How to Perform a Zero Trust AWS Assessment with Infection Monkey and ScoutSuite
The latest release of the Infection Monkey introduced several fresh features that help IT security teams evaluate their network’s defenses against today’s evolving threat landscape and identify possible security gaps. However, one of the most a-peeling (🍌) new features is the tool’s new ability to assess organizations’ Zero Trust posture in the cloud through integration with ScoutSuite.
ScoutSuite is an open-source cloud security-auditing tool. It queries your cloud API to collect configuration data. Based on the information gathered, ScoutSuite shows security issues and risks present in your infrastructure. Infection Monkey can now take the findings from a ScoutSuite scan and categorize them according to Forrester’s Zero Trust eXtended (ZTX) ecosystem.
Why is assessing Zero Trust in AWS important?
The ZTX ecosystem stipulates that security professionals should never trust anything by default and always verify activity in the network on a case-by-case basis. However, with different configuration options in every tool or platform, it can be challenging to ensure there are no security gaps in your setup, such as overly permissive user access policies.
Running a cloud security scan using the Infection Monkey and ScoutSuite integration capabilities will help you assess your AWS configuration according to the key competencies of the ZTX ecosystem. By taking action on any issues highlighted in the resulting report, you can ensure your defenses are shored up in the event of a breach, significantly minimizing impact and potential data loss.
