Introducing an Effortless Way to Deploy Akamai API Security
There's exciting news for those looking to enhance their security measures by incorporating Akamai API Security into their technology stack. Our new native connector now seamlessly integrates API Security with Akamai Connected Cloud, allowing any Akamai CDN customer to analyze their API traffic easily.
The API Security solution is specifically designed to discover and audit APIs and monitor API activity using behavioral analytics, which makes it an excellent solution for detecting and responding to API sprawl and API abuse. It helps to proactively secure application environments against the OWASP Top 10 API Security Risks, misconfigurations, and design flaws while simultaneously providing API attack protection.
Since the connector is integrated into API Security and the Akamai platform, the API traffic can be analyzed out of band and without latency or risk. In addition, attacker IPs can be blocked directly at the Akamai edge. While the native connector simplifies the integration process with Akamai Connected Cloud, API Security is still vendor-agnostic and can support all your existing platforms, including other CDNs, API gateways, and cloud environments.
From implementation to production in one step
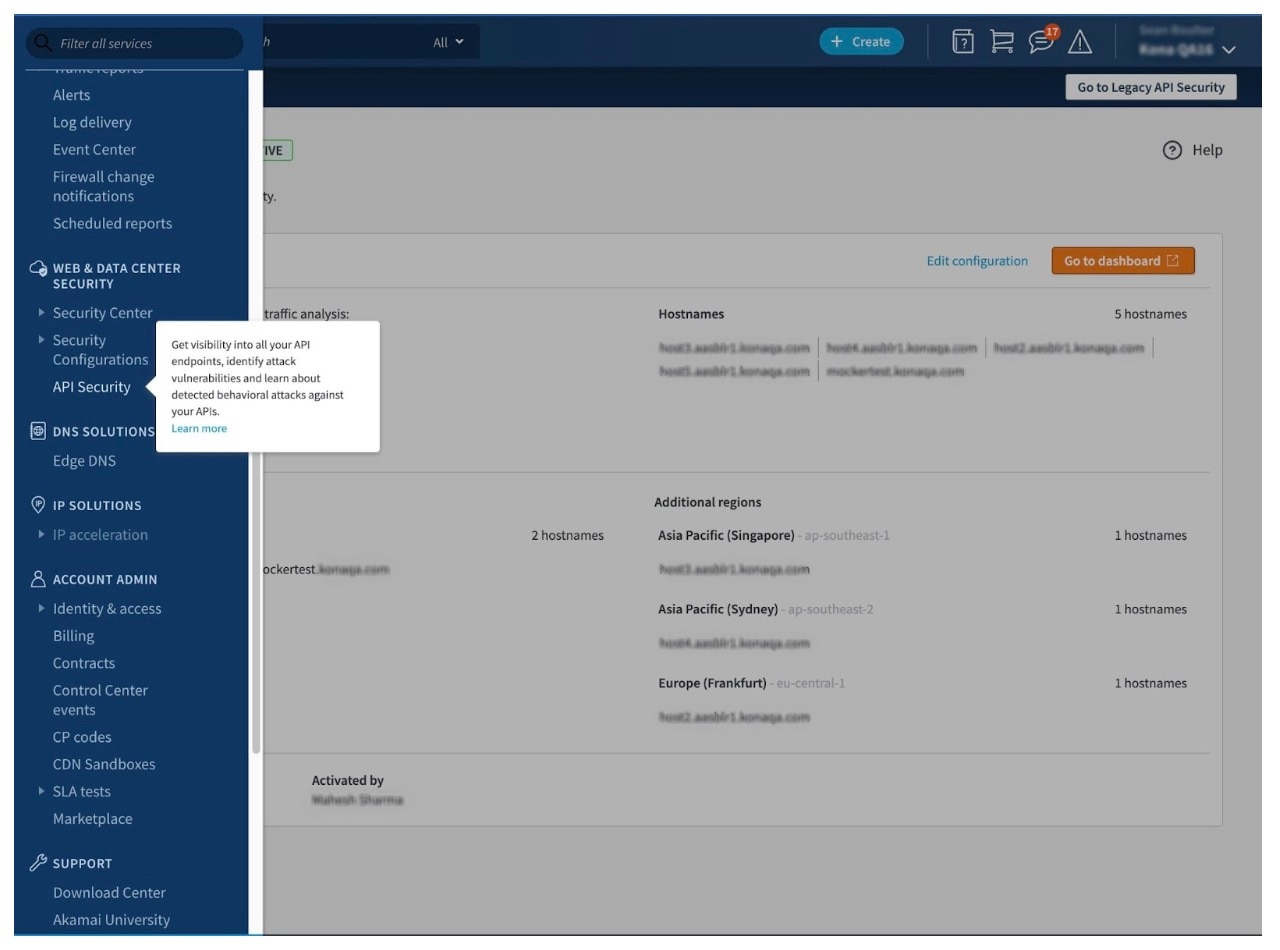
Typically, integrating traffic sources can take hours or even weeks and often requires cross-functional collaboration across multiple security and infrastructure teams. However, with our native connector, you can send a copy of your API traffic data from Akamai into the API Security product with just a few clicks (Figure 1). This allows you to go from implementation to production in one step without risk or adverse effects.
