Introducing Guardicore Cyber Threat Intelligence

Security teams are always on the lookout for trusted information sources to help them make sense of the suspicious IP addresses or domains they see in their security tools logs. Even if one of their tools has reported a malicious IP address, in many cases they are still missing the context in which the IP operated in – what type of malicious activity this IP was involved in, what other IoCs are associated with the attack coming from this IP etc’. This type of information could help them see the ‘bigger threat picture’ and fine tune their defenses against the threat they face.
Guardicore Labs is announcing the release of Cyber Threat Intelligence (CTI), a freely available resource to assist security teams in identifying and investigating malicious IP addresses and domains. Our Cyber Threat Intelligence is designed to allow security teams to keep track of potential threats that are specific to data center and cloud infrastructure. Guardicore CTI leverages Guardicore Global Sensor Network (GGSN), a network of sensors installed in multiple data centers around the world.

Who can benefit from this data
Security analysts, threat hunters, incident response and SOC teams can leverage Guardicore CTI to verify threats, understand attack patterns, and collect attack-related Indicators of Compromise (IoCs). For advanced research, teams can gain more insights from the Attack Flow section that places the malicious IP or domain into full context and allows them to assess the full scope of the attack. Unique to Guardicore Cyber Threat Intelligence, the Attack Flow walks you through all the major breach and post-breach operations in the same order they were executed by the attacker. This includes information on which services were targeted, files downloaded as part of the attack, associated IPs and domains and more.
Cyber Threat Intelligence updated weekly
Our Threat Intelligence dashboard provides a weekly summary of top attackers, attacked services and malicious domains. Users can browse and download a file consisting of this data and explore their environments for potential threats.
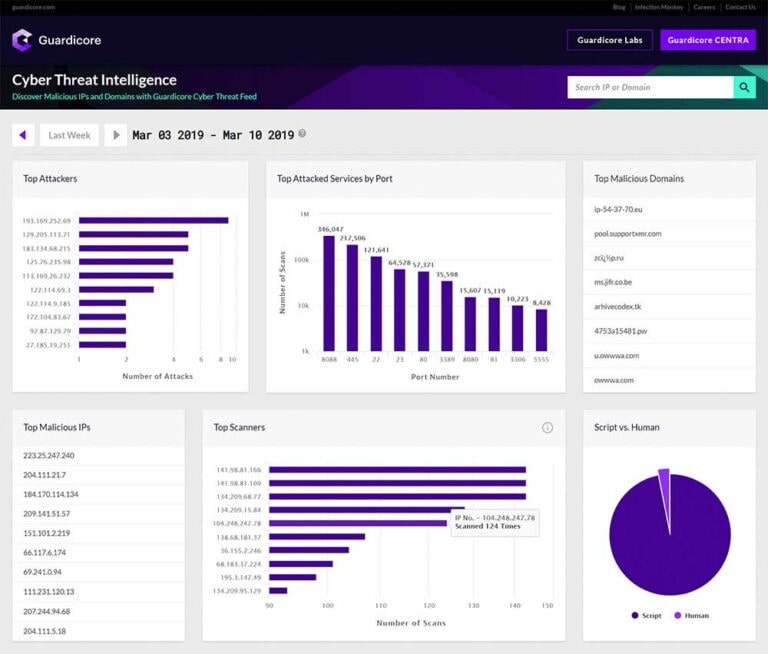
With Guardicore Cyber Threat Intelligence you can:
- Search for suspicious IP addresses and domains during an attack investigation
- Search through your network logs for top attackers and top malicious domains and IPs for signs of an active attack
- Investigate a security incident with our Attack Flow to get all the IoCs associated with a suspicious IP/domain
Let’s see how Guardicore Threat Intelligence helps you investigate a suspicious domain.
Problem: you noticed outgoing traffic from one of the servers in your data center to the domain name down.1226bye[.]pw. How can you tell whether this communication is legitimate or not?
