The Oracle of Delphi Will Steal Your Credentials

It was one of those warm summer nights, no clouds, just a bright full moon lighting the way. Someone had unknowingly stumbled upon our honeypot, completely unaware of the fact that her every move was recorded and fully analyzed. Thanks to our deception technology, we could easily reroute the attacker, making her believe she reached her real target. Something about this attack was different, though. All originating from the same source, the attacks repeatedly used brute force passwords for RDP credentials to connect to the victim machine, download and execute a previously undetected malware, which we named Trojan.sysscan. This is a new malware capable of running on every Windows version from XP through Server 2012 R2.
Attack Description
Trojan.sysscan, written in Delphi, has extensive capabilities to search and extract cookies and other credentials containing authentication details such as usernames and passwords targeted at banking, gambling and tax websites as well as information saved by Point of Sale (PoS) software. By stealing connection details, our attackers can easily steal identities and large quantities of money.

The attacker at work
Persistence
The malware can function both automatically and manually, depending on the configuration. If the malware runs as administrator, it will establish a persistent backdoor by adding a hidden user to the list of administrators with a known password using a known technique. It will then make sure RDP is accessible, on both desktop and server versions of Windows using the known RDP wrapper library which is packaged inside Trojan.sysscan.
Collection and Exfiltration
In addition to collecting credentials, Trojan.sysscan collects vast amounts of computer metadata. Borrowing a technique from Trojan.Barys, it recognizes when it’s being investigated by a security tool or run under a virtualized environment which allows the attacker to realize if they had been caught in a honeypot or sandbox. This information is collected and not directly acted upon, showing that at this point, attackers are not worried at all about being caught in endpoints or by scanning tools.
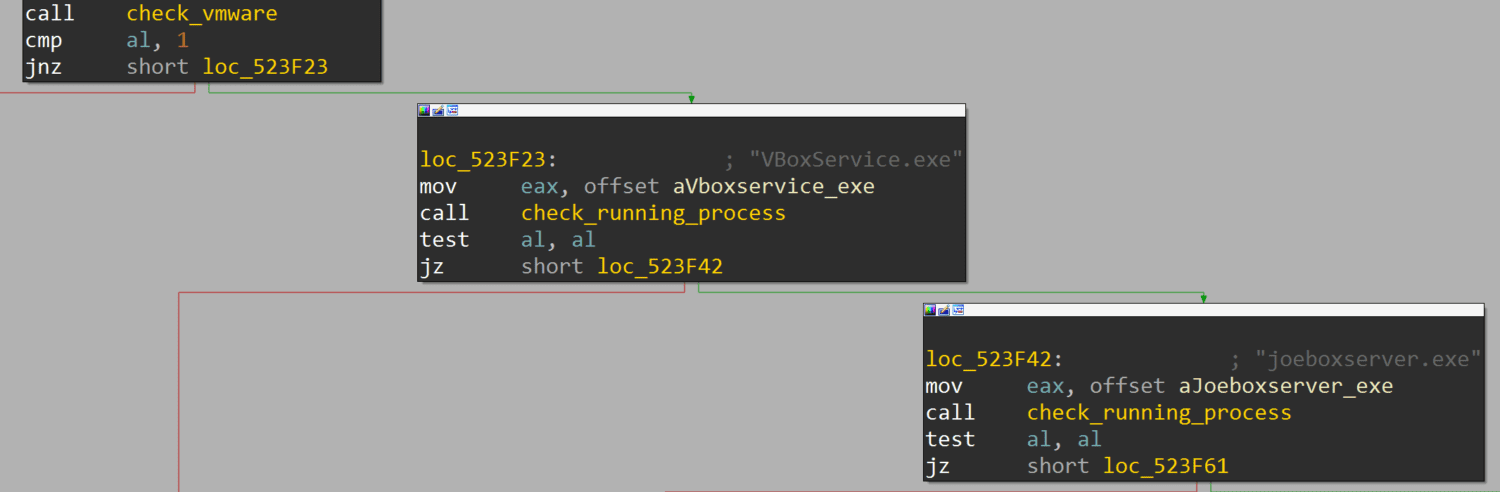
The malware thoroughly checks it’s not running in a researchers sandbox
To collect the credentials, the malware exhaustively scans the entire C: drive of the victim and the registry, searching for cookie files, SQLite databases and registry keys that match an internal database. Once found, the data is copied and exfiltrated. If the victim does not keep personal data on the drive, the malware won’t find it.
The primary method of exfiltrating data is by communicating with an exfiltration server (85.93.5.43) using a HTTP POST message over a non standard port (12421). This server is known to be the destination of many different malwares. If the Trojan is run interactively and fails to communicate, the attacker can copy the results to the Windows clipboard and then over RDP, copy it locally to their computer.
Detection and Prevention
During our investigation, we discovered that the sole attacking source known to us is the IP 144.76.137.166, which belongs to a Spanish hosting company, okITup, and has been observed performing a series of identical attacks. In none of the attacks did we observe this Trojan being dropped using an exploit, nor have we seen it packaged with any known droppers. This means that at this stage, prevention involves the use of strong password authentication to prevent brute force attacks.
