From Good to Great: Mastering Day-2 Network Security Policy
Creating an initial segmentation policy is just the beginning of effective network security. The continuing challenge lies in adapting it to close hidden gaps, reduce risks, and address changes both inside and outside your network. Factors like new applications, company growth, and migrations can disrupt established communication patterns. New CVEs, evolving attack campaigns, and third-party software can introduce new risks.
An effective network policy is dynamic by design — it should adapt to the environment, not force the environment to conform to it. Effective security demands ongoing fine-tuning.
7 use cases: Day-2 policy optimization
The Akamai Hunt team specializes in day-2 policy optimization; that is, helping our customers refine their segmentation strategies by identifying common policy gaps and providing proactive monitoring and actionable recommendations.
In this blog post, we will explore seven use cases we’ve seen in customer environments that can elevate your segmentation policy, including:
Overly permissive rules
Overly permissive rules often present a significant challenge in segmentation policies, allowing more access than necessary and increasing the network’s attack surface. To identify these rules, look for patterns like "allow any/any," overly broad IP ranges, or wide port ranges. Once identified, these rules should be tightened by defining specific source and destination IPs, restricting ports to those required for business needs, and implementing least-privilege principles.
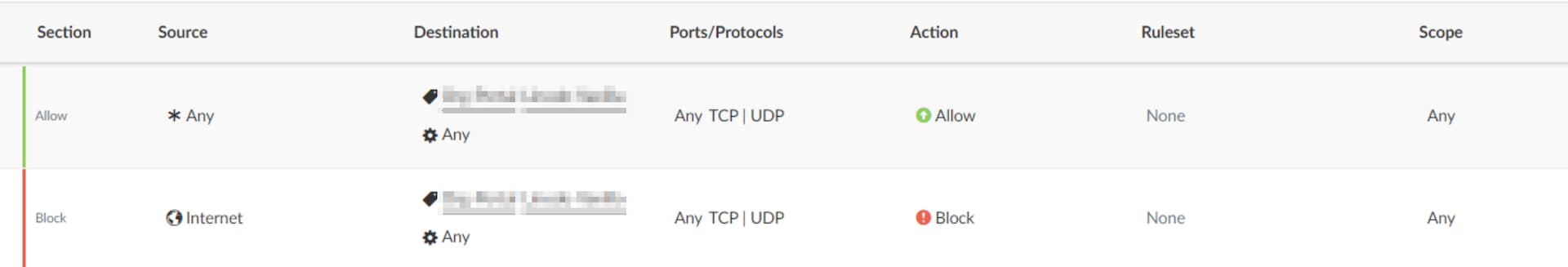
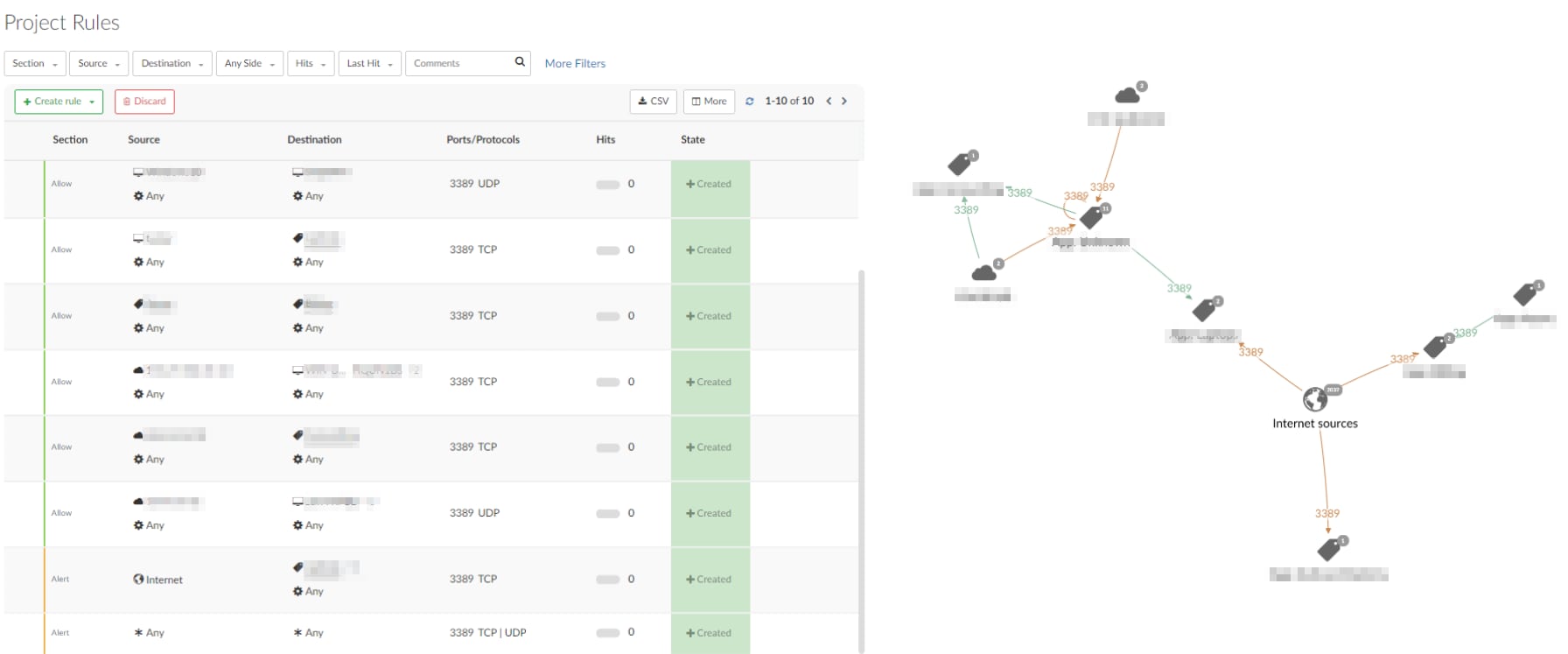
The Akamai Hunt team recently encountered the use case shown in Figure 1. Overly permissive rules not only create risk directly, but also can indirectly work against other security policies. In this customer’s environment, a rule allowed communication from any source to a specific label on any port. This rule was not only overly permissive, it also inadvertently overshadowed an existing block rule designed to prevent all internet access to that label.
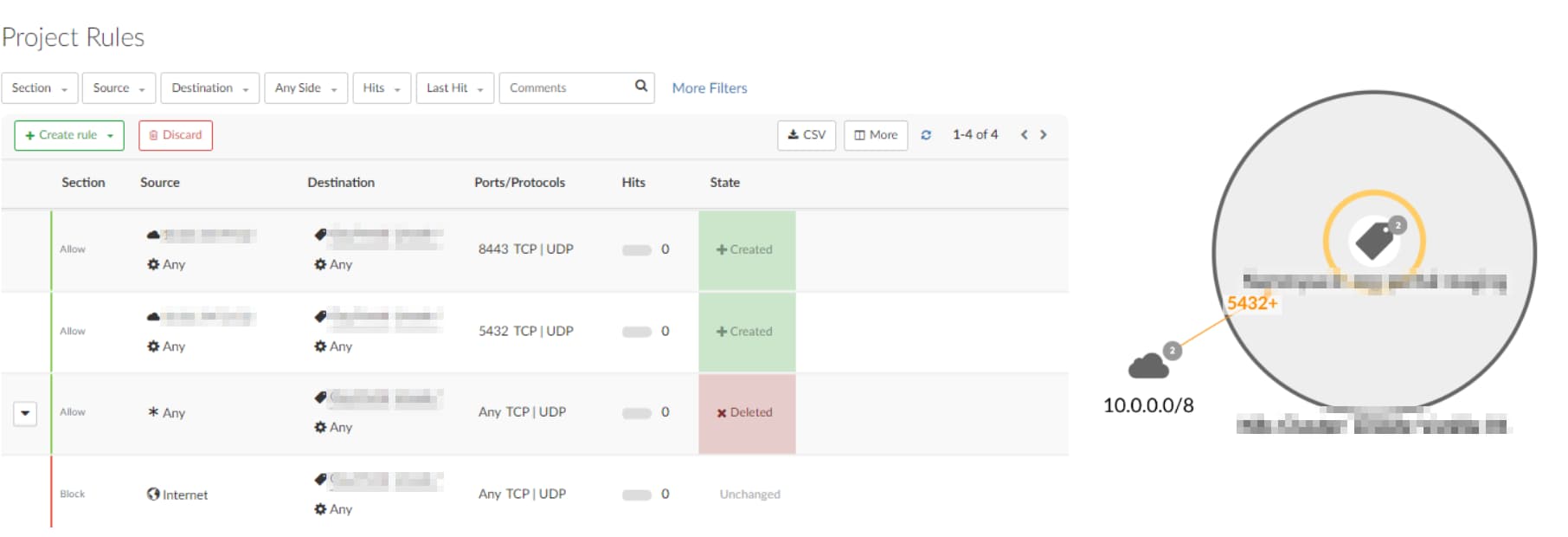
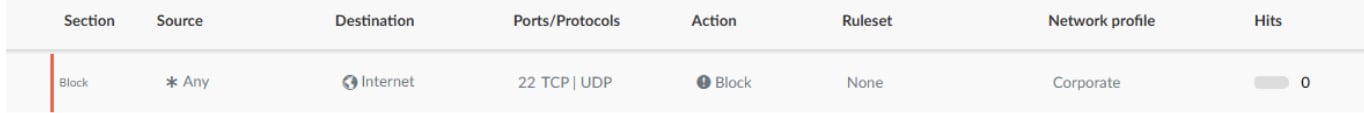
Every environment is different and requires custom handling, the direct opposite of the “allow any” mentality. After reviewing the situation, we suggested tailor-made allow rules instead of the overly permissive rule (Figure 2). This adjustment preserved essential internal communication while restoring the intended protection of the block rule.
