Noname Security Platform Updates: 3.29 Release
Akamai acquired Noname Security in June 2024. The Noname Security product is now Akamai API Security, but this archived blog post reflects the product and feature names on the original date of publication.
The Noname Security 3.29 release supports seamless integration with Amazon EKS, shareable links for incidents, API environment identification, application grouping in Active Testing, and more.
Core Platform
Seamless integration with Amazon EKS
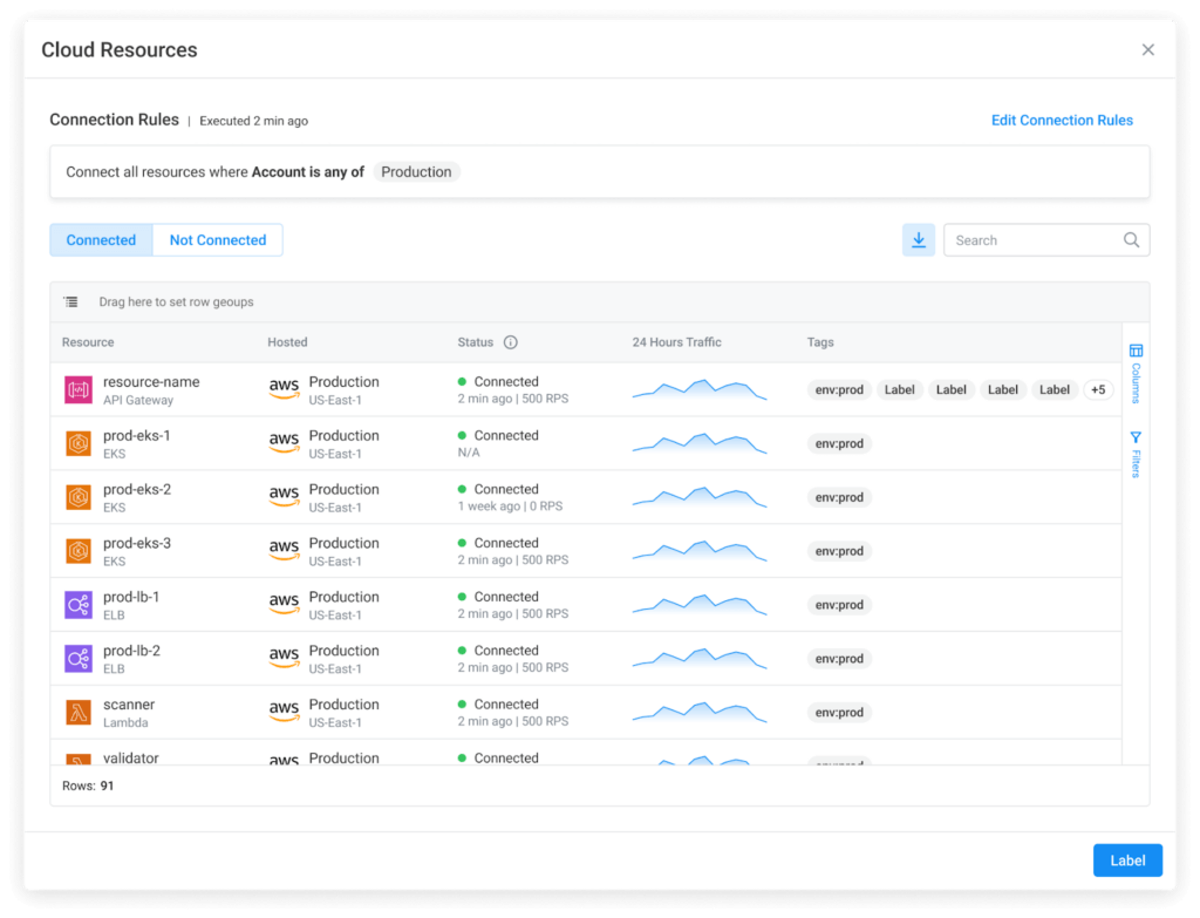
Noname Security platform now seamlessly integrates with Amazon Elastic Kubernetes Service (AWS EKS). With this integration, you can analyze traffic directly from your AWS EKS clusters, in addition to previously supported AWS API Gateways, AWS Elastic Load Balancers, and AWS Lambda, to enhance your security insights.
