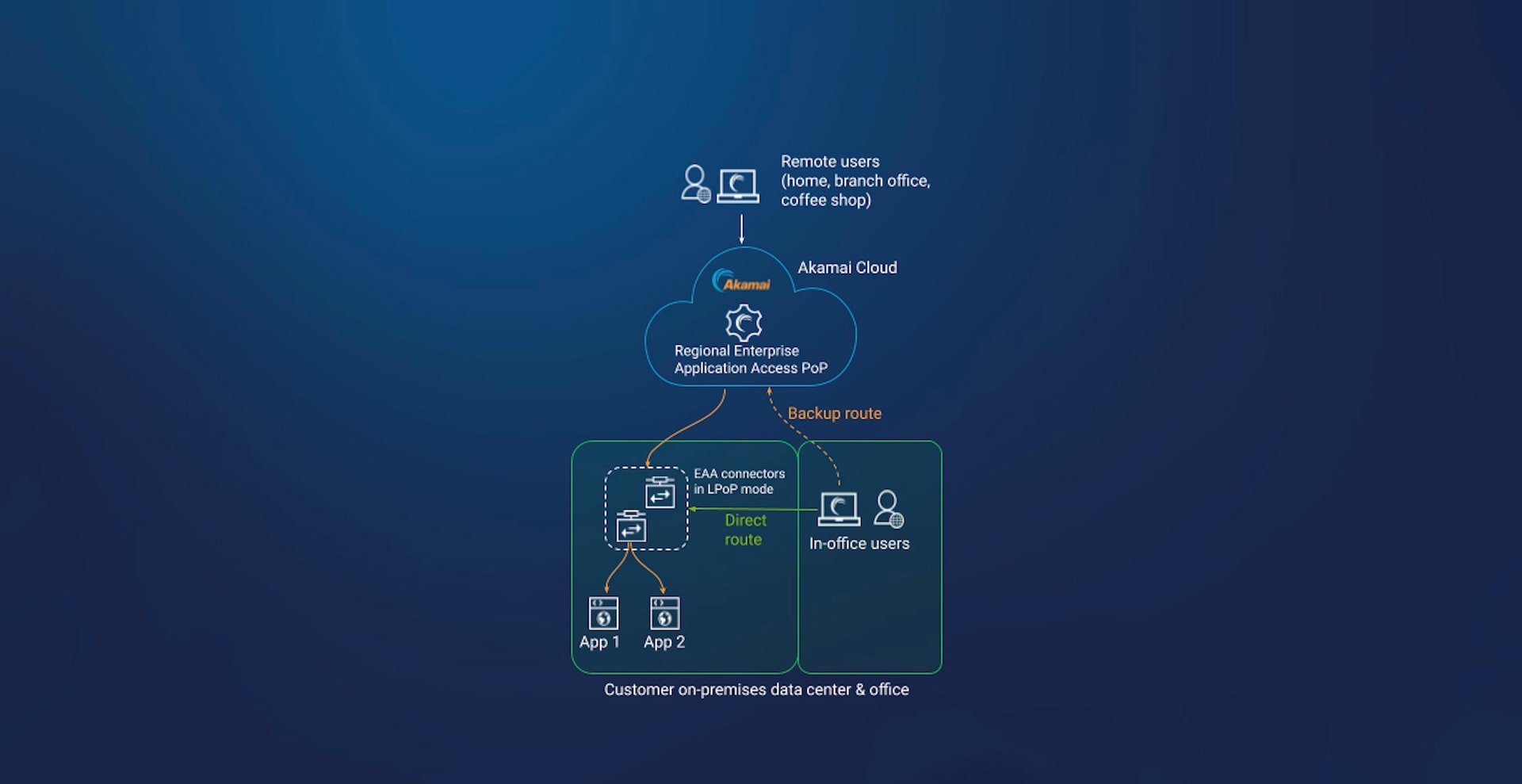
Enterprise Application Access in local point of presence (LPoP) mode solves the performance and security challenges that can occur when your employees and private applications are in the same location (Figure 2).
