Retrospective 2020: DDoS Risk Higher Than Ever

Never before has the risk of a distributed denial-of-service (DDoS) attack been higher. In 2020, we saw record-breaking attacks, a DDoS extortion campaign impacting thousands of organizations globally, more emergency customer support, and more Akamai customers attacked than any year on record -- and we've been successfully fighting DDoS attacks since 2003! We also saw a big increase in attacks targeting verticals that haven't seen as much activity of late, with 7 out of the 11 industries that we track seeing peak attack counts in 2020.
What drove this second renaissance of DDoS activity? DDoS risk profiles changed rapidly with the onset of COVID-19 as we increasingly relied on digital solutions in reaction to the global pandemic. Rapid online movement, combined with toolset improvements that made it easier to launch high-volume, complex DDoS attacks, created a perfect storm for the biggest year in DDoS since 2016. Politically-driven DDoS attacks haven't gone away, but they have been eclipsed by other motivations.
One threat leads to another
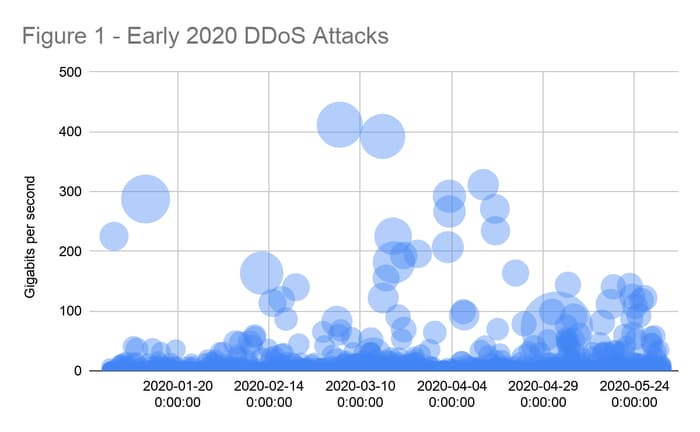
We entered the new year with sizable DDoS attack activity -- a steady number of large attacks but nothing earth-shattering or highly unusual. Then, very large attack sizes (think over 100 Gbps) started to dramatically increase, with the timing of the surge (not surprisingly) mapping to the beginning of the COVID-19 epidemic in Europe and the U.S., when online activity became critical. Organizations shifted focus on protecting virtual private network (VPN) connections and communication endpoints more than "generic" data centers, as their security postures rapidly evolved. As businesses across all industries adapted to remote work and increasing reliance on the internet, more of them became attractive and lucrative targets for DDoS threat vectors.
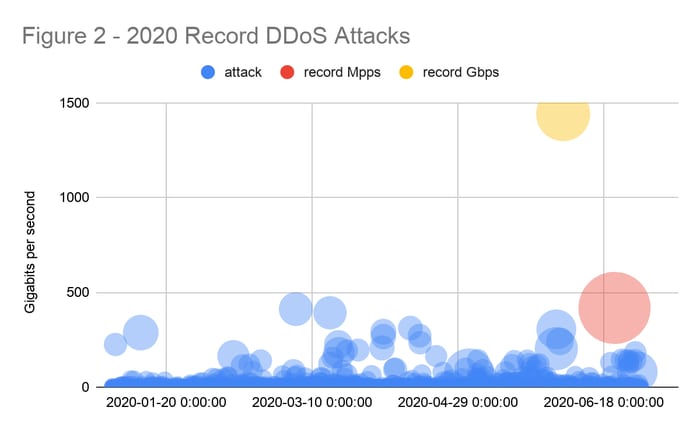
Then only a few months later, Akamai saw threat actors launch record-breaking 1.44 Tbps and 809 Mpps attacks against a large European bank and an internet hosting customer, which are considered higher risk targets for DDoS activity because of their respective verticals. The massive Tbps attack was also highly complex, featuring nine different attack vectors and multiple botnet attack tools requiring a mix of automatic and human mitigation techniques to successfully block the attack vectors.