Running a Cloud Security scan with Infection Monkey
1. Download and install the Infection Monkey
Before you can go bananas, you’ll need to download the Infection Monkey open-source breach and attack simulation tool and swing over to our setup guides.
2. Enable ScoutSuite in Monkey Island
Next, you’ll need to provide the Infection Monkey with access to your cloud API (note: the ScoutSuite integration only supports AWS environments at this time).
Choose “Cloud Security Scan” in the “Run Monkey” options. Here you’ll also see more details about configuring ScoutSuite.
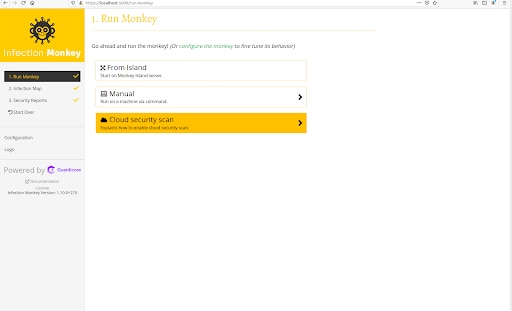 Choosing "Cloud Security Scan"
Choosing "Cloud Security Scan"
There are two options for providing access:
- Provide access keys:
- Create a new user with ReadOnlyAccess and SecurityAudit
policies and generate keys - Generate keys for your current user (faster but less secure)
- Create a new user with ReadOnlyAccess and SecurityAudit
- Configure AWS CLI:
- If the command-line interface is available on the Island, it will be used to access the cloud API
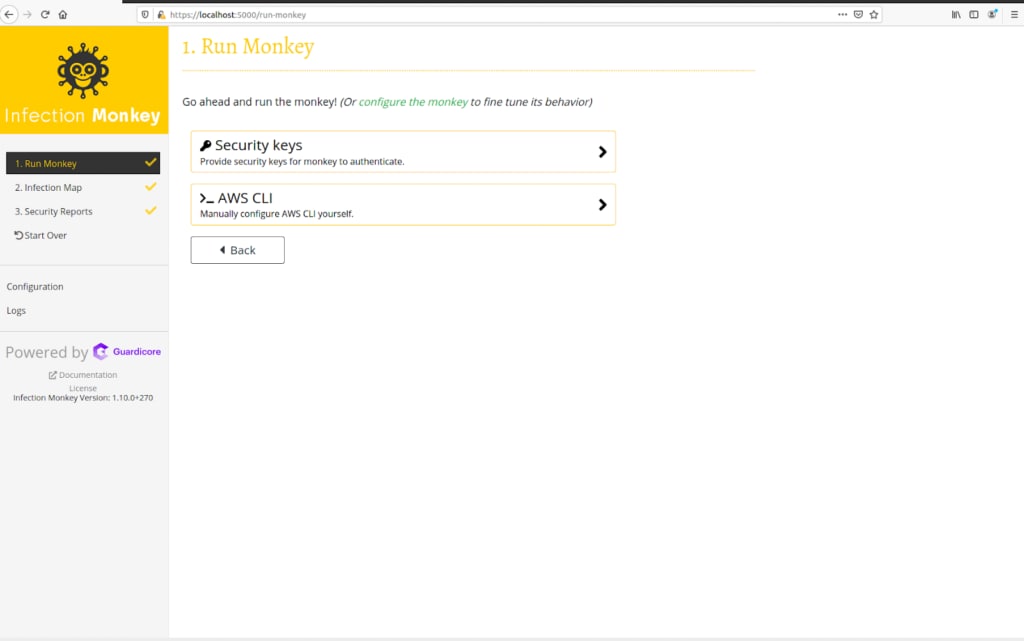 Providing access to the Monkey
Providing access to the Monkey
Before you move onto the next step, ensure a checkmark appears next to the AWS option. This verifies that ScoutSuite can access the API.
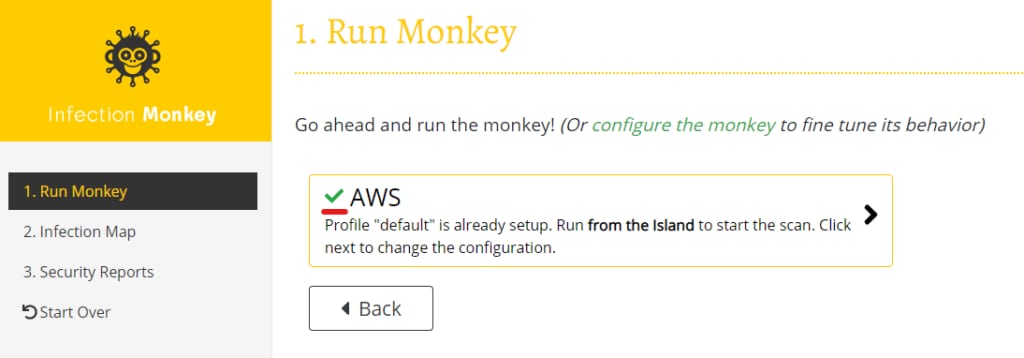 Look for the green checkmark to verify access
Look for the green checkmark to verify access
3. Release the Monkeys!
Navigate to “Run Monkey” and select the “From Island” option to start your scan. If you have successfully configured the cloud scan, the Infection Monkey will scan your cloud infrastructure to collect the configuration data.