With the introduction of LPoP, enterprises can quickly activate the functionality in their existing Enterprise Application Access connectors — no additional software components need to be deployed and managed.
By associating on-premises applications in the access policy with the LPoP, hairpinning of traffic to the Enterprise Application Access cloud PoP is eliminated. End users experience near wire-speed access to on-premises applications and, most important, the same Zero Trust access policies are upheld and enforced by the Enterprise Application Access connector operating in LPoP mode.
Universal ZTNA
Now, no matter where users are working from, they can enjoy fast application access with the same granular application access privileges. In fact, beta program customers have reported up to a 300% improvement in file download speeds when using an LPoP vs. an Enterprise Application Access cloud PoP — a significant boost in performance.
Naturally, since our industry loves acronyms, this new capability has been named Universal ZTNA (UZTNA).
Ensuring application performance everywhere
Ensuring security without affecting performance is possible in local situations with LPoP, but what happens when employees and applications are scattered across the world?
For example, imagine that you're a global company with dozens of offices and numerous applications hosted across different regions and infrastructures, such as on-premises, infrastructure as a service (IaaS), security as a service (SaaS), or public cloud. If you have employees working in, say, Brazil who need to access specific applications hosted in the United States or Germany, ensuring optimal application performance with ZTNA solutions can be exceptionally challenging. It's critical to do so, however, to maintain productivity and user satisfaction.
Performance challenges