Getting started with our AWS EKS integration is easy — simply navigate to the Traffic Sources page and follow the prompts to deploy the AWS connector. Under resource types, you’ll be able to select AWS Elastic K8s Service and set up appropriate connection rules to specify applicable AWS accounts. Once configured, your Kubernetes clusters will automatically be connected to Noname, sending traffic for inspection.
For more information on configuring our Amazon EKS integration, please visit our AWS connector documentation or contact our Customer Success Team.
Shareable links for incidents and findings
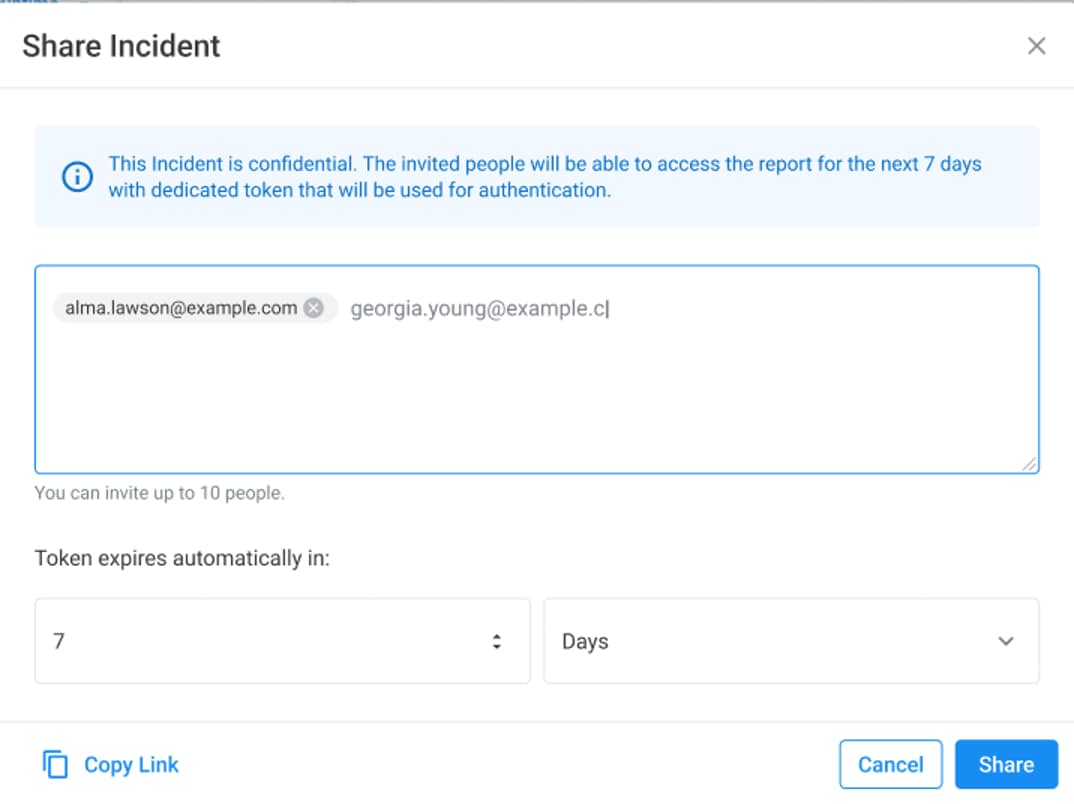
Shareable links enable you to quickly copy and share hyperlinks to Noname incidents and findings with your coworkers. Sending someone a shared link to an incident allows you to work with that person without the need to provision access to the entire Noname Security platform. Each link provides time-restricted view-only access to a specific incident or finding and can be revoked at any time.
Noname Security administrators can also granularly control access to shareable link creation on a per-role basis, configure default link expiration behavior, and audit all created links — both active and expired. This allows you to safely collaborate with relevant stakeholders and coworkers without managing access or permissions within the Noname Security platform.
To learn more about creating and managing shareable links, please see documentation.
