2024: Old CVEs, New Targets — Active Exploitation of ThinkPHP
Editorial and additional commentary by Tricia Howard
Executive summary
Akamai researchers have discovered a new campaign that targets ThinkPHP applications that are vulnerable to CVE-2018-20062 and CVE-2019-9082. The campaign appears to be orchestrated by a Chinese-speaking cyberthreat group.
The campaign seems to have started in as early as October 2023 by targeting a limited number of customers/organizations. It only recently became widespread.
The attacks originated from various IP addresses associated with servers hosted on the "Zenlayer" cloud provider (ASN 21859), primarily located in Hong Kong.
The exploit attempts to retrieve additional obfuscated code from another compromised ThinkPHP server to gain initial foothold.
After successfully exploiting the system, the attackers will install a Chinese language web shell named Dama to maintain persistent access to the server.
Subsequent actions may involve spreading further within the victim's data center or enlisting the server for use in attack infrastructure.
Introduction
We are seeing a troubling trend in security: Attackers are exploiting known vulnerabilities, some of them several years old, and they are having success doing so. A prime example of this is the ThinkPHP remote code execution (RCE) vulnerabilities CVE-2018-20062 and CVE-2019-9082. As you can tell by the CVE names, these have been in the wild since at least 2018, and yet, the attack activity continues today.
We first detected signs of this attack behavior on October 17, 2023. We observed a limited series of probes exploiting these vulnerabilities, but not in the way you’d expect. Unlike the common "proof of concept" commands seen with automated tools and scanners, the payload instructed the victim servers to install an obfuscated shell from a remote server under the attacker's control.
The campaign was active only for a few days and then these limited probes ceased, but that seems to have only been the beginning. As of April 2024, we have observed a similar campaign, and this one is much larger than its predecessor.
In this blog post, we will outline the CVEs, the observed exploit attempts, and the recommended mitigations for those affected by this campaign.
About the CVEs
What is ThinkPHP?
ThinkPHP is a Chinese open-source web application framework, primarily used for developing PHP-based web applications. It provides a set of libraries, components, and tools that simplify the process of building web applications by following the model-view-controller (MVC) architectural pattern.
CVE-2018-20062 and CVE-2019-9082 are vulnerabilities found in older versions of the popular Chinese ThinkPHP framework. These vulnerabilities affect content management systems that are based on this framework, such as NoneCMS and open-source BMS. They enable attackers to remotely execute code on the victim’s server. Both vulnerabilities are part of a series of exploit variants that target different ThinkPHP components, which was disclosed over a few years starting from 2018 when the initial attack vector was revealed.
Observed exploitation attempts
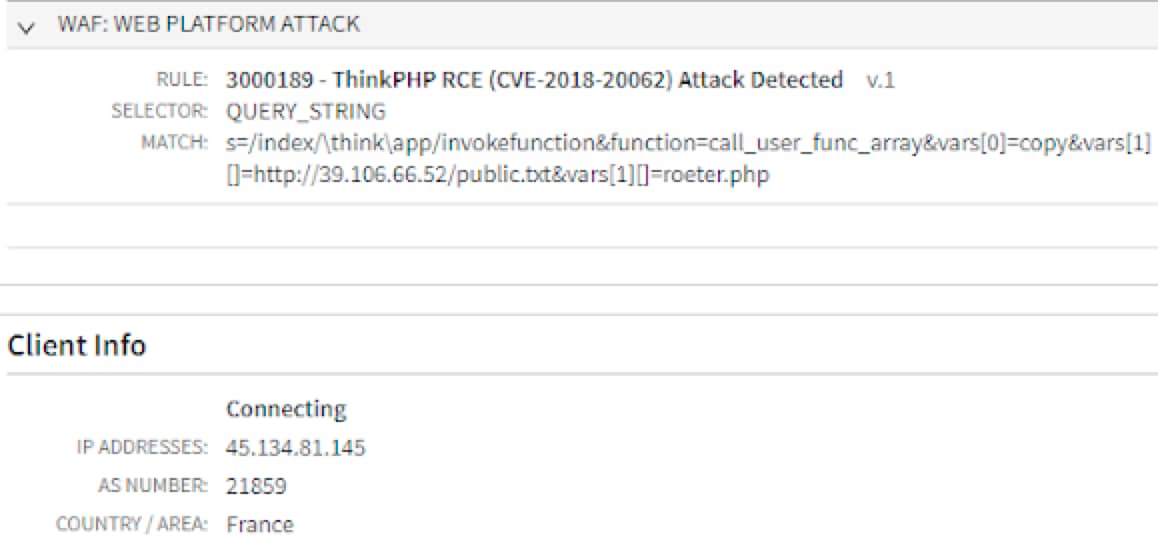
The exploit attempts (detected and recorded by Akamai App & API Protector) attempt to use the CVEs to download a file named "public.txt" from what appears to be a compromised server located in China. The new malicious file will then be saved on the victim's systems with the name "roeter.php," which we believe to be a misspelling of "router" (Figure 1).