In the example scenario above, one specific challenge is ensuring that you have a global ZTNA infrastructure located close to both the users and applications across the entire network. The planetary scale of Akamai Cloud helps solve that challenge for most enterprises.
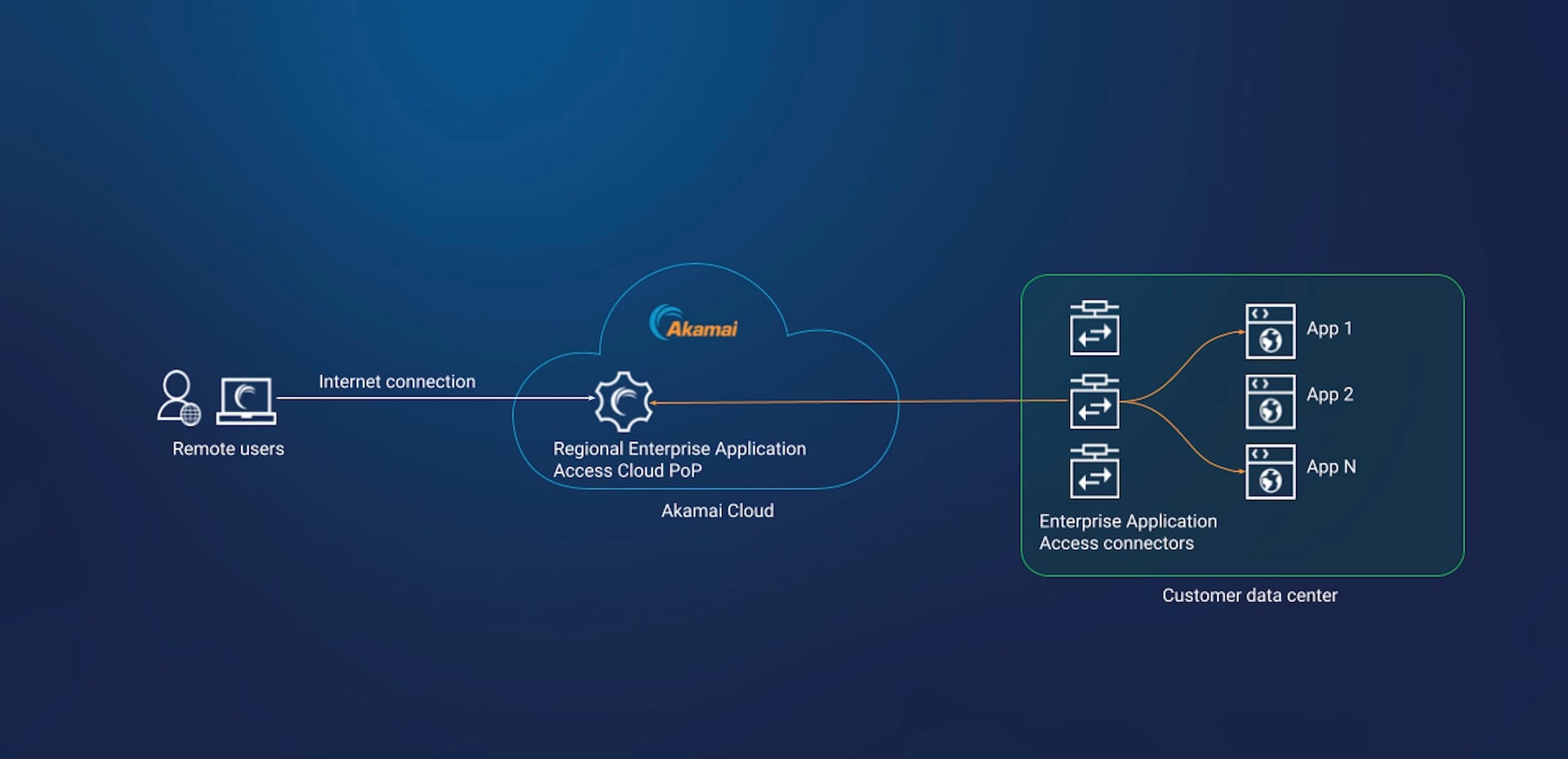
Figure 3 illustrates the current high-level architecture of Enterprise Application Access. Today, we have more than 40 regional Enterprise Application Access cloud PoP zones deployed. However, we often find deployment scenarios in which the applications are located close to a zone, but the end users are located a considerable distance from a zone.
This can sometimes translate into variable application performance, especially when the first-mile internet connection is poor or the application uses a chatty protocol such as Microsoft SMB.
Enterprise Application Access with Edge Transport delivers outstanding application performance
To develop a solution, we went back to the drawing board and came up with a new approach that both applies the scale of Akamai Cloud and taps into one of Akamai’s core businesses: content delivery.
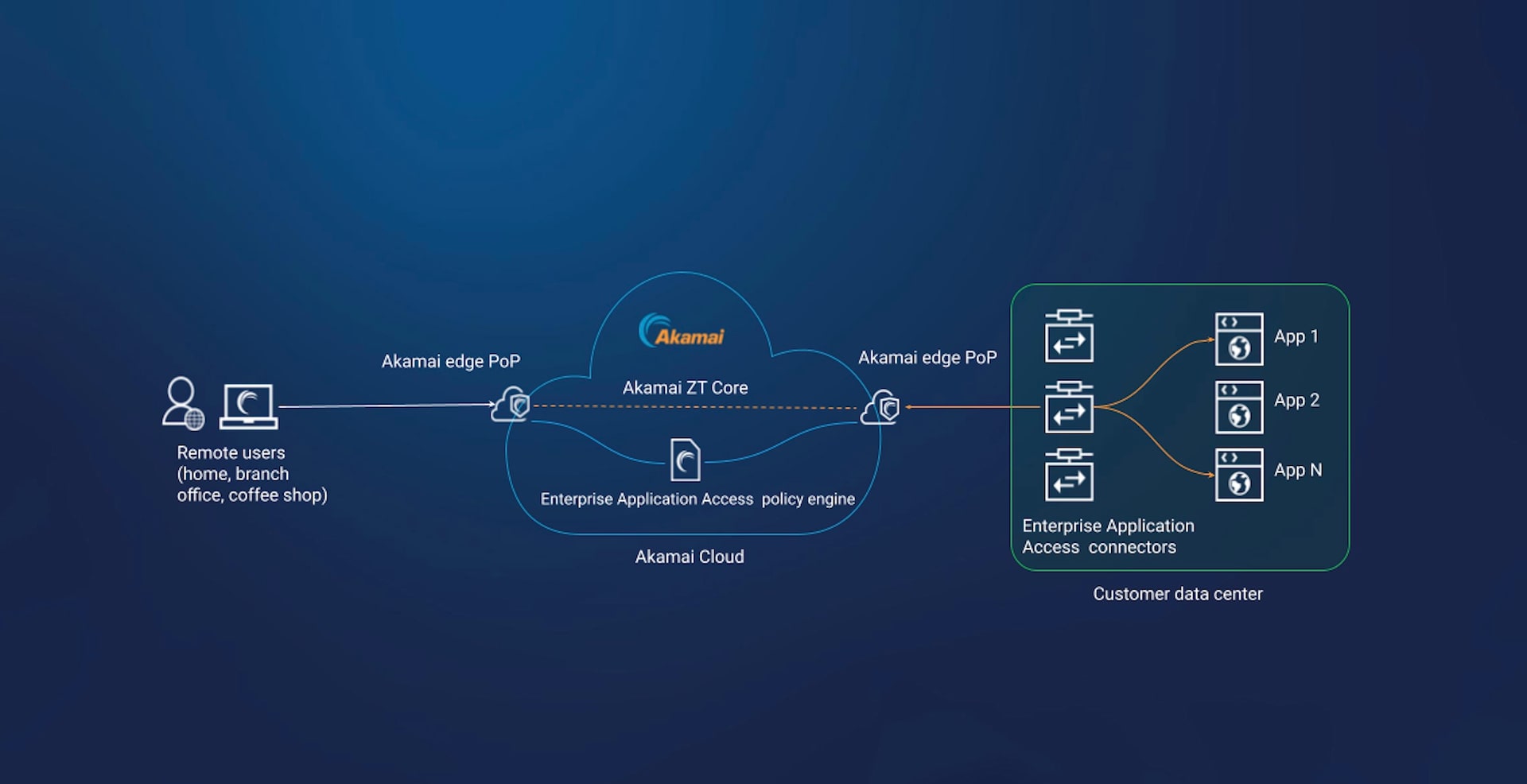
Figure 4 shows the Enterprise Application Access architecture with Edge Transport for client-based (TCP/UDP) applications.
In this configuration, the architecture has a few key differences. Most significantly, we have eliminated the Enterprise Application Access cloud PoPs from the architecture. Instead, we are now using Akamai edge PoPs to on-ramp and off-ramp application traffic.
In terms of scale, we currently have more than 4,200 edge PoPs, which means we can now bring Enterprise Application Access infrastructure closer to both user devices and applications — no matter where they’re located.
In terms of policy, there’s now an Enterprise Application Access policy engine that federates the customers’ Enterprise Application Access policies out to the edge PoPs, meaning policy is enforced at the edge and closer to the users.