API environment awareness
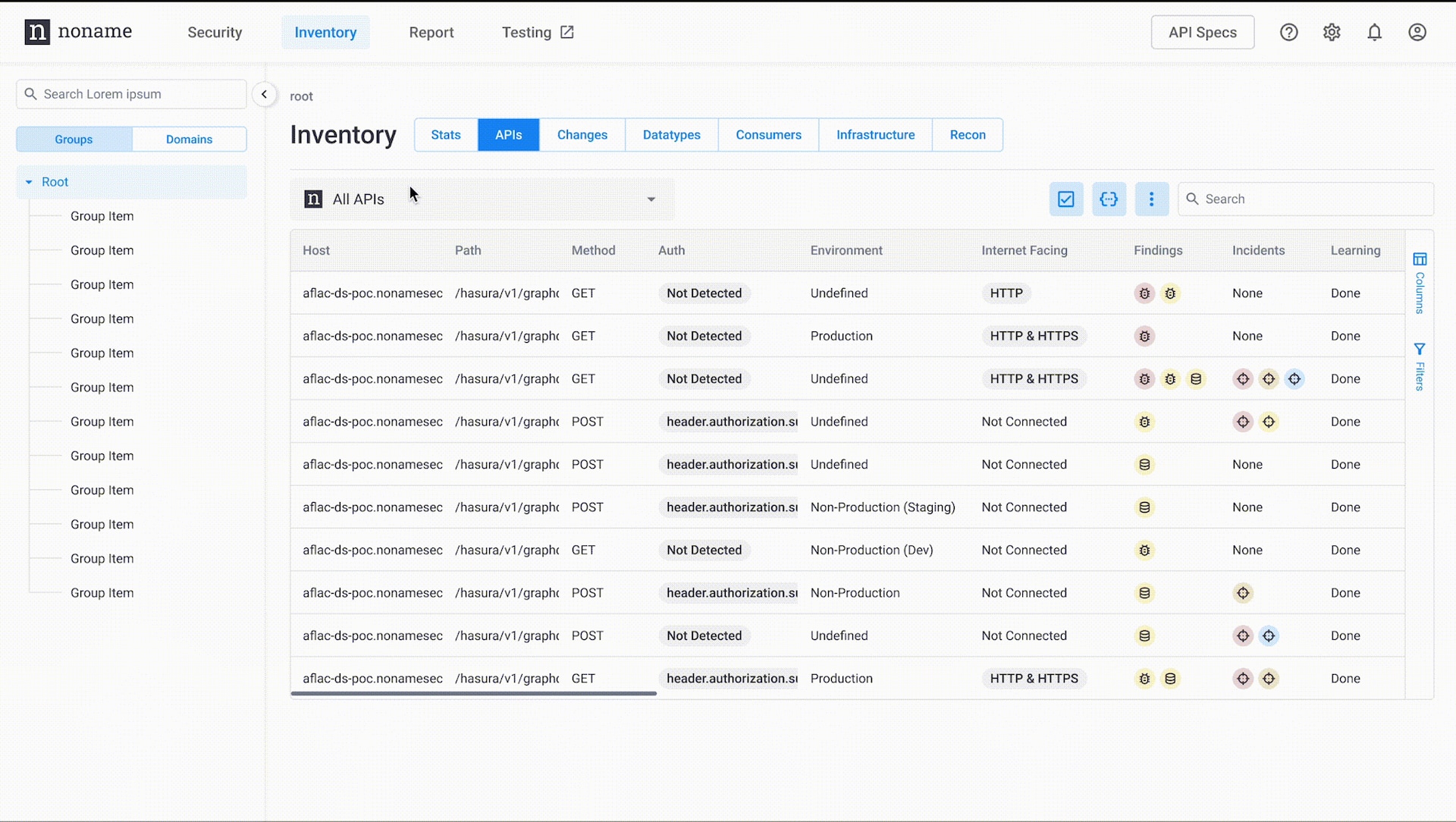
With this release, the Noname Security platform supports a new API property to identify the type of environment an API is running in. For example, you can specify if an API belongs to a nonproduction environment, such as QA or Staging, or is live in your Production environment. The environment type is defined for each API in your inventory under API details, and this information automatically propagates to your incidents and findings.
