How To Protect Your Systems Against Critical SMB Vulnerabilities (CVE-2020-0796)

Microsoft has issued its latest set of cumulative updates for Windows for the month of March. There are a total of 117 vulnerabilities, 25 of which are rated critical
One particular vulnerability stands out from the crowd: CVE-2020-0796. This is a critical vulnerability in the Server Message Block (SMB) protocol in new versions of Windows operating systems. This SMB vulnerability could cause a wide range of wormable attacks and potentially a new Eternal Blue. Without going into the gory details, a flaw in the new SMBv3 compression mechanism potentially allows an attacker to take down or take over a Windows system.
- Windows 10 Version 1903 for 32-bit Systems
- Windows 10 Version 1903 for ARM64-based Systems
- Windows 10 Version 1903 for x64-based Systems
- Windows 10 Version 1909 for 32-bit Systems
- Windows 10 Version 1909 for ARM64-based Systems
- Windows 10 Version 1909 for x64-based Systems
- Windows Server, version 1903 (Server Core installation)
- Windows Server, version 1909 (Server Core installation)
Advisories on this CVE suggest patching your systems (which you should be doing regardless) as well as “Block TCP port 445 at the enterprise perimeter firewall,” which should be the case in any network. If you can’t patch your Windows system, you can manually disable the SMBv3 compression feature. That is the root of all evil in this case.
Set-ItemProperty -Path
"HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters"
DisableCompression -Type DWORD -Value 1 -Force
Why Are SMB Vulnerabilities Problematic?
SMB vulnerabilities are not more common than any other Windows vulnerability. The SMB protocol is amazingly useful, but also one of the easiest ways to move laterally in an organization’s data center. All an attacker needs to do is gain access to one system in order to spread across the whole data center. In fact, the WannaCry campaign and EternalBlue vulnerability are great examples of how an SMB vulnerability can have a wide and crippling impact on organizations worldwide.
The question that many ask is, “How do SMB vulnerabilities still happen if we patch and deny all the SMB traffic from external networks?” Moving from theory to reality, we know that not 100% of hosts get patches. In fact, most companies are still struggling with this basic task today. In addition, networks are complex animals that can’t simply be wrangled by placing a box in an arbitrary location.
Moreover, the main reason for widespread damage in most SMB-related incidents we’ve encountered is the fact that hosts within the network can freely move laterally on any port (and specifically on 445 AKA SMB). There is no real justification for allowing this type of behavior inside the network. SMB inside the network should usually only be allowed to communicate with the DC and, in some cases, dedicated file share and backup services. In most cases, servers shouldn’t be communicating with one another over SMB.
So why not just deny the SMB traffic? The answer is that it’s hard for organizations that rely on legacy technologies like gateway firewalls. These tools only enforce traffic going between network zones, not what’s inside.
How Can SMB Vulnerabilities Be Stopped?
One of the first things we recommend to our customers is to improve their network hygiene by implementing basic best practices policies. For example, you can allow only DC, backup, and files SMB traffic. The rest of the traffic should be blocked, regardless of VLANS or network topology. More explicitly, you should deny lateral SMB traffic.
Guardicore Centra helps prevent SMB vulnerabilities by providing a simple and fast way to create and apply policies across the network. These policies allow only legitimate SMB traffic, while blocking the rest of the lateral movement between the hosts.
For example, see how this screenshot demonstrates how only legitimate SMB traffic is allowed within the network:
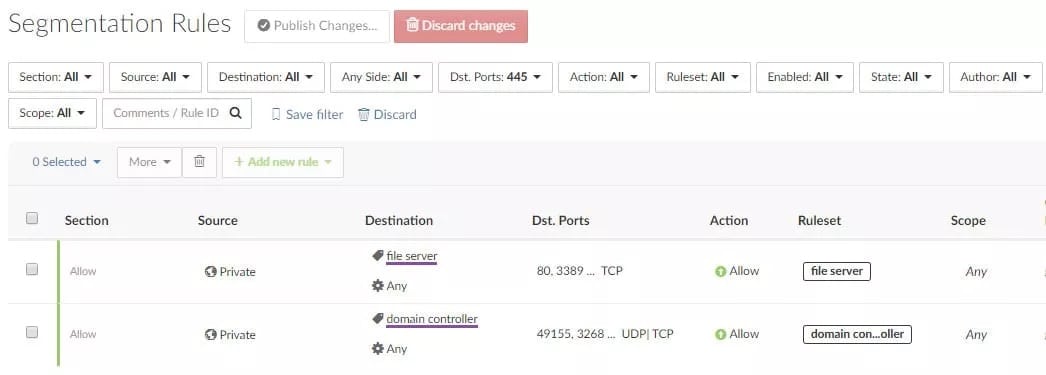
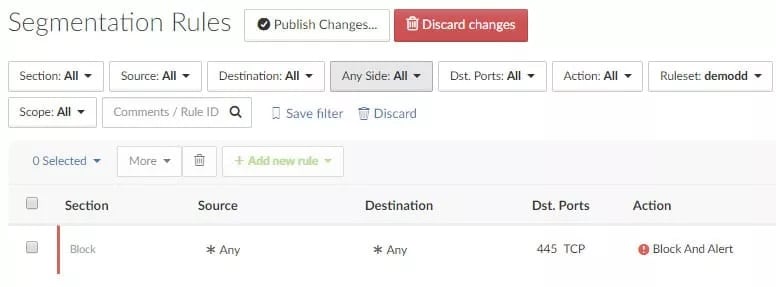
And here, Centra blocks the rest of the 445 traffic:
Conclusion
A simple common protocol like SMB can pose a great risk to the datacenter. However the risk of SMB vulnerabilities can be easily mitigated with three rules. Simply apply segmentation policies using a tool like Guardicore Centra to prevent lateral SMB traffic inside the datacenter.
Contact us to learn how to reduce your attack surface and prevent lateral movement with fast and simple segmentation that works everywhere.



