Battling Fatigue: How to Defend Against Relentless DNS Attacks
Fortify your DNS to prevent team fatigue
Domain Name System (DNS) is essential to infrastructure security and enables all digital services for an organization.
Unfortunately, the number of DNS attacks is on the rise across industries and around the world. With one smart distributed denial-of-service (DDoS) attack, cybercriminals can make DNS unreliable, slow, or unavailable — damaging the digital services experience for customers and employees alike. These attacks exhaust the time and energy of IT staff, security administrators, and leaders who are all trying to maintain exceptional customer experiences.
Read on to learn how you can fortify your DNS and prevent staff fatigue by adopting a deterrence through diversity approach.
Common use cases that consume time and energy
As shown in Akamai’s 2023 State of the Internet (SOTI) report, Attack Superhighway: A Deep Dive on Malicious DNS Traffic, DNS attacks powered by malicious entities that use sophisticated and distributed bots and botnets are a growing concern for almost every industry.
One key trend has been the increasing size, frequency, and sustained duration of malicious NXDOMAIN attacks. A 2023 report by the U.S. Health Sector Cybersecurity Coordination Center (HC3) illustrates how cybercriminals are using DNS NXDOMAIN attacks to target critical public infrastructure like healthcare. Figure 1 illustrates the anatomy of an unpredictable NXDOMAIN attack that relentlessly drains essential resources — from the people defending your digital presence to underlying technologies like DNS name servers, firewalls, and global server load balancers (GSLBs).
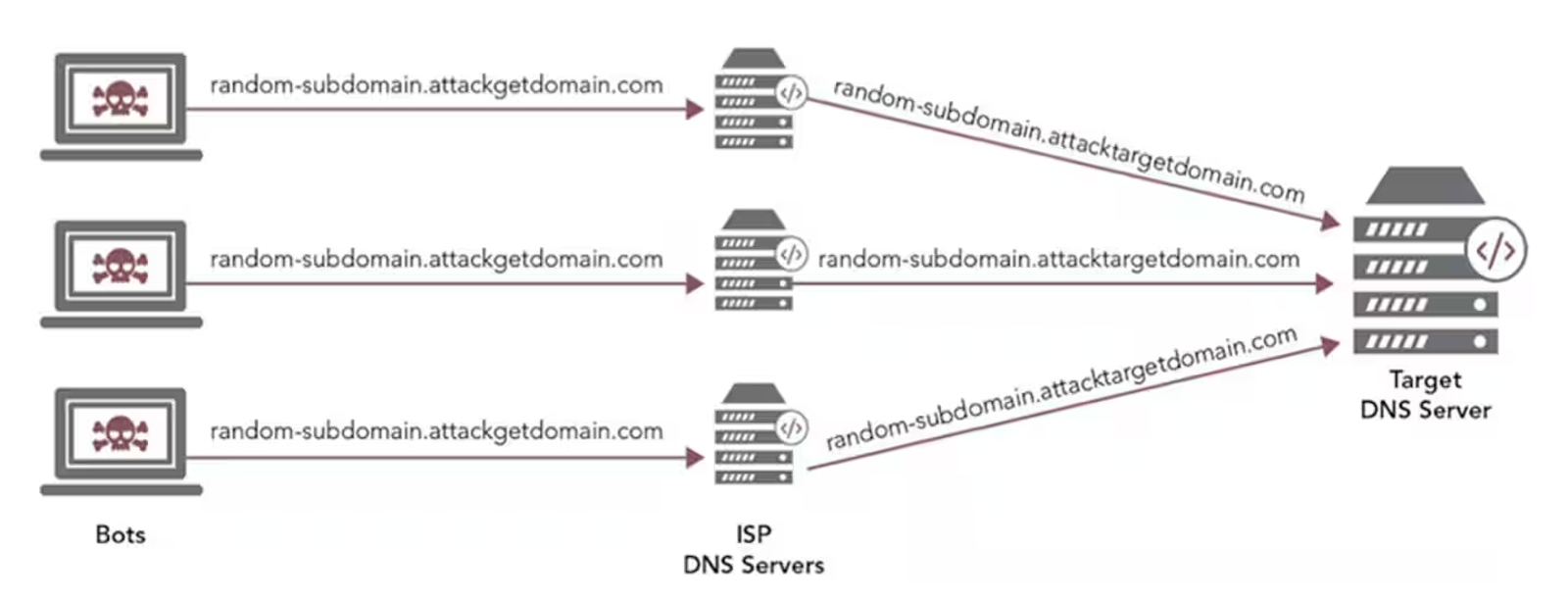 Fig. 1: Anatomy of unpredictable NXDOMAIN attacks on a target DNS server (Source: Akamai)
