Record 0-Second SLA PPS Mitigation

Record-high 312 mpps attack mitigated in 0 seconds
On May 2, 2020, Akamai blocked a large PPS-focused attack against one of our financial services customers in 0 seconds, utilizing a proactive mitigation posture. This was one of the largest PPS levels we have on record, and the biggest mitigated to date in 0 seconds. The attacker launched a bevy of minimally sized UDP packets in an attempt to overwhelm network gear in the customer's data center.
There are two ways to quantify the impact of a DDoS attack -- by overall bits per second (BPS) and by packets per second (PPS). Some in the industry erroneously tout PPS as the one true measure of a DDoS attack's veracity, while in reality both BPS and PPS are important:
- BPS-focused attacks are largely designed to saturate internet links
- PPS-focused attacks are largely designed to overwhelm gear and/or applications
While we've shared examples of Akamai's 0-second SLA on BPS-focused link saturation attacks, our analysis below will show our proactive mitigation controls are equally at home thwarting PPS-focused network infrastructure and application attacks.
Attack graphs for the incident in question show large peaks on entry into Akamai's scrubbing network (left) and no attack traffic exiting through to the customer (right) for both.
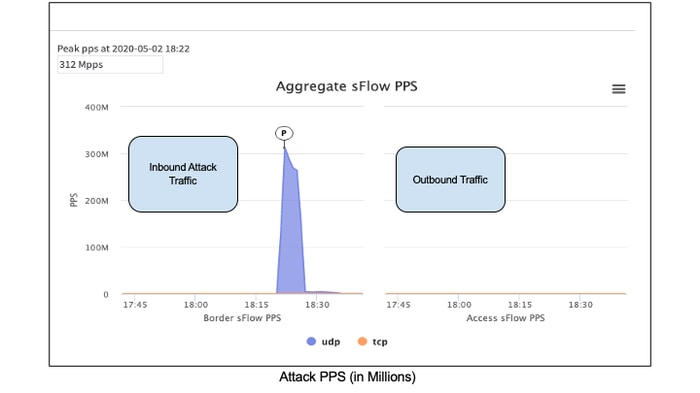
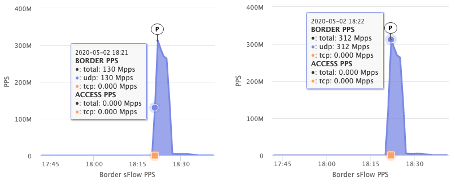
The attack ramped up very quickly, hitting 130 Mpps in 1 minute and 312 Mpps in 2 minutes. It continued on for 6 minutes before leveling off at low levels and simmering for another 10 minutes at pre-attack traffic levels before completely going away.
It took less than 2 minutes for this attack to hit a peak force.
Examining the attack through our behavioral mitigation recommendation engine shows swings in protocol, destination port, packet length, and geolocation (listed in order of baseline deviation).
In fact, there were a number of valid targeted methods to block this attack:
- Any of the highlighted methods could have effectively blocked the attack with no collateral damage
- Our featured 0-second SLA controls include frequently seen attack vectors (bold)
- As when Akamai mitigated the 1.3 Tbps UDP reflection attack in 2019 (an example of a BPS attack), packet level and more complex mitigations were unnecessary
Large baseline deviations of unexpected traffic make good block candidates:
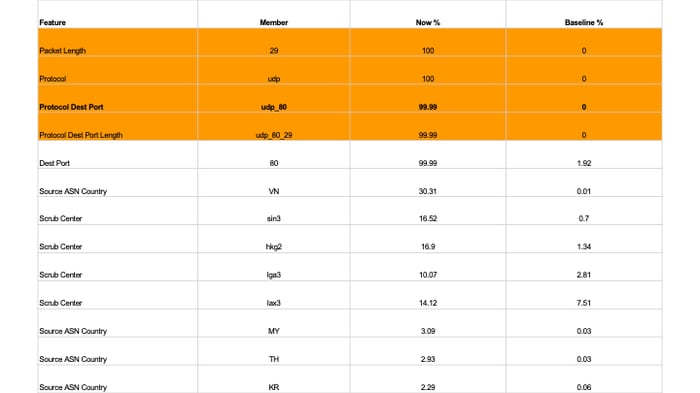
It is important to note that proactive mitigation does not impede threat analysis or reporting. We lose no visibility into telemetry or packet captures.
Our approach is to mitigate the majority of attacks with proactive mitigation postures. This holds across attacks of all shapes, sizes, vectors, customer industries, and geolocations. You are either ahead of or behind attacks, and we greatly prefer to partner with our customers to build a proactive defensive posture that places them ahead of potential attacks.
The following chart shows mitigations by Gbps (Y) and Mpps (Z) over time (X).
Attacks skew heavily towards proactive mitigation:
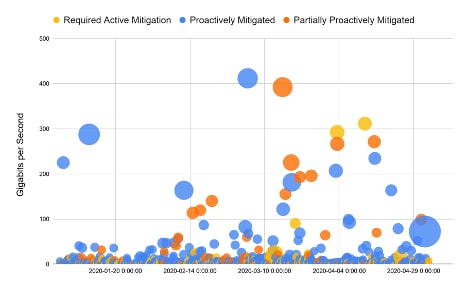
As you can see, our proactive approach to DDoS mitigation has paid dividends to our customers that face fast-ramping attacks that consume network bandwidth and capacity.
You can't get faster than a 0-second mitigation time!



