The Massive Propagation Of The Smominru Botnet

Guardicore Labs has been tracking the Smominru botnet and its different variants – Hexmen and Mykings – since 2017. The attack compromises Windows machines using an EternalBlue exploit and brute-force on various services, including MS-SQL, RDP, Telnet and more. In its post-infection phase, it steals victim credentials, installs a Trojan module and a cryptominer and propagates inside the network.
In this post, Guardicore Labs provides an in-depth analysis of the attack campaign, focusing on victim analysis and attack infrastructure. Additionally, we have published a script to detect Smominru’s residues on infected machines, as well as a full list of the campaign IoCs.
Among other things, we found that many machines were reinfected even after removing Smominru. This suggests that these systems remain unpatched, and therefore vulnerable to this botnet or other similar attackers. Since patching is often complicated in large data centers, it is highly important to use additional security controls, such as applying network segmentation and minimizing the number of internet-facing servers.

Smominru victim statistics
Scope and victims
The Smominru botnet appeared in recent publications describing the group’s new capabilities and malicious intent. These prompted us to seek out the campaign’s indicators in Guardicore Global Sensors Network (GGSN) and Guardicore Cyber Threat Intelligence. Analysis of the attacks showed strong resemblance to the Hexmen group we researched last year and led us to further analyze the campaign’s most recent iteration.
Guardicore Labs gained access to one of the attackers’ core servers – one which stores victim information and credentials. Monitoring the server’s contents over time enabled us to study infection patterns and draw conclusions of the extent of the campaign. Guardicore Labs has informed identifiable victims and provided them with the details of their infected machines.
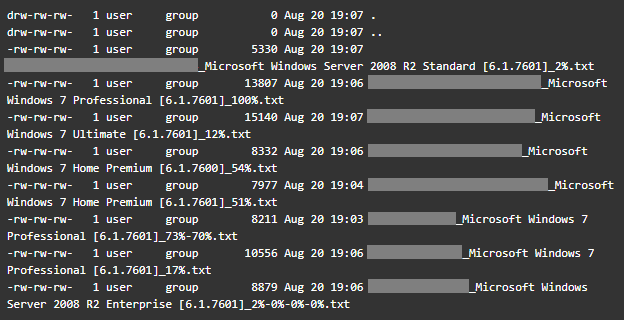
Directory listing of the attacker’s FTP server
The attackers’ logs describe each infected host; its external and internal IP addresses, the operating system it runs and even the load on the system’s CPU(s). Furthermore, the attackers attempt to collect the running processes and steal credentials using Mimikatz.
Guardicore Labs decided to take a closer look at the nature of the victims to better understand who is in the crosshairs of Smominru’s (and similar groups’) attacks.
Victims analysis and statistics
During August, the Smominru botnet infected 90,000 machines around the world, with an infection rate of 4,700 machines per day. Countries with several thousands of infected machines include China, Taiwan, Russia, Brazil and the US.
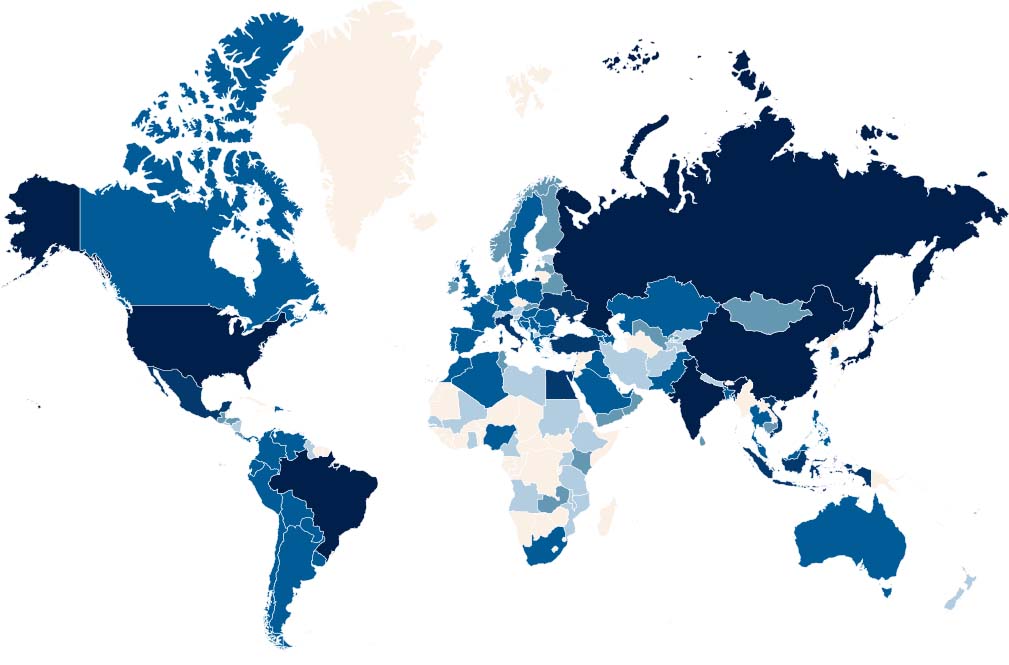
Global distribution of Smominru. Darker colors represent more infected countries.
