Reaching the Convergence of Security and Productivity

It’s all too common that IT security tools and practices come at the cost of productivity. Even physical security has this trade-off. There would be no rush to arrive at the airport an hour early if it weren’t for the extensive security measures that flying entails. As a result of this trade-off, our concern often isn’t if we can increase security in our networks — rather, it’s if the increased security is worth the impact on the business.
We must also consider the risk vs. reward implications when adopting new business-enabling technologies. After we decide that a new technology is of value to the business, we then have to decide if that value outweighs the expanded attack surface and, in turn, the breach risk that comes along with it. Because of this, a constant tension between security and IT teams has become a given. But this doesn’t have to be the case.
In the April 2022 platform update, we’ll dive into the ways in which Akamai is building a future of work in which its customers can embark on a Zero Trust journey that minimizes breach risk while accelerating business productivity. Reaching this convergence of security and productivity begins with tackling the challenges that are commonly associated with implementing Zero Trust principles.
The dark side of Zero Trust
Analysts, vendors, and security professionals have offered plenty of perspectives on what “Zero Trust” means and how to achieve it. The one thing that we all seem to agree on is that it is a strong foundation on which security teams can minimize breach risk and impact. However, it’s easy to agree on the ideal end state of Zero Trust without delving into the details on how to get there and what impact it may have on the business.
Consider Zero Trust to have an end state at which you “zero out” any implicit trust within the environment that creates risk but doesn’t facilitate work. I think we can all agree on how amazing that would be; there would be no room for attackers to abuse vulnerabilities in our systems or to introduce new malware.
The dark side of Zero Trust comes into view when we consider everything that must happen to get to that end state. We have to consider the journey to Zero Trust and not just the destination. A lack of focus on the journey itself is a large part of the reason it’s rarely put into practice. There are a few key points to think about as we highlight this journey.
Productivity slowdowns
The first is the impact on employee productivity, either by accident or design. A fundamental aspect of Zero Trust is restricting access, primarily through denylisting. This is the practice of dictating what can happen; everything else is denied by default. As we decrease an attacker’s ability to carry out their malicious campaign, we often increase the likelihood of accidentally preventing someone from being able to do their job.
It is unlikely that a security team can foresee each and every possible scenario in which assets and people must communicate with one another. Furthermore, businesses and workforces evolve and change in unpredictable ways. IT and security teams must account for scenarios in which trust is not granted, but should be.
Another potentially harmful implication of enacting Zero Trust principles are slow-downs in productivity that are accounted for. Added identity checks, agents that burden workloads and end-user devices, and tools that end users must log into are just a few of these. Each one on its own may well be within our tolerance. However, when we consider the stacked impact of these minor hindrances, they can reach the point where they are no longer worth the value that they provide.
The need for multiple touchpoints
The last but not least of the pain points in the Zero Trust journey that we’ll discuss is the impact on security teams, and their integrators, architects, and analysts. Currently, there is no single product on the market that can facilitate the Zero Trust journey on its own. As a result, security teams need to maintain policy across multiple consoles, roll out multiple agents, and maintain multiple integrations.
This is a difficult task for even the most well-staffed security teams, and can incur substantial costs in both dollars and people-hours. This final issue compounds the first two by increasing the likelihood of false positives as well as the number of agents and tools that begin to burden end users.
An asymptotic pursuit
It’s also worth noting that the pursuit of true Zero Trust is actually asymptotic; we can get close, but removing every iota of implicit trust is likely an impossibility. Especially if we expand our thinking on exactly where we can invoke Zero Trust principles.
For example, consider a supply chain attack in which we have a trusted user downloading and launching a trusted application from a trusted source. Current definitions of Zero Trust would allow this to happen and the malicious payload is able to bypass all our zones of trust. In that case, we might consider a need for Zero Trust applied to the endpoint, within memory … but that is a conversation for another day. The point is that while perfect Zero Trust might be an impossibility, and moving closer to our goals might involve several pain points, it is very much a worthy endeavor because it offers a future of work in which minimizing risk and maximizing productivity go hand in hand.
In today’s post, we’ll discuss how Akamai is working toward helping businesses make this vision a reality. With each step along the journey, we can reduce the likelihood of a catastrophic breach without disrupting the business. With the wide adoption of Zero Trust as the desired end state, it is now incumbent on security vendors like Akamai to make these steps achievable by more businesses, rapidly, and without any negative consequences such as those mentioned above.
