Protecting Unmanaged Devices with Armis and Akamai
Every year, more types of devices connect to one another and to the internet. We usually think of connected devices being things like smart TVs, refrigerators, and watches, but they also include medical devices, operational technology (OT), building systems (such as heating, ventilation, and air conditioning), cameras, and more.
As these devices become connected to the network, they need to be secured. Ideally, they should also be monitored and controlled as a dynamic part of an organization’s entire network, and not left within a silo.
But this isn’t always easy to accomplish.
The challenges of unmanaged devices
Many of these devices are known as unmanaged, meaning they can’t have a software agent deployed on them. Because of this, many agent-based security solutions are not able to provide the necessary visibility and control over network connections to and from these devices.
Traditional methods for controlling access are usually ineffective for unmanaged devices, as some compromised devices might still be able to authenticate with the network.
And in the event of a known vulnerability, many of these devices cannot be patched. If exploited, these vulnerable devices (which have become a prime target for cybercriminals) can become an entry point for attackers to move laterally inside the network by providing an open door to a growing amount of sensitive data.
Unmanaged does not equal uncontrollable
To better help our customers see, protect, and manage their connected devices — IoT, OT, IoMT, and more –- Akamai and Armis are teaming up to provide an integration that enables you to create better security policies for your connected devices with Akamai Guardicore Segmentation.
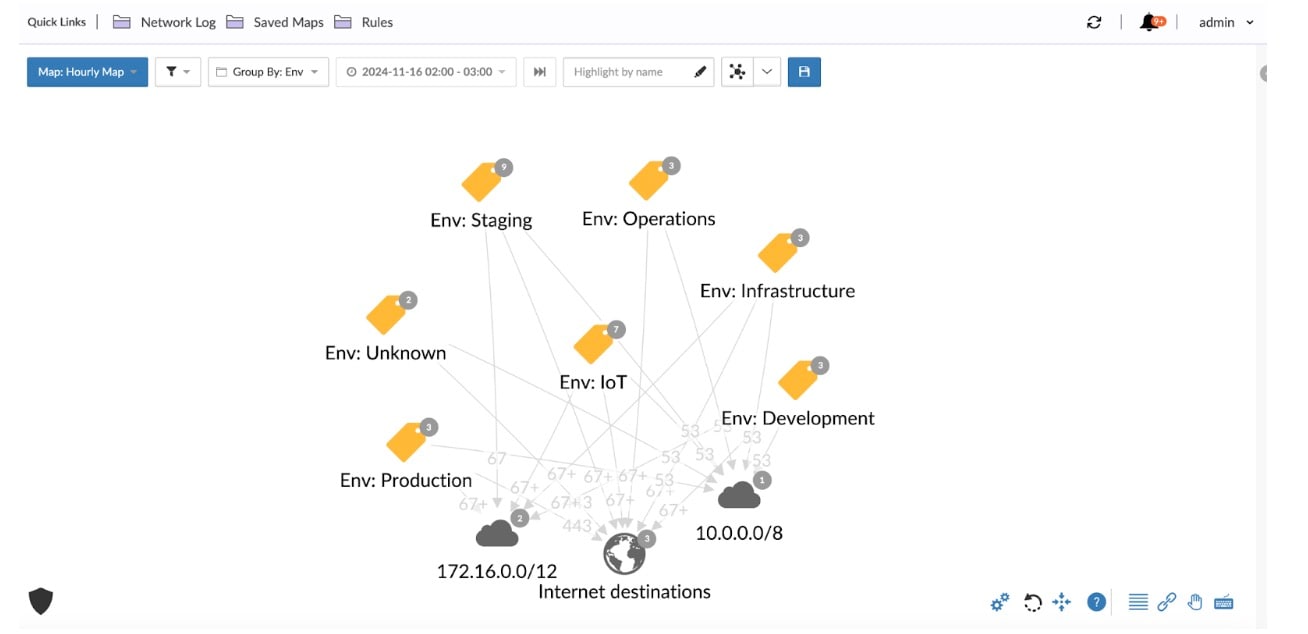
Akamai Guardicore Segmentation customers get better visibility into their connected, unmanaged devices by integrating with Armis. From one detailed map, you can now see what these devices are and where they meet the data center, including traffic origins and any application dependencies.
