Why Payers Are Pivotal to API Security Across the Healthcare Ecosystem
As Akamai celebrates 10 years of State of the Internet (SOTI) reports, we’re sharing insights from key industries we serve, including healthcare and life sciences. This is the first blog post in a SOTI series that will culminate in a comprehensive report later this year.

With robust access to both clinical and financial data, payers are the nexus of data sharing across the healthcare ecosystem — and they increasingly rely on application programming interfaces (APIs) to do that sharing. APIs make it possible to share data among providers, payers, patients, and other third parties, such as electronic health record systems, medical device companies, and health information exchanges.
The drive toward interoperability enables better patient and financial outcomes, but also comes with tradeoffs — notably, significant compliance requirements and security considerations. Cybercriminals and aggregators are attacking and abusing these capabilities, which can result in both safety and privacy issues.
For payers, API-enabled attacks can also result in service disruptions that impact open enrollment and claims operations, lead to costly downtime, and damage the company's brand.
In this blog post, we analyze threat data and trends related to attacks on APIs to understand the extent of the risks and present best practices for their mitigation.
API attacks under the microscope
Akamai research found that from January through December 2023, nearly half the API attacks that targeted the healthcare ecosystem (payers, providers, and pharmaceutical and life science companies) were against payer organizations. This indicates that payers face a more concentrated risk of API abuse by attackers than do other less digital-centric industry sub-verticals.
We see a similar trend in other regulated industries — especially those that handle payment systems. The finance industry, for example, is further along in its digital transformation journey and is already using more integrated APIs as part of its business models. Open banking is driving its use of APIs and introducing more security risks. Therefore, the finance sector is experiencing a higher concentration of API-focused attacks. (Read more about attack trends in Akamai’s recent State of the Internet (SOTI) report, Lurking in the Shadows: Attack Trends Shine Light on API Threats.)
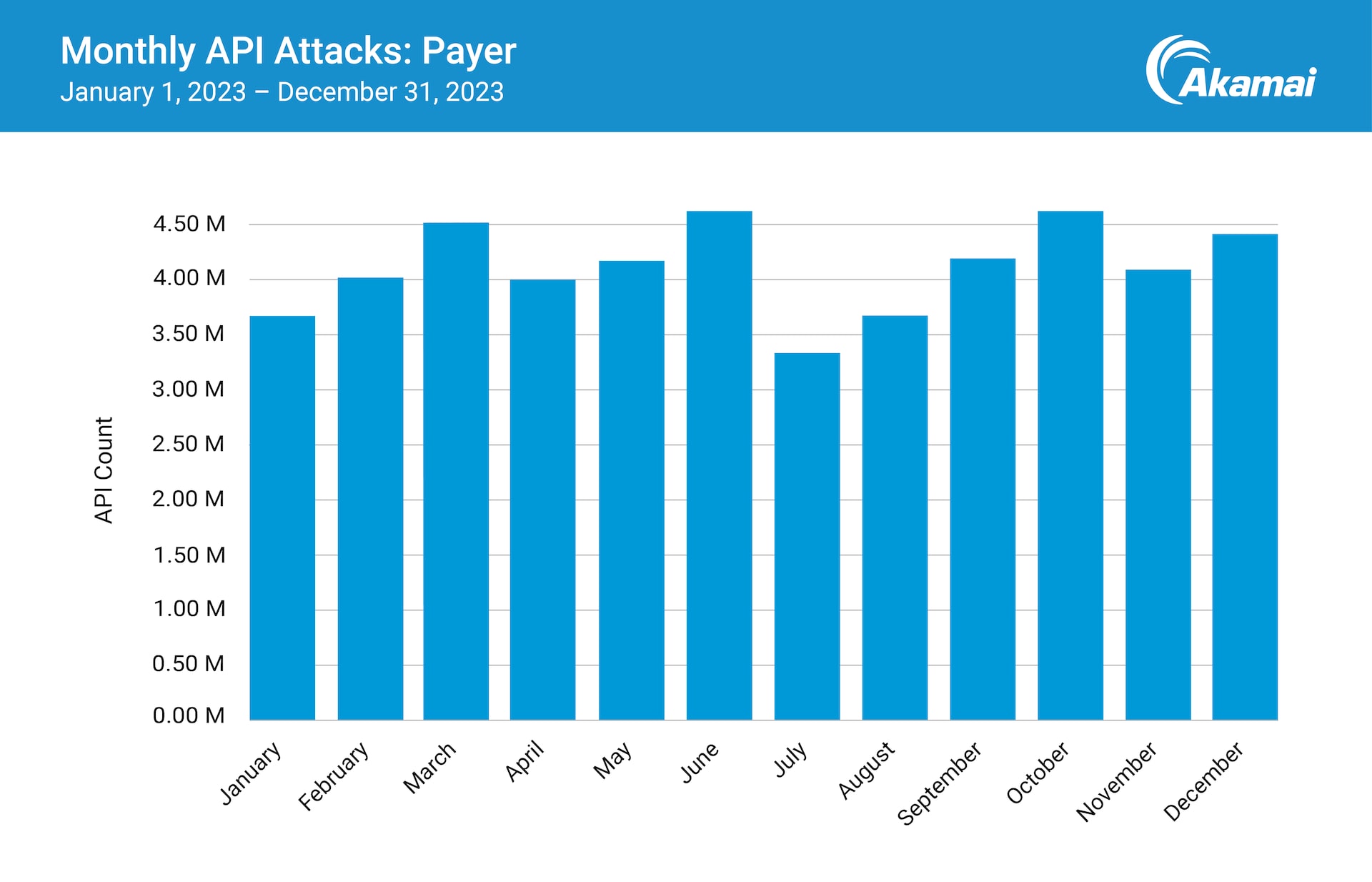
By looking more closely at payer API attack data, Akamai researchers observed fluctuations in activity during the year, particularly quarterly. This may reflect syncing at the end of the quarter among systems to reconcile predicted and actual data.