This allows you to prioritize your misconfigurations or vulnerabilities, fine-tune policy enforcement, and create more granular reports. In addition, soon you’ll be able to use environment types to automate your API testing processes. For example, by marking nonproduction APIs as “safe to test,” you’ll be able to perform automated API testing and prevent misconfigurations from advancing to production stages.
To learn more about setting environment types for your APIs, please see documentation.
Centralized configuration management for plug-ins
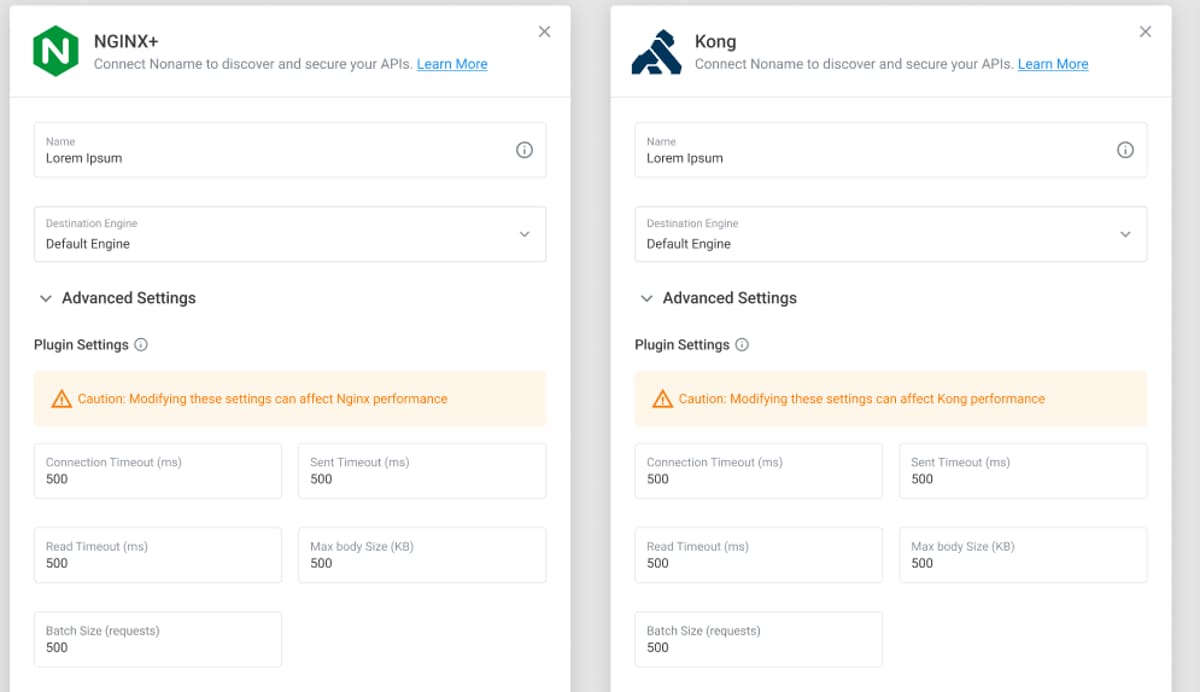
The Noname Security platform now supports centralized configuration management for traffic source plug-ins, including NGINX and Kong. Previously, some plug-in modifications had to be performed manually by updating static configuration files. Now, you can make configuration changes directly from the Noname Security platform user interface. This reduces the time required to reconfigure traffic source plug-ins and allows you to manage your plug-ins at scale.
To learn more about centralized plug-in management, please see the Kong plug-in and NGINX plug-in documentation.