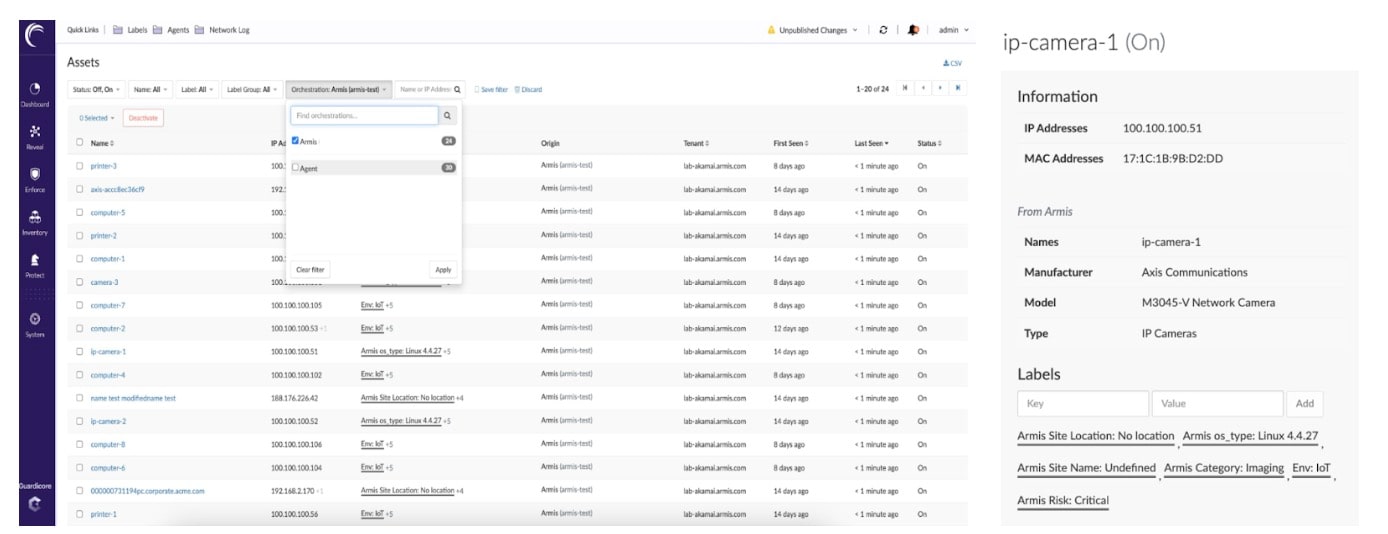
You can import specific device attributes and metadata to create labels based on contextual information, such as device location and risk scores from Armis. In turn, you can create targeted security policies to control what these devices are allowed to talk to within your data center, restricting unnecessary communications and preventing lateral movement in the event of an exploited vulnerability. All of a sudden, your unmanaged devices are much more manageable.
Armis and Akamai Guardicore Segmentation: Key integration capabilities
Armis and Akamai Guardicore Segmentation offer essential integration capabilities, including the ability to
- Import asset types and rich metadata
- Create targeted segmentation policies
- Apply the risk scores assigned by Armis
Import asset types and rich metadata
Import asset types and rich metadata from Armis into Guardicore to enable administrators to label their devices and visualize their communications using a near–real time interactive map of true network flows. Understand the application dependencies and gain a more complete picture of what is communicating within your environment.
Create targeted segmentation policy
Create targeted segmentation policy using metadata from Armis, including OS, manufacturer, model, geographical location, and more, as attributes. Create one-rule policies that can control communications to your data center from all machines of a certain type, make, or specific location.
Apply risk scores assigned by Armis
Apply the risk scores assigned by Armis as a way to create and enforce policy for vulnerability management. Akamai Guardicore Segmentation supports the creation of labels based on these risk scores, which can be assigned to high-risk devices and used to build rules that control access from known vulnerable devices and support a comprehensive vulnerability management strategy — especially for devices that cannot be patched (Figures 1 and 2).
With Armis and Akamai Guardicore Segmentation, you can quickly uncover and eliminate gaps in network visibility, optimize your IT network security, define policies to enforce security controls for your devices, and ensure compliance with regulations and industry standards.
Find out more
For more information on protecting your devices with Armis and Akamai, speak with one of our technical experts.