Overshadowing rules
The first example also shows us another common misconfiguration — overshadowing rules. This problem occurs when a broader allow rule takes precedence over more specific ones, rendering the latter ineffective. To identify these overshadowing rules, analyze your rule hierarchy and traffic flow to spot cases where specific rules are never triggered due to a more general rule above them. Once identified, adjust the rule order or refine the broader rule to ensure the specific rules are effective. Properly addressing overshadowing rules improves policy precision and reduces unnecessary exposure.
This process can be quite taxing and time-consuming depending on the size of your environment and/or the level of granularity in which your rules are set. Finding places where you can automate detection of these overshadowing rules is key to continuous success with this one.
We tackled this issue with automation through our detection engine, which continuously identifies the top overshadowing rules and includes them as part of a comprehensive report (Figure 3). This allows you to quickly prioritize and address the most critical issues, ensuring that specific rules function as intended and your segmentation policy remains effective in reducing unnecessary exposure.
Zero-hit count rules
There is a pretty wide swath of potential reasons for zero-hit count rules: policies that receive no traffic, often because they are unnecessary, misconfigured, overshadowed by broader rules, or left over as legacy rules. Identifying the cause first is paramount to finding the proper solution.
Overshadowing: Adjust the rule order or refine broader rules to ensure the zero-hit rule can function as intended
Redundancy: Consider converting it to a block rule to better safeguard your network against unwanted communication (this is particularly relevant for alert rules, which are often implemented with the intention of being transitioned to block rules over time)
Misconfiguration: Ensure the rule is written properly as is and make edits as needed, all the while checking to ensure no other rules are negatively affected by your change
Legacy rules: Ensure the rule is not the building block of newer rules and is not required for legacy systems to run properly; if this is not the case, delete the rule to reduce the number of rules to make prioritization simpler
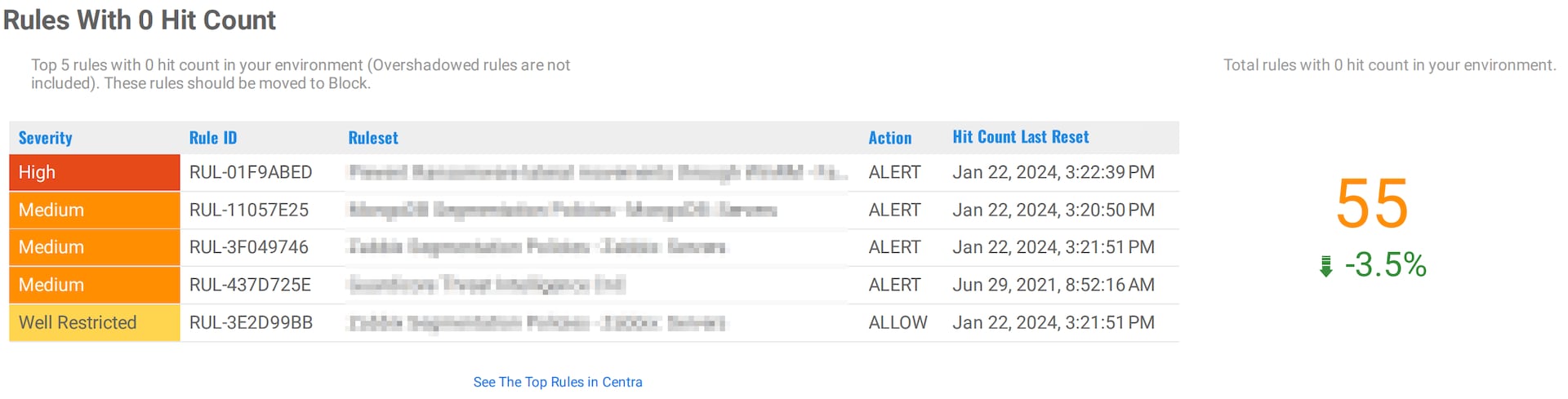
Effective policy management is key to a properly running segmentation environment. Akamai Hunt has successfully identified the top zero-hit count rules every month (Figure 4). These insights enable you to focus on refining, removing, and blocking these rules to optimize your network’s security posture.
Default administrative communication
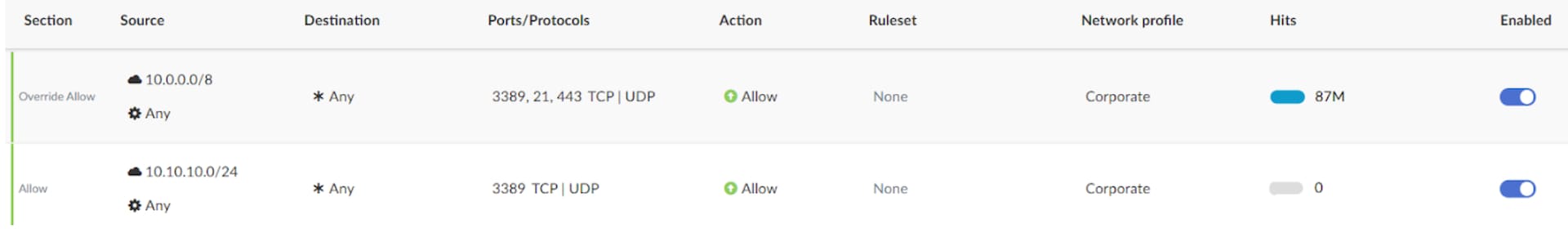
Administrative communication allowed by default can introduce unnecessary risks, as it often bypasses strict segmentation policies. To address this, identify all default administrative communication and analyze traffic patterns to determine whether the communication is truly required, and block unnecessary communication and add more specific rules that define only the necessary access.
Detection and analysis are key here, but that can be an incredibly time-consuming (and, therefore, costly) process, especially for a small team. Several of our customers rely on Akamai Hunt’s detection engine, which actively identifies instances of default administrative communication and generates tailored rule suggestions to effectively segment administrative traffic without disrupting the network’s functionality (Figure 5). Every suggested rule is carefully reviewed and validated to ensure alignment with the customer’s unique operational needs while reducing the attack surface.
Administrative traffic to the internet
Allowing administrative traffic to access the internet poses a significant security risk, as it can expose sensitive systems to external threats or enable data exfiltration. This type of traffic is often unnecessary and results from overly permissive rules or default configurations. To address this, identify all administrative systems with internet access and evaluate whether this access is truly required. Where possible, block internet access for administrative traffic or restrict it to specific, trusted sources and destinations.
If the ports show no legitimate communication activity, we recommend blocking them to eliminate unnecessary exposure and strengthen the security of administrative systems, as shown in Figure 6.
Remote access tool communication
Remote access tools (RATs) are commonly used for legitimate administrative purposes, but their mismanagement can introduce security risks. Unsegmented RAT communication can allow access to sensitive systems and make an attacker's options for lateral movement much easier.
To manage this, identify all instances of RAT use and monitor the communication patterns. Look for excessive privileges, open access to the internet, or connections to unapproved destinations. Restrict RAT communication to specific IPs, ports, protocols, and the specific RATs that are required for legitimate business operations, and implement strict authentication and monitoring.