Bridging the gap between vision and reality
Zero Trust means allowing only what is needed for a business to operate, and prohibiting everything else. Making the distinction between necessary and unnecessary actions and then acting on them with precision is at the heart of the Zero Trust journey. Without the right tools in place, this is nearly impossible. As a result, businesses allow more than is necessary and are left exposed to too many risks, or they prevent more than they should, which inhibits productivity.
Daunting as this task might be, there are ways to remove implicit trust with such precision and granularity that end users won’t even notice. Furthermore, if done correctly, this can minimize the attack surface to the point where adopting new technologies is safe and all business-enabling actions are trusted. Security and productivity will converge such that Zero Trust both minimizes breach risk and impact while simultaneously enabling the workforce. But how do we make this future of work a reality?
Three key components of achieving Zero Trust
There are three key components to getting to Zero Trust without having to realize its dark side. These are:
Visibility
Understanding
Control
We need real-time and historical visibility of all of our assets and their respective flows. We need to understand what is happening and why. And, finally, we need to act on this understanding with precise and granular control.
Visibility means providing the security admin a view into the various assets, flows, applications, and users from which we are trying to remove implicit trust. This visibility needs to be broad enough to cover the various operating systems, devices, and other aspects of our network.
Next, we have to understand the function of that which we now have visibility. Only with this understanding can we accurately delineate between what is required and what is not. Context, guidance, and visualizations allow us to understand what should and should not be happening, what is required for the business, and what is creating risk.
Once everything can be seen, and we understand what is happening, we can begin to remove implicit trust. Granularity and precision are key here. For example, some processes are required for normal operations but have services that are not required, which adversaries will abuse. In this case, we need to be able to enforce policy at the service level. A broad stroke policy at the machine or even application layer would lead to false positives.
The tools of the trade
As it stands, no one tool can offer the enforcement capabilities required to root out all implicit trust in our networks such that we can reach Zero Trust. To combat this, Akamai is building the most complete portfolio of Zero Trust products with a roadmap that shows these tools fully integrated.
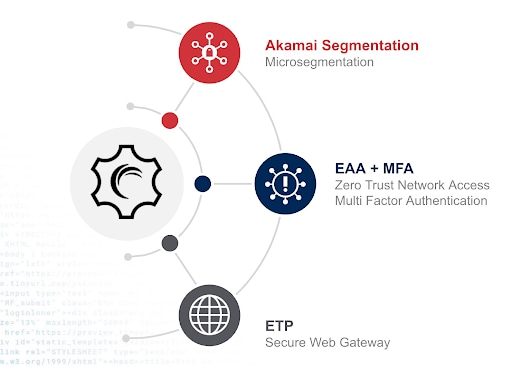
Microsegmentation
Akamai Guardicore Segmentation is the world’s leading microsegmentation solution and acts as a key facilitator of Zero Trust by allowing control of flows inside the network. Akamai acquired Guardicore in large part because the product exemplifies the core tenants that Akamai considers paramount to Zero Trust.
The broadest coverage of supported operating systems with real-time and historical views into the network offers unparalleled visibility. Flexible labeling and an intuitive UI enable easy understanding of dependencies within even the most complex environments. And guided policy enforcement down to the application and even service level means precise and granular control.
In the April 2022 platform update, we’re not only introducing Akamai Guardicore Segmentation to the portfolio in general, but also a host of improvements to the product itself that drive further simplicity, security, and coverage. We’ll shine a spotlight on a few features such as ransomware mitigation templates that enable service-level control to easily stop advanced ransomware techniques.
Zero Trust network access and multi-factor authentication
Akamai Enterprise Application Access provides users with true Zero Trust–based access to only those applications they need and drastically reduces the attack surface by eliminating the need to allow access to, and visibility of, the entire network.
Akamai MFA complements Enterprise Application Access’s authentication capabilities by adding FIDO2 multi-factor authentication (MFA) to secure the user. Unlike other FIDO2-based MFA solutions that require physical security keys, Akamai MFA uses a smartphone app, which reduces cost and complexity.
We strongly recommend always combining Zero Trust Network Access (ZTNA) with FIDO2-based MFA. We’re not alone: The U.S. government has also realized that deploying MFA is critical to help improve the country’s cyber resilience. In May 2021, President Biden issued an executive order that mandated the use of MFA for all federal agencies, and in January 2022, the U.S. Office of Management and Budget provided much more detail that the MFA service deployed should be phish-proof and based on FIDO2 standards.