Guardicore CTI analysis: A search for this domain name in the Guardicore Threat Intelligence dashboard will lead you to a dedicated domain page:
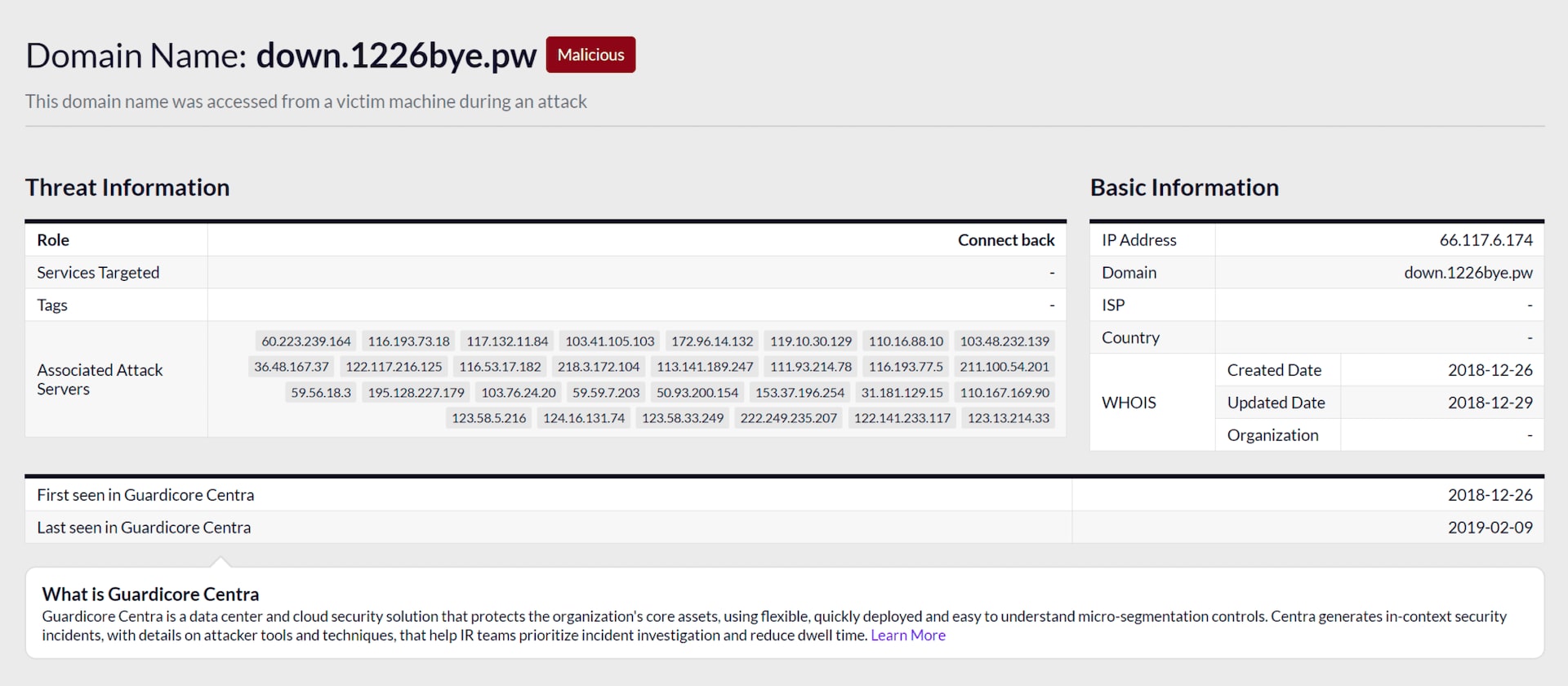 Guardicore CTI page for down.1226bye[.]pw
Guardicore CTI page for down.1226bye[.]pw
Basic Information pane
The right-hand pane provides the domain name, country of origin, name of Internet Service Provider (ISP) and WHOIS information. The Associated Attack Servers pane on the left displays the list of attackers this domain communicated with. Clicking a random IP address on the list, say 117.132.11[.]84, opens a dedicated page that features key information we gathered on this IP address.
