In-App Browsers and Akamai Client-Side Protection & Compliance

A report published by Felix Krause in August 2022 raised awareness about security and privacy risks to which users might be exposed as part of their usage of native mobile applications that have in-app browsers.
The report revealed that some of the most popular mobile applications use their in-app browser in order to inject their own JavaScript code into third-party websites, which are opened as part of the usage of their apps (e.g., clicking on a link inside the app, opening an ad, etc.).
Having the ability to execute any JavaScript code on an unrelated site can expose the end users to security and privacy risks. However, those injections are not necessarily malicious. At least some of the most popular mobile applications use those injections regularly for a long time in order to improve their user experience and send error logs.
In the following blog post, we will share what Akamai sees regarding in-app browser usage — and how we track those in-app browser injections to make sure our customers' users' sensitive information is kept safe and private.
What are in-app browsers?
In-app browsers (also called WebView browsers) are embeddable browsers that native mobile applications can implement in order to present web pages as part of the application itself. In-app browsers are lighter, have fewer functionalities than regular mobile browsers (such as Chrome and Safari), and are controlled by the native application that opened them.
The main purpose of in-app browsers is to reduce the requirement of developing similar pages or functionalities that have already been created as part of the applications’ websites, and to let mobile apps open their web pages inside of them.
As part of their control of the browser, mobile apps can inject JavaScript code into pages opened by them. In most cases, the injected script provides the native application the ability to improve the user experience by enabling features (such as autocomplete and password management), tracking browser performance and errors, and increasing end-user security and privacy.
On the other hand, in severe cases, native applications can abuse this ability in order to inject malicious code into third-party pages, and use it to exfiltrate sensitive user information or show ads on top of those sites.
Akamai point of view
In Akamai Client-Side Protection & Compliance, we see more than 5 million (15%) of our customers’ mobile sessions originating from in-app browsers daily.
A significant percentage of sessions among them originated from the most popular social media mobile applications. In fact, some of our customers have 10% to 15% of their sessions coming from in-app browsers associated with those applications.
The injected script behaves as any other script on the page. Client-Side Protection & Compliance monitors those scripts and has the visibility to detect whether a script collects user information, tracks the user activity, and so forth.
In the figure below, we share how Client-Side Protection & Compliance tracks a script resource that was injected into a customer site from one of the world's most popular mobile applications. This resource is particularly notable because of the number of affected beacons (affected pages) on which it was seen: approximately 8% of the customer's pages loaded this resource — which comprises 400,000 pages per day for the Android version of this application alone.
In addition, according to Client-Side Protection & Compliance, this script monitors the input fields on the page. It is important to mention that it does not send their sensitive values out of the page. Monitoring sensitive fields is a common behavior among analytics services that track the way that the user interacts with the page, fills form fields, etc.
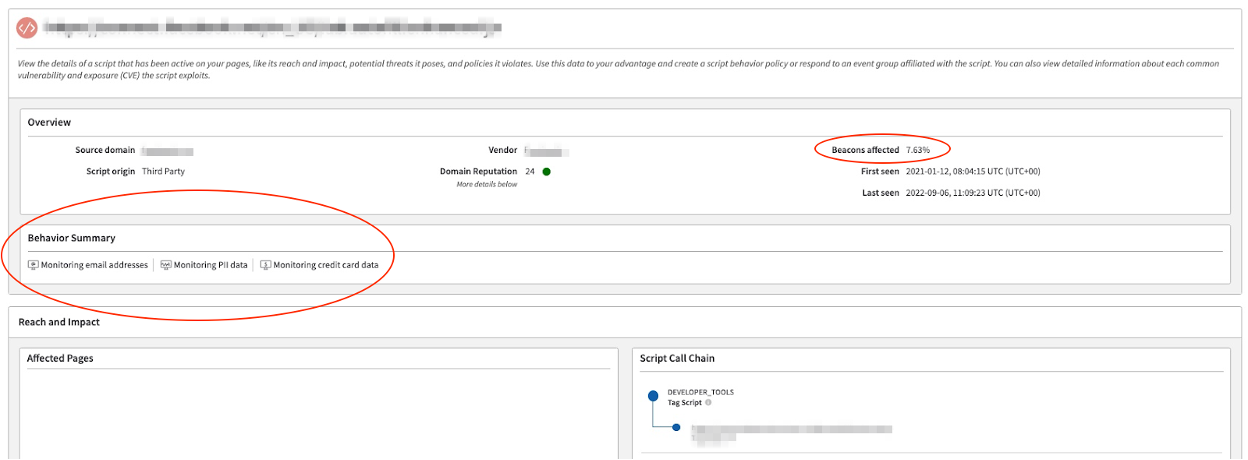
Client-Side Protection & Compliance also provides protection from malicious attacks that may occur as part of in-app usage. Similar to any other JavaScript code on the page, Client-Side Protection & Compliance analyzes the injected script in runtime and sends an alert if the script tries to exfiltrate sensitive user information out of the protected application.
Detecting and preventing client-side threats with Client-Side Protection & Compliance
Client-Side Protection & Compliance focuses on the script execution behavior, with unprecedented visibility into the runtime environment. It collects information about the different scripts that run on a web page, the actions they take, and their relation to other scripts on the page. Pairing this data with our multilayered detection approach — leveraging heuristics, risk scoring, artificial intelligence, and other factors — allows Client-Side Protection & Compliance to detect different types of client-side attacks, with a high focus on data exfiltration and web skimming attacks.
JavaScript code that is injected into the page using in-app browsers will be treated the same as any other scripts on the page. As noted previously, Client-Side Protection & Compliance has the ability to monitor each and every JavaScript execution on the page.
More than that, Client-Side Protection & Compliance provides customers with the ability to deny unwanted network requests, as well as access sensitive information for unauthorized JavaScript resources in just one click. This significantly lowers the response time for detected events and decreases the impact on our customers’ users.
Conclusion
In-app browsers are common and used by almost every mobile application. They are lean browsers that provide native mobile applications the ability to present web pages as part of the application itself.
As part of their control of the browser, mobile applications can inject custom JavaScript code into third-party web pages. This custom JavaScript code is usually used for enhancing the user experience in the application, but can be abused and could be a privacy and security risk for the end users.
As more and more web traffic is coming from mobile devices, in-app browsers are becoming a significant part of the traffic we see.
Akamai Client-Side Protection & Compliance monitors the injected scripts the same as any other scripts and provides its customers visibility into what those scripts are — and, more important, provides protection in case of malicious usage.
Find out more
Learn more about Akamai Client-Side Protection & Compliance and get a free script risk-assessment report.


