Ransomware on the Move: Evolving Exploitation Techniques and the Active Pursuit of Zero-Days

Executive summary
The ransomware threat landscape is seeing a concerning shift in attack techniques with the rampant abuse of zero-day and one-day vulnerabilities in the past six months, which led to a 143% increase in victims from Q1 2022 to Q1 2023.
Ransomware groups now increasingly target the exfiltration of files, which has become the primary source of extortion, as seen with the recent exploitation of GoAnywhere and MOVEit.
Akamai research finds victims of multiple ransomware groups are almost 6x more likely to experience a subsequent attack within the first three months of the initial attack.
Ransomware groups, such as CL0P, are aggressively pursuing the attainment and development of in-house zero-day vulnerabilities. This has proven to be a successful strategy, with CL0P growing its number of victims by 9x from Q1 2022 to Q1 2023.
- LockBit dominates the ransomware scene with 39% of total victims (1,091 victims), more than triple the number of the second-highest ranked ransomware group. It has risen significantly in the absence of the previous front-runner, Conti, with its victim count increasing by 92% from Q4 2022 to Q1 2023.
According to our latest State of the Internet (SOTI) report, in an evolving ransomware landscape in which adversaries seek to evolve past the ability of their victims to defend, ransomware groups are shifting their attack techniques from phishing to put a greater emphasis on zero-day vulnerability abuse. Vulnerability abuse has grown considerably, both in scope and sophistication, as we extensively examined in our 2022 reports, such as Slipping Through the Security Gaps.
In addition, ransomware groups have become more aggressive in their methods of both extortion and vulnerability exploitation, such as through in-house development of zero-day attacks and bug bounty programs. Ransomware groups are willing to pay for the opportunity for financial gain, whether it’s to pay other hackers to find vulnerabilities in their software, or to acquire access to their intended targets via initial access brokers (IABs).
Attackers are shifting gears to gain an advantage
Attackers are also shifting gears regarding tactics that can generate a more profitable pathway of value. They are finding more success as they move away from their initial extortion tactic — encryption — and focus their efforts more on data theft to gain an advantage over organizations that rely on their backups.
This also allows attackers to resort to additional extortion tactics like harassing the victim’s customers or partners, through emails or phone calls, to get them to encourage the victim to pay (Figure 1). Some of the emerging attack techniques also include phishing emails with new types of payload with attackers ditching the use of macros, the use of stolen credentials, and drive-by compromises.
 Fig. 1: Overview of the ransomware kill chain, including some of the updates in extortion tactics
Fig. 1: Overview of the ransomware kill chain, including some of the updates in extortion tactics