Fig. 1: Anatomy of unpredictable NXDOMAIN attacks on a target DNS server (Source: Akamai)
During these “DNS flood attacks,” attackers target a domain with nonexistent, randomly generated, prefixed subdomain requests, causing target DNS servers to look up the nonexistent subdomain and reply with a NXDOMAIN response. Normally, internet service provider (ISP) domain servers will place any frequently occurring subdomains in a DNS cache to reduce load on the authoritative DNS server. But by generating random subdomains, attackers ensure that every DNS request goes to the origin, thus overwhelming the service.
While attackers aim to target a business’s DNS service, their attacks can also exhaust resources in the customer environment — including firewalls and GSLBs, which both process DNS queries. These attacks can cause a customer’s firewall or GSLBs to go offline, which can negatively impact the customer's business. DNS resource exhaustion attacks are also known as DNS water torture attacks or pseudo-random subdomain (PRSD) attacks.
PRSD attacks are common across industries like healthcare and financial services. Figure 2 illustrates an example of blocked NXDOMAIN DNS traffic over a one-week period for one of the largest financial services institutions in the world. Attack spikes were observed on several days within the week, and the attacks were often significantly larger than the moving average of legitimate DNS queries (shown via the green part of the chart). In this instance, there were more than 25 million NXDOMAIN queries blocked on May 16. To ensure effective service, systems must have a great capacity to manage these unpredictable surges.
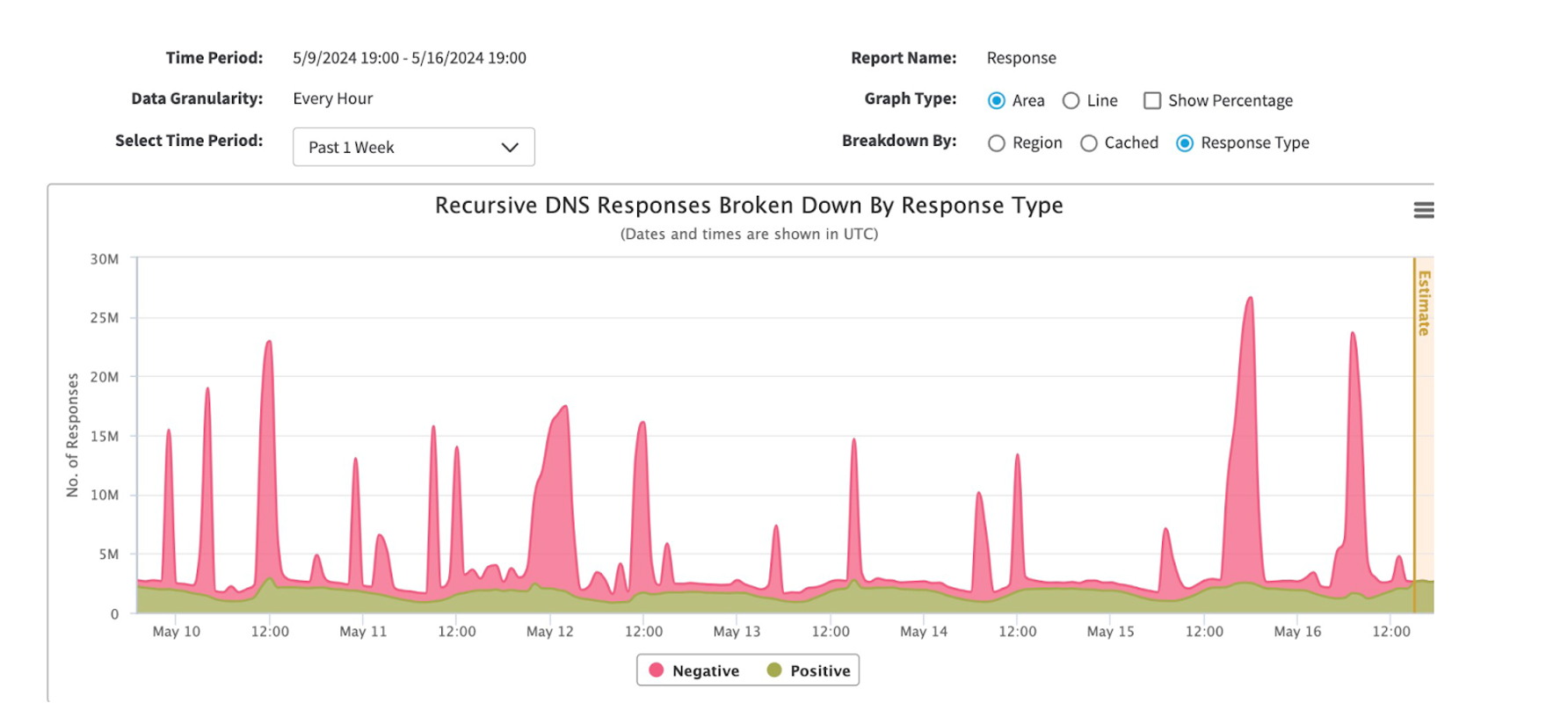 Fig. 2: Illegitimate DNS traffic queries blocked via refusal or NXDOMAIN response over a one-week period (Source: Akamai)
