Introducing Guardicore Threat Intelligence Firewall
The Threat Intelligence Firewall is a new Guardicore Centra feature that blocks incoming and outgoing connections to known malicious IPs, eliminating malicious activity before it reaches your data center. To be up-to-date with the most recent threats, the list of known malicious IPs is updated once a day.
Guardicore’s Threat Intelligence Firewall is based on our recently launched CyberThreat Intelligence (CTI), a service that offers unique information on malicious IP addresses and domains. The data is collected by Guardicore’s threat intelligence sensors installed in multiple data centers, organizations and cloud providers worldwide.
What types of IP addresses we block
Guardicore’s Threat Intelligence Firewall blocks three types of IP addresses:
Attackers IPs
An Attacker IP is a machine that has managed to breach Guardicore’s threat intelligence sensors and executes attacks on them such as malware dropping, scanning internal subnets, modifying system files etc.
Scanners IPs
A Scanner IP is a machine that accesses one or more services across one or more subnets monitored by Threat Intelligence Sensors. This way we prevent the mere possibility of scanning your network which is normally one of the first steps of an attacker while looking for easy targets.
C&C IPs
A C&C IP is a machine that attackers connect to after breaching our Threat Intelligence Sensors. This way we prevent the attacker from communicating with its C&C servers which will ultimately cut the chain of attack.
These three types of IP addresses are grouped into three labels – Top Attackers, Top Scanners and Top C&C:
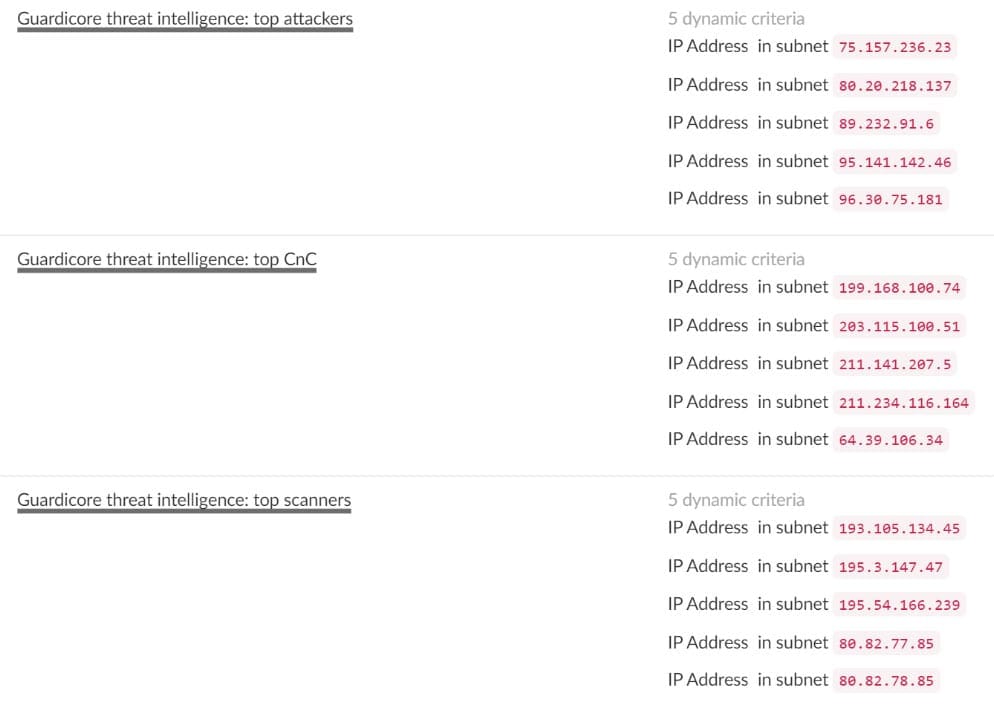
The Guardicore Threat Intelligence labels
Stopping Attackers at Bay
Updated daily, these IP blacklists are automatically fed into Centra to create rules to alert and block communications. We block incoming and outgoing connections to and from any port and process.
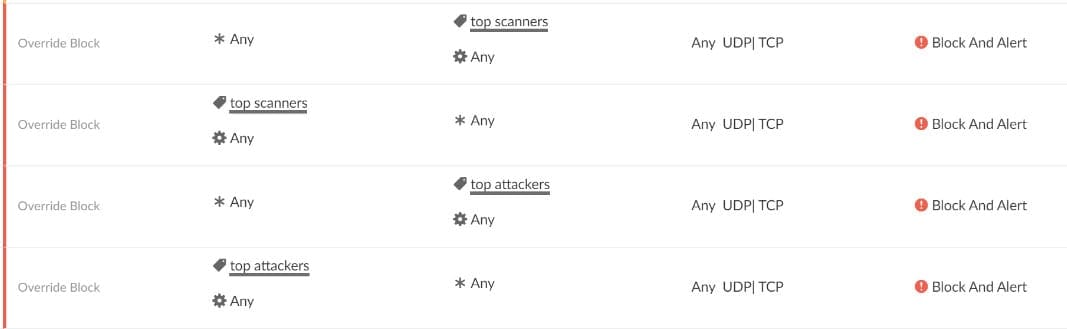
Example of the TI FW block policy rules
The Threat Intelligence Firewall rules take precedence over standard Allow, Alert, and Block rules so they don’t conflict with any other security policies you may have in place.
How do I know if a connection was blocked by the Threat Intelligence firewall?
For any firewall blocked connection an incident is created. The Threat Intelligence Firewall incidents are located under Centra’s Policy Violations section and are tagged with the Threat Intelligence Firewall tag. But what does a Threat Intelligence Firewall incident mean? Well, it depends. Let’s distinguish between policy violation incidents that are generated by an inbound connection as opposed to an outbound connection.
Inbound connection incident
If an inbound connection has been blocked, you shouldn’t be worried – you’ve been scanned by a compromised server. Check Guardicore Cyber Threat Intelligence to find out more about the attack you’ve just avoided.
Outbound connection incident
An outbound connection to a malicious destination means that you’ve probably been hacked. In that case, you should find the source of the attack. Consult with our security experts.
How to get Guardicore Threat Intelligence firewall
This feature is an enhancement offered to customers upon request. If you are interested in this solution, contact our customer success team [https://www.akamai.com/global-services/support]. If you’re not yet a customer and interested in more information, contact sales.