Infected networks include US-based higher-education institutions, medical firms and even cyber security companies. As the attacks were untargeted and did not discriminate against industries or targets, they reached victims in various sectors. When discussing worms, there are no interesting and uninteresting targets – every vulnerable server is under attack.
Once it gains a foothold, Smominru attempts to move laterally and infect as many machines as possible inside the organization. Within one month, more than 4,900 networks were infected by the worm. Many of these networks had dozens of internal machines infected. The largest network belongs to a healthcare provider in Italy with a total of 65 infected hosts.
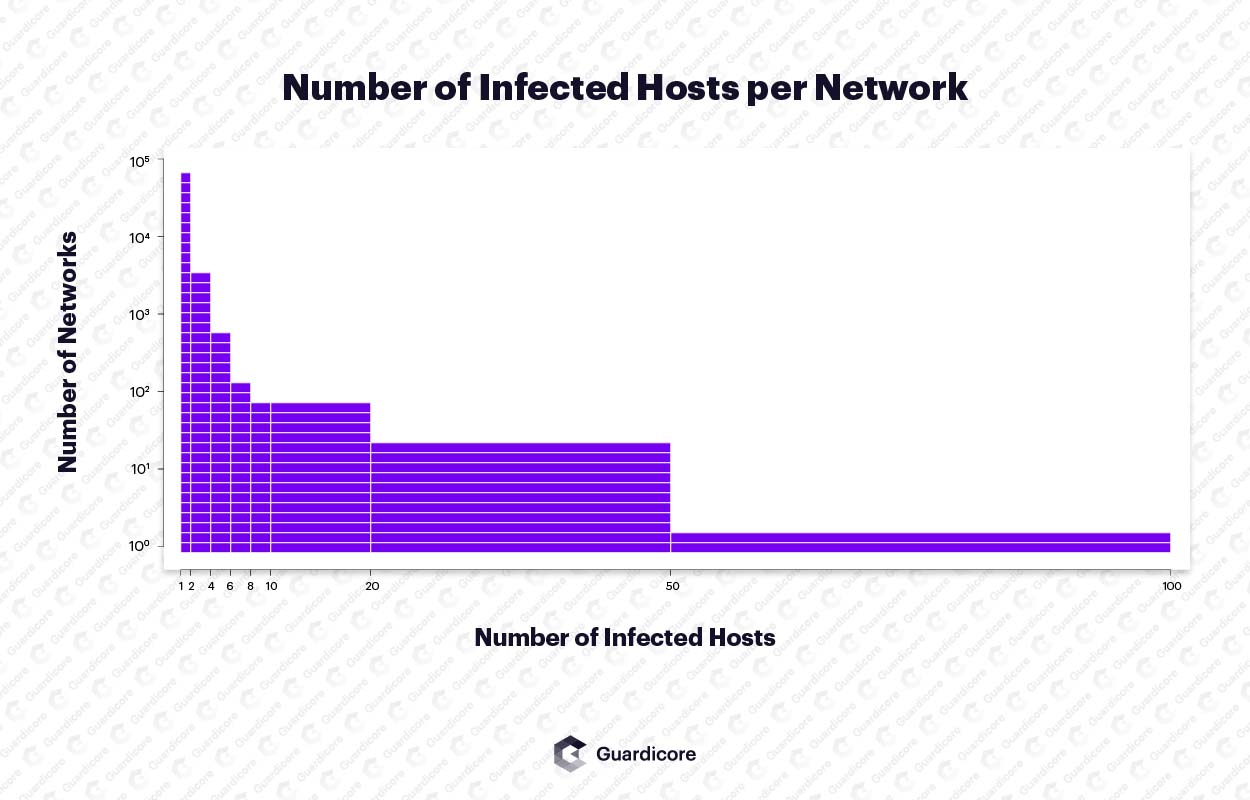
Number of infected hosts per network
Not surprisingly, Windows 7 and Windows Server 2008 are the most infected operating systems, representing 85 percent of all infections. These are Windows versions for which there is an operational EternalBlue exploit available on the internet. Other victim operating systems include Windows Server 2012, Windows XP and Windows Server 2003. These are either systems which have been out of support for many years, or about to be End of Life.