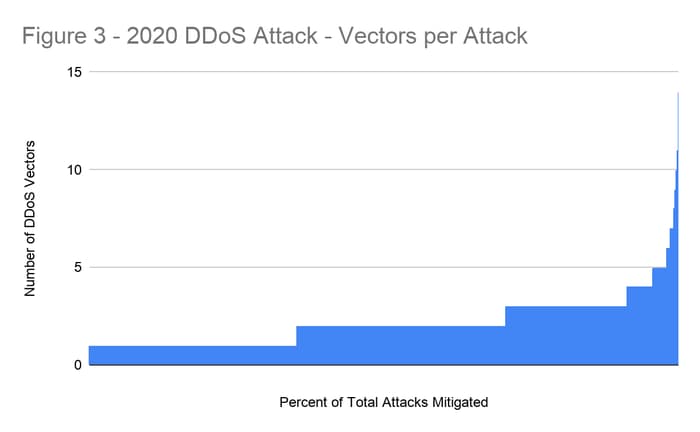
Looking back on 2020, 65% of the DDoS attacks we mitigated featured multi-vector assaults. In addition, as many as 14 different DDoS vectors were noted in a single attack.
The extortion campaign felt around the world
In mid-August, things really started to heat up when Akamai began to observe extortion-related DDoS campaigns that quickly exploded to become the largest of their kind. Unlike previous extortion events from years past, where there was a lot of talk and not a lot of action, this campaign featured show-of-force attacks upward of 500 Gbps -- a sign the criminals were very determined and highly capable of causing disruption.
A notable characteristic of this campaign was the level of reconnaissance conducted by the attackers prior to sending the extortion letters. The bad actors were highly targeted in their threats and wanted victims to know that they had uncovered specific weaknesses across internet-facing infrastructure or had identified revenue-impacting IPs that would be taken offline unless extortion demands were met.
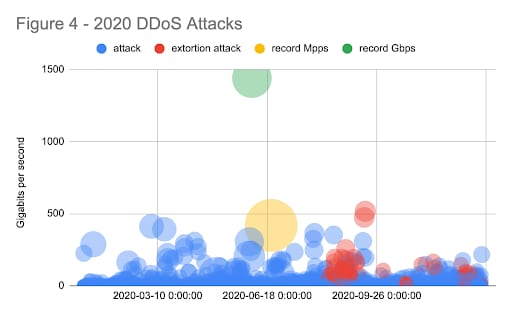
The 2020 campaign also signaled a significant shift in the types of industries targeted -- a foreshadowing of future DDoS activity -- with the threat actors pivoting from one vertical to the next, depending on the week, and in some cases circling back to organizations that had been previously victimized. As is the case with extortion, criminal rings won't stop until arrests are made, and the fact that the extortion campaigns are ongoing indicates that businesses are caving to their demands, which further incentivises the activity.
We continue to see extortion-related attacks, resulting in record emergency onboarding of new customers, a signal that the problem seems likely to persist well into 2021. Check out our DDoS Extortion Battle Plan for proactive tips on how to improve your defensive posture.
DDoS got even bigger and badder
As the extortion campaign set the DDoS world on fire and put a variety of industries on high alert, we then continued to track and observe another uptick in large attacks (> 50 Gbps) that started to surge with COVID-19-related activity.
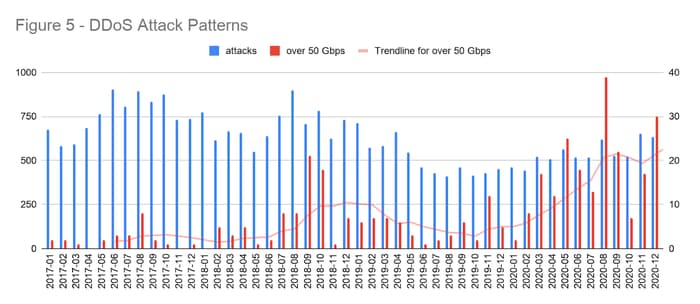
Somewhat hidden in the broader trend, we also noted a big jump in the number of customers seeing large DDoS attacks. This was a cross-industry phenomenon and consistent with the depth and breadth of verticals impacted by the extortion campaign.
Clearly, the increase in risk driven by the pandemic made DDoS an attractive vector for bad actors to continue to leverage during the back half of 2020. Adding to this threat pressure, the steady advancement and accessibility of DDoS attacker tools, combined with increasing internet speeds, allowed both seasoned and less sophisticated actors alike to launch large, complex, and disruptive assaults. We surmise that this contributed to the trending increase in attacks over the 50 Gbps threshold, as well as to the increase in overall attack volume.