This seems to be a sensible approach given the well-documented security weaknesses of MFA solutions that use short message service (SMS), other telephony methods, or standard push notifications as a second factor for users, and that are generally considered phishable and much less secure.
Addressing increasing cyberattacks
Over the past year, we have seen another driver for MFA among our customers: With ever-increasing cyberattacks, many businesses are now investing in cyberinsurance. Increasingly, insurance companies are now explicitly stating in the policy’s terms and conditions that companies need to deploy MFA on all local and remote logins to meet the conditions for insurance coverage.
This is most likely in direct response to the number of claims that they have received over the past few years that could have been prevented if the company had MFA in place: further evidence that employee logins are being targeted by attackers.
Delivering a strong phish-proof factor
As companies start to think about moving to passwordless authentication, replacing one weak authentication factor with another weak factor such as SMS does not solve the problem. FIDO2-based Akamai MFA provides a strong phish-proof factor that is critical to providing the expected security benefits that the elimination of passwords should deliver.
Together, Enterprise Application Access and Akamai MFA deliver a strong Zero Trust access solution to provide access to private corporate IT resources.
In the April 2022 platform update, we’re introducing various improvements to Enterprise Application Access and Akamai MFA to increase deployment flexibility and interoperation with neighboring threat protection technologies. Enhancements across platforms means Enterprise Application Access now supports a number of key enhancements to help with Zero Trust security across a wider range of platforms. These include the ability to detect Cylance AV and Microsoft Defender on MacOS as part of a device posture assessment. In addition, our SCIM integration with Okta and Microsoft Azure AD is now going through certification and validation by those organizations. Plus, we have released a technical preview of an Enterprise Application Access client on Ubuntu for customers to test and validate, in anticipation of a full client release later in 2022.
Akamai MFA now supports context aware policies to provide adaptive MFA based on the IP address of the user’s network, where the user is located (geolocation) and if the user is known or unknown. When used in conjunction with Enterprise Application Access, this new capability improves security access by ensuring that you are providing Zero Trust access to only the right users.
In addition, Akamai MFA now supports virtual private network (VPN) server integration, which allows Akamai MFA to be integrated into VPN authentication flows and user provisioning from on-premises AD/LDAP directories.
Secure web gateway
Akamai Secure Internet Access Enterprise is our cloud-based secure web gateway that is designed to help security teams ensure that users can securely connect to the internet from wherever they happen to be or from the device they are using. This quick-to-configure and easy-to-deploy solution requires no hardware installation or maintenance and represents another crucial building block in a Zero Trust–based architecture.
Secure Internet Access Enterprise utilizes up-to-the-minute threat intelligence data and multiple payload analysis engines to only allow your employees access to benign web content. The threat intelligence is based on Akamai’s unprecedented visibility into internet traffic, including 3.3 trillion DNS requests that are resolved every day by the Akamai Intelligent Edge Platform, traffic logs from other Akamai security, CDN services, and hundreds of third-party security feeds.
Introducing multi-tenant management
In the April 2022 platform update, we’re introducing multi-tenant management, which allows service providers, ISPs, and MSSPs to easily manage individual customer configurations. To help identify and block web pages that use obfuscated JavaScript to evade detection, we’re adding a zero-day malicious JavaScript detection engine that can identify and block newly created malicious JavaScript-based pages in real time. For increased deployment flexibility, we're adding new ways to forward traffic to Secure Internet Access Enterprise, including a managed HTTP Forwarder and IPsec tunnel support.
The countdown to Zero (Trust)
Most people will agree that a state of Zero Trust, in which all entities are untrusted by default and least privilege access is enforced, will minimize the likelihood and impact of breaches. However, too few are shedding light on the implications of working toward this state, and how it may negatively impact your business. Even fewer are offering achievable steps for getting there. This is why Akamai is dedicated to building a future of work in which more businesses can reach a state of Zero Trust with more efficiency.
Today, the penultimate day of the platform update, we’ll expand on Akamai’s suite of solutions that are enabling Zero Trust. For Akamai, that means deep and broad visibility of all entities. It means understanding their functions through intuitive visualized mapping and rich context. And, finally, it means precise and granular control so that when it is time to enforce Zero Trust policy, you can stop only that which is creating risk so that business-enabling technologies can be embraced without fear.
What’s next?
In this future of work, Zero Trust is achievable by more businesses, more rapidly, and in a way that reduces risk and accelerates the business. Stay tuned for our final day, where Ari Weil will share what this future means for you.