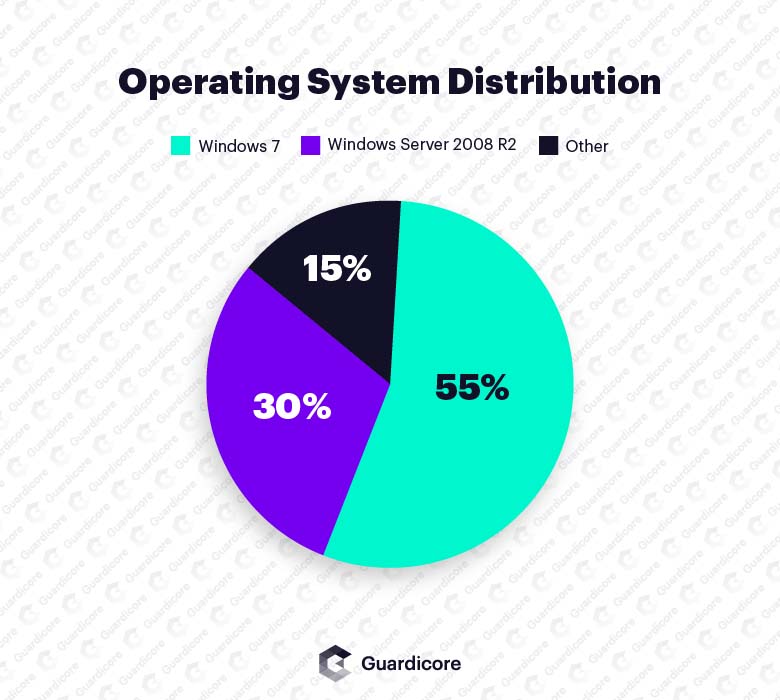
OS Distribution across victim machines
The infected machines are primarily small servers, with 1-4 CPU cores, but there were also some larger servers. We found more than 200 victim machines with more than 8 cores. One such machine was running on a 32-core server. Unfortunately, this demonstrates that while many companies spend money on expensive hardware, they are not taking basic security measures, such as patching their running operating system.
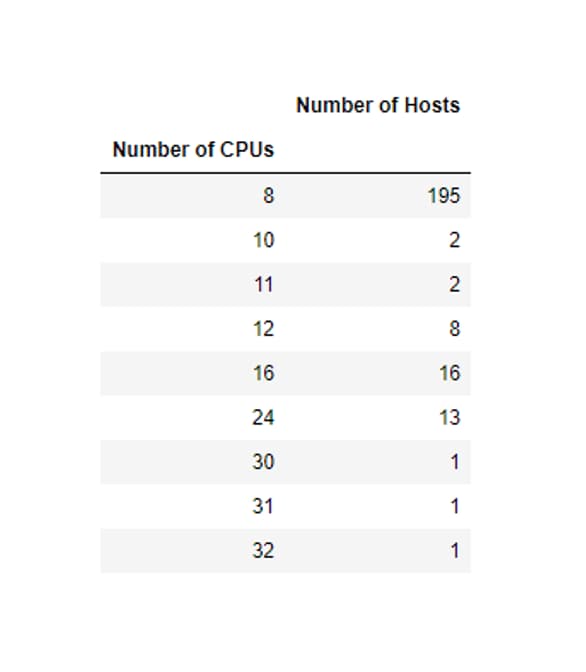
Number of hosts per number of CPUs
According to our analysis, one fourth of the victims were reinfected by the worm. This suggests that victims attempted to cleanup their systems without fixing the root cause issue that left them vulnerable in the first place.
Attack flow
Previous iterations of the Smominru botnet used many different services and attack files, and this version is no different. A common theme with prior variants such as Hexmen, is removing other criminal infections and adding backdoor users. However, all the IoCs found in this attack were new.
