Akamai Named an Overall Leader for Zero Trust Network Access

The Zero Trust model is a strategic approach to cybersecurity that secures an organization by removing implicit trust. Instead of assuming everything behind the corporate firewall is safe, the Zero Trust approach applies least-privilege access to every request, regardless of where it originates.
Zero Trust has become top of mind for organizations that need to more effectively adapt to the ever-changing modern environment. These organizations are looking for a new security model that embraces the hybrid workforce and protects users, devices, and apps wherever they are located. Sorting through all the choices, however, is complicated.
Insights into the Zero Trust Network access market
In January 2024, KuppingerCole Analysts AG published an in-depth report on the Zero Trust Network Access (ZTNA) market. Lead analyst Alejandro Leal evaluated 20 ZTNA vendors and provided detailed insights, including:
An analysis of the ZTNA market and why it is experiencing rapid growth
Why ZTNA is a key component for enterprises transforming to a Zero Trust architecture
The business and security benefits that ZTNA delivers and the different ZTNA architectures
Why a careful approach to implementation for ZTNA is required, especially for larger enterprises
ZTNA is a pivotal shift in security strategy
The report highlights that conventional perimeter-based security approaches are no longer sufficient to protect today’s dynamic and distributed IT ecosystems. Today, private applications can be hosted anywhere and employees require secure application access from everywhere from both managed and unmanaged devices. Unlike this legacy approach, ZTNA operates under the assumption that no entity, whether inside or outside the network, should be inherently trusted.
The analysis also emphasizes the fact that ZTNA is a key technology that is essential for any enterprise transitioning to a Zero Trust architecture. It enforces strict identity verification and least-privilege access policies for every user, device, or application, regardless of where they are located. And ZTNA reduces an enterprise’s attack surface, prevents lateral movement, and simplifies user and administrator experiences.
The report’s structured description of ZTNA will be useful for both novice and experienced security professionals. Akamai recommends using this report as a tool for assessing your ZTNA and Zero Trust architecture strategy and as a guide to what to look for in a ZTNA security vendor.
Akamai recognized as an Overall Leader
