India Becomes Top Global Target for API Attacks

The rise of India’s API economy
With digitalization playing an integral part in every facet of our lives, web application programming interfaces (APIs) have become the center of every digital experience today. Mobile applications run on web APIs and websites rely on APIs for core functionalities, such as logins and requests. APIs provide an open way to connect diverse applications to get data faster.
The shift to the cloud has driven the adoption of cloud-native application workloads with microservices that rely on APIs for communication and integration. Regulators have taken notice and have required the use of web APIs for ease of integration in areas such as open banking.
India leads the way in Asia Pacific (and globally!) in moving to an API economy.
2021 was considered the year of open banking in India and it is quickly keeping pace in 2022. Many banks in India are building their own open banking strategy by developing and monetizing APIs by banking on their digital platforms.
A rapidly expanding attack surface
However, with the increased adoption of APIs comes the risk of API attacks, and this new attack surface is expanding rapidly. This is in line with Gartner’s 2021 prediction that API abuses will be the most frequent attack vector, resulting in data breaches for enterprise applications. Web APIs seem to be a primary target for attackers as APIs are often left unprotected and they are less expensive to attack.
Securing public and private APIs
The rapid adoption of DevOps as part of the software development lifecycle has also increased the use of APIs for platform management and integration. Exposing API keys or sensitive data shared on open source repositories like GitHub has become a serious risk. Most developers do not have API security in mind when building their applications, and it is critical for businesses to adopt a security strategy to secure all their public and private APIs.
Global API attacks
Globally, from December 2021 to February 2022, we can observe that the United States saw the most attacks by an overwhelming majority (more than 3 billion attacks) and India came in at fifth overall. India experienced a total of 193,510,152 attacks during that period.
Figure 1 depicts the breakdown of attacks in billions and per attack vector for each country.
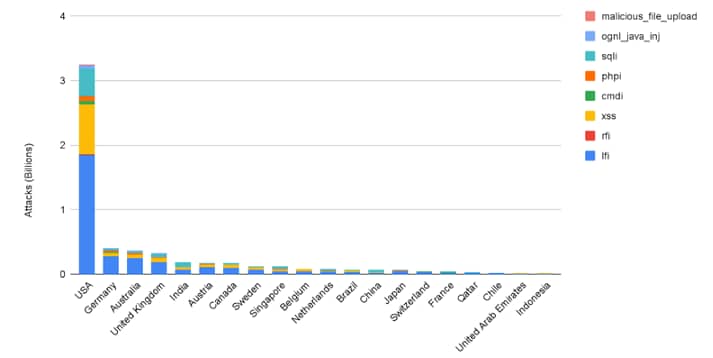 Fig. 1: Global web application and API attacks by destination country (Source: Akamai Intelligent Edge Platform)
Fig. 1: Global web application and API attacks by destination country (Source: Akamai Intelligent Edge Platform)
One clear observation, apart from the global presence of web applications and API attacks, is that the most used attack vector has now become local file inclusion (LFI).
This was consistent for the top five countries across the globe from December 2021 to March 2022. Previous Akamai threat research reports indicated that Structured Query Language injection (SQLi) was formerly the most used attack vector. .
Understanding the LFI attack vector
LFI is a software attack technique in which the attacker tries to trick a web application into running or exposing files on a web server. It is considered by the Open Web Application Security Project as a dangerous attack as it can expose sensitive data and lead to other attacks such as cross site scripting (XSS), remote code execution, or distributed denial of service.
For example, when a web page receives as input the path to a file with unsanitized content, the server would allow the content of the file to run as part of the web application code.
This enables the attacker to remotely execute malicious code such as malware, which could be the first stage of a ransomware attack.
Another use case would be directory traversal, which would allow the attacker to expose sensitive or confidential information like users’ credentials.
A simple example of a directory traversal attack is when an application displays or allows the user to download a file by changing a parameter in the web URL.
FROM:
https://vulnerable-site.com/?module=contact.php
TO:
https://vulnerable-site.com/?file=/etc/password
A vulnerable server would subsequently allow the system call, switch to root, and expose the content of the passwd file.
India: a top global attack target
Figure 2 depicts the number of web application and API attacks in India in millions from December 2021 to February 2022. Each graph line represents an attack vector, with the dark green line representing the total number of attacks inclusive of all attack vectors.
We observed:
Two major spikes, with February lasting the whole month indicating that attackers were renewing their focus in targeting web applications and APIs
LFI was the preferred attack vector
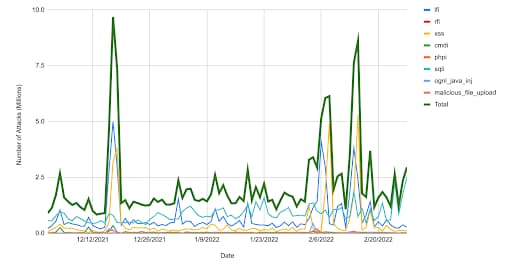 Fig. 2: Web application and API attacks in India over time (Source: Akamai Intelligent Edge Platform)
Fig. 2: Web application and API attacks in India over time (Source: Akamai Intelligent Edge Platform)
Financial services: API attack magnet
To understand which industry sector is driving those attack spikes, we analyzed the total attacks in India by industry. Figure 3 depicts financial services, ecommerce and digital media (eg, social media) as the top three most attacked verticals.
These three verticals have aggressively adopted an API-driven business model, opening their applications to attacks.
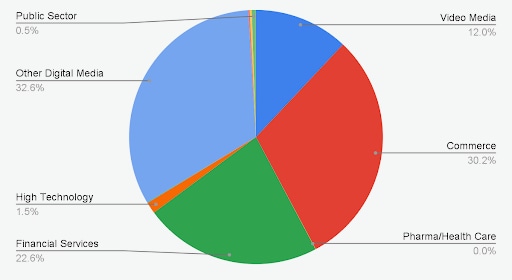 Fig. 3: Web application and API attacks in India by vertical (Source: Akamai)
Fig. 3: Web application and API attacks in India by vertical (Source: Akamai)
The top three verticals plotted over time shows that the financial services industry was the target of the majority of the LFI attacks, and was responsible for the two major spikes in December 2021 and February 2022, as indicated in Figure 4.
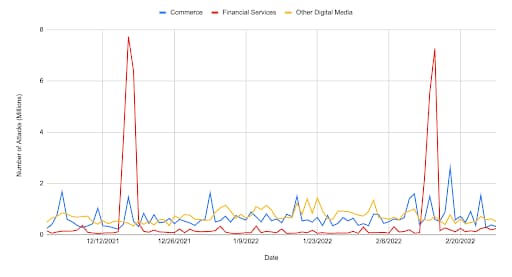 Fig. 4: Web application and API attacks in India by vertical over time (Source: Akamai Intelligent Edge Platform)
Fig. 4: Web application and API attacks in India by vertical over time (Source: Akamai Intelligent Edge Platform)
This could explain the change of attack vectors to LFI as attackers have been trying to find the easiest way to expose sensitive data or to create a staging ground for ransomware attacks.
We have seen major data breaches in India in which the command and control servers were actually an internal server used as a launching pad for lateral movement attacks such as ransomware.
Weak authentication and account takeover
Other key API vulnerabilities are weak authentication and account takeover. Unlike APIs, web browsers are traditionally able to issue challenges like captcha by rendering JavaScript as a first line of defense against credential stuffing attacks by malicious bots.
APIs are not able to render JavaScript and prevent credential stuffing–type attacks, making them vulnerable to using stolen credentials to gain unauthorized access to a server or endpoint.
Malicious bot requests
In the first half of 2022, we observed a steady increase of malicious bot attacks in India, hitting over 1 billion malicious bot requests in April 2022. Akamai research shows that an overwhelming number of bot requests are malicious and 10 times higher than benign requests; this would indicate that attackers are extensively using malicious bots to automate API attacks (Figure 5).
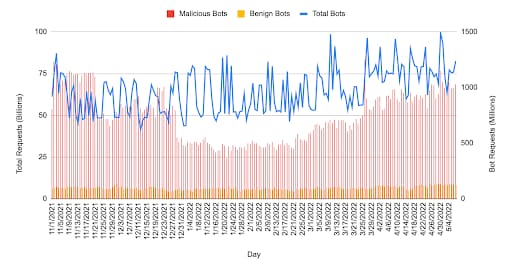 Fig. 5: India’s bot activity by category (Source: Akamai Intelligent Edge Platform)
Fig. 5: India’s bot activity by category (Source: Akamai Intelligent Edge Platform)
India needs to adopt an API security-first approach
To effectively mitigate the API attack surface, it is critical for all industry sectors in India to adopt adequate security best practices to secure their private and public APIs. Here are some actions to consider:
Adopt a security-first approach in the development of APIs. Developers should adopt security checks from code to runtime with code inspection and API validation.
Select a security solution that provides full visibility to all APIs to understand who is accessing your APIs from where and how.
Provide proactive API protection tailored to a customer’s organizational needs.
Encrypt all API traffic with TLS.
Ensure that your APIs do not expose more data than absolutely necessary. Enforce access of data at the API level. Prevent the sharing of confidential data.
Adopt strong authentication and authorization for your APIs to prevent credential stuffing and account takeover.
Deploy web application and API protection with built-in bot mitigation.
In September 2021, Akamai was named a Leader in the “Gartner Magic Quadrant for Web Application and API Protection” report and placed highest in the Ability to Execute category among the companies evaluated for their ability to protect web applications and APIs.
In addition, Akamai also received the highest scores for three of the four use cases in the “2021 Gartner Critical Capabilities for Cloud Web Application and API Protection” report, including the API Security Use Case.
Visit our website for more information about App & API Protector.




