Take Cover: Securing Games Truly Is a Battle Royale
Data analysis by Camila Cabrera Camacho
Copy editing by Maria Vlasak
Special thanks to Chris Finch, Alan Evans, Dan Greer, Ken Eaton, and Todd Loewenstein for their expertise
The games industry is arguably one of the most influential industries of our time. With 2.58 billion video gamers around the world and an appraisal of US$184.4 billion, this elephantine industry is only going to grow as each generation becomes more reliant on technology. In this three-part blog post series, we will explore the wonderful world of Games from a few different perspectives.
🔒 In this inaugural post, we will focus on the security challenges by reviewing the statistics from the past 18 months (January 2023 – June 2024).
👾 In our second post, we’ll move into 3D and discuss the people behind the games (on both sides of the screen).
☁️ In our third, and final post, the series will conclude with a technical view of cloud-distributed games.
Pick your drop, security pros
One of the most interesting parts of the games industry is its unique security position — there are cyber land mines at every turn both for the players and the developers. The average gamer is more technologically savvy than most consumers in other industries, which means an “insider threat” in the games industry can come from inside the network or from inside your digital reality.
This industry also has a highly unique prevalent threat actor profile: the troublemaker. A streamer says something they don’t like? They’ll build a bot to take them offline. A troublemaker can also build trust by pretending to be an ally in the game, and then deliver malicious payloads or URLs through the chat feature.
The good, the bad, and the ugly of a technologically savvy demographic
The industry is appreciative of openness and collaboration among players — and it has the technologic mindset to match, which, by its nature, is antithetical to security’s plight. Some behaviors viewed as suspicious or even malicious in the security sphere are not only commonplace in the games industry, but they’re also embraced and encouraged; for example, modding is integral to the culture of games and botting is considered part of gameplay in some scenarios.
The security community knows all too well that the same tactics, techniques, and procedures that give the community its charm can also be used for malice. There is an overlap in the Venn diagram of people interested in games and those with technical know-how, which creates opportunities for both rule breaking and technical discoveries.
It also means that attackers’ goals can be different, and those differences influence attack trends. Where else than in the world of games can you bot for currency in two different realms? You could even do it at the same time if you wanted to.
In this blog post, we will discuss the security challenges we saw in the games industry in the last 18 months.
Looting on- and offline
On top of the player vs. player cyber concerns, the games industry still has to deal with all the other security challenges facing the world. We all know that fiduciary-fueled attackers follow the money, and this industry might as well advertise itself with neon dollar signs.
Cyberthreats are not always technical (as we well know!) and nefarious behavior isn’t exclusive to attackers. Some mobile game ad targeting could be seen as malicious, or even unethical, though not illegal. But, of course, that describes advertising in general; it’s not specific to the games industry. Regardless of their intent, the targeted ads affect the spending habits of players, which, in turn, affect where the threat actors head next.
Subscriptions
Game publishers can expect to dole out millions of dollars to create a triple A (AAA) title — and that cost trickles down to the consumer. The jump from US$60 to US$70 per title is not insignificant, and can affect a budget-conscious gamers’ decision on when (or if) to buy a game outright, especially with the multitude of subscription services available.
As in similar media genres, subscription services reign supreme in the gaming world. The sheer number of games on the market makes it financially unfeasible to purchase them all. Including mobile options, there are more than a dozen gaming subscription services available today, all fighting for a piece of that US$11.7 billion dollar pie.
Attack arithmetic
Let’s do the math: more subscription services = more user accounts = more opportunities for credential stuffing or account abuse. And with more brands to impersonate, there is more content for threat actors to mimic for phishing campaigns or other scams.
Subscription fatigue is real, and it gets costly. There’s also the issue of physical or virtual storage space that must be accounted for.