A snapshot of activity by top ransomware groups
Our quarterly analysis shows significant shifts in top ransomware (Figure 2). Although LockBit still dominates the ransomware landscape, CL0P ascended to second spot in Q1 2023. This marks a significant jump from number 10 in Q4 2022, which can be attributed to CL0P’s leveraging a variety of zero-day vulnerabilities as points of entry.
Additionally, we observe that most ransomware threats ramped up their activities at the beginning of the year, resulting in a notable growth in the number of victims; others sustained their ranking in the top 4, as is the case of ALPHV and Royal.
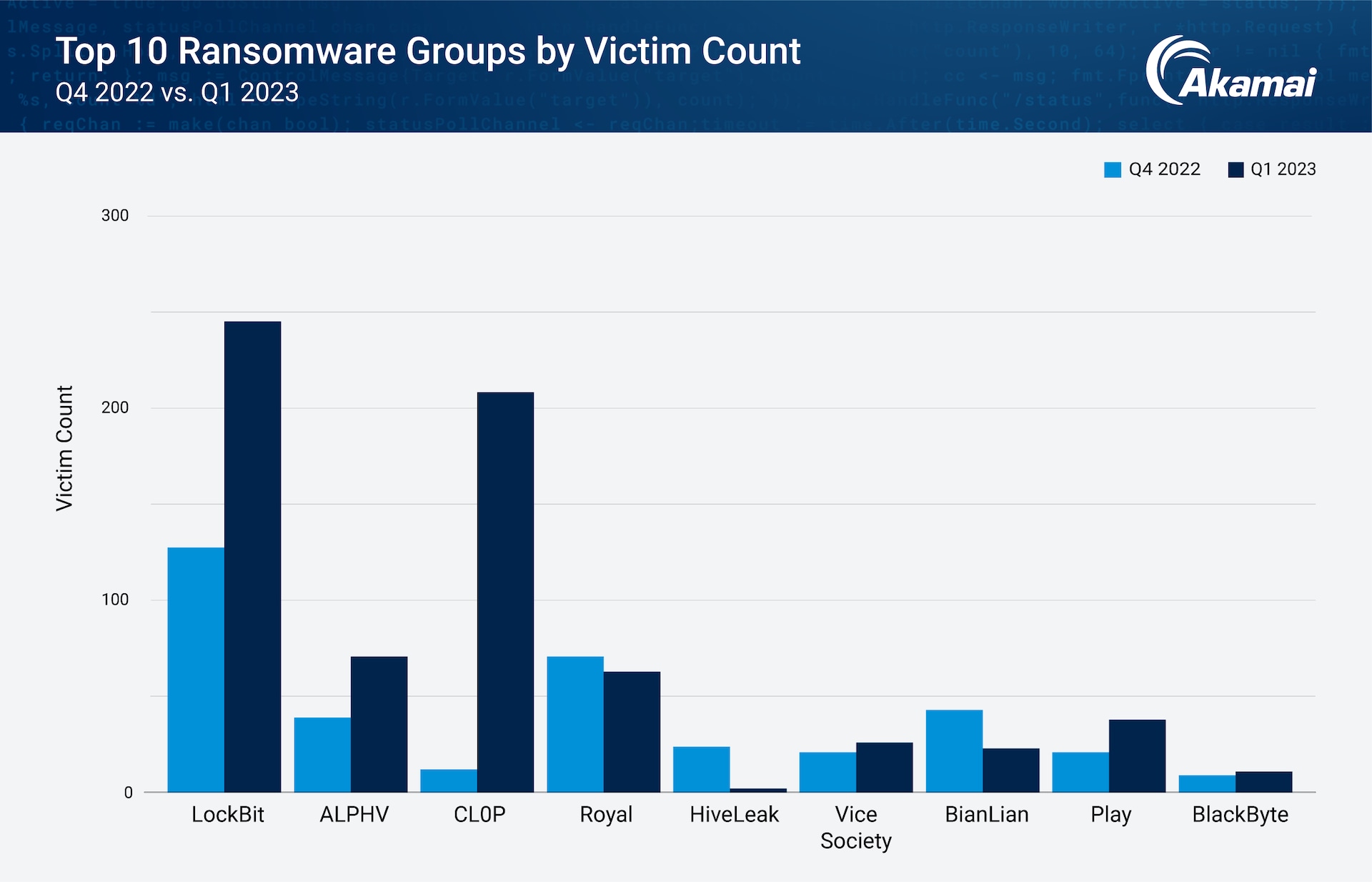 Fig. 2: CL0P’s giant leap can be attributed to its perusal of a variety of zero-day vulnerabilities as points of entry
Fig. 2: CL0P’s giant leap can be attributed to its perusal of a variety of zero-day vulnerabilities as points of entry
How do initial access brokers figure into RaaS business models?
It is also worth noting that we continue to see specialization, with some criminal groups focusing on acting as IABs. These cybercriminal groups are responsible for selling corporate network access to ransomware attackers, as well as to other groups.
As such, it lowers the bar of expertise and reduces the time needed to launch attacks to intended targets. This ransomware as a service (RaaS) combined with expansion of extortion models has resulted in more successful campaigns.
Holding stolen data hostage
In fact, we have seen a shift from traditional encryption to holding the stolen data hostage. The criminals even tell customers of the victims that they have stolen their data and encourage them to ask the victim company to pay the ransom. This is done to further exert pressure on the victimized organization to pay the demands.
Additionally, we have seen some attackers also incorporate a distributed denial-of-service (DDoS) attack to overwhelm defensives during the attack.
No target is too small
When we looked at victims based on revenue size, we saw smaller organizations at high risk of ransomware, with more than 60% of analyzed victims being in the smaller revenue bracket (up to US$50 million), which demonstrates that attackers are also successful in launching attacks against smaller organizations.
However, let’s not discount the fact that a significant number (12%) of victim organizations are in the higher revenue category (US$501 million and beyond).
Critical industries are at elevated risk
In terms of industry breakdown, critical industries, particularly manufacturing, show an elevated risk of ransomware (Figure 3). This increased risk comes from the plethora of legacy or old commercial software deployed across diverse manufacturing and supply chain sites, including on operational equipment, sensors, and other connected endpoints, from connected cars to chemical plants.
This elevated risk is also observed in our data findings in which the number of affected manufacturing companies spiked by 42% between Q4 2021 and Q4 2022.
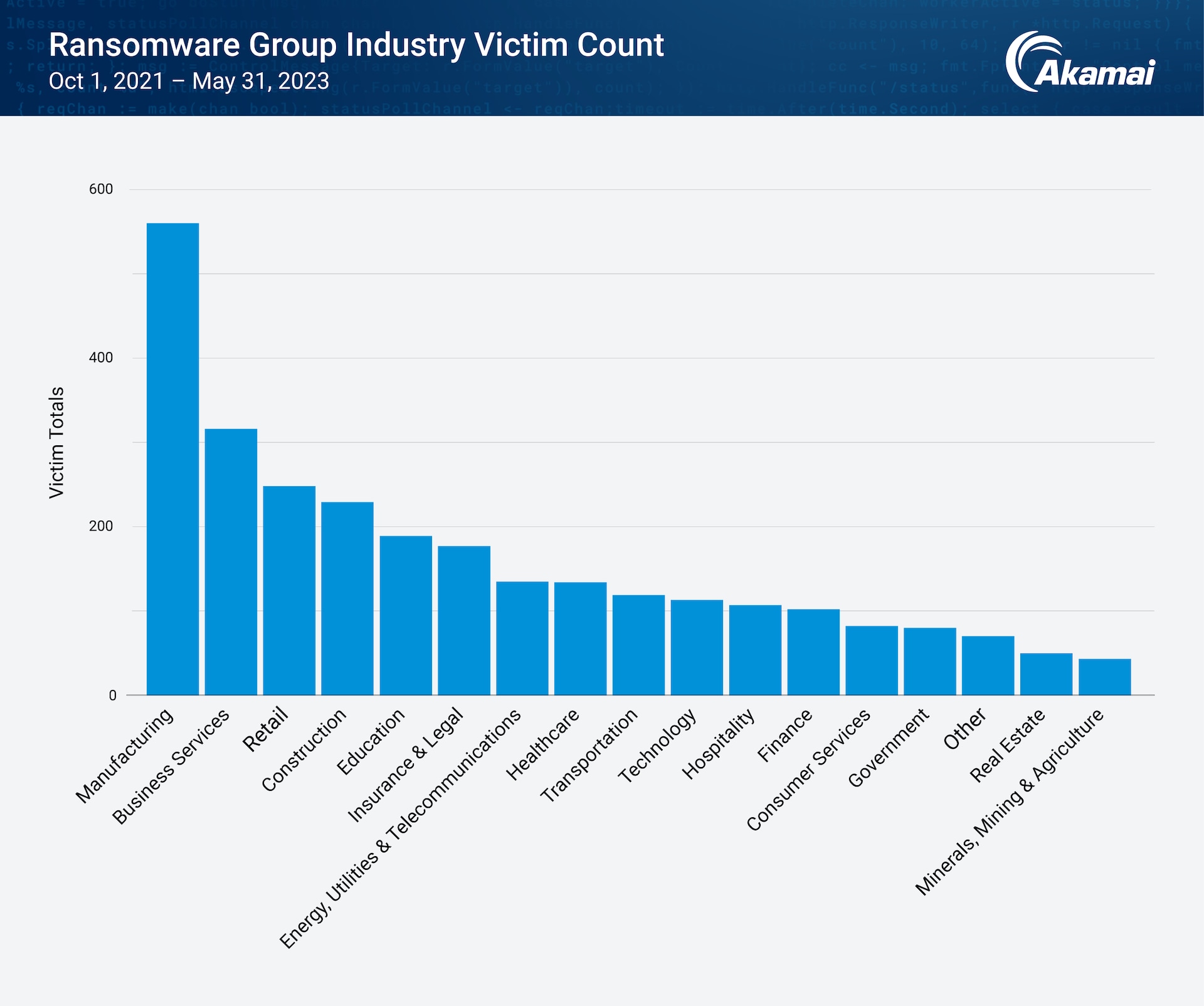 Fig. 3: Manufacturing remains the top vertical with the highest number of victims of ransomware attacks
Fig. 3: Manufacturing remains the top vertical with the highest number of victims of ransomware attacks
Noteworthy OFAC regulations
One area of note was that regulations enforced by the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) may make it illegal to pay ransom to certain parties or individuals. Organizations that ignore the many potential impacts of ransomware attacks and data theft may face the difficult decision of violating OFAC regulations when giving in to ransom demands.
Recommendations
Our SOTI report provides recommendations broken out by different stages of the attack, but here are some of the overall recommendations:
Have a strong understanding of your attack surface
Have strong processes/playbooks
Monitor your outbound traffic for indicators of compromise (IOCs)
Ensure that your legal team is tracking legislation
Patch, train, and protect
First, have a strong understanding of your attack surface (and minimize it where you can). Rogue APIs, legacy systems, and internal systems that are not monitored or segmented are all at high risk.
Second, have strong processes/playbooks that have been validated with exercises like red teaming. If you want to use groups like CL0P to guide red team mythology you can leverage MITRE — don’t forget to check out the Navigator tool for great graphics.
Next, ensure that you are monitoring outbound traffic for IoCs. You want to detect both the data being exfiltrated and command and control communications.
Then, make sure that your legal team is tracking legislation on paying ransomware to make sure your plan is complete and compliant.
And, finally, the basics are always key: patching, employee training, and protected backups are still important. You can leverage the Cybersecurity & Infrastructure Security Agency and your Information Sharing and Analysis Center for best practices as well.
Don’t stop defending
For me, the most troubling insight was the fact you cannot stop defending to deal with an intrusion. A DDoS attack can mask a different attack, and you can be hit by a second ransomware attack while dealing with or recovering from an attack.
Learn more
In addition to the global findings, the full SOTI report includes ransomware trends by region: Asia-Pacific and Japan (APJ), and Europe, the Middle East, and Africa (EMEA). And, for even more insights, stay plugged into our latest research by checking out our Security Research Hub.





