DDoS Attacks Against Life Sciences Organizations Likely to Rise
As Akamai celebrates 10 years of State of the Internet (SOTI) reports, we’re sharing insights from key industries that we serve, including healthcare & life sciences. This is the second blog post in a SOTI series that will culminate in a comprehensive report later this year. You can read the first post in the series here.

A recent cyberattack that severely stymied prescription processing and payments across the country set up something like a chain of attack dominoes that clobbered the rest of the healthcare ecosystem. Some provider groups lost up to US$100 million daily, there was havoc for payer member experience teams, and many patients were forced to pay out of pocket for their medications or else wait for the claims system to be restored. The U.S. government stepped in with work-arounds to provide relief, but the knots are still being untangled.
The focus on pharmaceutical cybersecurity became laser sharp during the COVID-19 crisis, when vaccine development research, trial data, manufacturing, production, and rollout were all considered fair game by threat actors. But today, it’s even more clear why healthcare is classified as U.S. critical infrastructure, and why new bipartisan funding elevates resilience requirements across sectors that are deemed critical.
The president and CEO of the American Hospital Association characterized a recent attack that disrupted the link between pharmacies and payers as “the most significant and consequential incident of its kind against the U.S. healthcare system in history.”*
DDoS attacks are increasing
International tensions continue to rise globally, and the geopolitical climate weighs heavily on the executives who responded to PwC’s 25th Annual Global CEO Survey. Almost one-third of the respondents said that geopolitical conflict threatens their companies’ growth, and more than two-thirds said it’s an expected factor in supply chain disruption.
Approaches like localized sourcing and enhanced use of blockchain technology can help enhance resiliency and improve clinical and business impacts.
Akamai global data for the life sciences industry suggests that distributed denial-of-service (DDoS) attacks — and the number of groups perpetrating them — are only growing; resilience is just what this sector needs.
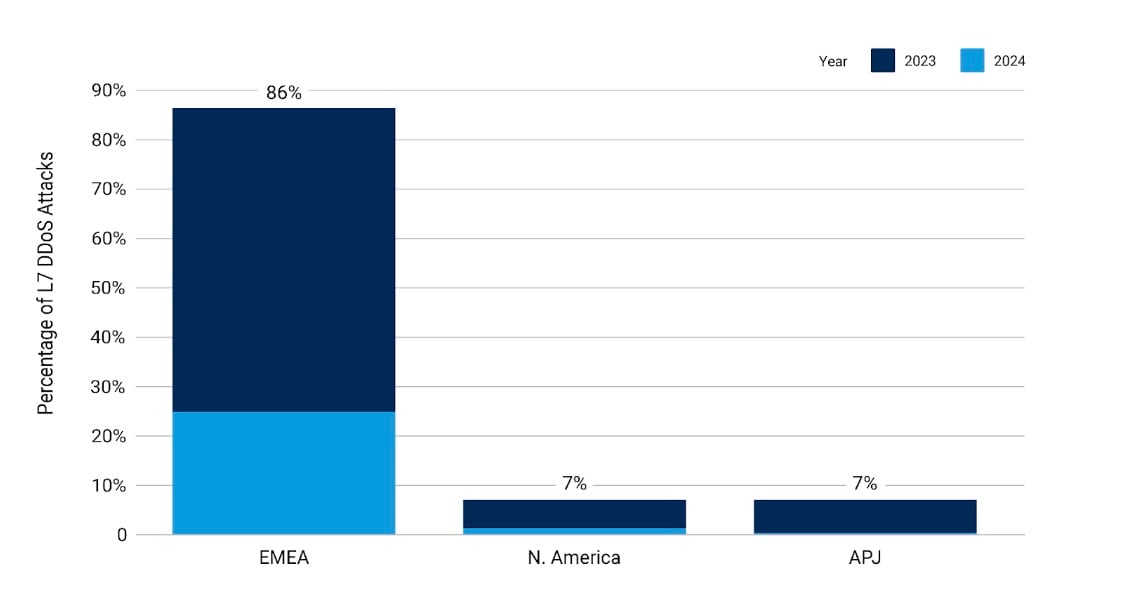
EMEA targeted by application-layer DDoS attacks
Akamai research found that from January to December 2023, the Europe, Middle East, and Africa (EMEA) region experienced 86% of all application-layer (Layer 7) DDoS attacks, while North America and Asia-Pacific and Japan (APJ) accounted for 7% each. Looking at January to March 2024, we see the concentration in EMEA continuing and attacks in North America outpacing APJ (Figure 1).
Regional L7 DDoS Attacks: Pharmaceuticals
January 1, 2023 – March 31, 2024
Unlike traditional Layer 3 or Layer 4 DDoS attacks, which aim to overwhelm network and transport-layer infrastructure, application-layer DDoS attacks target specific application functionalities or the application server itself. They could cause significant damage even with a relatively small amount of malicious traffic.
Application-layer DDoS attacks target application-level resources, such as CPU and memory, so the targeted application or service may become slow or entirely unresponsive even if the network remains available.
Increased DDoS attacks in the European Union
The ENISA 2023 Threat Landscape: Health Sector report confirms an increased number of DDoS attacks in the healthcare & life sciences industry in the European Union. It’s interesting to note that the “hot spot” countries for cyber incidents in the report (especially France, Germany, and the Netherlands) correlate closely with the geographic concentration of the pharmaceutical and biotech companies in 2022’s leading 1,000 companies in the European Union.
ENISA (the European Union Agency for Cybersecurity) attributes the increase in DDoS attacks to geopolitical developments and pro-Russian hacktivist groups such as Killnet.
U.S. hospitals targeted next
That attack group first targeted European hospitals before moving on to hospital targets in each U.S. state. Although those cyberattacks made most of the headlines, an April 2023 report from U.S. Health and Human Services notes the percentage of organizations targeted by Killnet was actually highest among pharmaceutical and biotechnology companies.