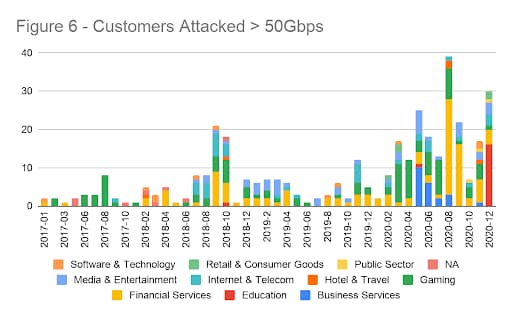
In fact, across all attacks, 7 of the 11 industries we track saw more attacks in 2020 than in any year to date. Think about that. This activity was led by huge jumps in Business Services (960%), Education (180%), Financial Services (190%), Retail & Consumer Goods (445%), and Software & Technology (196%).
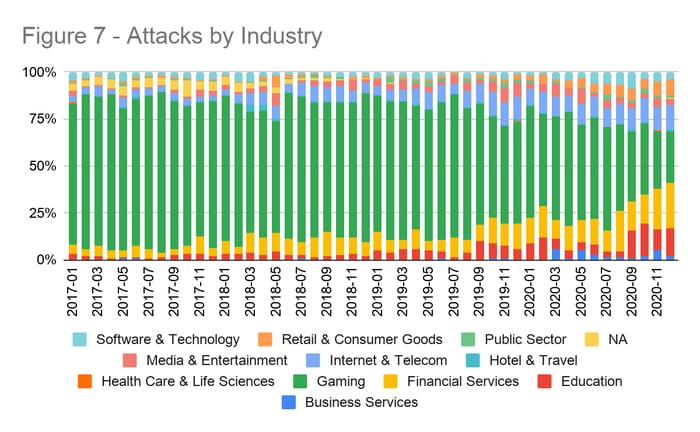
Just when we thought the worst was over...
The flurry of DDoS activity and increasing threat pressure led to perhaps the most interesting records of 2020. We had more customers attacked in November 2020 than in any prior month and more customers affected by DDoS attacks sized over 50 Gbps in August. Both of these records go back to the heyday of DDoS in 2016. Neither trend shows any signs of abating.
The increase in the number of customers attacked continued even after we started seeing fewer extortion attacks against existing customers on our DDoS mitigation platforms. We were made aware of extortion-related activity through emergency-onboarded customers that had been attacked, or were under the threat of an impending attack, and needed protection as soon as possible.
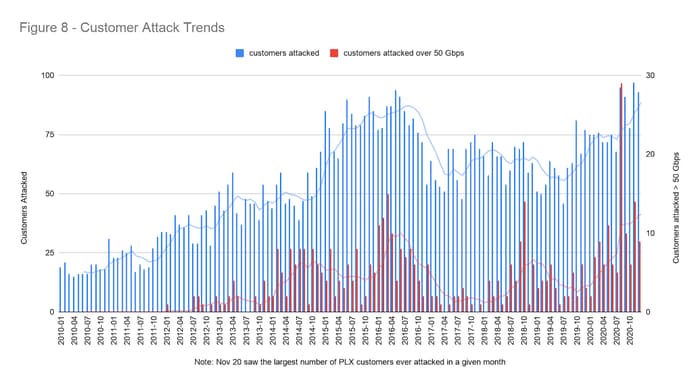
Therefore, it didn't shock us when threat actors showed up in full force during Cyberweek 2020, the prime shopping season of the year. This particular week was overloaded with pent-up online shopping demand waiting to be unleashed as consumers faced pandemic lockdowns and restrictions. And criminals took notice, intent on causing disruption by stepping up attack activity.
During Cyberweek 2020 alone we saw:
65% more attacks launched against our customers than during Cyberweek 2019
The number of customers targeted was up 57% year over year
Attacks were launched across an expanded industry base
These stats are similar to what was witnessed with the latest DDoS extortion campaign and reflective of broader trends for the year -- more customers in more industries seeing attacks.
What’s next?
The DDoS landscape rapidly shifted and evolved throughout 2020, and many organizations now realize that procuring DDoS defenses is the cost of doing business today. While we can't make any definitive predictions on record attacks or DDoS campaigns, history has shown that ultra-large DDoS attacks often raise the bar, attacker motivations shift, and extortion campaigns are generally cyclical in nature. Leaning in, we can expect to see more attack activity throughout 2021 as the nature of DDoS continues to advance and evolve.
If you are currently under DDoS attack or threat of extortion, reach out to the Akamai DDoS hotline, 1-877-425-2624, for immediate assistance.
For more technical details and additional DDoS-related resources, please see the following blog posts and materials:



