Dogged Persistence— The Name of the Game for One DDoS Attacker

With DDoS, we typically observe a moderate degree of attacker persistence.
DDoS attacks are relatively easy to launch from a number of online booter services, and the availability of cryptocurrencies for payment has made it easy to remain anonymous. Attackers can try their hand at DDoS for little effort and money, and in relative safety. They give it a go, try a few things (vector, endpoint, and scale changes), and for those with effective defenses, the attacker eventually burns out.
This changed with DDoS extortion campaigns launched primarily between fall 2020 and late spring 2021, which were a pure numbers game.

Attackers cycled through entire industries, launching proof-of-capability attacks en masse against a wide swath of targets, hoping to elicit payment in exchange for a promise not to launch future attacks. Companies that successfully mitigated attacks were generally left alone, as the extortionists moved on to softer targets.
“Once in a blue moon” attack campaign
Every now and then, however, we do see extreme examples of DDoS attacker persistence. This was the case starting late last month (July 2021). What made this particular series of DDoS events notable is not only the determination, but also the attack vector sizes targeting multiple IPs across several of the customer's subnets.
Several distinct waves can be noted over the 10-day span that targeted the various endpoints using a diverse array of DDoS tactics and techniques. While the attacker was highly motivated and had massive amounts of bandwidth to burn, nearly all of these attacks were automatically mitigated via Prolexic's zero-second SLA. Those that weren't were dealt with swiftly by the Akamai SOCC.
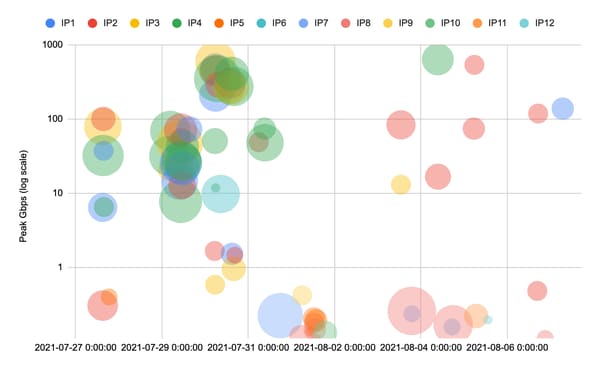
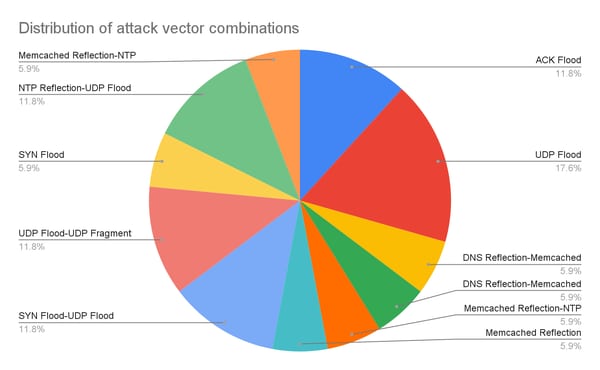
The attackers threw in the kitchen sink as they pivoted across multiple IPs and employed a number of attack vectors and combinations whilst attempting to find weak spots. Both TCP and UDP stacks were targeted almost equally, and the criminals used a combination of 11 different vectors during the various assaults.
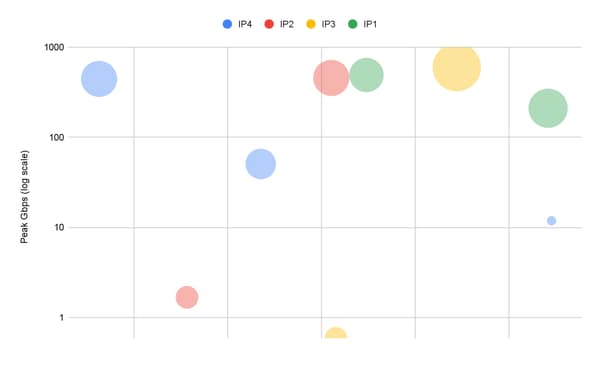
The threat actors clearly had access to the DDoS attack cannons. One 30-minute span saw 200+ Gbps spread across six destination IPs, with the top target reaching 600+ Gbps.
With attackers ramping bandwidth from 0 to 100s of Gbps in under a minute and pivoting multiple vectors and endpoints on a whim, cloud-based DDoS defense — with automated and proactive mitigation controls in place — is the most effective way to fight back.
A closer look at the attack campaign by the numbers
Duration |
10 days |
Destination IPs Targeted |
12 |
Distinct Attack Events |
156 |
Distinct Attack Vectors |
14 |
Peak Gbps |
600.9 |
Peak Mpps |
53.1 |
Average Attack Event Duration |
13.8 minutes |
Max Attack Event Duration |
80 minutes |
Mitigation Outcome |
95.3% 0-second SLA proactively mitigated |
Our takeaway
While we have customers that are attacked daily -- even hourly -- we also have customers that are seldom targeted. This specific customer falls in the middle, averaging about six DDoS attacks per month.
The level of persistence for this particular campaign highlights the importance of a well-oiled defense against motivated DDoS attackers, who not only can turn up the heat in terms of high-volume attacks but also are very nimble in pivoting their TTPs (tactics, techniques, and procedures). These types of attacks highlight the need for skilled security responders that can quickly mitigate attacks that would be considered more "zero day" for the enterprise.
DDoS attacks in particular also represent a growing trend with respect to the threat actor's arsenal of exploits and tools -- they are more readily available and powerful than ever before -- a combination for network defenders to take note of and prepare for as barriers to entry remain low.