Fig. 2: Illegitimate DNS traffic queries blocked via refusal or NXDOMAIN response over a one-week period (Source: Akamai)
Figure 3 shows how attackers used illegitimate NXDOMAIN traffic in a sustained manner over a one-month period to bring down the DNS infrastructure of a customer. This is a common pattern in which NXDOMAIN attacks are not just a one-off attack but a continuous challenge faced by companies. Akamai successfully prevented the attack by blocking the attack traffic spikes while allowing legitimate DNS queries (as indicated by the relatively flat green section of the chart).
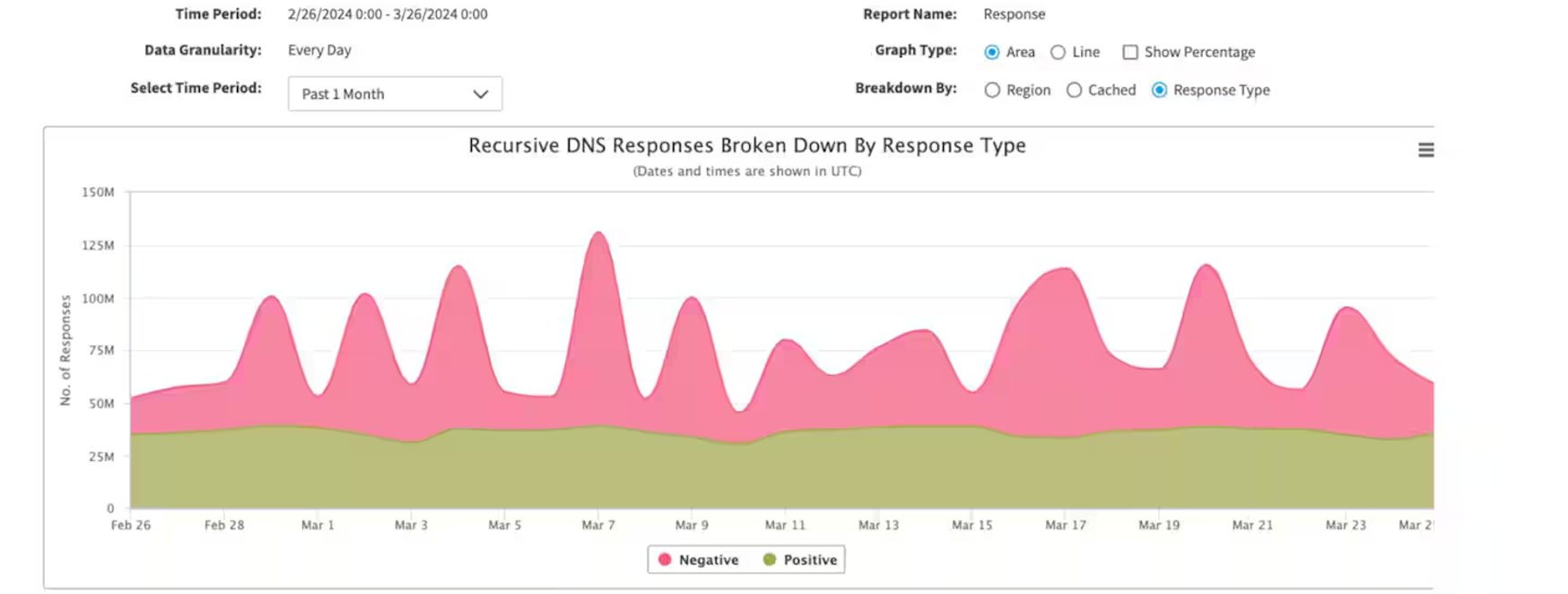 Fig. 3: Common NXDOMAIN response pattern over a one-month period
Fig. 3: Common NXDOMAIN response pattern over a one-month period
Best practices against NXDOMAIN attacks
To prevent NXDOMAIN attacks, your network needs enough capacity to handle high-volume traffic surges. This can be challenging, since it’s often difficult to forecast a surge’s size and duration. One way to sufficiently increase capability is to use elastic services with large amounts of scalable capacity, like an external DNS service. Many leading external DNS services will also announce service from many locations, creating a broad interface or surface area that disrupts attacks with anomalous traffic. By ensuring ample capacity without locking cash into an idle fixed asset, you can help improve return on assets and fund other important projects.
Another key to success is ensuring a DNS system that is managing traffic floods enforces policies like prioritizing queries from allowlisted sources. This can be crucial, as blocking legitimate requests with approaches like DNS response rate limiting can disrupt services.
You can also improve your organization’s NXDOMAIN defense position by varying your surface area implementation. An architect can ensure variance or DNS diversity by using multiple providers or by flowing traffic through DNS systems with unique architectures.
Every service provider will encounter issues. But with multiple providers in an active-active configuration, you can improve system reliability in the event that an attack disrupts a provider.
Establish DNS diversity
To achieve DNS diversity, implementation networks should use Akamai’s IP Anycast technique combined with globally diverse physical name server locations. External DNS services need redundant network links, collocation with ISPs throughout the world, and robust peering arrangements. Other ways to create DNS diversity include:
- Using large, multi-home DNS data centers. Network diversity can be just as important as capacity. Large DNS DDoS attacks can overwhelm upstream ISPs and other networks before reaching a data center, causing congestion and service outages even if the data center remains unaffected. To preserve availability and respond to DNS queries from end users during attacks, the DNS service must deploy name servers into large data centers with sizable capacity and connectivity through multiple networks.
- Colocating DNS name servers inside ISPs. In many cases, DNS name server clusters should be directly in the networks of individual ISPs. These name servers often broadcast their IP Anycast traffic only within those networks and resolve DNS queries only for the end users of those ISPs. While this arrangement limits the number of end users that specific name server clusters can serve, it also preserves availability for those users when an IP Anycast cloud is targeted by an attack outside that ISP. An attacker would need systems on that specific ISP’s network to see those name servers, and available capacity is often only enough to protect that one cloud environment.