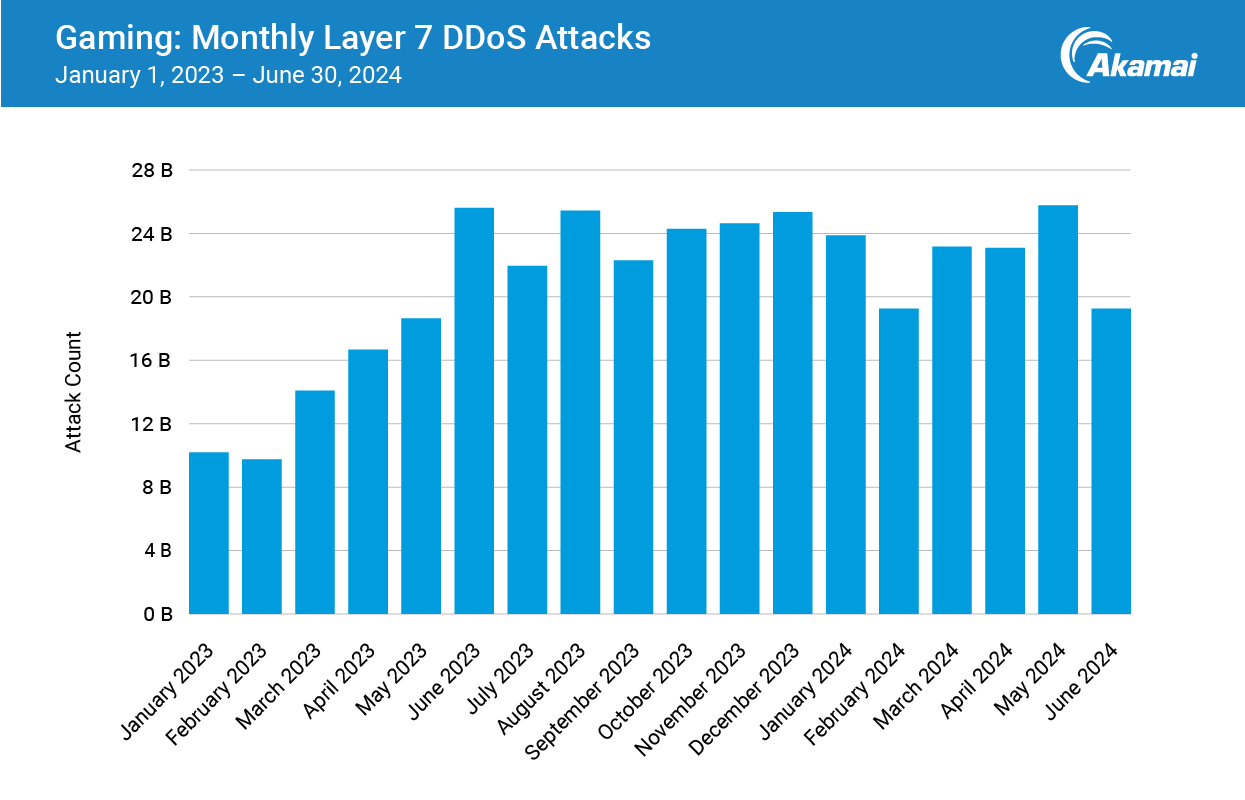
Layer 7 DDoS attacks climb the leaderboard
Layer 7 distributed denial-of-service (DDoS) attacks have increased by 94% year over year. The attack numbers remain high: 4 of the 18 observed months (June, August, and December 2023, and May 2024) saw more than 25 billion Layer 7 DDoS attacks over the course of that single month (Figure 1).
January through March 2023 experienced the lowest number of assaults on Layer 7, with less than 15 billion monthly attacks each. The upward trajectory of this vector is wild: The dip in February 2024 was the lowest number of monthly attacks in 2024 so far, at more than 19 billion — which means that the lowest number of monthly attacks in 2024 to date is still higher than the number of attacks in January, February, March, and April of 2023.