The botnet compromises machines using various methods, the prominent ones being the EternalBlue exploit and brute-force of different services and protocols, such as MS-SQL, RDP and Telnet. This section will focus on the EternalBlue attack flow.
EternalBlue is a cyberattack exploit allegedly developed by the US National Security Agency (NSA). The exploit uses a security vulnerability in Windows SMB server stack and was weaponized for Windows 7 / Windows Server 2012 R2 targets.
After the initial compromise, a first-stage Powershell script named blueps.txt is downloaded onto the machine. This script performs several operations (detailed in the next sections):
- It downloads and executes three binary files;
- It creates a new administrative user named admin$ on the system;
- It downloads additional scripts to perform malicious actions.
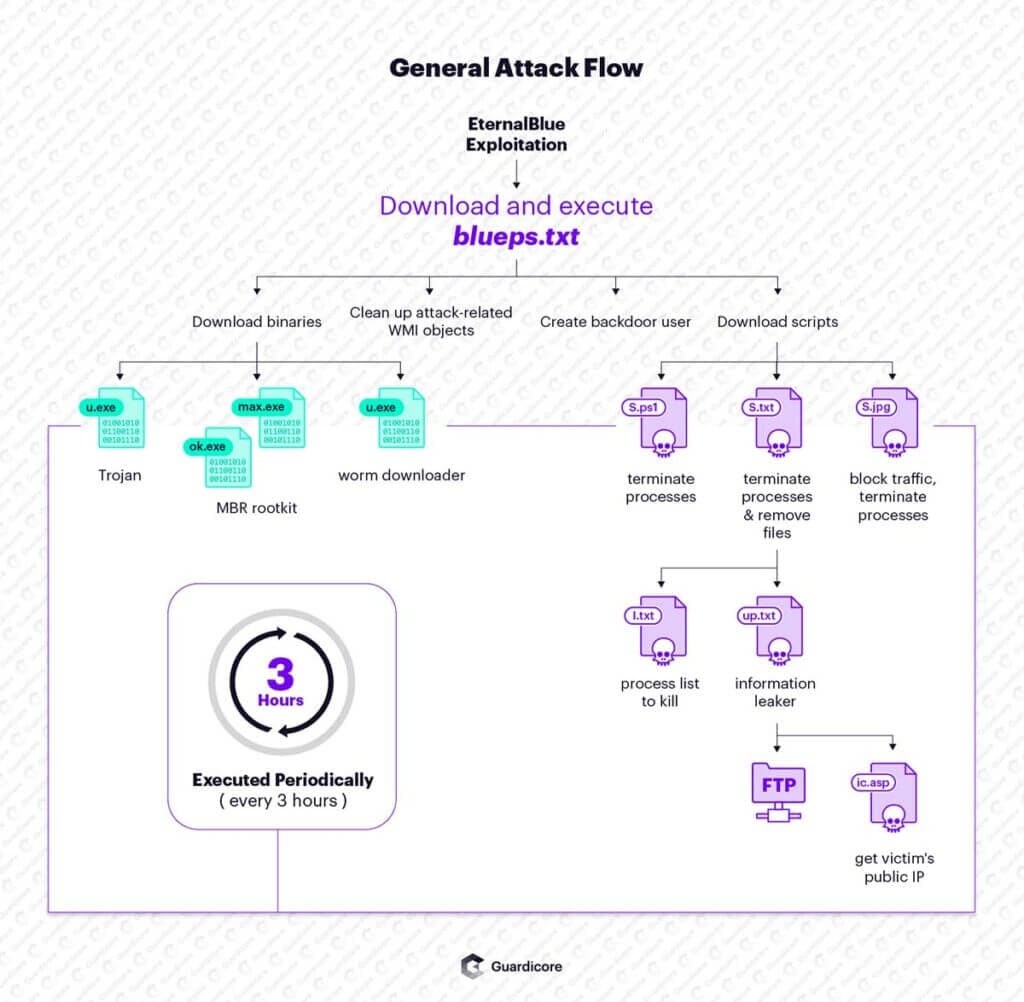
Smominru’s initial attack phase
The attackers create many backdoors on the machine in different phases of the attack. These include newly-created users, scheduled tasks, WMI objects and services set to run at boot time. The MS-SQL attack flow includes a unique persistence method; the attackers use the obscure task scheduling engine inside MS-SQL to run jobs at different time intervals, e.g. upon reboot, every 30 minutes, etc.
