Entering Through the Gift Shop: Attacks on Commerce

Executive summary
Akamai sees a huge number of attacks across all our security tools. In the latest State of the Internet/Security (SOTI) report, we share what we see in terms of shifts in malware attacks, customer impacts, regulatory requirements, and emerging threats to commerce. Our report includes these key points:
Commerce remains the top vertical for web application and API attacks, with more than 14 billion attacks — largely due to the industry’s continued digitalization and the availability of web application vulnerabilities that attackers can use to breach their intended targets.
Local File Inclusion (LFI) attacks increased by 314% between Q3 2021 and Q3 2022, showing an attack trend leaning toward remote code execution, and indicating that attackers are leveraging LFI vulnerabilities to gain a foothold and for data exfiltration.
Half the JavaScript that the commerce vertical uses comes from third-party vendors, and this introduces the increased threat of client-side attacks, such as web skimming and Magecart attacks. It is critical to put mechanisms in place that will detect these attacks on payment pages to remain compliant with the new requirements in Payment Card Industry Data Security Standard (PCI DSS) version 4.0.
Attackers can also abuse security gaps in scripts, and as such, can create a pathway to infiltrate bigger, more lucrative targets in supply chain attacks.
In Q1 2023, Akamai Security Intelligence Group observed that more than 30% of phishing campaigns were activated against commerce customers.
Akamai observed more than 5 trillion malicious bot requests in 15 months, with assaults against commerce customers proliferating via credential stuffing attacks that can lead to fraud.
Commerce organizations are challenged with having a complex and dynamic attack surface, as well as troves of sensitive data that criminals want. This post will highlight some of the findings from the recent commerce-focused SOTI report. The report covers the growth in web app and API attacks, changes to the JavaScript environment, trends in bot attacks, and insights on phishing methods.
The struggle: Limited security budgets for a higher need
Although commerce is not as heavily regulated as the financial services or healthcare industries, it needs the same mature security level. Commerce is characterized by a complex ecosystem of infrastructure, including point of sale (PoS) terminals, Internet of Things (IoT) devices, mobile, and leverage web applications and API to drive business further.
Scripts from third-party vendors are often tapped to enhance the overall customer experience and drive conversions on the commerce websites. Tapping these scripts introduces another layer of risks, as most third-party scripts use open source libraries, and attackers could exploit vulnerabilities found in those libraries. We see this trend in Magecart-style attacks in which JavaScript libraries are abused via exploitation of security flaws.
