Have Web Trust Issues? Bot Management Can Help
Executive summary
There are many different kinds of good and bad bots, and it’s important to be able to distinguish whether a bot is helpful or harmful.
Bot management solutions can help organizations allow, block, or take nuanced action against individual bots, depending on their risk index.
Bot management solutions detect bot activity, categorize bot types, respond to bot activity in real time, and monitor results.
These solutions employ several tools and strategies to accurately detect, categorize, and respond to potential bot activity, including IP reputation analysis and device fingerprinting.
Your bot management solution should offer many compelling benefits, like superior bot detection, minimal false positives, and granular visibility and reporting.
Some bots play extremely helpful and important roles. For example, search engines rely on bots that scan websites to understand and index content. But many other bots perform annoying or malicious tasks, like scraping content to gather competitive intelligence, hoarding inventory, driving up fake traffic on a website, participating in DDoS attacks, or gaining unauthorized access to user accounts through credential stuffing.
Additionally, bots are constantly evolving, making it harder for organizations to mitigate malicious bots while allowing good bots to do their work.
Determining who you can trust online with bot management
The rise of bots has made bot management solutions a top priority for security teams everywhere. Bot management is the task of detecting, identifying, and blocking or allowing bots that interact with websites, applications, and networks. With a superior solution, you can understand bots better and apply a strategic approach to managing them — whether you want to allow them, block them, or take more nuanced action with them.
Distinguishing good bots from bad bots
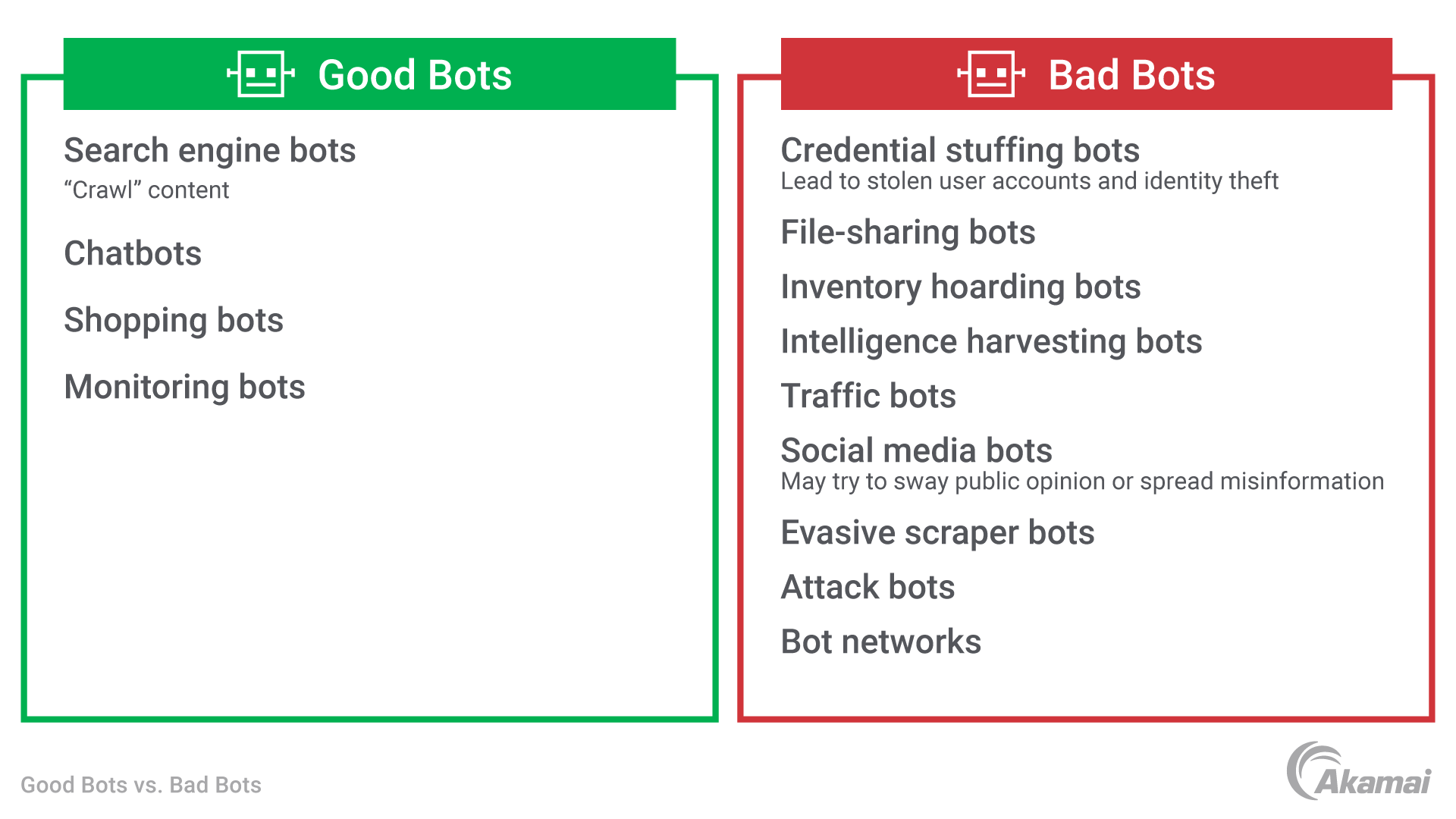
Bots can play both invaluable and detrimental roles in the digital world. The figure shows examples of good and bad bots.