Eliminating other malicious actors
Unlike previous versions of the botnet, it appears that the attackers are putting much effort in disabling and blocking other malicious actors’ activity. This is done in various ways:
1. Processes identified as other campaigns’ are killed, and their corresponding executable files are deleted;
taskkill /f /m help.exe /m doc001.exe /m dhelllllper.exe /m DOC001.exe /m dhelper.exe /m conime.exe /m a.exe /m docv8.exe /m king.exe /m name.exe /m doc.exe /m wodCmdTerm.exe /m win1ogins.exe /m win1ogins.exe /m lsaus.exe /m lsars.exe /m lsacs.exe /m regedit.exe /m lsmsm.exe /m v5.exe /m anydesk.exe /m sqler.exe /m sqlservr.exe /m NsCpuCNMiner64.exe /m NsCpuCNMiner32.exe /m tlscntr.exe /m eter.exe /m lsmo.exe /m lsarr.exe /m convert.exe /m WinSCV.exe /m ctfmonc.exe /m lsmose.exe /m svhost.exe /m secscan.exe /m wuauser.exe /m splwow64.exe /m boy.exe /m powered.EXE /m systems.exe /m acnom.exe /m regdrv.exe /m mscsuscr.exe /m Pviunc.exe /m Bllianc.exe /m st.exe /m nvidia_update.exe /m dether.exe /m buff2.exe /m a.exe /m lacas.exe
2. Backdoor credentials of other groups are dropped or deliberately broken by password modification (among these groups is Guardicore’s discovered Nansh0u)
exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','users'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','usera'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','ps'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','fox'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','wwo'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','wq'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','so'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','gaibian'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','xxa'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','win7'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','vice'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','sz'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','ss'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','se'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','gd'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','syn'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','sasa'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','count'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','Myar'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','chica'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','masqer'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','system'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','Rolename'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','kisadminnew1'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','nanshou1433'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','nanshou'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','shitou'; exec sp_password Null,'5yqbm5,m`~!@ ~#$%^&*(),.; ','nanshou';
3. Scheduled tasks created by other groups are removed;
SCHTASKS /Delete /TN "WindowsUpdate1" /F& SCHTASKS /Delete /TN "WindowsUpdate3" /F& SCHTASKS /Delete /TN "Windows_Update" /F& SCHTASKS /Delete /TN "Update" /F& SCHTASKS /Delete /TN "Update2" /F& SCHTASKS /Delete /TN "Update4" /F& SCHTASKS /Delete /TN "Update3" /F& SCHTASKS /Delete /TN "windowsinit" /F& SCHTASKS /Delete /TN "System Security Check" /F& SCHTASKS /Delete /TN "AdobeFlashPlayer" /F& SCHTASKS /Delete /TN "updat_windows" /F& SCHTASKS /Delete /TN "at1" /F& SCHTASKS /Delete /TN "at2" /F& SCHTASKS /Delete /TN "Microsoft LocalManager[Windows Server 2008 R2 Enterprise]" /F& SCHTASKS /DELETE /TN "\Microsoft\Windows\UPnP\Services" /f& SCHTASKS /Delete /TN "Microsoft LocalManager[Windows Server 2008 R2 Standard]" /F
4. MS-SQL jobs created by other attack campaigns are deleted;
use msdb EXEC sp_delete_job @job_name = 'dbdotas'; EXEC sp_delete_job @job_name = 'ftpback.exe'; EXEC sp_delete_job @job_name = 'pdoor.exe'; EXEC sp_delete_job @job_name = 'kils.exe'; EXEC sp_delete_job @job_name = 'install.exe'; EXEC sp_delete_job @job_name = 'java.exe'; EXEC sp_delete_job @job_name = 'shengda.exe'; EXEC sp_delete_job @job_name = 'mac.exe'; EXEC sp_delete_job @job_name = 'reg.exe'; EXEC sp_delete_job @job_name = 'wmi'; EXEC sp_delete_job @job_name = 'regs.exe';
In addition, Smominru blocks various TCP ports (SMB, RPC) in order to prevent other attackers from breaching its own infected machines.
