Inside the NIST Cybersecurity Framework 2.0 and API Security
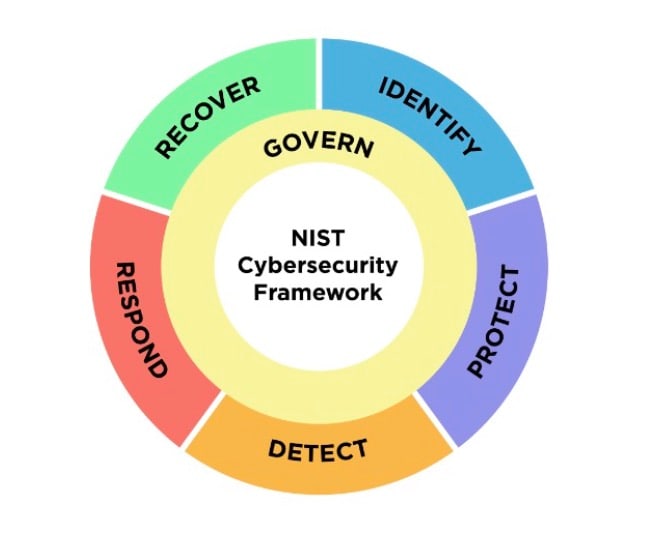
What is the NIST Cybersecurity Framework?
The National Institute of Standards and Technology (NIST), an agency of the United States Department of Commerce, has significantly updated its Cybersecurity Framework (CSF), a structural guideline widely used by U.S. organizations to better understand and manage their cybersecurity risks.
Initially released as version 1.0 in 2014 and updated to version 1.1 in 2018, CSF version 2.0 was released in February 2024. The newest version offers updated guidance to various industries, government agencies, the private sector, and other organizations on how to more effectively mitigate modern cybersecurity risks.
It provides a taxonomy of high-level cybersecurity outcomes that any organization, regardless of size, sector, or maturity, can use to better understand, assess, prioritize, and communicate its cybersecurity efforts. The cyberframework does not dictate how to achieve these outcomes; instead, it maps to resources that offer additional practices and controls guidance that can be used to achieve these outcomes.
Why should organizations follow NIST Cybersecurity Framework 2.0?
The NIST Cybersecurity Framework 2.0 (NIST CSF 2.0) serves as a guidebook for organizations looking to enhance their online security. It establishes cybersecurity goals in common language, organized by function, category, and subcategory, which are applicable to all organization types — from small businesses to global enterprises.
Rather than prescribing specific actions, CSF 2.0 lets organizations determine how best to achieve these goals in the way that works for them. The order of these goals isn’t indicative of their importance; each goal is an important part of maintaining online safety.
The risk management framework doesn’t delve into specific cybersecurity technologies or differentiate between IoT devices and network devices, which can make it challenging to understand how and why organizations should follow the framework to benefit their API security.
To provide some clarity, the team at Akamai created this guide on how to map the new CSF 2.0 guidelines to your API security program — or more accurately, how to integrate API security into your overall cybersecurity posture and risk management program.
How API security aligns with the NIST Cybersecurity Framework
Govern: Establish and monitor cybersecurity risk management strategy, expectations, and policy
The NIST Cybersecurity Framework’s Govern function serves as a guide to how an organization can achieve and prioritize the other five functions’ results in the context of its mission and stakeholder expectations. Governance activities are crucial for integrating cybersecurity into an organization's broader enterprise risk management strategy.
In particular, Govern encourages people within an organization to come to a common understanding of cybersecurity within the context of their organization. It suggests that each organization establish a cybersecurity program and strategy, supply chain risk and asset management strategy that includes roles, responsibilities, authorities, policies, processes, and procedures.
Govern’s application to API security
The key to using Govern to improve API security is to incorporate API management and security into your overall security strategy. That way, you avoid silos that could create critical security gaps or allow APIs to be overlooked in governance. This means including your APIs in your cybersecurity risk management decisions, risk tolerance assessments, prioritization, internal operations, and supply chain risk management processes — particularly for any open-source APIs used in development.