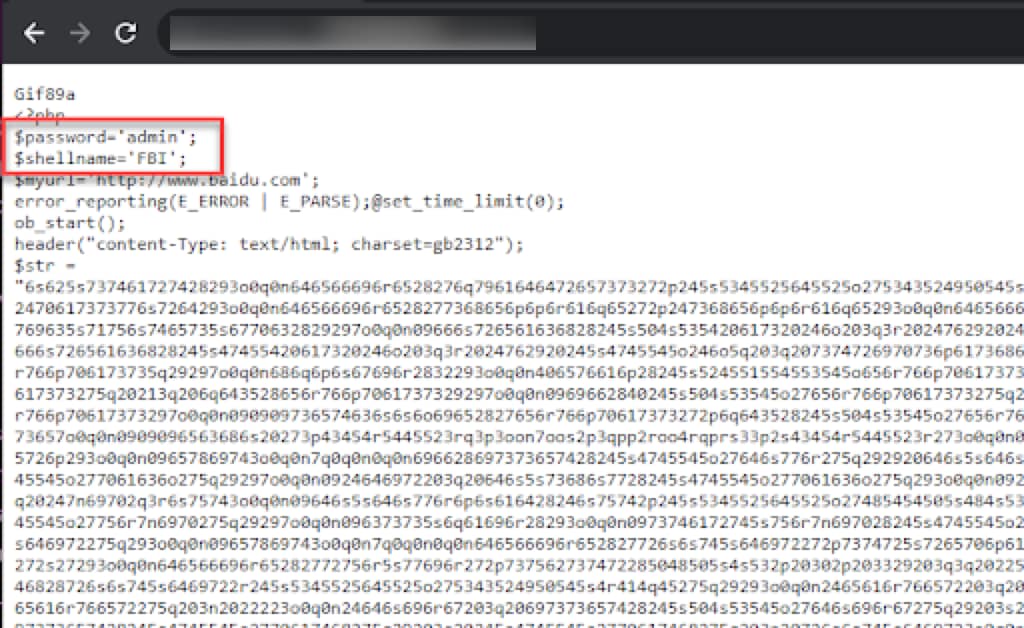
The downloaded text file contains an obfuscated version of a web shell, a server-side backdoor script for remote server control. The web shell code uses obfuscation, specifically a basic ROT13 transformation that results in a single, lengthy HEX string (Figure 2). Interestingly, the attackers chose a very simple password — "admin" — to access the web shell.
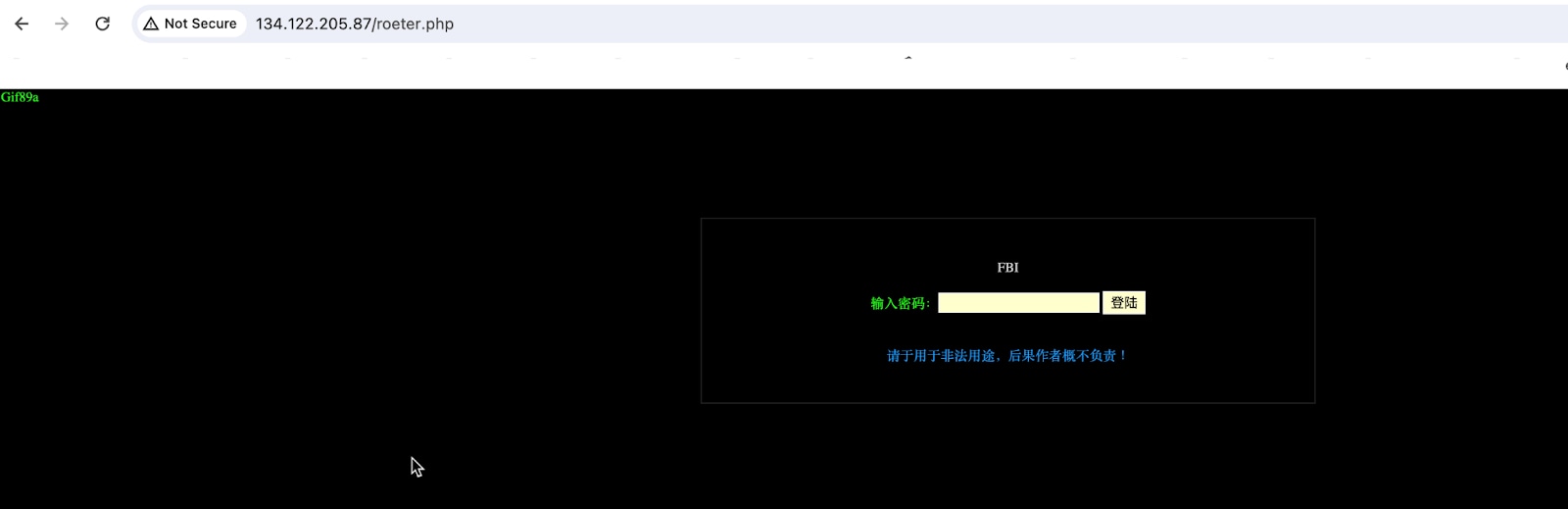
The attacks originated from various IP addresses associated with servers hosted on the Zenlayer cloud provider (ASN 21859), primarily located in Hong Kong. Our brief inspection of the server that was hosting the backdoor code revealed that it was also infected with the same web shell (Figure 3).