cmd.exe /c netsh ipsec static delete policy name=win netsh ipsec static add policy name=win netsh ipsec static add filterlist name=Allowlist netsh ipsec static add filterlist name=denylist netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=135 netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=137 netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=138 netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=139 netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=445 netsh ipsec static add filteraction name=Allow action=permit netsh ipsec static add filteraction name=deny action=block netsh ipsec static add rule name=deny1 policy=win filterlist=denylist filteraction=deny netsh ipsec static set policy name=win assign=y
Binary payloads
The binary files downloaded by blueps.txt include a worm downloader (u.exe / ups.exe), a Trojan horse (upsupx.exe) and an MBR rootkit (max.exe / ok.exe).
u.exe (also named ups.exe, and previously referred to as cab.exe) is responsible for the worm module. It lays the groundwork for the worm by downloading DLLs required to perform network scans. Then, it connects to an attack server, checks for the latest version of the worm and downloads it. The versioning mechanism allows the attackers to add, modify and remove propagation techniques within the worm program. Finally, the worm is registered as a service named xWinWpdSrv and its downloader – u.exe – deletes itself.
The Master Boot Record (MBR) is a popular target for malware authors targeting older operating systems. By maliciously modifying the MBR, attackers can take over the operating systems boot process and inject their code into every part of the system.
The worm is an executable file downloaded as wpd.jpg and saved locally as msinfo.exe. This is the module responsible for spreading the malicious payloads within the network, using a Python-based EternalBlue exploit and brute-force of multiple Windows services, such as MS-SQL, Telnet, RDP, and more.
The third executable (upsupx.exe) drops a variant of an open-source Trojan named PcShare. The Trojan has many capabilities, including download and execute, command and control, screenshot capturing and information stealing. In the Smominru campaign, we suspect that the Trojan is used primarily to download a Monero cryptominer.
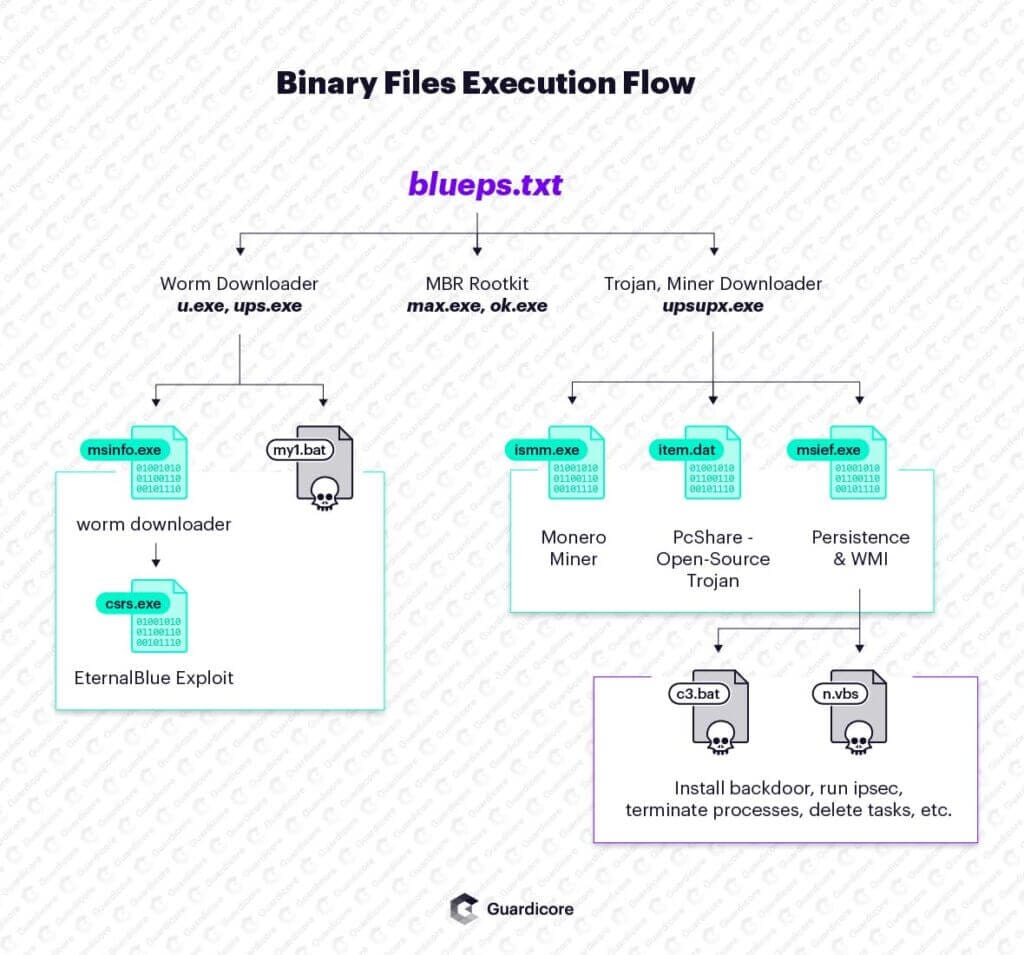
Smominru Binaries Execution Flow
Attack infrastructure and backend
The Smominru group tends to use a large collection of payloads throughout the attack. In its current iteration, Smominru downloads and runs almost twenty distinct scripts and binary payloads.