Akamai is thrilled to be an Overall Leader in the ZTNA market and to receive recognition for our ZTNA solution, which comprises Akamai Enterprise Application Access and Akamai MFA (Figure 1). We were also named a Leader in the other three categories: Product (Figure 2), Market, and Innovation.
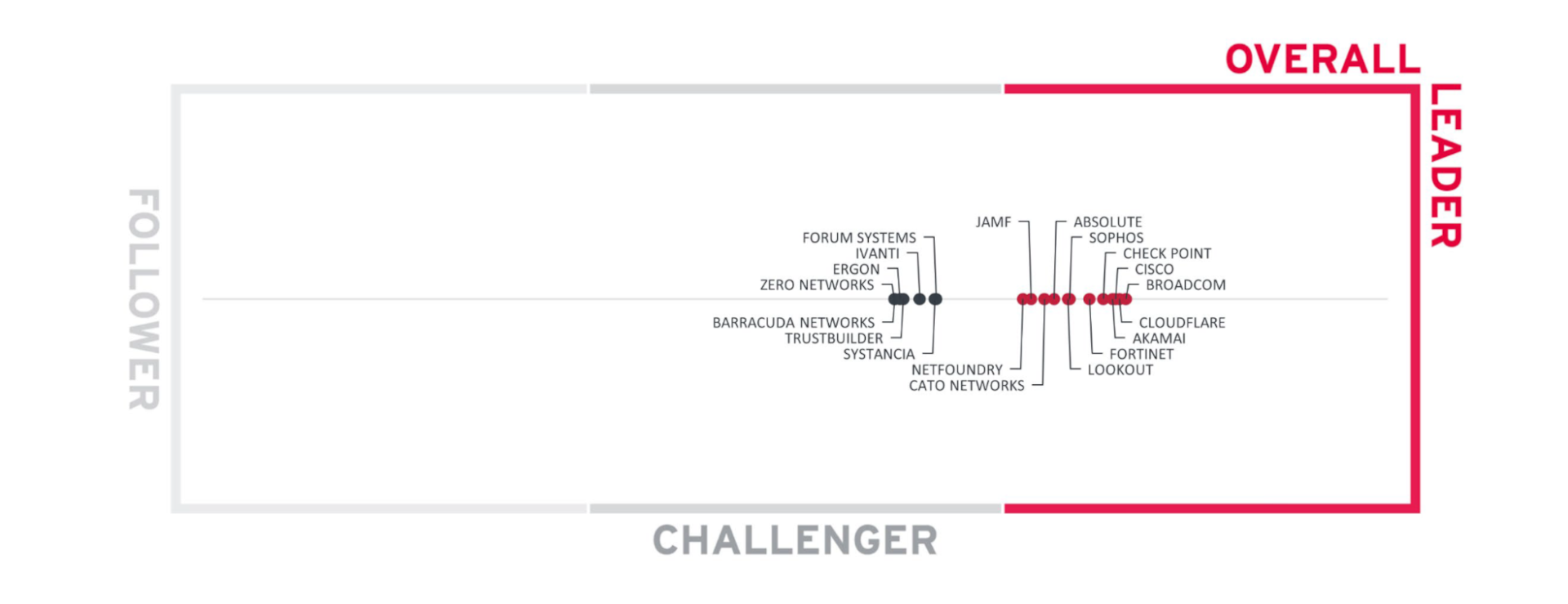 Fig. 1: Akamai is named an Overall Leader in the ZTNA market
Fig. 1: Akamai is named an Overall Leader in the ZTNA market
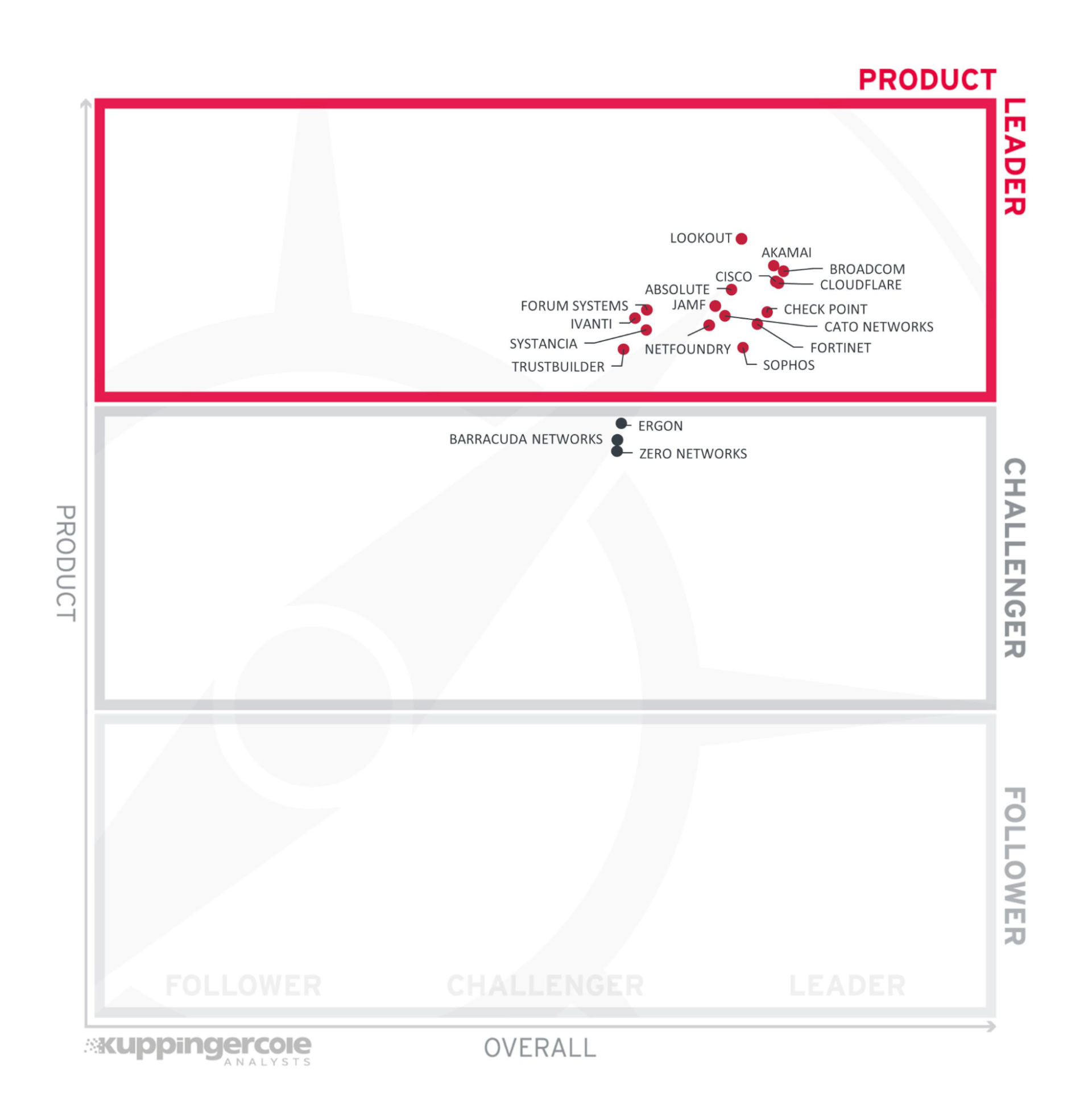 Fig. 2: Akamai is named a Leader in the Product category
Fig. 2: Akamai is named a Leader in the Product category
In the report, KuppingerCole identifies Akamai’s strengths among the ZTNA vendors, including:
Akamai Connected Cloud, a robust global infrastructure that enhances the delivery of secure access services and contributes to a reliable and high-performance user experience
Easy integrations with all notable identity providers
A focus on strong authentication with Akamai MFA, a FIDO2-based multi-factor solution that eliminates the need for physical security keys
The available add-ons of other Akamai security and CDN services, including Akamai App & API Protector, Akamai API Security, and Akamai Prolexic, to further enhance the ZTNA solution
Akamai’s global presence and strong partner ecosystem
The solution’s unique positioning for large enterprises with hundreds of business applications and complex business requirements
Successfully move to Zero Trust Network Access with Akamai
The need to move to a Zero Trust architecture that includes ZTNA as a key component has never been greater. Threat actors continue to exploit the inherent security risks that a perimeter-based security approach introduces, and VPNs no longer support the work-from-anywhere model.
Deploying Akamai’s ZTNA solution will help enterprises:
Start or continue their transition to a Zero Trust architecture
Minimize their attack surface and reduce lateral movement by minimizing the need for network-level access
Provide secure, reliable, and performant application access for employees, contractors, and third parties based on context and device posture
Reduce VPN usage and deliver modern application access
Akamai already protects some of the world’s largest companies
Akamai’s ZTNA solution has been successfully deployed by many of the world’s largest enterprises. For example, a global shipping and logistics company has deployed Akamai Enterprise Application Access to provide secure application access for more than 40,000 employees. This has allowed the company to accelerate its transition to cloud, improve its security posture, and reduce risk.
Read more
Get a complimentary copy of the report, and learn why you can trust Akamai to help you successfully deploy ZTNA across your organization.