However, the spike in activity observed by Akamai researchers at the beginning of Q4 2023 and an overall increase in activity during that period can likely be attributed to attackers targeting open enrollment periods to disrupt operations (Figure).
The regulatory landscape increasingly requires APIs
The promise of better financial and clinical outcomes via data exchange and the need to comply with regulatory requirements that mandate said exchange go hand in hand. What’s important is to understand both aspects — and optimize for both aspects.
The move toward value-based care (VBC), a longitudinal approach that rewards health outcomes over appointment volumes, is a prime example of the amount and variety of information that now needs to be shared. Payers have long held access to patient and provider financial data. But more VBC data points, like medication adherence and hospital admissions, require a continuum that’s not only more innovative but more interoperable — and require a means to share this data. APIs are the conduits.
There are not currently any regulations that specifically address API use or security but there are a number of existing regulations that include API requirements, such as the General Data Protection Regulation (GDPR), The European Union’s revised Payment Services Directive (PSD2) and the Payment Card Industry Data Security Standard (PCI DSS).
The requirements for APIs are evolving quickly. Notably, the March 2024 PCI DSS v4.0 includes new standards on the use of APIs in the development and maintenance of systems and software to reduce the risk of compromise.
And, a new CMS Interoperability and Prior Authorization Rule requires payers to maintain three main categories of APIs.
Patient Access API: This will increase members' access to their own medical data and likely enhance member satisfaction
Provider Directory API: This allows members to search for healthcare providers and facilities based on their location and medical specialty, enhancing access to care
Payer-Provider and Payer-Payer APIs: These can help address and reduce patient care gaps and possibly cut duplicative and costly services
The larger intent is to reduce expensive administrative burdens — especially the manual processing of prior authorizations that can mean patients have to wait for their insurance company to approve certain medical procedures before they are performed. Delays can result in adverse (and often costly) medical impacts.
Administrative complexity — including prior authorization processes — costs the U.S. healthcare industry $265.6 billion annually."
Better performance may equal bigger risk
Performance is becoming a bigger concern as patients are expecting the same level of user experience across all their applications. This means the healthcare ecosystem needs to be protected from denial-of-service attacks as well as abuse attacks.
While payers’ high use of APIs delivers tremendous benefits, it also introduces risk. API sprawl can lead to a lack of visibility that becomes murkier as the attack surface expands. APIs are often part of complex digital transformation projects, so they may not be on the radar for healthcare organizations — security programs, even less so. (There are, however, some great reference standards, like the OWASP Top 10 API Security Risks).
Compounding the challenges for payers, the types of data — both medical and financial — involved in daily business activities are both highly regulated and liable to be targeted by cybercriminals.
Defending the ecosystem with visibility
API security is more important than ever from a risk management and compliance perspective. However, because of API sprawl, it’s increasingly complex to identify, catalog, and protect healthcare APIs.
Four strategy milestones
Adopting a strong API security program helps you improve visibility into all your APIs and understand your exposure to risk, so you can ramp up protection. Here are four strategy milestones for a strong API security program.
Remove infrastructure blind spots by systematically discovering rogue or shadow APIs, and ensure that each one is either decommissioned or incorporated into API security controls.
Determine and harden risk posture by analyzing common alert types and correcting flaws in API code, addressing misconfiguration issues, and implementing processes to prevent future vulnerabilities based on lessons learned.
Sharpen threat detection and response by understanding normal behavior and identifying potential abuse based on spikes in API security alerts. Then, engage well-defined response procedures to bring risk and alert volume down to normal levels.
- Develop a stronger offense by establishing a formal API threat hunting discipline with the goal of identifying possible threats before they escalate to a reactive scenario.
Now is the time to act
Transformation will never stop, but now is the time to get APIs under control. Resilient healthcare organizations need capabilities to provide situational awareness, facilitate investigations, and execute rapid response.
Learn more
Learn more about how Akamai partners with healthcare and life sciences organizations to enhance their security programs.