Finally, the middle-mile transport uses a new architecture: ZT Core. This applies Akamai’s 25+ years of expertise in running the world’s largest and most distributed CDN to route application traffic over our platform in the most effective, efficient way.
Edge Transport, which can also be deployed for web-based apps, ensures that employees enjoy a great application experience no matter where they are or where the applications are located — even when the first-mile internet link is problematic.
Seamless and reliable end-user experiences
To date, our early adopters are unlocking impressive performance gains with Edge Transport. Here’s some of what they’re seeing:
Faster file transfers: Microsoft Server Message Block (MS-SMB) file uploads and downloads are now up to 40% faster, making day-to-day operations significantly smoother.
Snappier applications: Critical business apps feel more responsive with noticeably reduced latency, even during demanding workflows.
Resilience in unpredictable networks: Users are enjoying consistent, high-performance application access, even when network connectivity isn’t at its best.
The result? A more seamless and reliable end-user experience across the board. Teams are completing tasks faster, interruptions are minimized, and overall productivity is on the rise.
Edge Transport isn’t just a technical upgrade to ZTNA. It’s a tangible improvement in how users interact with their most critical applications.
Get Zero Trust security and great performance regardless of location
These new Enterprise Application Access features will help global enterprises apply Zero Trust security policies no matter where users are located or where the applications are hosted — all while maintaining a delightful end-user experience. That’s essential, since no one should have to choose between great security and a great user experience.
Learn more
If you’d like to learn more about Enterprise Application Access or these new capabilities, please contact our experts.