This suggests that the server may be another node in the attacker's infrastructure. This approach could help reduce operational costs and, more importantly, obscure attribution, making it more challenging for law enforcement to take down the server, as they cannot simply ask the ISP to shut down a legitimate organization’s production server.
The Dama web shell
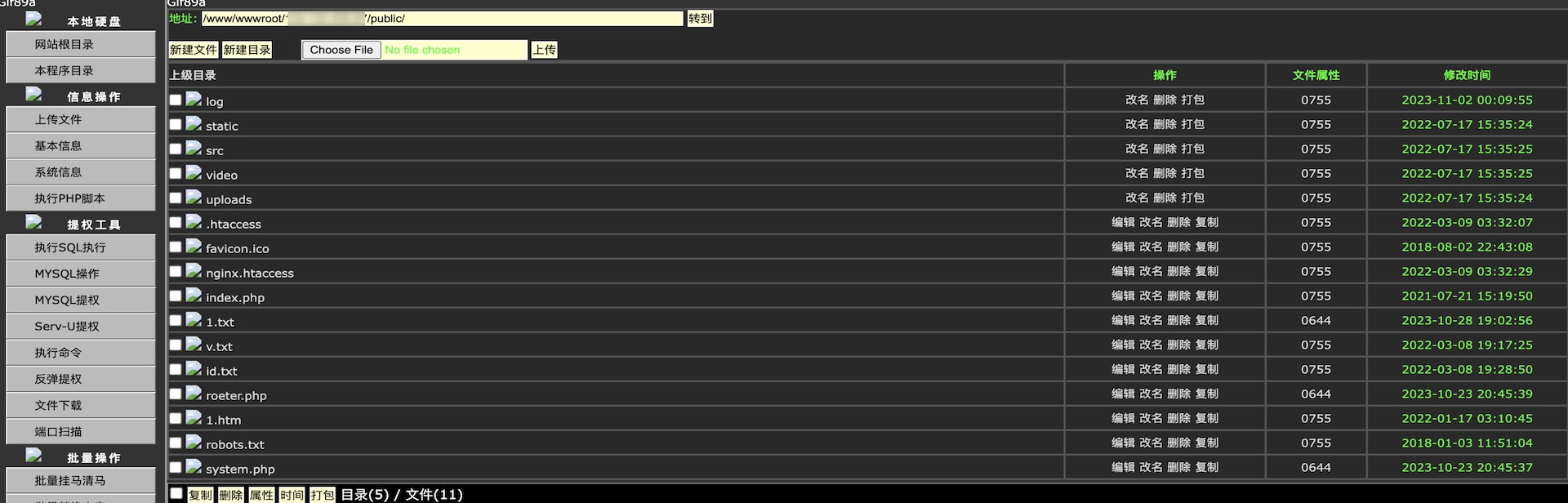
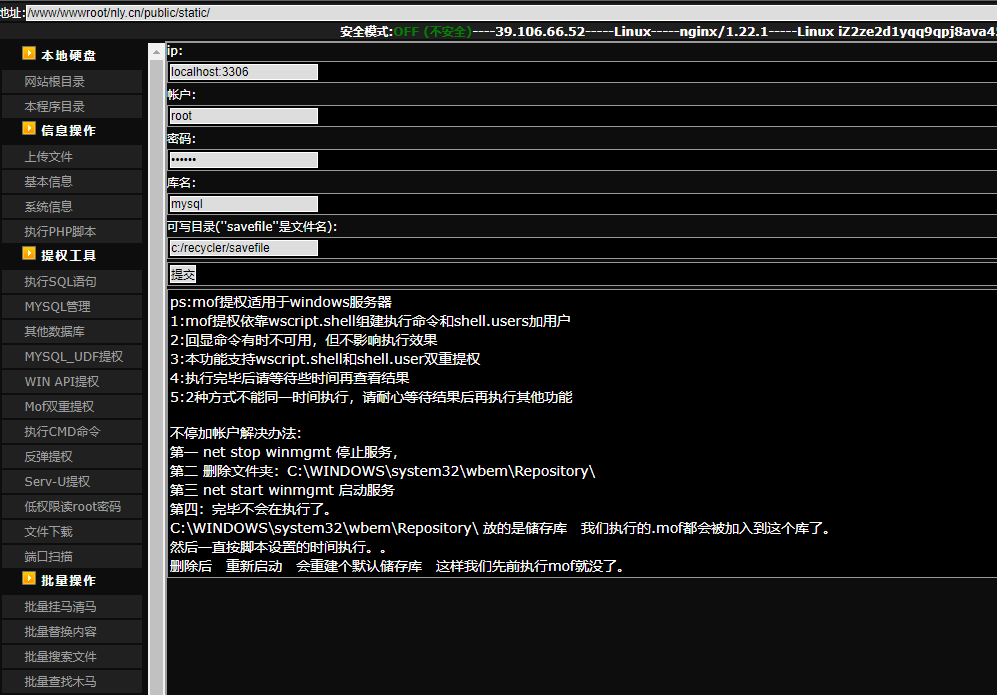
The web shell demonstrates advanced capabilities, such as navigating the file system, which enables operations like file editing, deletion, and timestamp modification for obfuscation purposes. Although it's common to observe Western and Eastern European threat actors using web shells in English (e.g., the WSO-NG web shell), this one stands out because of the Chinese origin of the user interface (Figure 4).
In addition to the aforementioned advanced mechanisms, Dama facilitates file uploads to the server and gathers crucial technical system data, including precise OS versions and PHP information, which aids in the identification of pertinent privilege escalation exploits (Figure 5).
It doesn’t stop there. Post exploitation features include network port scanning and access to existing databases and server data. Furthermore, the web shell offers diverse methods for privilege escalation, such as bypassing disabled sensitive PHP functions to escape the PHP sandbox and execute shell commands on the server.
It also leverages the Windows task scheduler to reconfigure WMI and add high-privileged users. Although equipped with a PHP interpreter for direct code execution, support for a command-line interface (CLI) for executing direct OS shell commands is notably absent, which is surprising given its extensive functionality.
Mitigating with App & API Protector
It is highly recommended to upgrade ThinkPHP to the most recent version, currently 8.0.
As it is challenging to identify all the assets that might be vulnerable to these CVEs and patching itself might not be a feasible option, we strongly advise implementing App & API Protector with its Adaptive Security Engine to reduce the risks associated with ThinkPHP CVEs.