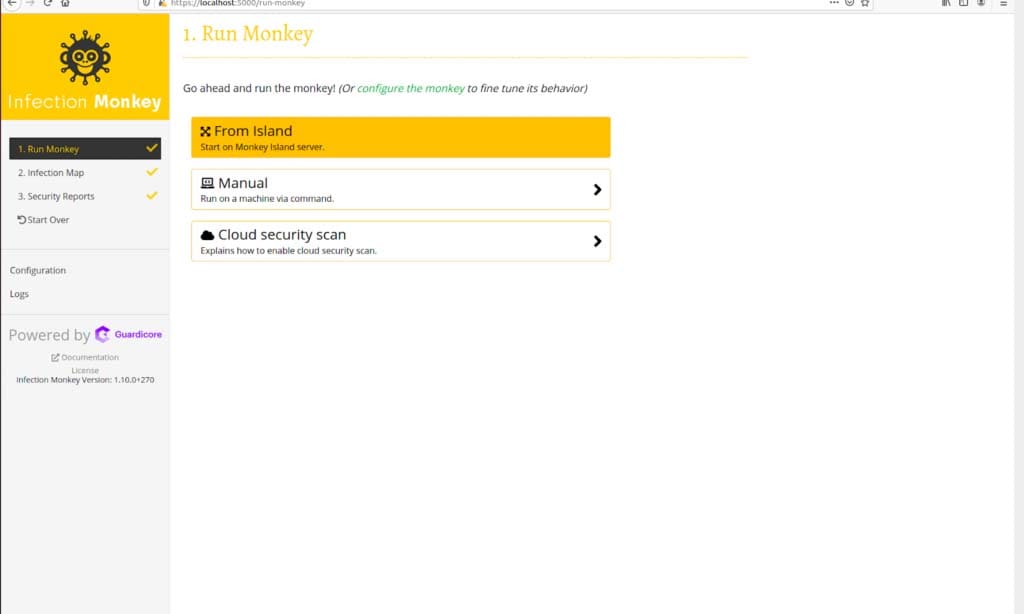 Selecting "From Island" to start the scan
Selecting "From Island" to start the scan
The scope of the network scan and other activities you may have configured the Infection Monkey agent to perform are ignored by the ScoutSuite integration, except Monkey Configuration -> System info collectors -> AWS collector, which needs to remain enabled!
Assessing your results
After the monkey agents finish their scan, all results, including tests run by ScoutSuite, can be reviewed in the Zero Trust report section. You’ll see that the assessment is categorized according to each pillar of Forrester’s ZTX ecosystem, allowing you to systematically prioritize, review and address issues by category. For example, if ScouteSuite identified an unmet ZTX requirement around authentication, it would be grouped under the ‘People’ pillar category of the report.
To access the findings click on “Security Reports” in the right-hand menu and select the “Zero Trust report” tab that appears along the top of your window.
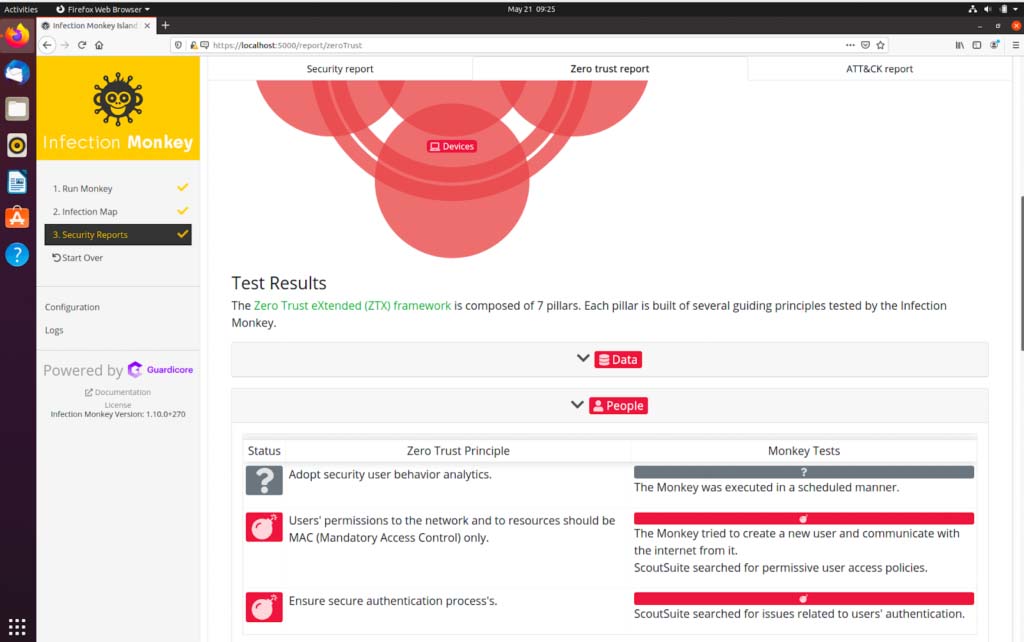 Test results mapped to ZTX framework
Test results mapped to ZTX framework
Specific tests are described in the “Test Results” section, which shows details about the Infection Monkey and ScoutSuite actions. The main difference between Infection Monkey findings and ScoutSuite findings is that the latter looks for violations of rules respectively created by the authors of ScoutSuite. These were constructed to evaluate the general configuration of AWS instances and flag gaps that might introduce security risks.