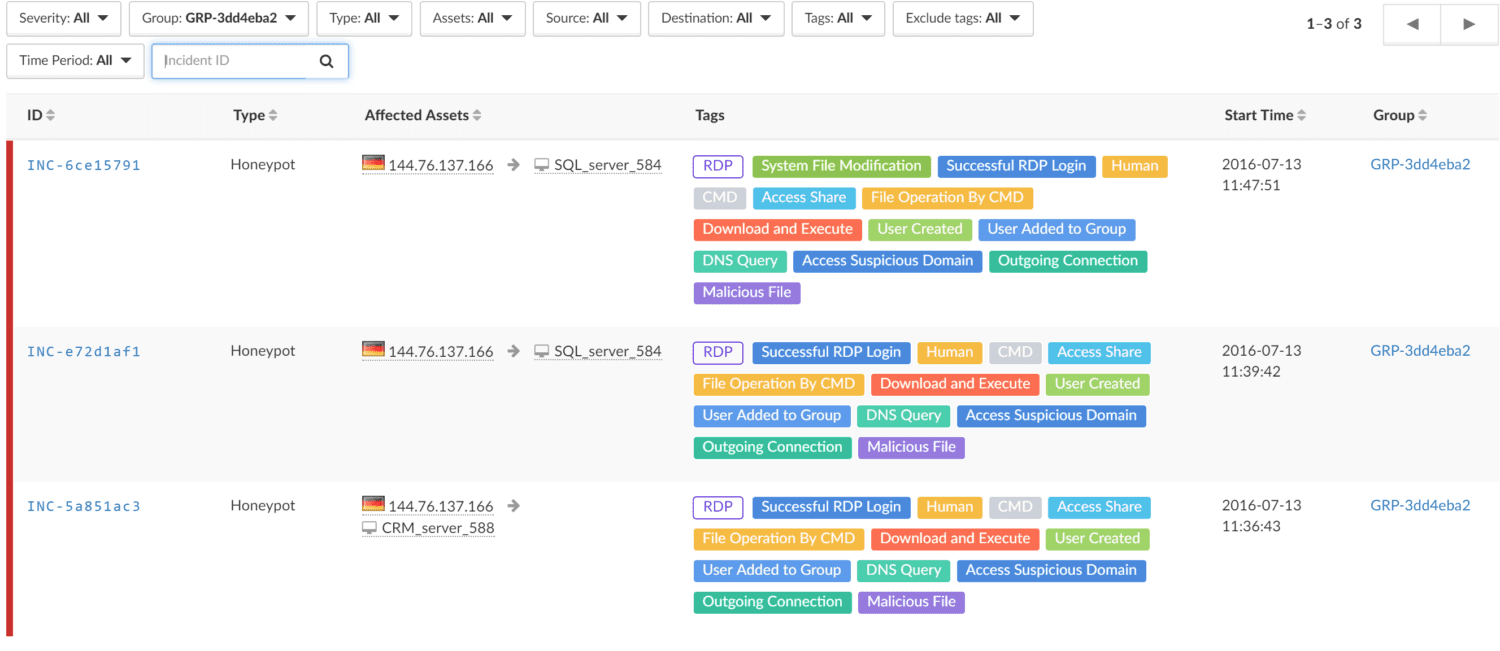
The series of attacks
At this point, Trojan.sysscan is undetected by the vast majority of antivirus engines as a malicious software. Malware that requires command line parameters or other user input is hard to investigate in a sandbox and Trojan.Sysscan does not use any possibly malicious system calls. This makes it hard on the antivirus to conclusively decide whether the executable is malware. Detection therefore is limited to checking for hidden accounts and whether the RDP wrapper library is installed. Detection of this malware requires modern security software built for defense in depth, assuming a breach, detecting and mitigating it, for example one that can detect the search and exfiltration of sensitive data.
Conclusion
Trojan.sysscan is an example of a credential stealing Trojan, backdooring machines and exfiltrating large amounts of credentials. Unlike other types of Trojans that have a specific goal like currency mining, the purpose of this malware is stealing credentials, making it particularly dangerous to large organizations. Trojan.sysscan evades detection easily which unfortunately is not unique. The usage of Delphi, while not a popular language, provides the coders with versatile frameworks that simplify their code as it allows them to use 3rd party libraries that perform many tasks for them, such as communication, computer scanning and metadata extraction.
Modern data centers and corporate networks provide fruitful ground for malware to flourish. Newer techniques are required to provide effective security in those environments, such as the kind of deception and honeypot technology we develop.
Indicators of Compromise
Files
Filenames: csrss.exe, sysscan.exe
MD5 4f b7 ac 01 3b 7c ff ff 3c 78 2d 15 03 30 eb 32
SHA256 31 83 3c 4b 17 9c 4e 4d e4 49 32 c5 7d eb fb 65 62 bb 6e 83 3d 9f d1 41 5f ee 64 11 aa ce a4 5b
IP Addresses
- 144.76.137.166
- 85.93.5.43



