Revealing Guardicore Reveal™

For the last year or so, we’ve been hard at work building Guardicore Reveal™, our Data Center Visibility platform. As we’ve officially released it earlier this week, I’m finally allowed to tell you all about it (and, yes, show off a bit!).
Do you really know what’s going on in your Data Center?
When we started having conversations with Data Center administrators, DevOps and security teams, we realized that while security was in everyone’s mind, a far more basic need wasn’t being fulfilled. Teams whose daily job is maintaining data centers didn’t have the tool to answer two simple questions:
- Which applications are running in my Data Center?
- How are these apps talking to each other, and with the Internet?
These questions weren’t asked out of pure curiosity; answering them is crucial to better maintain and secure data centers.
So we’ve built the perfect tool to answer them, and act upon these answers.
Guardicore to the rescue
We’ve developed a beautiful, robust platform which collects, stores and displays a comprehensive visual map of applications running in your data center:
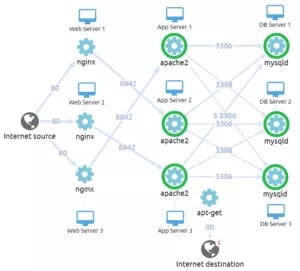 A 3 tiered Data Center in AWS VPC — as visualized by Guardicore Reveal
A 3 tiered Data Center in AWS VPC — as visualized by Guardicore Reveal
Data Center teams are now able to fully reveal the application flows in their infrastructure. With this information, teams are better equipped to segment data centers, identify bad configurations which weaken security postures, and get a better understanding of suspicious and malicious activity.
And unlike other “application aware” solutions, we actually identify the exact process running the application — including its entire context, such as username, full path, command line arguments and checksum.
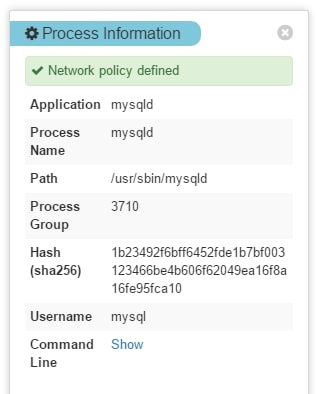 Full process data on every application
Full process data on every application
Application level segmentation

Once we’ve revealed how applications talk to each other in the data center, the next step was to build some tight security policies around these flows. Deviations from the expected app flows should be detected and acted upon in real time.
See those green circles around applications in our map above? That’s a process-level policy, protecting these apps from being accessed by unauthorized processes.
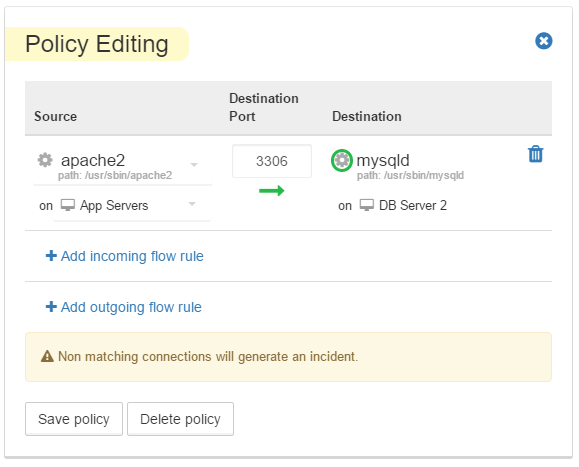 Our DB servers should only be accessed by apache2 servers, running on App Server VMs
Our DB servers should only be accessed by apache2 servers, running on App Server VMs
You can build these policies around your specific use case; here are some ideas:
- Sensitive database servers? Make sure that only specific client applications can access them.
- Automatically deploying new apps or micro-services? Make sure that they’re being used as you’ve wanted, without any (malicious) surprises
- Compliance requirements? Validate that your applications are meeting them, by ensuring their expected traffic sources and destinations
Policies can be set by using our beautiful UI, or by utilizing REST APIs to define your own rules. And policy violations are detected in real time.
As simple as it gets
Want to give it try? It’s as simple as running a single command on servers you want to visualize and protect. It works on Windows and Linux machines, running on all private or public data center infrastructures.
Just drop me an email at lior@guardicore.com, and we’ll get you up and running in no time.
I’m really excited about Guardicore Reveal — and this is just the beginning. We’re already developing more Reveal features, which will make it even easier to explore and secure data centers.
What do you think? I’d be glad to answer any questions, and to hear your thoughts and comments about Reveal.