Active Testing
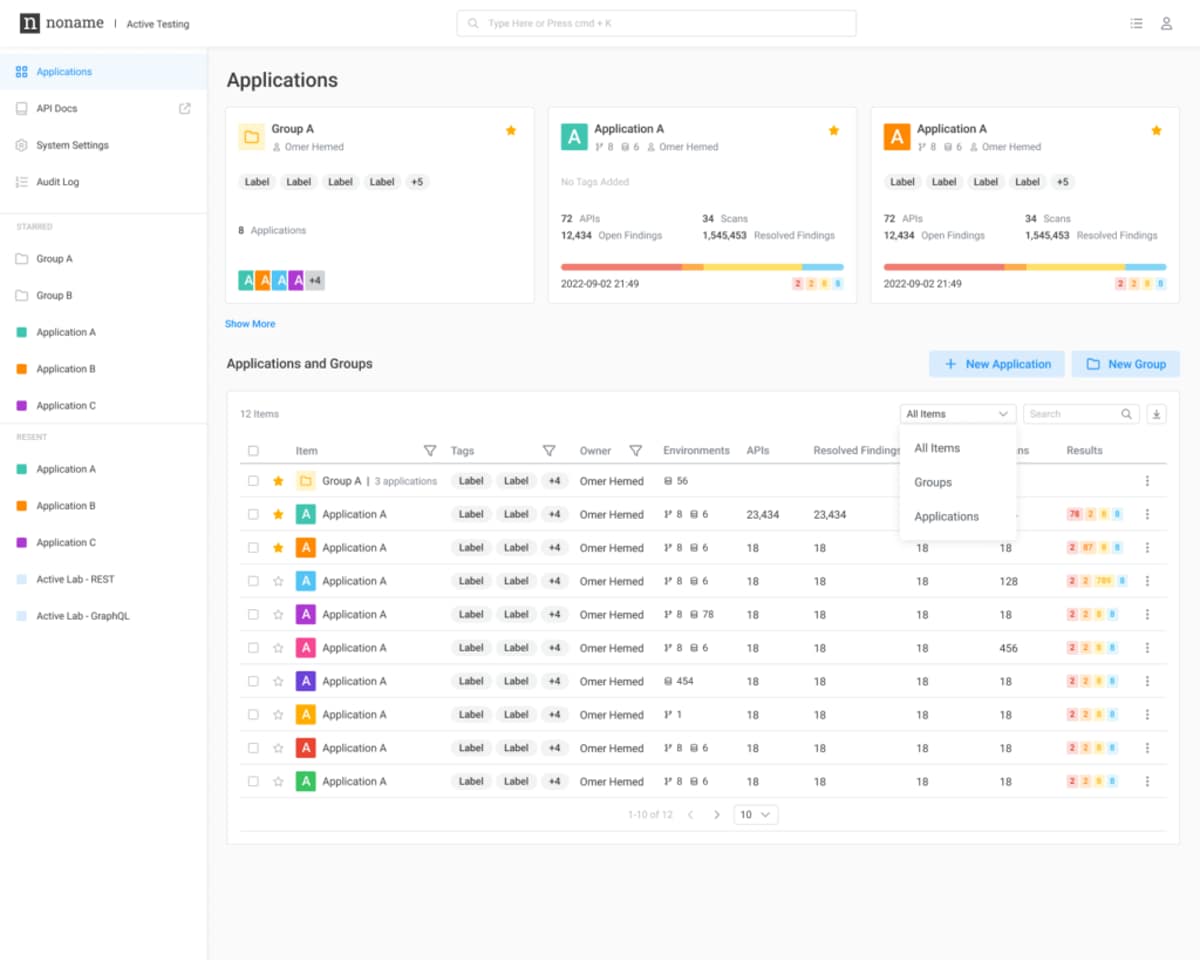
Application Grouping
The new Application Grouping feature streamlines at-scale application management and assignment for development teams. This feature improves how applications are organized and displayed within the Active Testing instance, offering a logical grouping of applications by team. For example, when a user logs in, they are now presented with a structured overview of application groups, allowing for an intuitive drill down into specific applications.
The grouping feature is tailored to display relevant applications based on the user’s role within the organization, enabling a personalized view that ranges from team-specific applications for managers to an all-encompassing overview for VPs or the CEO. This hierarchical visibility ensures that management at every level has direct access to the applications relevant to their teams, enhancing usability and oversight.
To learn more about this feature, please visit the documentation.
For additional information about the Noname Security 3.29 release, please review the release notes.