Given that the United States has a larger life sciences global market share (50%) than EMEA (34%), it is reasonable to expect that the threat of DDoS attacks on pharmaceutical companies based in the United States may intensify.
But no country or geography is immune. India, one of the world’s largest producers and exporters of generic medicines, suffered major consequences last year after a data breach that leaked 17 TB of company data. The ransomware gang and threat actor ALPHV/BlackCat claimed responsibility for the ransomware attack that included sensitive information on vendors, customers, and documents for 1,500 U.S. employees.
Which threat actors are using which tactics?
The ENISA report cites ALPHV/BlackCat as one of the main attacker groups against life sciences in EMEA — the same group that clobbered the U.S. supply chain earlier this year.
Like Killnet, Anonymous Sudan is mentioned in the report as being politically motivated; this criminal organization first targeted provider groups but is now expanding its targets to include other parts of the healthcare ecosystem.
That makes recent developments like Anonymous Sudan’s claim of responsibility for recent DDoS attacks against Open AI even more worrisome. The group says it used the Skynet botnet, which recently incorporated support for application-layer attacks (Layer 7 DDoS attacks) to overwhelm applications and generate errors.
Pharmaceutical companies: High stakes require a conservative approach
Pharmaceutical companies have long been healthcare industry leaders in the use of artificial intelligence (AI) and machine learning (ML), benefiting from their ability to analyze large datasets for myriad applications, including earlier detection of disease, faster drug discovery, and drug manufacturing improvements. However, similar to other industries that have embraced digital transformation — such as financial services — life sciences is at the crossroads of innovation and risk.
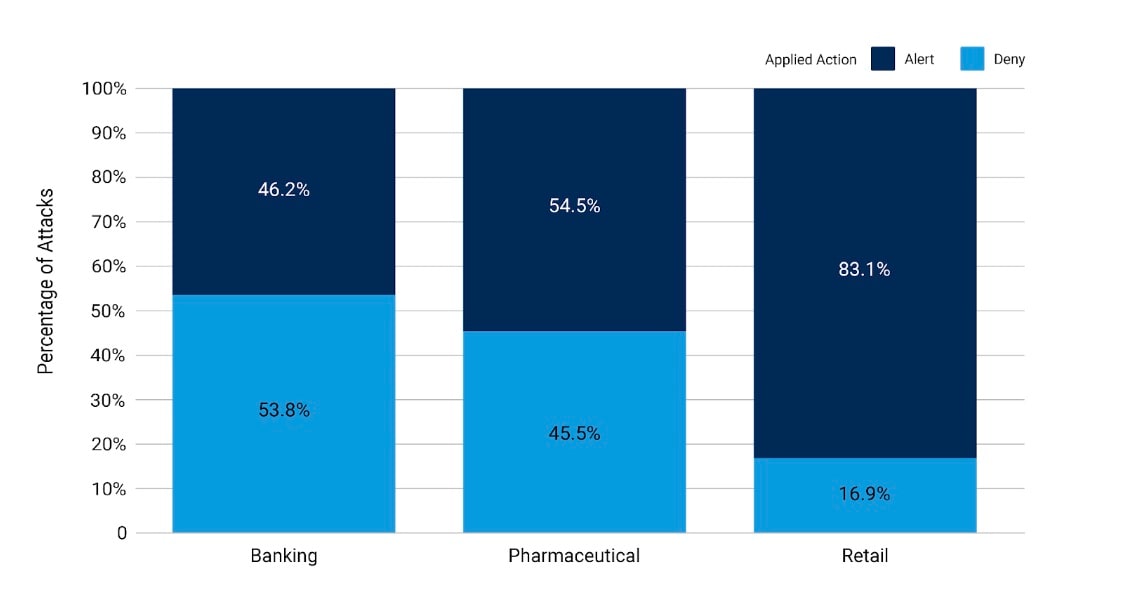
Pharmaceutical organizations are taking a stand. By looking at how other regulated industries handle Layer 7 DDoS attacks, Akamai researchers found that when it comes to the percentage of “deny” versus “alert” actions applied, pharmaceutical companies have conservative policies that deny anomalous activity at a comparatively high rate (Figure 2).
L7 DDoS Applied Action by Sub-Vertical
January 1, 2023 – March 31, 2024
Other industries such as financial services and banking share these similarly conservative policies; both banking and life sciences are considered critical infrastructure and thus heavily regulated, which accounts for many parallels.
Additionally, in the case of pharmaceutical organizations, the consequences of a successful DDoS attack can be severe, potentially endangering people’s lives by delaying access to life-sustaining medications. It makes sense to lean into “deny” and then investigate.
In contrast, retail takes a less aggressive stance, allowing for more time to receive an alert and assess anomalous activity before taking action. But we may see a shift to more frequent deny actions among retailers if new regulations come into play, particularly around the use of AI/ML.
Strengthen resilience with a layered defense
Pharmaceutical companies are intentionally moving in the right direction — toward strengthening defenses and controlling access. However, because threat actors quickly shift their targets, tactics, and motivations, staying on top of risks as you innovate requires a layered defense.
Here is a list to help you determine if you’re on the right track and to help you focus investments accordingly.
Secure your infrastructure with a DDoS mitigation tool and a microsegmentation approach to contain an attack
Secure your access with Zero Trust Network Access, including multi-factor authentication to avoid account takeovers
Secure your web applications and APIs to ensure data and analytics outcome integrity
Learn more
Learn more about how Akamai partners with life sciences organizations to understand and solve for emerging and evolving threats.
*Jonathan Reed. Change Healthcare attack expected to exceed $1 billion in costs. Security Intelligence. May 8, 2024.