Because retailers hold a huge volume of sensitive data to protect against, we’re also seeing ransomware groups go after them. In our Akamai Ransomware Threat Report, commerce (retail and hospitality) accounted for 16% of Conti’s attacks. This is echoed by another report from Sophos that noted the surging attack rate in the retail industry.
Commerce remains the most-targeted web attack industry vertical and accounts for 34% of Akamai’s observed attacks (Figure 1). Within commerce, retail is still the leading subvertical, accounting for 62% of the attacks.
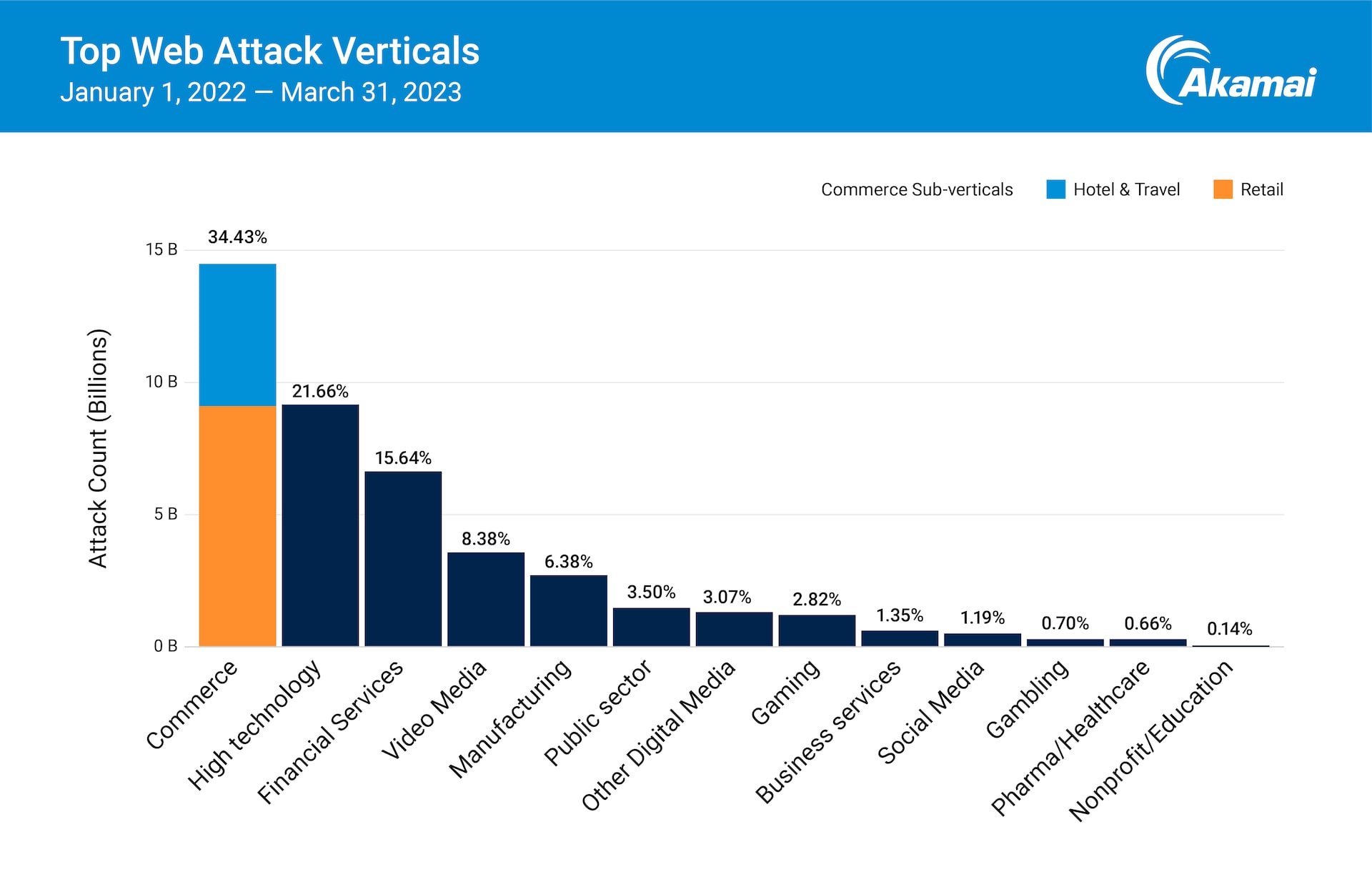 Fig. 1: Commerce remains the most-targeted web attack industry vertical, accounting for 34% of Akamai’s observed attacks; retail remains the leading subvertical within commerce, accounting for 62% of its attacks
Fig. 1: Commerce remains the most-targeted web attack industry vertical, accounting for 34% of Akamai’s observed attacks; retail remains the leading subvertical within commerce, accounting for 62% of its attacks
Although security and IT teams are feeling the pressure of protecting their perimeter and customer information, they are challenged with limited security budgets that require these teams to do more with less.
Attack vectors leading to data breaches and remote code execution
We continue to see shifts in attack vectors, with LFI attacks taking over from Structured Query Language injection and Cross-Site Scripting in the commerce vertical. We have also seen emerging remote code execution attacks; three, in particular, deserve our attention.
Server-Side Request Forgery (SSRF)
Server-Side Template Injection (SSTI)
Server-Side Code Injection
These types of attacks are on the rise because of their potential impact on commerce businesses — the damages caused by them can lead to data exfiltration and remote code execution. SSRF vulnerabilities are being used for maximum damage by ransomware attackers. SSTI appears to be an attacker’s favored technique for zero-day attacks (e.g., Log4J).
Malicious bots and third-party vendor scripts
Attackers are continuously increasing their capabilities and sophistication. This last year, commerce has been experiencing a large increase in malicious bot attacks, surpassing 5 trillion in the past 15 months; this has resulted in a surge in phishing and credential stuffing attacks leading to fraud.
On a second front, scalping operations using botnets are being offered “as a service” and are contributing to the adversarial challenge that bot manager product vendors face, as well as a loss in revenue for retailers.
Finally, we see 50% of commerce scripts are from third-party vendors, creating a larger attack surface and potentially introducing security risks that may lead to supply chain attacks (Figure 2). One example is the Magecart attack that compromised payment information for more than 350,000 customers of a major airline.