The storage infrastructure is widely distributed; more than 20 servers are used as part of the attacks. Each machine serves a few files, with each file referencing additional 2-3 servers. Many of the files are stored on more than one hosting server, making the attack infrastructure flexible and fairly resistant to takedowns.
Unlike the typical botnet, most of the machines are dedicated servers used by the attackers rather than repurposed victim servers. These machines are mostly hosted in the US, with some hosted by ISPs in Malaysia and Bulgaria. Guardicore has informed the ISPs of the abused machines. None of these ISPs has replied, but we noticed that some of them no longer host malicious files after receiving our emails.
A significant amount of the attacks originate from western ISPs. Many hosting companies proactively detect and block malicious activity coming from their networks. It is unclear why hosting companies such as Verizon or Rackspace are incapable of policing their networks in a similar fashion. Such actions would have stopped a large fraction of these attacks.
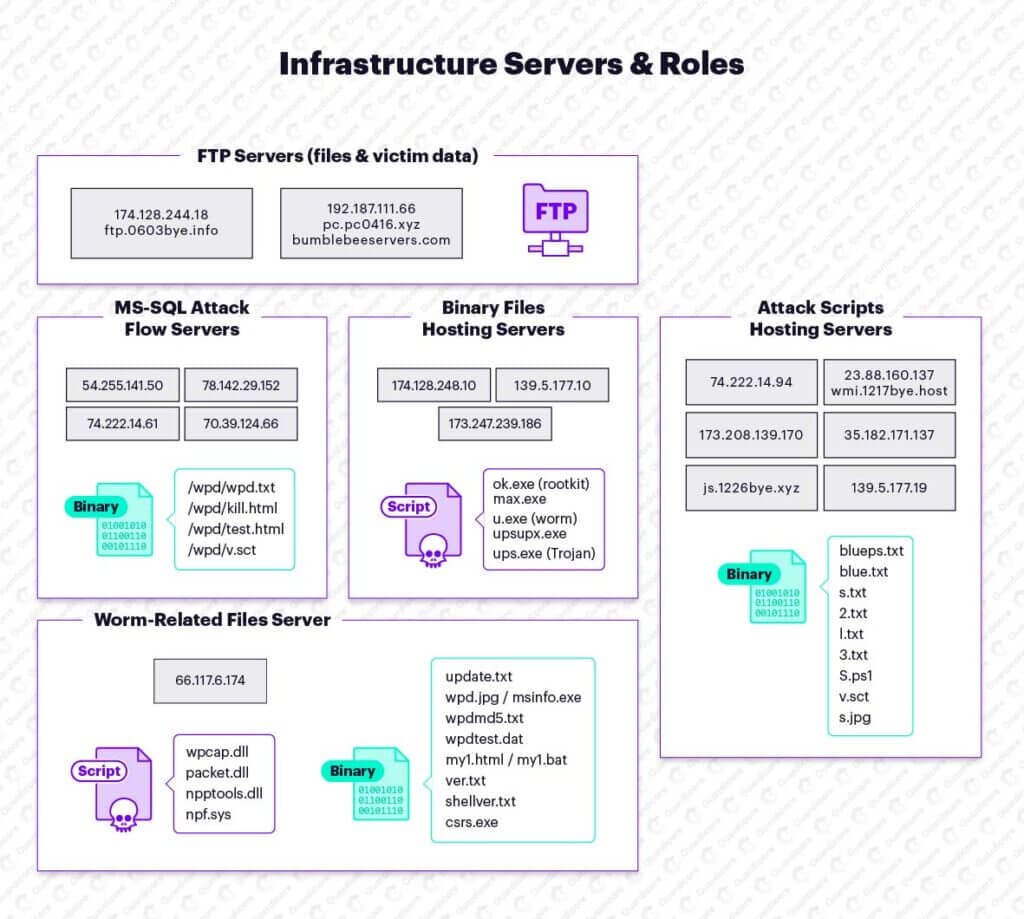
Core servers in the attack infrastructure
Detection
Guardicore Labs has developed a Powershell script to detect machines infected with the Smominru worm. The script is easily run from Windows command line interface. For more details and usage instructions, please visit our campaign repository.
