Multiple Extortion: An Existential Threat
This blog post was updated on 07/19/2024.

In today's increasingly vulnerable digital landscape, companies across the globe face unprecedented security challenges. Medium-sized organizations in particular aren’t always well prepared to defend against malicious actors. Multiple extortion stands out among these growing cyberthreats as a particularly dangerous risk that demands immediate attention.
What is multiple extortion?
Executing a ransomware attack has traditionally involved infiltrating an organization’s IT systems, encrypting sensitive data, and demanding a ransom for its release.
However, cybercriminals are increasingly expanding the scope and scale of their threats with the inclusion of a sophisticated three-pronged ransomware attack approach known as multiple extortion.
Encryption of sensitive information: The initial phase of the attack involves infecting IT systems with ransomware, rendering critical data inaccessible. This puts immense pressure on the organization to act swiftly to regain control of its assets.
Data exfiltration and threat of leakage: In addition to encrypting data, attackers extract sensitive information and threaten to leak it online. This poses a grave threat, as the exposure of sensitive company, personal, or customer information can lead to reputational damage, legal repercussions, and financial losses.
DDoS attack threat: To compound pressure on the targeted organization, cybercriminals may threaten to launch a distributed denial-of-service (DDoS) attack. This technique aims to overwhelm the organization’s network infrastructure, making its online services unavailable to legitimate users. DDoS attack threats amplify the organization’s urgency to comply with the attacker’s ransom demands, and may be used to distract the victim while the attacker executes other attack vectors.
Cyberattackers use multiple extortion because it’s a more compelling and holistic threat than simply encrypting data that victims can recover with a backup.
The severity of multiple extortion attacks across industries
Healthcare is particularly vulnerable
Healthcare institutions, among other important industries, are particularly vulnerable to multiple extortion attacks because of the sensitivity of patient healthcare data. In January 2023, the hacktivist group Killnet launched a DDoS attack against 14 medical centers across the United States.
Attackers like Killnet know healthcare institutions rely on timely access to patient data and operational systems, making those victims more likely to comply with ransom demands under pressure. By stealing, encrypting, and threatening to expose protected patient data, the attackers put human lives at risk and force organizations to make quick decisions that may compromise patient care or violate privacy regulations.
Cyberattacks against critical infrastructure
The Colonial Pipeline attack in May 2021 — the largest publicly disclosed cyberattack against critical infrastructure in the United States — is another prominent example of multiple extortion. A cybercriminal group known as DarkSide successfully infiltrated Colonial Pipeline to encrypt company systems and exfiltrate significant amounts of sensitive data: all to make a compelling case for their demanded ransom payment.
The success of this attack led to widespread fuel shortages and highlighted the dire impacts of multiple extortion attacks on infrastructure and the economy, and even compelled President Biden to declare a nationwide state of emergency.
The threat to SMBs
It’s a common misconception that only large enterprises are targets for multiple extortion attacks. The reality is that small and medium-sized businesses typically lacking in robust security infrastructure are equally, if not more, vulnerable. In fact, cybercriminals increasingly target smaller organizations to exploit system vulnerabilities from weak security investments and encrypt and demand ransoms for their critical data.
Medium-sized organizations, in particular, face a tough dilemma: pay the ransom and risk financial strain or refuse to comply and face potential data leaks along with potential operational disruptions. With potentially limited security resources and expertise, but the ability to pay a ransom, these organizations are more at risk of succumbing to pressure from multiple extortion attacks.
Safeguard employee access to resources with ZTNA
To mitigate risks associated with multiple extortion attacks, companies of all sizes and across industries should prioritize the protection of employee access to enterprise resources. Implementing end-to-end Zero Trust Network Access (ZTNA) can drastically reduce a company’s vulnerability (Figure 1).
ZTNA provides identity-based access control that surpasses traditional firewall and VPN solutions that are seen as woefully inadequate for addressing today’s more threatening cyberattacks. ZTNA solutions take a “never trust, always verify” organizational safeguarding approach to ensure safe and granular access to resources based on user identity, device security posture, and contextual factors.
 Fig. 1: Zero Trust relies on strong authentication and authorization for every device and every person
Fig. 1: Zero Trust relies on strong authentication and authorization for every device and every person
Fortify organizational security using MFA
Businesses should further fortify organizational security by adopting multi-factor authentication (MFA) solutions that incorporate additional verification layers beyond traditional username and password combinations (Figure 2).
MFA significantly raises the bar for cyberattacks that use phishing, credential abuse, and identity theft to gain access to corporate systems. It is highly recommended to deploy a solution that provides phishing-proof FIDO2-level authentication, ideally coupled with smartphone apps for a seamless user experience and without the need for costly hardware tokens.
