Compromised Enterprise Devices Detection Based on Abnormal Behavior Patterns— UEBA in Action

Recently, many reports of incidents have been making headlines, proving that no business or industry is immune to advanced threat actors. Applying user and entity behavior analytics (UEBA) for the challenging task of the detection of compromised devices over time can play a critical role in your defense mechanisms. In this blog, I'll showcase a newly-developed algorithm called MORTON, which aims to detect devices that are engaging in malicious Domain Name System (DNS) behavior.
Until recently, our focus was on finding an indication of compromise via a domain or URL in order to increase our DNS\HTTP proxy blocklist, and from there infer that a device is being compromised. However, Akamai has added substantial improvements to our defense toolsets with the indication of compromise based solely on the behavior of devices.
After malware has been downloaded and executed on a device, delivered mostly by spam and phishing emails, the device effectively becomes part of a botnet (see Figure 1). The attacker exchanges control messages with its bots through a command and control (C2) channel, sending instructions to perform attacks, such as data theft or distributed denial of service (DDoS).
 Fig. 1. A common infection chain
Fig. 1. A common infection chain
Existing systems and techniques for detecting compromised devices rely heavily on signatures of known attacks, such as file hashes of malware or predefined rules. Some of these well-known techniques include the use of Yara rules, designed for the detection of malicious files during a scan, or Snort rules, designed for the detection of malicious network traffic. However, the main drawback of these techniques is that they are only able to detect adversaries who use known malware and common exploitation frameworks.
In order to deal with these attacks and mitigate them, we seek to identify enterprise devices with anomalous behavior patterns, thus aiming at the detection of suspicious activity and not only known malicious TTPs. This approach is widely known as UEBA.
UEBA is a general term for tracking the behavior of users and devices over time and identifying suspicious activity. For example, if the regular working hours of a particular device are daytime business hours, but suddenly it connects in the middle of the night, the system would be able to detect this anomaly and alert you to the potential security threat. Akamai's UEBA approach involves monitoring various sources of our customers' network data, observing the behavior of their devices, and applying algorithms to identify the anomalies.
One of the algorithms we developed is called MORTON, which detects dozens of different threats every day in enterprise networks based on the existence of automatic routine DNS communication between devices and disreputable hostnames (C2).
MORTON leverages an efficient signal processing technique called power spectral density (PSD) and a deep-learning model for final classification. The algorithm transforms the input, a time series of outgoing DNS queries made by the device, to a PSD vector that characterizes the intensity of periodic communication at various frequencies.
A PSD vector can be thought of as the intensity of the rate of events at particular time frequencies. Accordingly, a frequency entry within the PSD vector that has a high value indicates a routine event occurring within that frequency. Figure 2 shows a demonstration of PSD graphs as a function of frequency for two types of devices. On the right graph, a circled spike indicates that the device has a process communicating with an external server in a periodic manner; on the left, a non-compromised device shows low values across all frequencies in the PSD vector.
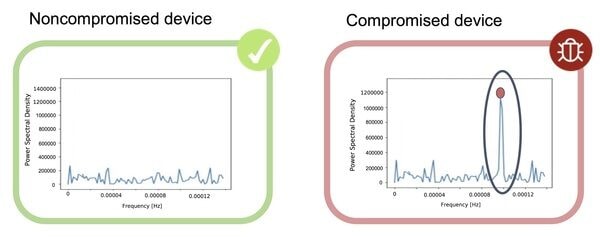 Fig. 2. PSD graph of a non-compromised device vs. a compromised device
Fig. 2. PSD graph of a non-compromised device vs. a compromised device
Once we compute a PSD vector embedding for each device, we use these vectors as an input to a feedforward neural network, a classification model that will decide whether the device is compromised. With the help of MORTON, we can identify dozens of various threats every day that leverage the automatic communication techniques.
One of the detected threats is Zusy. Zusy, also known as TinyBanker or Tinba, is a powerful Trojan that uses man-in-the-middle attacks to steal banking information and is very hard to detect. Zusy injects itself into other system processes in an attempt to convert the device into a zombie, or a compromised device that is now part of botnet.
Upon infection, the Trojan obtains sensitive data by viewing packets passed between the browser and the server or by creating a fake form that requests login information for the bank after the user accessed the legitimate website and sends that data back to one of its C2 servers. In order to maintain connection with remote servers, Zusy is known to maintain a list of hard-coded domains to use as fallback if one of the C2 servers goes down or loses communication. To showcase the detected automatic routine of DNS traffic that was generated by a device compromised with Zusy, Figure 3 describes the number of DNS queries being made to its C2 servers through four different domains over time.
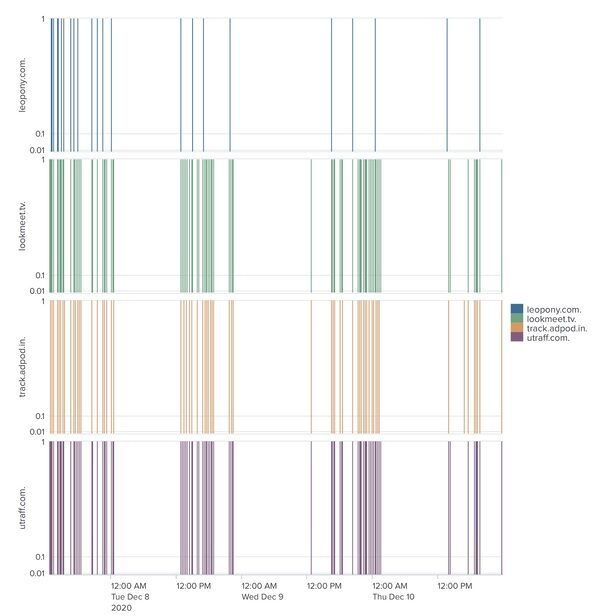 Fig. 3. Outgoing periodic DNS requests made by enterprise device to four different C2 domains related to Zusy threat as observed on Akamai's platform
Fig. 3. Outgoing periodic DNS requests made by enterprise device to four different C2 domains related to Zusy threat as observed on Akamai's platform
This detection sparked further interest and an investigation by our Security Operations Command Center (SOCC) team to understand the nature of this suspicious activity. Figure 4 depicts an investigation into this use case using VirusTotal (VT). Every blue globe represents a domain name, and every red file represents a file that's been observed communicating to that Internet Protocol (IP) and detected as malicious.
 Fig. 4. Analyzing the detected hostnames using VT
Fig. 4. Analyzing the detected hostnames using VT
As seen in Figure 4, the VT investigation shows that there are three specific malicious files that are communicating with three of the four domains that were detected by MORTON. The three malicious files are all labeled as Zusy by the security engines in VT. Now that we have attributed this suspicious activity to Zusy, the SOCC team can mitigate that threat.
To summarize, applying UEBA solutions can drastically advance all enterprise defense capabilities by managing and enhancing detections, stopping the latest threats, and identifying out-of-the-ordinary activity.
If you wish to learn more about the algorithm, our researchers recently published a full academic paper in collaboration with Ben Gurion University of the Negev.