- Deploying clients intelligently across the entire global platform. Assign customers to diverse cloud environments, some with ISP-specific server locations and others with a range of connecting machines. This architecture assures a given client’s recursive name servers always connect to a fast DNS edge.
Use unique network paths
The quantity and design of DNS delegations and name server addresses can also impact diversity. For example, using two delegation servers offers two network paths to the authoritative answers, whereas six delegation servers offer six network paths to the authoritative answers. Each name server address has its own routing path in separate geographic locations. For IPv4, this means that each name server address should have its own /24 IP address.
For example, the Akamai DNS delegation server set in the table has six network routes to many locations across the world that can provide an answer.
| TTL | Record type | Record data | IPv4 address | IPv4 /24 prefix |
|---|---|---|---|---|
| 172800 | NS | a1-206.akam.net. | 193.108.91.206 | 193.108.91.0/24 |
| 172800 | NS | a10-67.akam.net. | 96.7.50.67 | 96.7.50.0/24 |
| 172800 | NS | a16-64.akam.net. | 23.211.132.66 | 23.211.132.0/24 |
| 172800 | NS | a5-65.akam.net. | 95.100.168.66 | 95.100.168.0/24 |
| 172800 | NS | a6-66.akam.net. | 23.211.133.66 | 23.211.133.0/24 |
| 172800 | NS | a9-67.akam.net. | 184.85.248.67 | 184.85.248.0/24 |
Table: Akamai DNS delegation server set with six network routes
Use varying implementation stacks
Diversifying your DNS delegation implementations is another way to help prevent DNS attacks. For example, one delegation address may use a DNS proxy server to shield origin name servers, another may use a secondary authoritative DNS service to host zone information that an origin name server transfers, and a third may use network layer policy enforcement to forward only clean and valid DNS traffic to a customer’s origin.
Figure 4 shows how recursive DNS resolvers can interact with DNS proxies that enforce policies, like dropping queries for invalid namespaces. The onboarding workflow is straightforward, involving setting delegations to use Anycast virtual IPs for shield proxies. These delegations direct traffic to the shield that enables malicious traffic mitigation and legitimate traffic green-lighting.