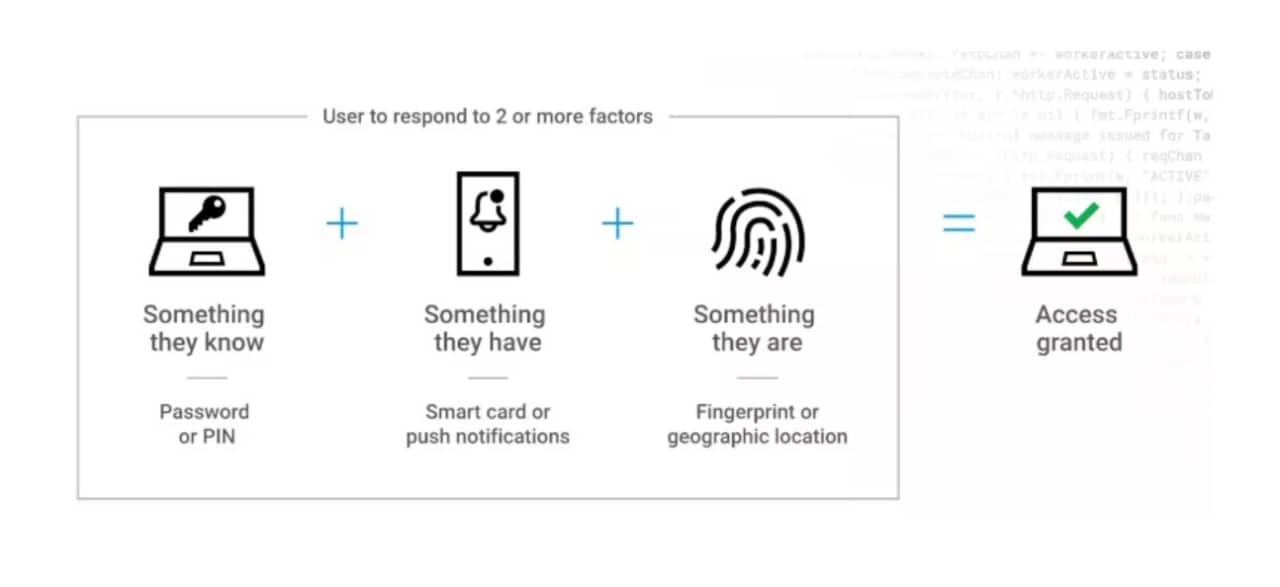 Fig. 2: MFA’s layered approach to verifying a user’s identity ensures that if one of the authentication factors is compromised, then there are additional barriers to prevent access
Fig. 2: MFA’s layered approach to verifying a user’s identity ensures that if one of the authentication factors is compromised, then there are additional barriers to prevent access
Defend infrastructure against evolving threats
Protect your digital network infrastructure from DDoS attacks
To protect network infrastructure, companies must stay one step ahead of cybercriminals. A robust, flexible and comprehensive DDoS protection platform can provide effective protection against DDoS attacks and malicious traffic threats, wherever an organization needs it (on-prem, in cloud, or hybrid) and however they need it (always on or on demand).
Secure your DNS
The Domain Name System (DNS) plays a similarly crucial role in network infrastructure. To ensure uninterrupted availability of servers, applications, APIs, and other network resources, companies must secure their DNS. Protection against DDoS attacks and manipulation ensures the integrity and resilience of the DNS infrastructure to safeguard against service disruptions and unauthorized access.
Mitigate threat with purpose-built solutions
As cybercriminals continue to evolve their tactics, multiple extortion attacks pose an existential threat to companies of all sizes. The combination of data encryption, data leakage threats, and the possibility of DDoS attacks creates a high-stakes environment for targeted organizations.
Akamai Prolexic
Akamai Prolexic is a purpose-built DDoS protection platform that is available on-prem, in the cloud, or as a hybrid of both. Prolexic Cloud is powered by advanced automation, machine intelligence, and a global network of several cloud scrubbing centers across 32 global metro areas and more than 20 Tbps of dedicated defense capacity.
The keyword to note there is “dedicated” — unlike some solutions that piggyback on their content delivery network capacity, thereby offering cybercriminals a single point of defense to overcome. To put Prolexic’s defense capacity in perspective, even the largest known Layer 3 and Layer 4 DDoS attacks don’t make up 10% of the capacity available to Prolexic customers.
Prolexic Network Cloud Firewall
Prolexic also extends your defenses beyond DDoS with Prolexic Network Cloud Firewall. Customers can quickly, centrally, and globally block traffic that they don’t want to hit their networks or certain targets within their networks. Prolexic Network Cloud Firewall also recommends access control lists for the best proactive defense posture based on Akamai’s threat intelligence data, and delivers actionable analytics of existing rules.
As a next-generation firewall as a service (FWaaS), Prolexic Network Cloud Firewall empowers customers to:
- Define proactive defenses to block malicious traffic instantly
- Alleviate local infrastructure by moving rules to the edge
- Quickly adapt to network changes via a new user interface
Akamai Edge DNS
Akamai Edge DNS offers a comprehensive, purpose-built, cloud-based authoritative DNS solution that uses the scale, security, and capacity of Akamai Connected Cloud to distribute your DNS zones across several thousand servers across the globe.
Customers delegate their zone authority to Edge DNS by updating nameserver records at the registrar and using those provided by Akamai. Edge DNS provides an unparalleled attack surface and proactive security controls that can mitigate even the largest DNS attacks without impacting a customer's DNS performance, reliability, and availability.
Akamai Shield NS53
Akamai Shield NS53 is a bidirectional DNS proxy solution that protects key components of your origin DNS infrastructure from resource exhaustion attacks. Using an intuitive user interface on the Akamai Control Center, you can self-configure, administer, manage, and enforce your organization’s specific dynamic security policies in real time. Illegitimate DNS queries and DNS attack floods are dropped at the edge of the Akamai network, keeping your DNS secure, reliable, and available.
Akamai App & API Protector
Akamai App & API Protector is a single solution that brings together many security technologies, including web application firewall (WAF), bot mitigation, API protection, and application layer DDoS defense. App & API Protector is recognized as the leading WAAP solution for swiftly identifying and mitigating threats beyond the traditional WAF to protect entire digital estates from multidimensional attacks. The platform is easier to implement and use, provides holistic visibility, and automatically implements up-to-date, customized protections via Akamai Adaptive Security Engine.


