Now Available on GitHub: Akamai CLI Utility v1.0 for Akamai Terraform

DevOps has made an undeniable impact in the technology space, paving the path for shorter development cycles, rapid deployment, and robust automation. It’s now considered a vital way to create a multifaceted defense — before cyberattacks occur.
By seamlessly integrating DevOps practices into agile development, companies can weave security into each stage of the final product rather than applying it after development ends. Although traditional development cycles have security classified as a separate process, DevOps makes security an active component from the beginning of a development cycle all the way to the time of application delivery.
Embrace a DevOps approach to security
Throughout the entire cycle, security teams can assess, audit, and test code for potential security flaws, taking a more proactive approach to securing an application. By embracing a DevOps approach to security, companies benefit from the following:
A cost-efficient way to accelerate software delivery
Improved security performance through a DevOps workflow
Faster recovery speed after a security breach
Automated security checks at every stage of software development through the integration of security tools and processes
Strengthened infrastructure with security coverage and automation
A reliable, iterative process that continues to adapt to rapid change
Increased visibility of an application and its level of security
Compatibility with modern software development
Introducing DevOps to security also improves collaboration between development, cybersecurity, and operations teams, allowing them to better target incidents and address vulnerabilities as they occur. To ensure that all teams are familiar with the integration of DevOps into security, it’s essential to align their understanding of an organization’s security procedures.
Helping security teams stay ahead
Simply put, DevOps has revolutionized application development, enabling teams to set up new application infrastructure and deploy apps and application programming interfaces (APIs) in the cloud faster than they could with on-premises data centers. This speed has security teams struggling (and sometimes failing) to keep up with rapidly changing apps and APIs and to protect their organization from new vulnerabilities or threats.
To keep pace with modern application development teams, security teams now use some of the same DevOps patterns and tools that allow AppDev teams to move so quickly. An example of this is the use ofTerraform and infrastructure as code (IaC) practices to manage web application and API protection (WAAP) configurations.
With an IaC approach to configuring and managing WAAP, security teams can distribute ownership of WAAP configuration to the AppDev teams themselves, removing a bottleneck when it comes to securing newly deployed apps and APIs. This allows development teams to continue to ship new products and features quickly and securely.
Transitioning to IaC with Akamai CLI for Akamai Terraform
Taking an existing WAAP configuration that was previously managed solely via a UI and converting it to Terraform can be a daunting task that requires not just knowledge of Terraform and HashiCorp Configuration Language (HCL), but also specifics of the WAAP configuration itself.
To make this transition easier, we are excited to announce v1.0 of our command-line interface (CLI) utility for Akamai Terraform, with a new WAAP configuration export ability.
Using Akamai CLI for Akamai Terraform to export WAAP configurations
The new version of the CLI introduces the command export-appsec, which when directed at an existing Akamai Kona Site Defender, Web Application Protector, or App & API Protector security configuration, will automatically export the WAAP configuration as HCL, along with a script that executes all the terraform import commands required to import existing WAAP configuration into the Terraform state.
Before we dive into its process, we recommend reading the following material as a prerequisite:
Here’s an example of how it works:
1. Go to https://github.com/akamai/cli and install the Akamai CLI, which will make it easier to install the CLI for Akamai Terraform.
2. Once the Akamai CLI is installed, run this command to install the CLI for the Akamai Terraform module:
$ akamai install terraform
The public repo for the CLI for Akamai Terraform is available at https://github.com/akamai/cli-terraform, where you can view instructions on the available commands as well as the release notes.
3. Once the Akamai CLI Terraform module is installed, run the following command to start generating the HCL for an existing security configuration:
$ akamai terraform export-appsec [name of security configuration]
The name of the security configuration can be found by going into the Akamai Control Center, clicking the hamburger menu in the top left, and selecting Security Configurations (under Web and Data Center Security).