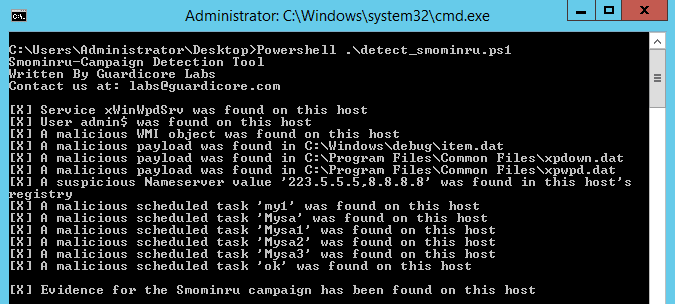
Guardicore’s Detection Script run in cmd
Alternatively, you can manually check for the existence of the admin$ user, or the existence of the following files which indicate the Trojan’s execution on the machine.
C:\Windows\Debug\item.dat C:\Program Files\Common Files\xpdown.dat C:\Program Files\common Files\xpwpd.dat
Mitigation
The spreading of Smominru is heavily based on weak passwords, but it also relies on the existence of EternalBlue vulnerable machines. Unpatched systems allow the campaign to infect countless machines worldwide and propagate inside internal networks. Thus, it is crucial that operating systems be aligned with the currently-available software updates.
However, patching is never as simple as stated. Therefore, it is of high importance to apply additional security measures in the data center or the organization. Network microsegmentation and real time threat detection of possibly malicious internet traffic as well as limiting internet-exposed servers are all critical to maintaining a strong security posture.
IoCs
For a full list of the Smominru campaign’s indicators of compromise, please visit Guardicore Labs’ campaigns repository. Some IoCs are shared in this section.
Backdoor usernames
- user: admin$
- password: Zxcvbnm,.1234
| IP ADDRESS | DOMAIN |
| 35.182.171.137 | |
| 54.255.141.50 | |
| 173.247.239.186 | |
| 66.117.6.174 | fra.gamesoxalic.com, down.1226bye.pw |
| 192.187.111.66 | pc.pc0416.xyz, bee12.bumblebeeservers.com |
| 23.88.160.137 | wmi.1217bye.host. d20.xtrmserver.com |
| 139.5.177.10 | |
| 139.5.177.19 | |
| 78.142.29.152 | |
| 79.124.78.127 | |
| 74.222.14.61 | |
| 74.222.14.94 | |
| 174.128.244.18 | ftp.0603bye.info |
| 174.128.248.10 | garrafa8.itaucredicard.tk |
| 45.58.135.106 | |
| 70.39.124.66 | |
| 223.25.247.240 | worldsender.info, server.triangleww.com |
| 173.208.139.170 | |
| 173.208.172.202 | grinknowledge.com |
| js.1226bye.xyz |
Binary files
| IP ADDRESS | SHA256 (links are to VirusTotal) |
| ok.exe max.exe |
A3BB132AB1BA3E706B90D6FB514504105F174C4E444E87BE7BCE1995F798044D |
| u.exe ups.exe |
BE5E698BD72FD58A8D202E511CF356924F0A1200E91BD25DCB5442E33A7B4F14 |
| upsupx.exe | 9EC520EBA82B8EAEB11BC00612748C6DB210E6753D8E87905747270EBCFA9EB2 |
| msinfo.exe wpd.jpg |
7EC433DD0454553B09F11C39944E251E3EE32E4981F52F02ADC3011EB0CE6537 |
| csrs.exe | 4958C38BA2D7DEF9BA44C5382F2C5A41C619D5A5EEDFB8AC4697DBF75C306933 |
| msief.exe | E8DDEFD237646A47DEBC01DF9AA02FBCAE40686F96B7860511C73798C7546201 |
| item.dat | 80F8BA7992A5DBAA4A2F76263258D5D7BF3BB8994F9E8A4A5294F70AB8E38EA4 |
| lsmm.exe | 8246293A368A1DA86ABA696BEA93460705CA4C40AA4C75DDE909B8D9DFF5EFCB |



