Yes, My Name is ||
Boolean operator
Different cultures and nationalities have different naming conventions; I came from a one that led me to face the universe with a personal name "Or". I fact, my name has different meanings in different languages. In English the meaning of "Or" is function word that indicate alternatives and in computer coding languages the name "Or" is being used as Boolean operator that enable us to write conditions in our code.
So, Yes, I'm having hard time introducing my name to English speaking people, and yes, appending comment with my name in source code that I have written creates ambiguous meanings once being read by other coders!
But this time it has gone too far...
How to overcome the pain of rejection
Recently, I tried to join a well-known, chain-brand hotel's members club and got rejected.
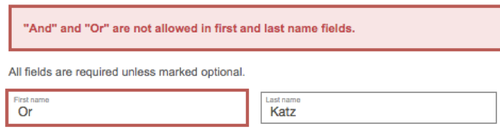
Apparently "Or" can't be used as first name in the submission form. The shame, the insult, the rage, all those feelings emerged each at its time, but after a while when I came to my senses. I let my security researcher instincts take over.
Code injection
In order to understand the reason why I was rejected, I looked at the returned error message once again, and things got much clearer, it is not personal!
The hotel Web application is checking that the Boolean operators "or" and "and" are not being used as first/last name.
In order to validate this assumption, I decided to re-send my registration request with another representation of "or" Boolean operator. This time I used special character, pipe ("|") in the first name form field, as I suspected the Web application rejected my request with the following message:
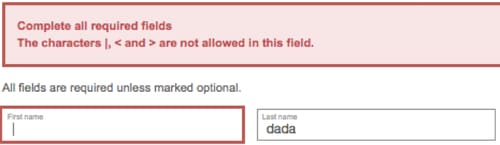
The reason why we see this kind of text validation is related to the presence of security controls such as Web Application Firewall (WAF), responsible for filtering out any indications of code injection being sent from the client to the server.
Code injection payloads can abuse Web application functionality and can lead to variety of security issues such as: information leakage from Web Application Database, authentication bypass (SQL Injection) and in other cases to injection of malicious code being executed on users' browsers (Cross-Site Scripting, also known as XSS).
Oh boy, here I come...
Here comes an interesting twist in story's plot; they made a mistake and rejected the wrong guy!
Being a security researcher with years of experience writing WAF defensive rules designed to stop code injection attacks gave me the ability to evaluate the security control I'm faced against. Therefore, I decided to register again but this time with different personal name; one that also has a Boolean operator code contextual meaning, "xor" (also known as exclusive or). If "or" is not be permitted to join the party then one would expect that "xor" is neither. But guess what? Registration was approved, those bad feeling reemerged...
I also verified other keywords related to variety of code injection scenarios many of those were accepted.
Let's get serious
It is time to be serious and say what is obvious to me but apparently not to all, if you really want to protect your Web server from Web applications attacks, make sure you constantly evaluate your Web Application Firewall.
Make sure that mitigations for all attack vectors are covered, constantly being updated and being deployed in front all of your Web assets; at the same time, monitor triggered alerts, make sure that there are no false detections and that customers are not being... rejected.
So if you see me down the street just call me ||, and if I want to sign-in to your Web application, PLEASE let me in.
P.S. Or in Hebrew means light, I hope this blog post was enlightening.