4. Once the utility completes running, you will now have a number of files created:
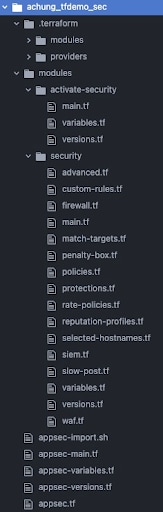
Directory/File |
Description |
./modules/activate-security |
Contains HCL for activating the security configuration |
./modules/activate-security/main.tf |
Defines the Terraform datasource and resource required for activation; uses the variables.tf file to populate values |
./modules/activate-security/variables.tf |
Defines variables used by main.tf; by default, set by the appsec-variables.tf file in the root folder |
./modules/activate-security/versions.tf |
Defines the version of the Akamai Terraform provider being used |
./modules/security |
Contains the HCL for the security configuration settings |
./modules/security/advanced.tf |
Defines the Terraform resources for advanced settings in the security configuration, such as pragma headers |
./modules/security/custom-rules.tf |
Defines the Terraform resources for custom rules |
./modules/security/firewall.tf |
Defines the Terraform resources for IP and GEO firewall settings |
./modules/security/main.tf |
Defines the Terraform resources for the security configuration and group |
./modules/security/match-targets.tf |
Defines the Terraform resources for the security policy/policies match targets |
./modules/security/penalty-box |
Defines the Terraform resources for the penalty box settings |
./modules/security/policies.tf |
Defines the Terraform resources for the security configuration’s security policy/policies |
./modules/security/protections.tf |
Defines the Terraform resources for the security configuration’s protections and their enabled status |
./modules/security/rate-policies.tf |
Defines the Terraform resources for the rate policies in the security configuration |
./modules/security/reputation-profiles.tf |
Defines the Terraform resources for the client reputation profiles in the security configuration |
./modules/security/selected-hostnames.tf |
Defines the Terraform resources for the selected hostnames in the security configuration |
./modules/security/siem.tf |
Defines the Terraform resources for the SIEM integration settings in the security configuration |
./modules/security/slow-post.tf |
Defines the Terraform resources the slow POST protection settings in the security configuration |
./modules/security/variables.tf |
Defines variables used by main.tf; by default, set by the appsec-variables.tf file in the root folder |
./modules/security/versions.tf |
Defines the version of the Akamai Terraform provider being used |
./modules/security/waf.tf |
Defines the Terraform resources that manage the WAF rules or attack groups in the security configuration |
./appsec-import.sh |
A script that executes the terraform import commands to import an existing configuration into the Terraform state |
./appsec-main.tf |
Defines the location for credentials for authenticating with Akamai EdgeGrid, to allow communication with Akamai’s open APIs |
./appsec-variables.tf |
Variables that should be configured by the user prior to running terraform plan or terraform apply |
./appsec-versions.tf |
Defines the version of the Akamai Terraform provider being used |
./appsec.tf |
Defines the “security” and “activate-security” modules that are stored in their own subdirectories |
5. Once the Terraform configuration files have been generated, edit ./appsec-variables.tf, entering the correct values for your security configuration. “group_name” and “contract_id” must be manually provided and can be found by expanding the security configuration in the Akamai Control Center on the Security Configurations screen mentioned in step 3.
6. Run sh ./appsec-import.sh to start importing the configuration into the local Terraform state.
Manage WAAP configuration as code
At this point, you should now have your Akamai WAAP Security Configuration represented in Terraform HCL, as well as your local state in sync with the configuration on the Akamai platform. From here, you can start to manage your WAAP configuration completely as code.
With v1.0 of the Akamai CLI for Akamai Terraform, it’s easier than ever to start using Terraform to manage your Akamai Kona Site Defender, Web Application Protector, or App & API Protector WAAP configurations. Also, v1.0 of the Akamai CLI for Terraform supports:
export-domain (alias: create-domain)
export-zone (alias: create-zone)
export-appsec (alias: create-appsec)
export-property (alias: create-property)
export-cloudlets-policy (alias: create-cloudlets-policy)
export-edgekv (alias: create-edgekv)
export-edgeworker (alias: create-edgeworker)
export-iam (alias: create-iam)
export-imaging (alias: create-imaging)
What’s more, application development teams can build on the generated code to configure Akamai WAAP themselves in their own automated deployment pipelines, removing the security team bottleneck for enabling WAAP protection and ensuring that the rapid pace of application development doesn’t require compromising on security.
Additional resources
If you’re new to Terraform, here are some resources to help you get started:
Learn more
If you’d like to learn more, reach out to devrel@akamai.com.