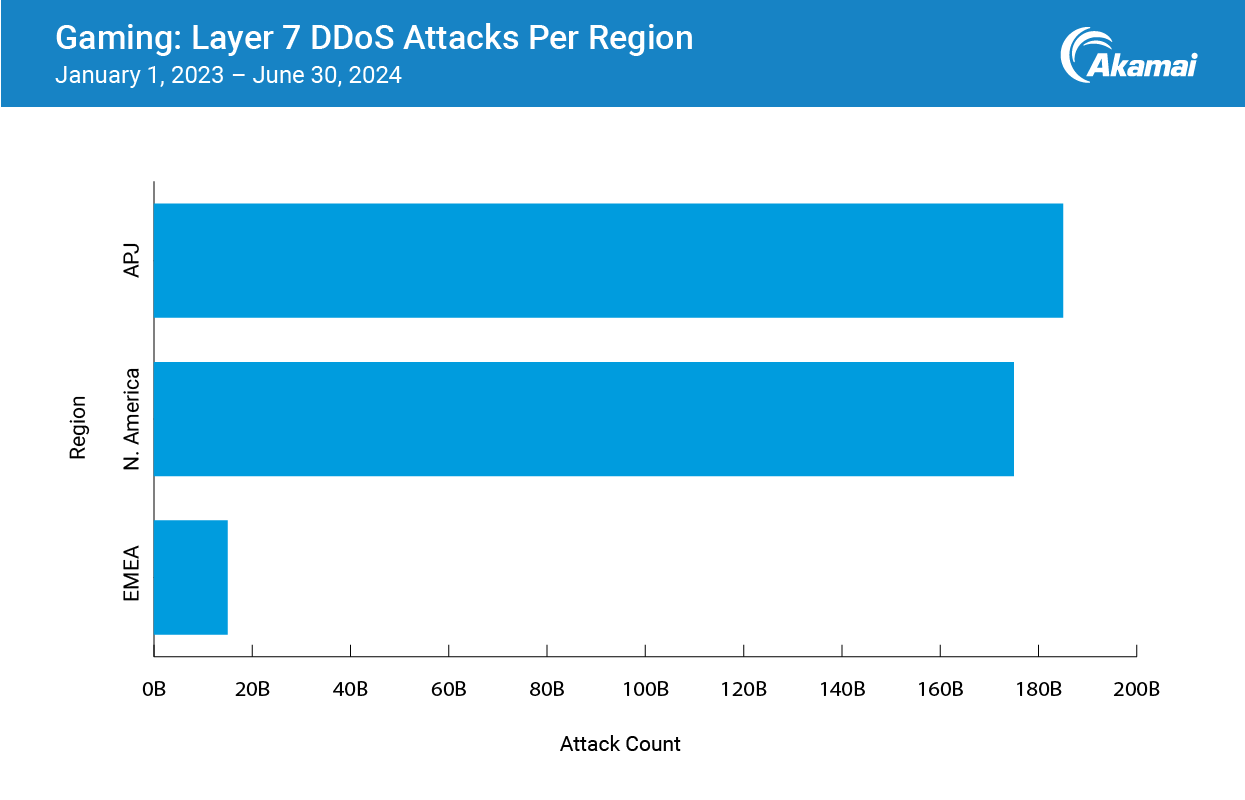
APJ sweeps the Layer 7 leaderboards
Considering the Asia-Pacific and Japan (APJ) region had the highest global revenue for the games industry in 2023 (US$85.8 billion) and the 179 billion players in that region alone account for 23% of the population, the impact of APJ on the industry is colossal.
This year, the overachieving APJ region added the most Layer 7 DDoS attacks to their decorated careers with 186 billion attacks in the last 18 months (Figure 2).
Prime times for bot requests
You can’t discuss security without talking about bots; they are prevalent in just about every industry. The goals of a botnet author, however, can differ greatly in the games vs. the finance (or other) industries, and the functionality the bot seeks can help us determine many things about the botnet author itself.
The time of year is another factor in attacker behavior. The following times seem to be especially prone to bot requests.