How to apply the Govern function to improve API security
To properly apply the NIST Cybersecurity Framework’s Govern function across your organization, you’ll need to:
- Ensure APIs completely match their specifications
- Detect all API changes
- Identify software in use
Identify: Help determine a threat’s cybersecurity risk to the organization
The Identify function involves finding and understanding all your assets — including data (and its backups), sensitive information, hardware, software, systems, facilities, services, and people — and related cybersecurity risks. In doing so, your organization can focus and prioritize its efforts in alignment with its risk management strategy and mission needs identified during the Govern function.
Identify also encourages readers to seek out room for improvement in their organization's policies, processes, procedures, and practices that support cybersecurity risk management, thereby informing your efforts across all six functions.
How to apply the Identify function to improve API security
The key to identifying all of your organization’s assets to improve API security is to ensure complete visibility of your entire API portfolio. Lacking this visibility can hinder your ability to fully secure them. Stay aware of all public, partner, and private APIs in use within your organization, and make sure that you understand their significance within your broader risk strategy.
Be sure to include APIs in your risk assessment process. Pay particular attention to externally accessible private and partner APIs, both of which are crucial to your internal operations.
To apply the Identity function across your organization, you’ll need to:
Inventory all APIs and endpoints
Classify API endpoints
Assess endpoint risks
Identify API vulnerabilities
Detect API endpoint changes
Protect: Use safeguards to prevent or reduce cybersecurity risk
After you’ve identified and prioritized assets and risks as part of the Identity function, the Protect function helps you secure those assets to reduce the probability and impact of cybersecurity incidents. This includes achieving outcomes like awareness and training, data security, information security, identity management, authentication, access control, and ensuring both physical and virtual technology infrastructure resilience.
How to apply the Protect function to improve API security
By deploying proactive and real-time API protections, you can minimize the risk of APIs becoming vulnerable targets for cyberattacks as part of the Protect function.
This involves several measures, including implementing strong authentication (AuthN) and authorization (AuthZ) practices, integrating API security best practices into your software development lifecycle (SDLC), and ensuring that API endpoints handling sensitive data flows are identified, monitored, and adequately protected.
To apply the Protect function across your organization, you’ll need to:
Identify out-of-date API components
Record API session data
Locate unauthorized or unmanaged APIs
Block attacks on your APIs
Detect: Find and analyze possible cybersecurity attacks and compromises
The Detect function enables the timely discovery and analysis of anomalies, compromise indicators, and other potential events that may indicate ongoing cybersecurity activities or incidents.
How to apply the Detect function to improve API security
Applying the Detect function to improve your organization’s API security controls and detection processes requires visibility into your API vulnerabilities and understanding of cyberthreats against them, in particular. More than 80% of web traffic now passes through APIs and because APIs are used extensively in many development environments such as GitHub.
This process involves monitoring all API endpoints regardless of protocol or underlying critical infrastructure; applying virtual patches; integrating real-world attack data into your SDLC processes; and providing robust support — comparable to traditional infrastructure and compiled code — for detecting and mitigating API incidents.
To apply the Detect function across your organization, you’ll need to:
Detect attacks against your APIs
Identify cybersecurity events and incidents in progress
Deliver incident data to Security Information and Event Management (SIEM) systems
Respond: Take action when a cybersecurity incident is detected
The Respond function of the Cybersecurity Framework enables the ability to contain the impact of cybersecurity incidents and includes outcomes like incident management, analysis, mitigation, reporting, and communication.
How to apply the Respond function to improve API security
The Respond function encourages organizations to be able to swiftly respond to attacks against APIs, ensuring incidents are managed using consistent processes and procedures across your digital domain. This involves applying a continuous monitoring approach to automatically detect security threats, performance issues, or compliance problems in IT systems and networks, then extending this approach to APIs to enable rapid incident response and response planning within your API portfolio.