Bots that perform beneficial activities
Some of the bots that are beneficial to websites and their users include:
Search engine crawlers. Also known as spiders, these bots inspect websites to help search engines like Google determine what type of content the site contains.
Chatbots. These bots simulate human conversation to provide users with information, answers to questions, or customer service help.
Shopping bots. These bots search for the best deals available on the web, helping consumers save money.
- Monitoring bots. These bots keep tabs on a website’s health, and issue reports when bugs or vulnerabilities are detected.
Bots that perform abusive or fraudulent activities
On the other hand, many bots are designed to perform activities that are fraudulent or malicious, including:
Credential stuffing bots. These bots attempt to give hackers unauthorized access to user accounts by repeatedly entering stolen usernames and passwords into a website’s login fields.
File-sharing bots. These bots track a user’s search engine queries and provide fake links that let threat actors infect a computer with malware.
Inventory hoarding or scalping bots. These bots purchase and hold high-demand items like tickets, sneakers, and limited-edition products, then resell them for significantly more than the original purchase price.
Intelligence harvesting bots. These bots scan social media platforms, websites, and other sites to find individuals’ personal information, which can be used in phishing attacks.
Spam bots. These bots aid spammers by harvesting email addresses from websites and sending unwanted, malicious email messages.
Traffic bots. These bots mimic the activity of human users to fraudulently drive up a website’s traffic or clicks.
Social media bots. These bots create fake accounts on social media platforms to spread misinformation or increase a particular social media account’s follower count.
Evasive scraper bots. These bots steal content for malicious purposes.
Adversarial attack bots. These bots help threat actors exploit software vulnerabilities or carry out cyberattacks such as ransomware attacks.
Bot networks. These are groups of thousands or millions of hijacked devices that attackers can direct to overwhelm a server or website with a flood of malicious requests, causing IT resources to crash or become unavailable to legitimate users. These networks are often involved in threats like distributed denial-of-service (DDoS) automated attacks.
Gray bots: Stuck in the middle (with you)
Although most people tend to think of bots as being either good or bad, bots actually exist on a spectrum — and even good bots can cause problems if they ping a site too often. We call bots in this middle ground “gray” bots. For example, imagine that APIs from other programs are constantly making calls to your system. Even if these partner bots are performing positive services, they can still cause site degradation by pinging your site 24/7.
You shouldn’t necessarily stop gray bots. Instead, try to manage them so they don’t degrade site performance or negatively impact user or customer experiences. For example, you can slow down bot access to your site during times of peak human use, like early evenings and weekends.
Consequences of poor bot management
When your technology can’t sufficiently manage bot traffic, the consequences can be severe. Those consequences of poor bot management may include:
Unreliable analytics. Site analytics can help you make better marketing decisions (like changing the customer journey on the basis of page traffic) and business decisions (like determining which inventory to purchase on the basis of product page hits). If bot traffic isn’t removed, those decisions can be skewed and lead to expensive missteps.