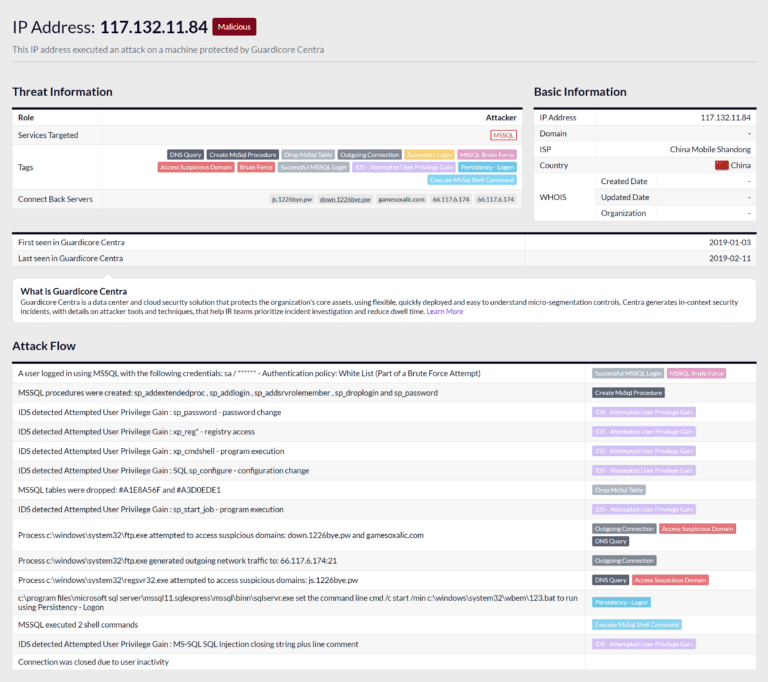 Guardicore CTI page for 117.132.11[.]84
Guardicore CTI page for 117.132.11[.]84
Threat Information pane
Role. First thing we can learn here is that this IP was playing the role of an Attacker. Roles include Attacker, Scanner and Connect-Back. An IP assigned with the Attacker role uses penetration techniques such as brute force password guessing and exploits known and unknown (zero day) vulnerabilities. Once the machine has been compromised, these attackers execute a wide range of attack tools to establish their control over the victim machine and attempt to further propagate across the network. A Scanner IP is a machine that accesses one or more services across one or more subnets monitored by Guardicore sensors without performing attacks. The Connect-Back role refers to a machine that attackers connect to after breaching a server. These machines usually serve as file servers to download post-breach tools such as Remote Administration Tools (RAT), C&C servers and logging servers to send data from the victim’s machine.
Services Targeted. This IP has targeted MS-SQL servers.
Tags. These are the highlights of the attack. We see that this attacker has been tagged with brute force password guessing, creating custom MS-SQL procedures and making outgoing connections and more.
Attack Flow pane
This part features the exact steps the attacker took to breach the MS-SQL server along with post-breach actions. The Attack Flow section walks you through the story of the attack:
- The attacker brute forced his way into an MS-SQL database
- Next, the attacker performed a sequence of malicious operations, such as changing passwords, executing shell commands using the xp_cmdshell plugin and changing the configuration of the database.
- Last, the attacker executed external commands, which had communicated with external servers, among them the domain name we started the investigation with – down.1226bye[.]pw.
Guardicore Labs cyber researchers also source Guardicore’s network of sensors (GGSN) to analyze attack campaigns. Examples include Prowli, Hexmen, Butter.
Why share this info?
We believe that sharing information and knowledge about threats helps the security community to improve its defenses and be better equipped to protect organizations and users. We invite the cybersecurity community to contribute to our CTI knowledge base by submitting data, asking questions and collaborating with Guardicore researchers on additional findings.