If you are already using Adaptive Security Engine, you can easily address these risks by configuring the Web Platform Attack group action to “Deny” to enhance protection. Alternatively, customers can opt to set the individual rule 3000189 (“ThinkPHP RCE (CVE-2018-20062)”) to “Deny.”
Summary
This web shell is yet another example of a one-day — despite how long they’ve been known, attackers continue to target and exploit them, with notable success. This underscores the persistent challenge organizations face in identifying vulnerable assets and maintaining effective patch management processes.
The recent attacks originated by a Chinese-speaking adversary highlight an ongoing trend of attackers using a fully fledged web shell, designed for advanced victim control. Interestingly, not all targeted customers were using ThinkPHP, which suggests that the attackers may be indiscriminately targeting a broad range of systems.
This is yet another interesting dichotomy that has increased in prevalence recently; that is, some aspects of the attacks are highly sophisticated (such as the obfuscation controls in the technology) and others are almost haphazard (such as not having support for a CLI). As more and more technological advancements occur, it’s likely we’ll see this gap continue to grow because although the technology is advanced, that doesn’t necessarily indicate the attacker behind them is advanced as well. That’s not to say the creator of the Dama web shell isn’t sophisticated; it is simply a comment on how the industry is changing as a whole.
Since our customers were protected from these attack attempts, we can't definitively determine the attackers' ultimate intention. However, based on our experience, their goals could have included incorporating victims’ systems into the attack infrastructure to launch additional attacks, recruiting the servers to a potent distributed denial-of-service (DDoS) or crypto botnet network, carrying out ransomware or extortion schemes, or conducting lateral movement to gather intelligence on organizations.
Stay tuned
The Akamai Security Intelligence Group will continue to monitor and defend against threats such as the Dama web shell and publish our findings for the community at large. For real-time updates, follow us on X (formerly Twitter).