Although other API security solutions have integrated with the Akamai CDN, our native connector is the only one designed, built, and supported by Akamai. As there is no need for implementation, maintenance, networking expenses, or any other ongoing costs, you can benefit from a lower total cost of ownership.
Can you purchase API Security if you’re not an existing Akamai customer?
Yes. API Security is a vendor-agnostic solution that works without the Akamai CDN. It can connect with more than 40 other traffic sources, including third-party web application firewalls, CDNs, API gateways, and cloud environments. In addition to analyzing traffic, Akamai API Security can ingest API information from infrastructure configurations, API test results, API spec files, and more.
Benefits of using the native connector
Our integration stands out as truly unique compared with other API security providers. It offers three distinct benefits that set it apart from other solutions:
Faster ROI with rapid deployment
Reduced total cost of ownership
Rapid attack response
Faster ROI with rapid deployment
Existing customers who use Akamai delivery services can activate the connector immediately in production and go from setup to seeing traffic in minutes, not days. The native connector eliminates the need to assign teams, reshuffle priorities, coordinate resources, or schedule projects.
Reduced total cost of ownership
The native connector is included as part of the API Security solution, requiring no extra on-premises infrastructure or implementation overhead. The connector is fully supported by Akamai and enhanced alongside the API Security product, adapting and scaling to your workflows as your organization evolves.
Rapid attack response
The connector analyzes the copy of your API traffic without negatively impacting performance. It comes with a built-in attack prevention capability that allows you to block high-probability attacks directly in Akamai Connected Cloud.
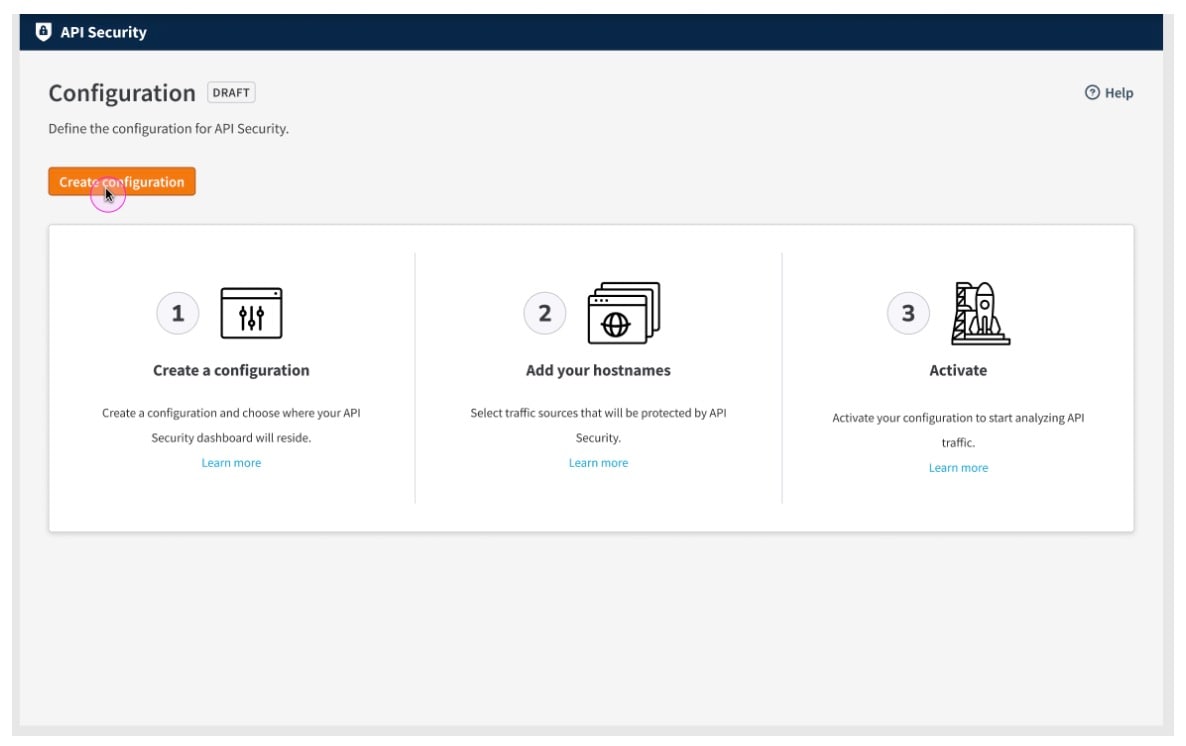
Deploy API Security and a native connector in 3 easy steps
API Security is deployed directly from the Akamai Control Center, which ensures that only users who have the connector can gain Akamai-authorized access to your API activity. It takes just three easy steps to deploy API Security (Figure 2):
Configure the region for your dashboard
Select traffic sources
Click Activate
It’s that simple.
Better together with Akamai App & API Protector
The Akamai API Security solution works alongside our web application and API protection tool, Akamai App & API Protector. This tool effectively defends websites, applications, and APIs by instantly blocking harmful traffic. With best-in-class application security, distributed denial-of-service (DDoS) protection, and bot protection, App & API Protector provides an automated and adaptable cloud-based solution for safeguarding web applications and APIs.
When used together, API Security and App & API Protector offer complete global protection by providing a wide range of features, such as monitoring API behavior and preventing attacks and misuse.
Learn more
For more information on how Akamai API Security can help you, reach out to your account representative or contact an Akamai sales representative.