Loss of revenue from competitive undercutting. If competitors scrape your site and use that information to constantly undercut your prices, you’ll make fewer sales and get a lower price for each sale.
Inventory hoarding and manipulation. Bots can purchase items faster than humans, frustrating users who want to buy a hot item. Bot operators can also add inventory to carts and leave it there, which prevents sales and drives customers to your competitors during shopping events like holiday sales.
Negative impacts on the bottom line. Bots can cost you a great deal of money by redirecting your website visitors to a competitor, causing your sales teams to chase false leads or slowing your security teams with DDoS responses and account takeover attack mitigation.
Loss of customer trust. Harmful digital materials like spam emails with malicious links, fake reviews, and fake social media accounts can impact your company’s reputation with customers.
Loss of advertising ROI. In search advertising, bots that repeatedly click on your paid search ads may cost you a lot of money.
How bot management works: 4 key tasks
Bot management solutions perform four essential tasks:
Detecting bot activity
Categorizing bot types
Responding in real time
Monitoring results
Detecting bot activity
Bot detection solutions identify bot traffic on web applications and websites by analyzing data like user behavior, web requests, and header information.
Categorizing bot types
Once bot traffic is detected, bot management solutions categorize traffic as human, good bot, bad bot, or questionable. This can often be thought of as low-risk, moderate-risk, or high-risk traffic.
Responding in real time
Bot management solutions must act swiftly to block malicious bots, but allow useful bots to challenge questionable traffic while performing regular tasks and specialized actions. An example of a specialized action would be allowing partners’ shopping bots through while blocking those you don’t believe offer any value.
Monitoring results
Bot management also involves tracking responses to bot activity to fine-tune performance as bots evolve and their operating environments continually change.
Tools and strategies of bot management solutions
To accurately detect, categorize, and respond to potential bot activity, bot management solutions rely on a variety of tools and strategies, such as:
Signature files and profiles of known bots enable bot management solutions to block malicious bots before they can access or attack web apps and APIs.
IP reputation analysis checks the reputation of IP addresses connected to web requests to see if they’re associated with malicious bots.
Transactions per second (TPS) parameters allow security teams to flag any traffic for which the number of requests exceeds a certain threshold, potentially indicating a malicious bot.
Device fingerprinting uses information like a device’s operating system, installed fonts, screen resolution, browser attributes, and HTTP request headers to determine whether a bot is malicious.
Rate limiting may be used to prevent bad bots from entering a network or to prevent bots of an uncertain nature from overwhelming APIs and systems.
CAPTCHA challenges help determine whether traffic is a product of human activity or bot activity. Traffic that can’t successfully complete a CAPTCHA challenge may be dropped or given additional verification challenges.
Serving alternate content specifically designed for bots can effectively prevent bad bots from accessing protected data or scraping proprietary information.
Collective bot intelligence is data about malicious bots that’s shared via automated threat intelligence feeds.
Allowlists and blocklists identify good and bad bots by tracking specific IP addresses and subnets.
What to look for in a bot management solution
Since bots are only getting more sophisticated and specialized, it’s important for companies to stay ahead of attacks by investing in innovative bot management solutions backed by cybersecurity specialists.
When choosing a bot management solution, IT teams should look for several key characteristics and capabilities, including:
Superior identification. Although every bot management solution detects bots, the best solutions should be able to spot even the most sophisticated bots that websites and networks encounter.
Resilient bot detection. Many bot management technologies detect bots initially but then lose track of bots as they begin to mutate. The most effective solutions learn and evolve to ensure bot mitigation techniques stay effective over time.
Minimal false positives. Blocking bad bots shouldn’t slow a business down. Products that block legitimate users or good bots inevitably impact productivity. Strong bot management solutions should provide autotuning capabilities that minimize false positives.
Granular visibility and reporting. When determining which bots to block, IT teams need granular visibility and reporting capabilities that can zoom in on specific bots, botnets, and bot characteristics.
API protection. In bot management systems without mitigation techniques to cover APIs, bots will simply migrate from web pages to APIs.
Akamai Bot Manager, our best-in-class bot management solution, can effectively detect the most sophisticated bot traffic, mitigate malicious bot attacks at the edge, and efficiently manage good bots — all without impacting user experience.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.