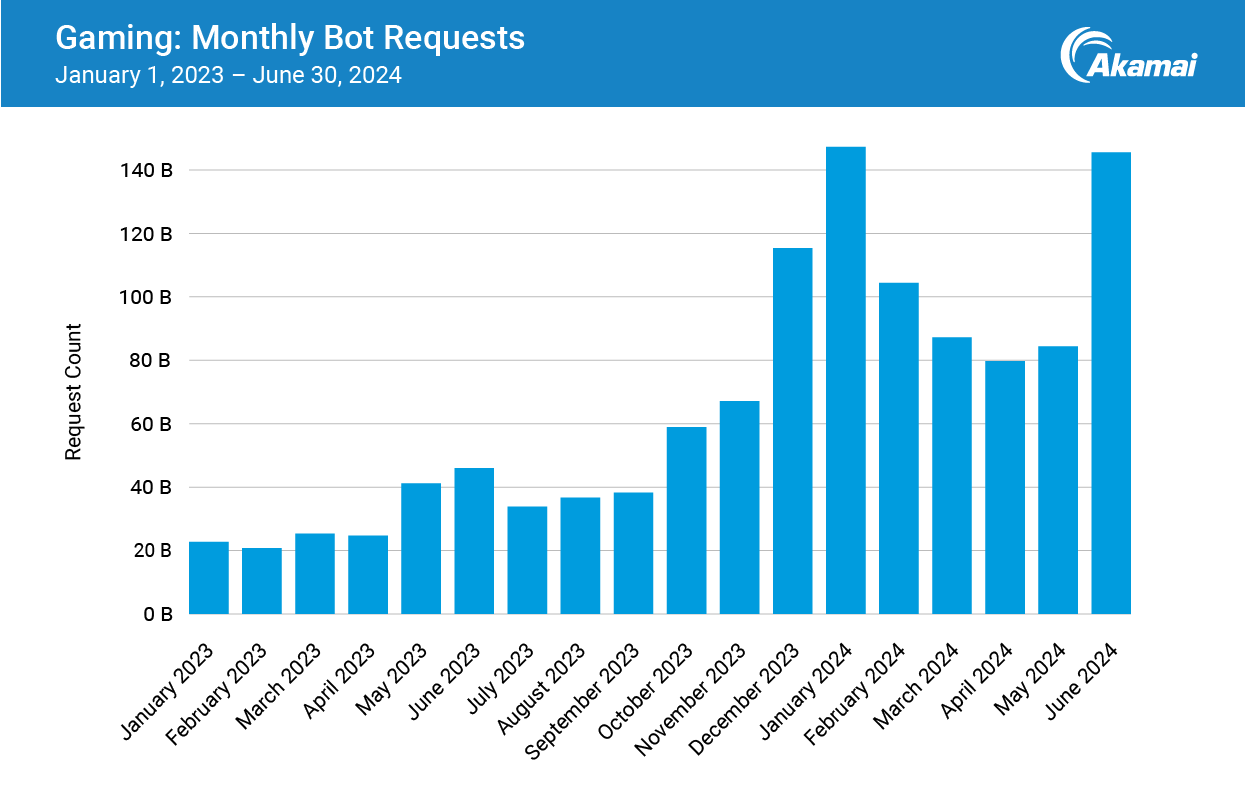
January and June
Bot requests saw a 391% growth from Q1 2023 to Q1 2024. They met that mark early — 2024 started with a record number of bot requests in the games industry: 147 billion. In one month (Figure 3).
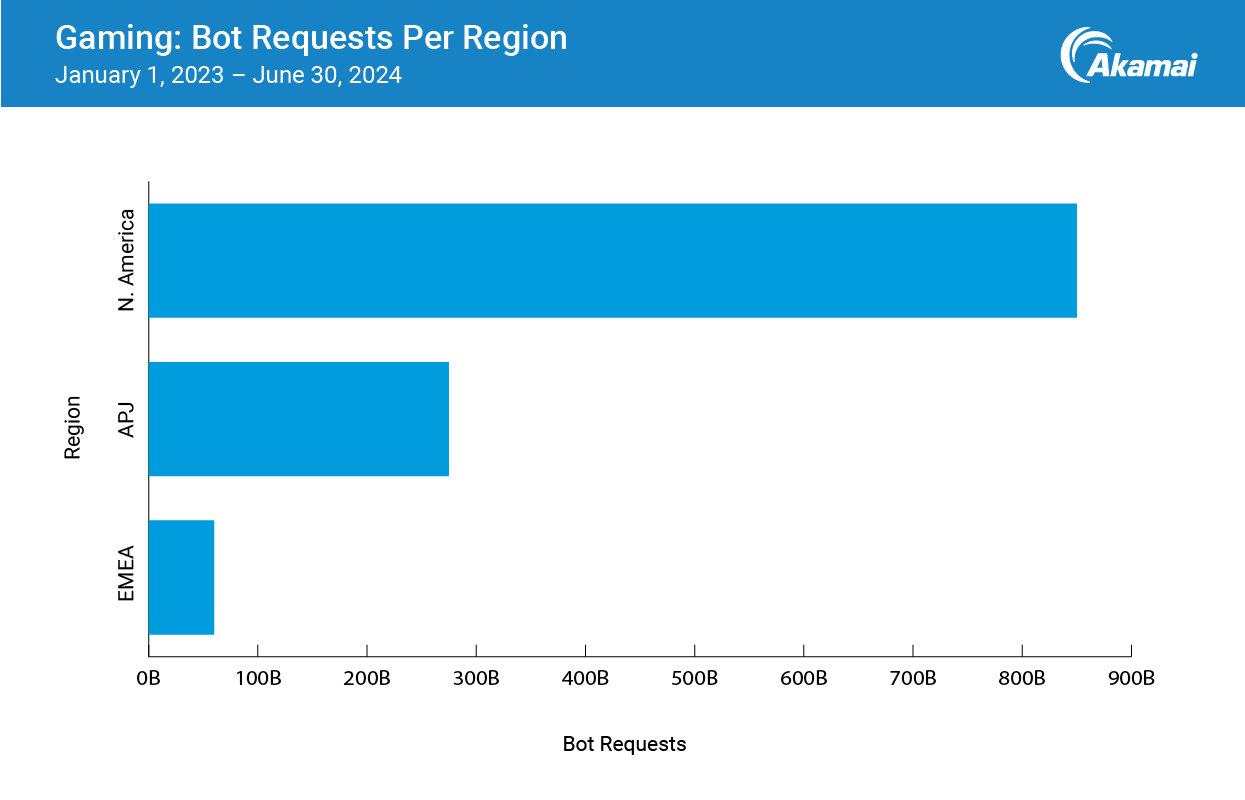
June gave January a run for its money (145 billion), more than tripling the amount in June 2023. To put those numbers into perspective: For the entire observed period, the Europe, Middle East, and Africa (EMEA) region only saw 59 billion bot requests (Figure 4).
Summer and winter
Since the Steam Summer Sale happens every June and July, it is likely these two months will continue to see gobs of bot traffic. This theory is supported by the mimicked trend for the months of December 2023 and January 2024 — Steam Winter Sale time. This theory is also supported by the fact that the most bot requests originated from North America — 845 billion, to be exact.
These two periods (June/July and December/January) tend to show increased online activity during heavy spending seasons, making them lucrative times for attackers to pounce. The gamers themselves, as well as the game companies, are especially under digital siege during those periods.
Web application firewall attacks
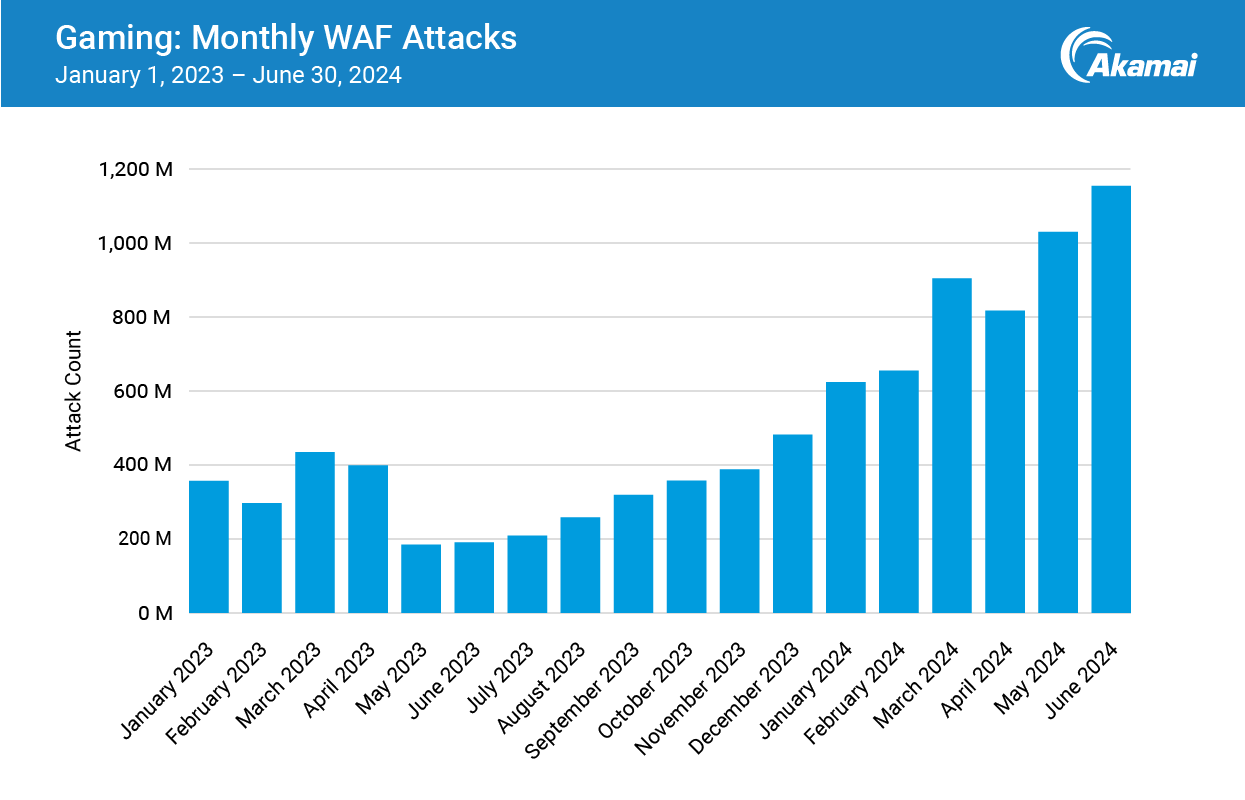
Web attacks in games grew by 94% from Q1 2023 to Q1 2024. The most steady increase was in web application firewall (WAF) attacks. After the dramatic drop in May 2023, you could draw a decently consistent upward trend month over month. June 2024 is currently topping out at 1 billion (Figure 5).