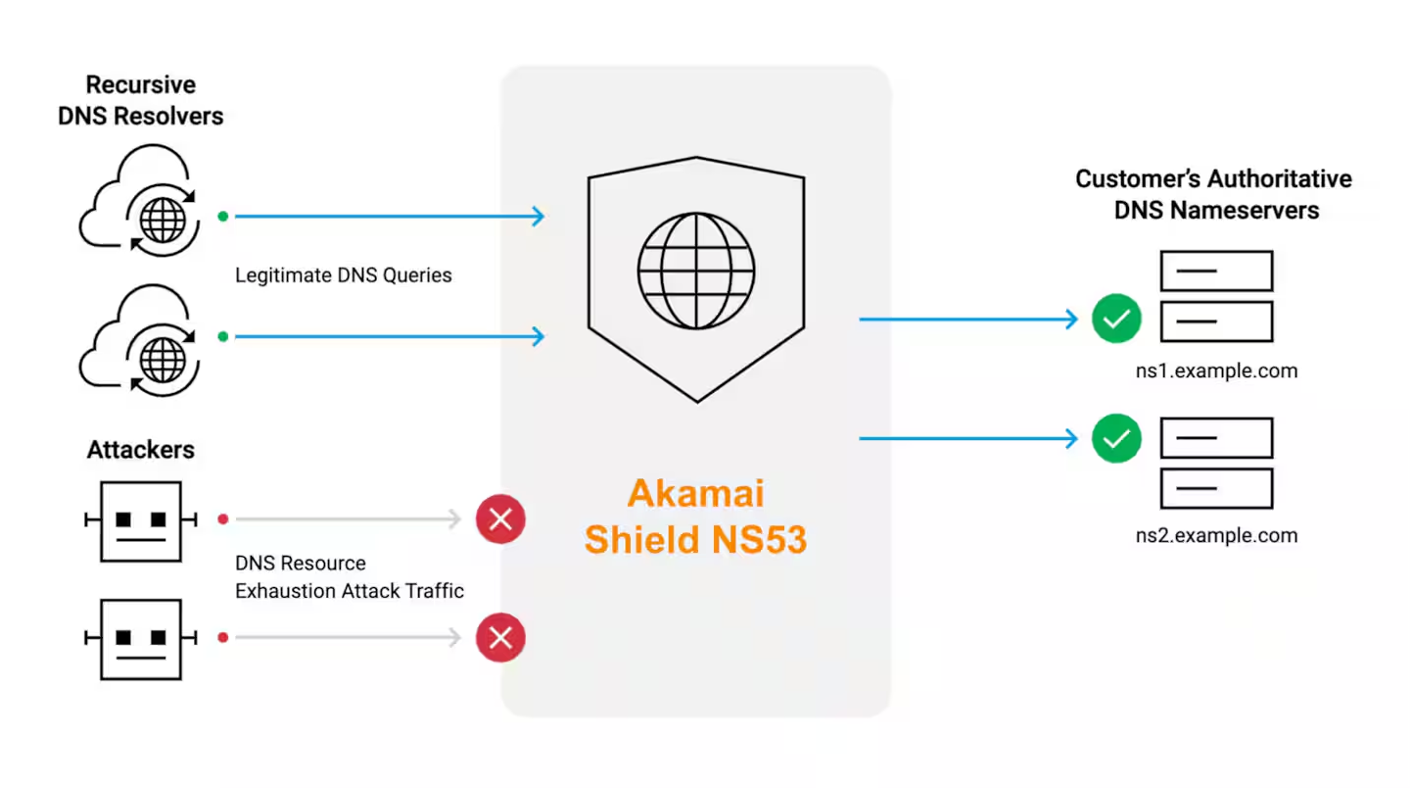 Fig. 4: Akamai Shield NS53 protects a customer’s DNS name servers by allowing legitimate queries from recursive DNS resolvers and denying illegitimate queries from attackers
Fig. 4: Akamai Shield NS53 protects a customer’s DNS name servers by allowing legitimate queries from recursive DNS resolvers and denying illegitimate queries from attackers
Name servers in secondary mode behave similarly by answering queries on behalf of origin name servers. Unlike a DNS proxy, secondary name servers know a zone’s DNS records from zone transfers and answer on behalf of the origin name servers while organizing traffic closer to users and providing scalability and resilient capacity
For a heightened network security posture, domain owners can mask their primary name servers by exclusively delegating zones to a DNS proxy or secondary DNS server and restricting origin name server traffic to only these layers. Transactional signatures (TSIGs) can also be implemented to authenticate zone transfers.
Get your weekends back with DNS protection from Akamai
If you’re concerned about DNS attack resiliency and you lack strong, reliable defense strategies, try deploying protection services like a DNS proxy to shield origin name servers or a secondary DNS service. By doing so, you will expand your current DNS workflow with an additional set of authoritative servers that durably provide answers about your zones while hiding your origin name servers from malicious attackers.
Benefits of this DNS defense approach include:
- Improved customer service
- Increased time to focus on projects that were previously overlooked because of ongoing DNS protection efforts
- Better employee morale, since there are fewer repetitive incidents that consume personal time and cause burnout
Akamai Shield NS53, part of the Akamai Edge DNS suite, helps protect organizations and their customers and employees from hostile types of DNS attacks. This DNS infrastructure and DDoS protection solution offers comprehensive security and unmatched performance to make it fast and easy to find and remedy DNS vulnerabilities on the world’s most distributed edge platform. And with up-to-the-minute threat intelligence and intuitive management features, your IT teams can oversee and self-configure DNS zones while enforcing your own dynamic policies in real time.
Ready to improve your enterprise organization’s DNS security position from end to end? Visit us to learn even more about Akamai Shield NS53 from Akamai Edge DNS.