To apply the Respond function across your organization, you’ll need to:
Identify attacked vulnerabilities
Capture attack details
Notify stakeholders of cybersecurity incidents
Block attacks and malicious behavior
Recover: Restore assets and operations impacted by a cybersecurity incident
The Recover function facilitates the timely restoration of normal operations following cybersecurity incidents. It aims to minimize incident impact and ensure effective organizational communication throughout recovery activities.
How to apply the Recover function to improve API security
By developing recovery plans that address API-specific requirements, particularly those involving third-party or open-source tools used in your development infrastructure, you enact the Recover function across your organization. This process involves creating, implementing, testing, and subsequently automating your API-specific recovery plans.
In addition, integrating API-specific outputs into your current security and reporting systems can ensure timelier and better coordinated internal and, when needed, external communications.
To apply the Recover function across your organization, you’ll need to:
Capture comprehensive details of API-related data breaches
Include API-based services in your recovery plans
Integrate API incident reporting into your existing security structure
Bolster your API security posture with Akamai API Security
With properly secured APIs, your team can craft incredible products, services, and experiences that enrich customers’ lives.
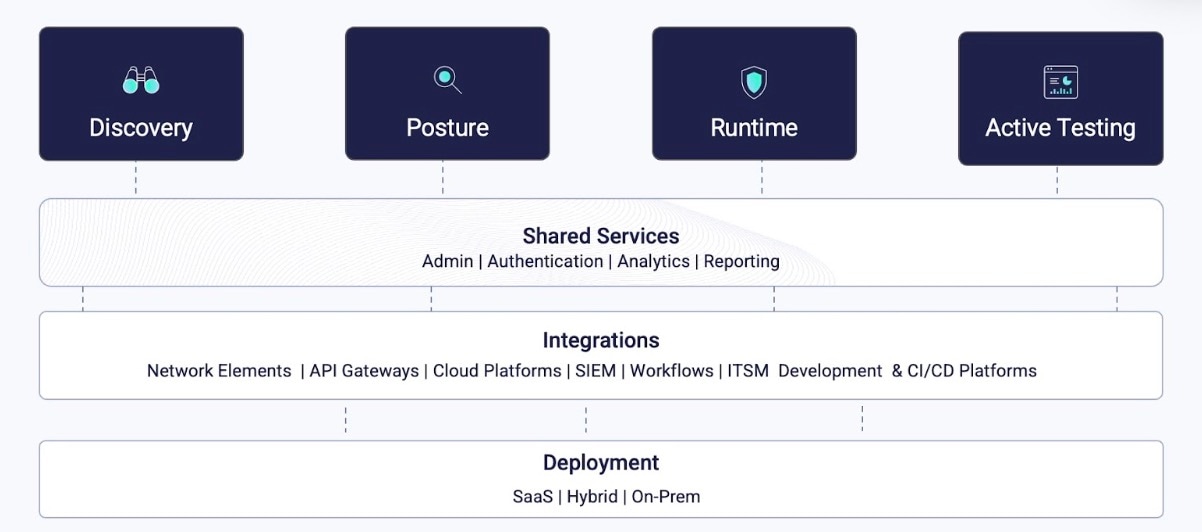
Akamai API Security is an API security solution that offers full visibility into your entire API estate through continuous discovery and real-time analysis (Figure 2) — helping your organization fully comply with the latest NIST Cybersecurity Framework 2.0 standards and updates for 360-degree protection.
With Akamai as your security solution provider, you can quickly discover all of your APIs — even shadow APIs — identify common vulnerabilities, and analyze API behavior so that you can more effectively detect threats and logic abuse within fast-growing attack surfaces.
Contact Akamai to get started redefining API security across your organization with Akamai API Security – informed by the six NIST Cybersecurity Framework functions.