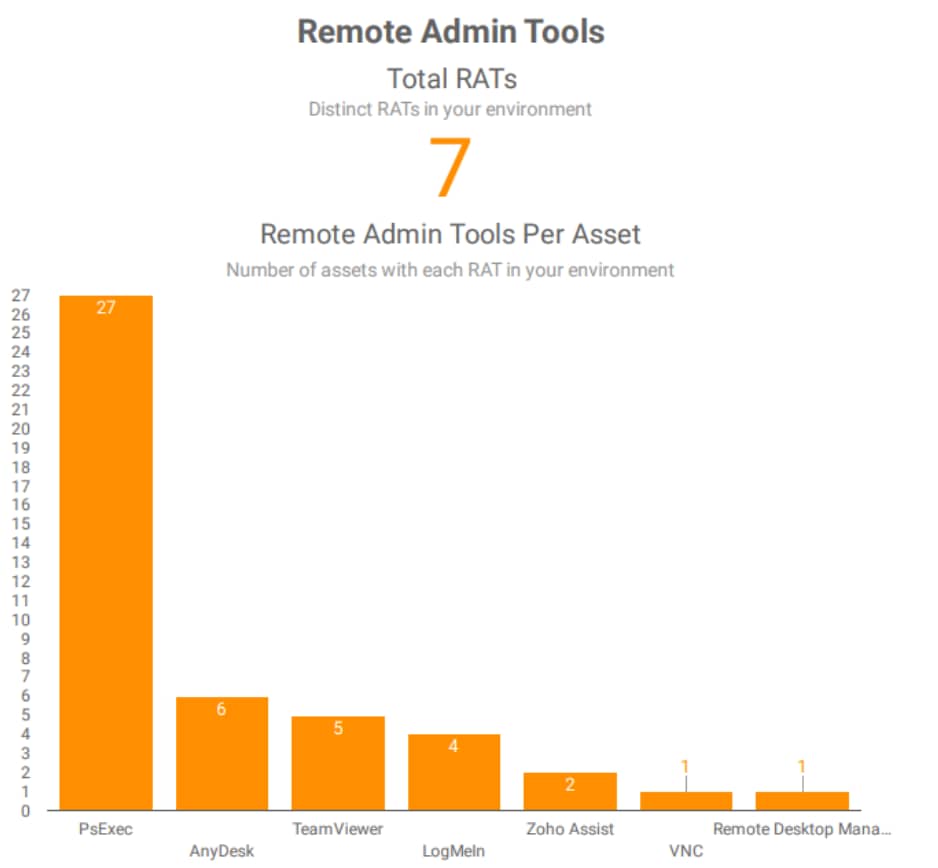
Networks evolve rapidly, and it only takes one entry point for an attacker to do serious damage. We suggest compiling a monthly comprehensive list of all RATs present in the network, including both newly detected and existing ones (Figure 7). We use this methodology with our customers. If necessary, the Akamai Hunt team will send a recommendation to create a dedicated segmentation project specifically for RAT communication, ensuring that access is tightly managed and aligned with business needs.
Unused open communication paths
Security is always more effective when we are blocking rather than allowing by default — this is the whole concept of Zero Trust. Just because your organization doesn’t use a particular path doesn’t mean an attacker won’t. Implementing broad blocking rules is a strong practice when your default segmentation rule is set to “allow” to mitigate propagation within your environment. Without sufficient block rules, gaps in the policy could leave the network vulnerable to misuse. To mitigate this, review your logs for traffic and apply restrictive block rules to eliminate these potential risks.
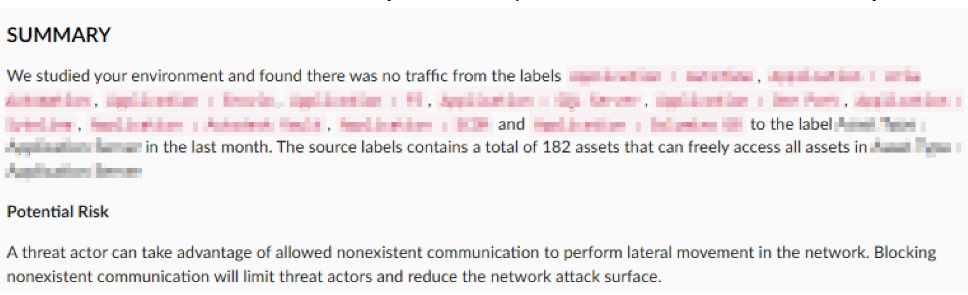
For example, Akamai Hunt identifies labels in customer environments that have no communication among them, even though the assets within these labels exist. The system then evaluates the criticality of the assets and the number of assets within each label to prioritize recommendations (Figure 8). Based on this analysis, Akamai Hunt suggests blocking these inactive communications to reduce unnecessary network exposure and enhance overall security.
Summary
You’ve probably noticed a pattern with these common use cases and mitigations: broad sweeping controls are more convenient than effective, so continuous analysis of these rules is required for proper security. It’s imperative that you have the proper tools and expertise to maintain effective segmentation, especially if you’re heading toward a Zero Trust model.
Whether you prefer to manage segmentation independently or to seek expert guidance, Akamai Hunt empowers you to maintain your network policy. If you are handling these challenges manually, begin by thoroughly reviewing the use cases detailed in this post, focusing on areas where your segmentation policy may be overly permissive, redundant, or misaligned with your network’s needs. Pay attention to communication patterns and ensure unnecessary or potentially risky traffic is identified and blocked.
The Akamai Hunt team specializes in the art of finding precise policy adjustments to address identified gaps and enhance network security. As a managed service, we continuously monitor your environment for threats and risks, delivering customized, actionable recommendations without false positives. Our approach blends automation with expert analysis to help you refine your network policies and stay ahead of evolving threats.