May and June 2024 saw mind-boggling increases over last year, at 451% and 504%, respectively. We expect these numbers to continue upward as application and API use increases.
Break it down for me, fellas: Traditional web attacks
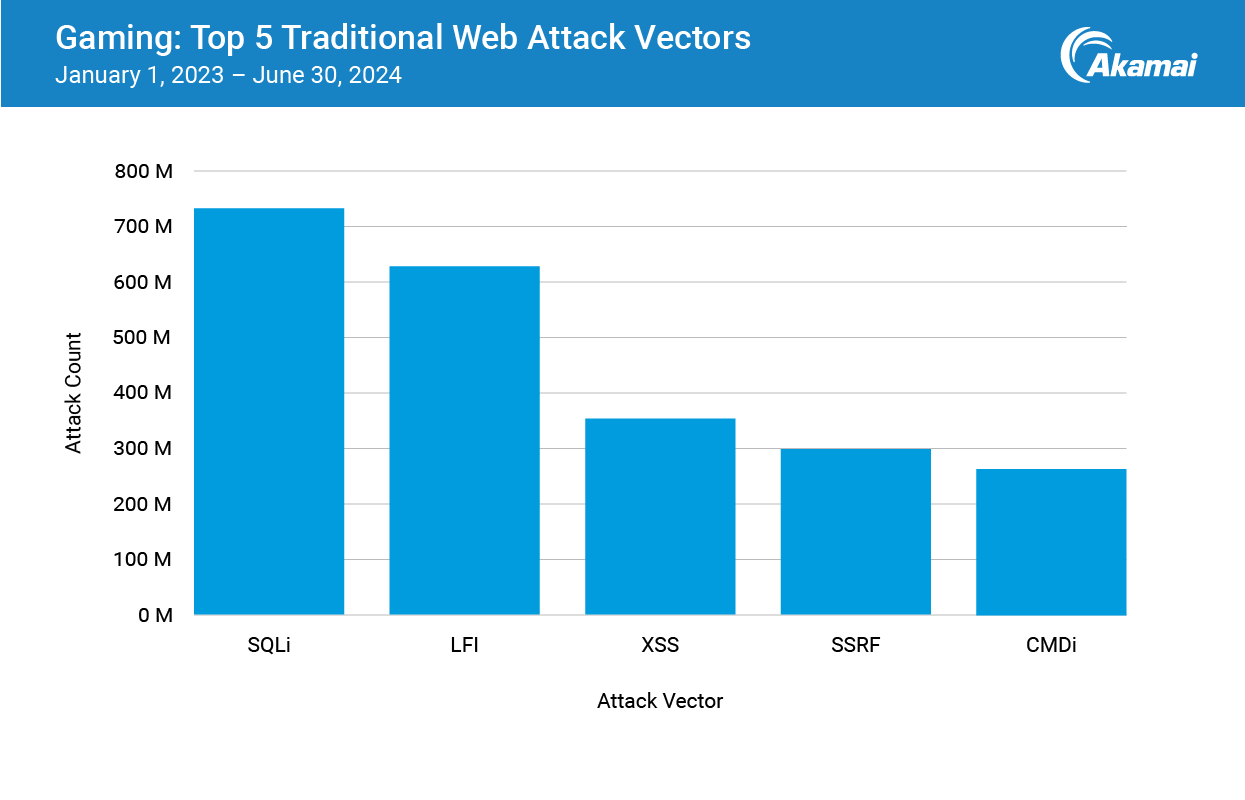
When we break these numbers down further and look at only our traditional web attacks (Structured Query Language injection [SQLi], command injection [CMDi], local file injection [LFI], cross-site scripting [XSS], remote file inclusion [RFI], and server-side request forgery [SSRF]), we see that SQLi was the largest web threat to the games industry during the observed period, with more than 700 million attacks (Figure 6). This isn’t exclusive to games companies, either — SQLi can put you at the top of the leaderboard as a gamer too.