To see which ScoutSuite rules were evaluated, click on the “Rules” button next to the relevant test. You’ll see a list of rule dropdowns that are color-coded according to their status. Expand a rule to see its description, remediation recommendations, and more details about resources flagged. Each flagged resource has a path so you can easily locate it in the cloud and remediate the issue.
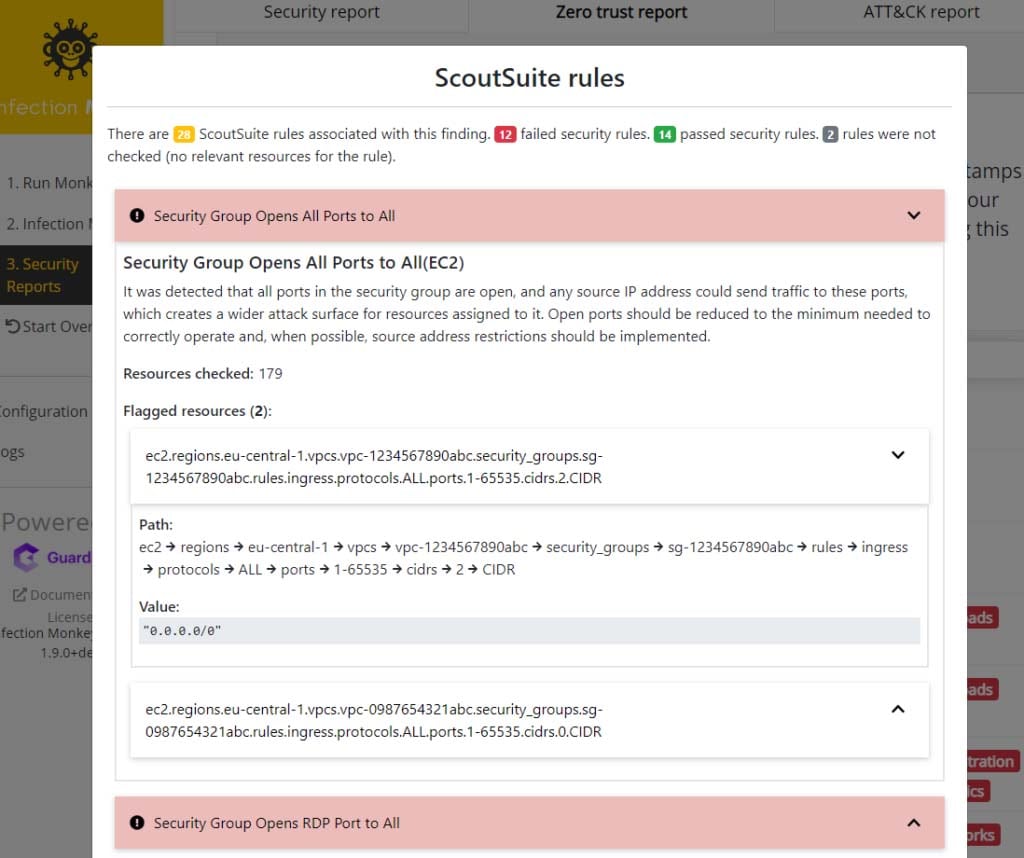 Rule dropdowns organized by status
Rule dropdowns organized by status
Ready to validate your security posture today? Join thousands of security teams that use Infection Monkey to assess their networks against ZTX ecosystem and MITRE ATT&CK framework.