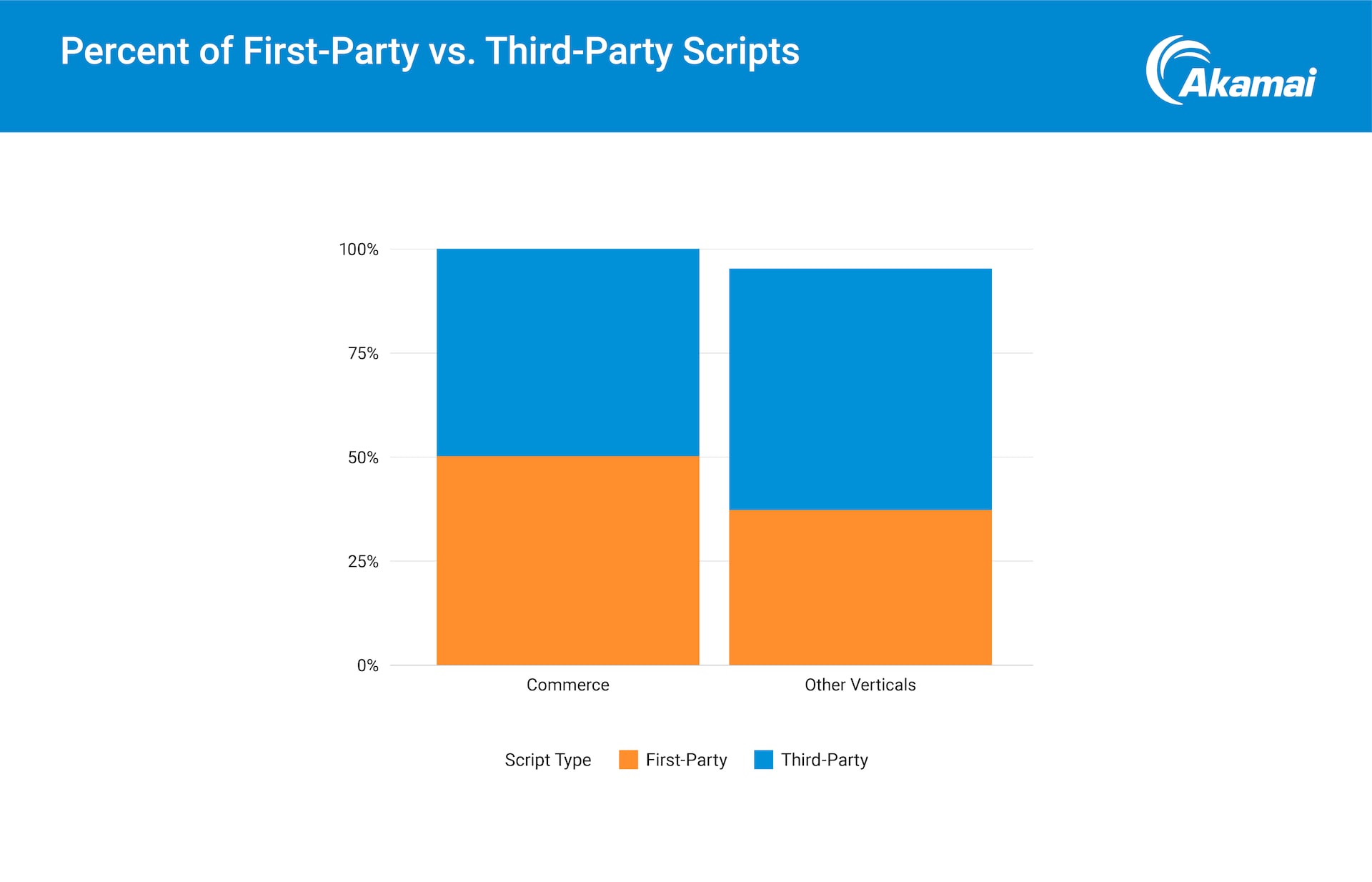 Fig. 2: Fifty percent of the JavaScripts used in commerce websites are from third-parties, compared with 39% for all other verticals that only use third-party vendors.
Fig. 2: Fifty percent of the JavaScripts used in commerce websites are from third-parties, compared with 39% for all other verticals that only use third-party vendors.
Take action
Changes in attack methods require us to update our playbooks and penetration test plans, and to train our developers on best practices. And changes to compliance standards can have long tails, so it is important to develop a plan now to meet new JavaScript requirements (e.g., PCI DSS 4.0).
Download the full SOTI report to see additional details and graphics. The report takes a deep dive into the current state of web app and API attacks, changes in the JavaScript environment, and trends in bot attacks; provides insights on phishing methods; delivers regional breakouts for APJ and EMEA for these categories; and offers recommendations for taking actions based on the findings.
Learn more
Stay plugged in to Akamai’s research and alerts. You will find SOTI reports, blogs about threats and threat protection best practices, and other tools and resources.