LFI has been steadily increasing across industries in the past several years. It can lead to other web-based attacks (such as XSS) and, in some cases, can lead to remote code execution. It’s certainly something for a games publisher to look out for.
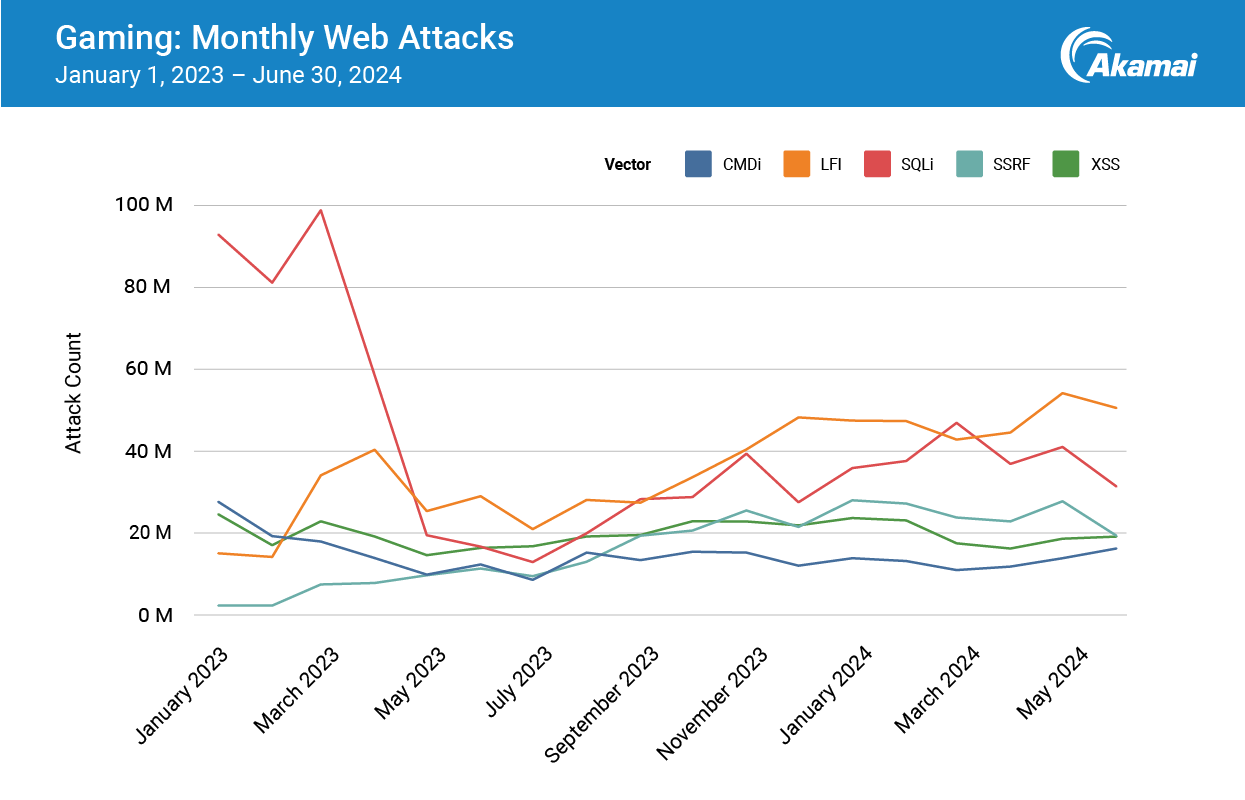
SQLi wasn’t just the leader — it was also the most staggeringly sporadic, which speaks to the nature of games. Figure 7 shows a monthly breakdown of the numbers shown in Figure 6, and the SQLi trajectory could make you as motion sick as a jerky first-person player.
