XMR Cryptomining Targeting x86/i686 Systems

I have been playing close attention to Internet of Things (IoT) malware targeting systems with Telnet enabled, while also collecting samples targeting systems with SSH enabled on port 22. I've collected over 650 samples landing in my honeypot within the last week. The earliest sample showed up on July 24th at 20:06. The honeypot allows logins using known default login credentials for root.
The malware is uploaded as gzip compressed tarball archives of binaries, scripts, and libraries. The libraries reside under the directory c/lib I thought it would be required to run the binaries in the tarball, but the binaries are compiled statically, so the libraries are extraneous.

The tarball contains three files and three directories under the rsync directory. The three files are shell scripts with the init and init2 being called from the main script initall. First, these scripts clean up previous crypto miners that might be running on the victim system.
Below is a screenshot of initall that does the clean up.

Then the script executes init2 if the directory .firefoxcatche (sic) doesn't exist. This is a check to see if this crypto mining software has already infected the victim. If it has, the script will exit with the command exit 0, else the script executes init2.
Then the script init2 kills any previous versions of the miner software that might be running, and installs itself. It also adds entries to crontab in order to ensure that the miner remains running even after a reboot.

Notice that binaries out of all three directories are run from the init script. Each directory contains a variation of the XMrig v2.14.1 cryptocurrency miner in either x86 32bit or 64bit format. Some of the binaries are named after common Unix utilities, like ps, in an attempt to blend into a normal process list.
The file b/run is a perl script that has base64 encoded text that decodes to a packed string, which is then evaled to the actual perl code. The perl code is a modification of a script on GitHub.
The modified shellbot script, packaged with the miner, contains the same features as the original shellbot script. It has command and control via IRC, DDoS, and port scanning functionality as illustrated by the code block below.

List of available functions.

Perl code for UDP flooding functionality.

Code for a full port scan of a target host.

Sample of code for quick port scan of most common ports.
$ file 3b0c38985b19be1e1f1adfa4e95d14921c66ef18f199b8addf67233bcd076334.tgz
3b0c38985b19be1e1f1adfa4e95d14921c66ef18f199b8addf67233bcd076334.tgz: gzip compressed data, last modified: Wed Jul 24 14:48:00 2019, from Unix

XMrig v2.14.1 renamed to anacron in order to evade detection.
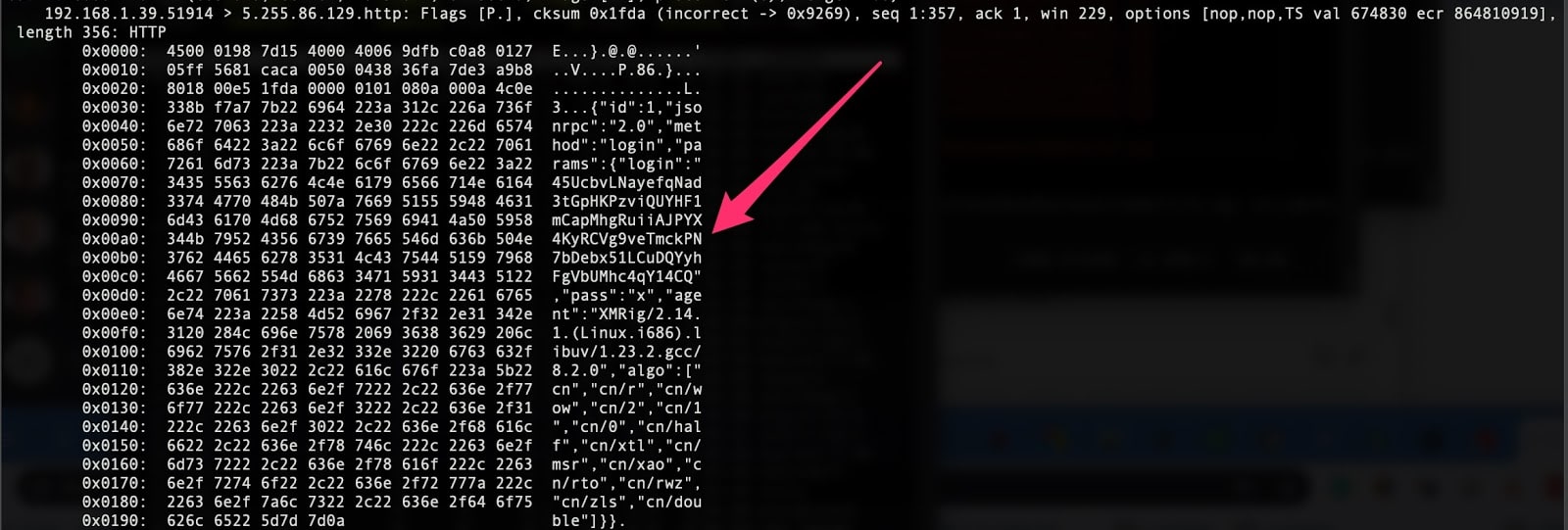
We can see traffic between our infected host and the xmr pool:
The attack originates from a pretty wide IP distribution with clusters in the Americas, Asia, and Europe.

Conclusion
Criminals will continue to monetize unsecured resources in any way they can. System administrators need to employ security best practices with the systems they manage. Unsecured services with unpatched vulnerabilities or weak passwords are prime targets for exploitation and abuse. Strong passwords, a vulnerability remediation plan, and two factors of authentication can go a long way to keep systems secure from the most basic and common attacks.