Q1 2023 saw a rapid release of games that were part of the COVID-19 backlog. The continued push back of release dates as a result of the pandemic has increased the demand for these titles, which likely contributed to the severe increase of SQLi during that time. The sporadic nature of SQLi also could speak to differences in the attackers’ goals.
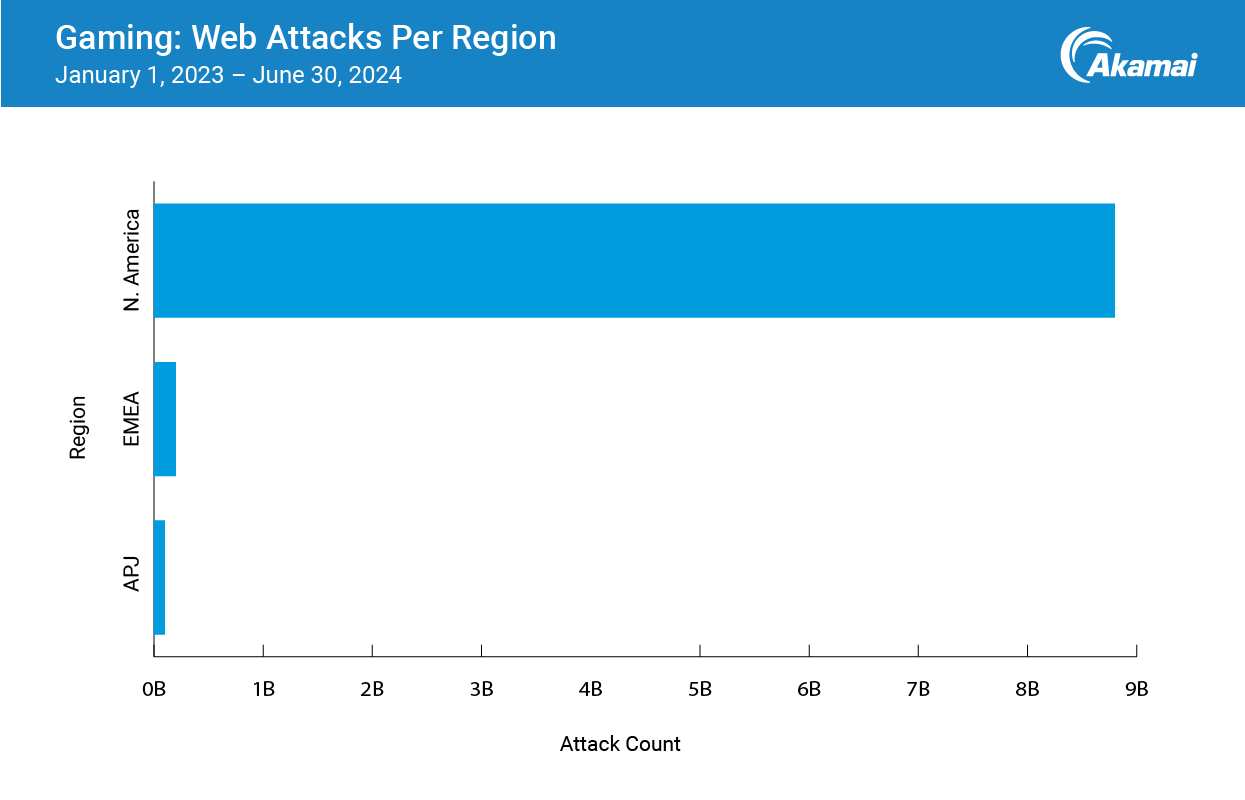
North America sees orders of magnitude more web attacks
It’s hard for humans to fathom the difference between 1 million and 1 billion, nevermind the vastness between 332 million and almost 9 billion. That is the combined gap between the number of web attacks in EMEA and APJ vs. North America between January 1, 2023, and June 30, 2024 (Figure 8).
Roll the credits
Gaming and other nerdtastic genres often inspire real-world innovation on both the micro and macro levels. From cosplay to self-driving cars, luxuries and lifestyles from the digital realm have been brought to life thanks to the games community.
The more digital our lives become the more valuable these games skills are to hone, and they can have positive effects on your career. Video games require a level of curiosity and problem-solving that is absolutely transferable into corporate success, and companies and universities alike are taking notice and acting accordingly.